http协议都是明文的,所以在基于Authtype控制访问页面的时候,利用抓包工具我们可以看到用户的账户和密码。https就是加密传输。对传输的数据进行加密
ssl会话过程
-
1、客户端发送可供选择的加密方式,并向服务器请求整数
-
2、服务器端发送证书以及选定的加密方式给客户端
-
3、客户端取得证书并进行证书验证,证书有以下几点注意
- 如果信任其给的证书
- a、验证证书的来源合法性;用CA的公钥解密证书上数字签名
- b、验证证书的内容的合法性,完整性验证
- c、检查证书的有效期限
- d、检查证书是否被吊销
- e、证书中拥有者的名字,与访问的目标主机要一致
- 4、客户端生成临时会话密钥(对称密钥),并使用服务器端的公钥加密比数据发送服务器,完成密钥交换
- 5、服务器用此密钥加密用户请求的资源,响应给客户端
ssl是基于ip地址实现,单ip地址的主机仅可以使用一个https虚拟机
- 如果信任其给的证书
https实现
首先创建私有ca自签证书
1)在CA主机上生成密钥
[root@CA CA]# (umask 066;openssl genrsa -out private/cakey.pem 2048)
Generating RSA private key, 2048 bit long modulus
...........................+++
......................+++
e is 65537 (0x10001)
2)在CA主机上生成自签证书
[root@CA CA]# openssl req -new -key private/cakey.pem -x509 -out cacert.pem -days 3650
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:beijing
Locality Name (eg, city) [Default City]:beijing
Organization Name (eg, company) [Default Company Ltd]:ydong.com
Organizational Unit Name (eg, section) []:opt
Common Name (eg, your name or your server's hostname) []:www.ydong.com
Email Address []:
3)创建CA证书所需要的文件
[root@CA CA]# touch index.txt
[root@CA CA]# echo 01 > serial
4)在httpd主机上安装ssl模块
[root@httpd ~]# yum install -y mod_ssl
5)在httpd主机上生成私钥
[root@httpd ~]# (umask 066;openssl genrsa -out /etc/pki/ssl/httpd.key 1024)
Generating RSA private key, 1024 bit long modulus
.............................................++++++
.............................................++++++
e is 65537 (0x10001)
6)httpd主机上生成签署请求
[root@httpd pki]# openssl req -new -key ssl/httpd.key -out ssl/http.csr -days 365
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:beijing
Locality Name (eg, city) [Default City]:beijing
Organization Name (eg, company) [Default Company Ltd]:ydong.com
Organizational Unit Name (eg, section) []:opt
Common Name (eg, your name or your server's hostname) []:www.ydong.com
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
7)将http.csr传输到CA主机上
[root@httpd pki]# scp ssl/http.csr 192.168.199.233:/tmp
8)CA审核httpd的请求
[root@CA CA]# openssl ca -in http.csr -out httpd.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Mar 16 13:34:07 2020 GMT
Not After : Mar 16 13:34:07 2021 GMT
Subject:
countryName = CN
stateOrProvinceName = beijing
organizationName = ydong.com
organizationalUnitName = opt
commonName = www.ydong.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
A4:46:CD:AC:9F:F4:72:BA:E2:AF:F7:B9:94:21:7B:C7:6C:6B:91:7D
X509v3 Authority Key Identifier:
keyid:AB:DE:71:81:02:EC:DB:66:7F:56:FE:BC:DD:15:4E:9A:0A:62:2B:31
Certificate is to be certified until Mar 16 13:34:07 2021 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
9)将httpd.crt发送到httpd主机上
[root@CA CA]# scp httpd.crt 192.168.199.243:/etc/pki/ssl
10)修改ssl.conf的配置文件
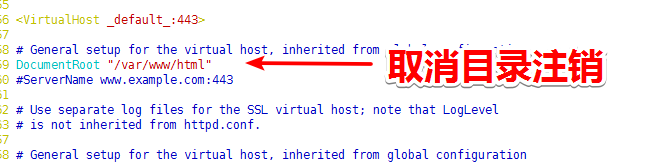
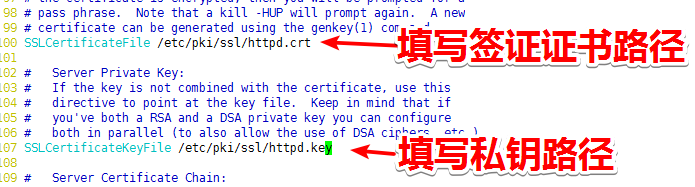
11)重启服务,测试
[root@httpd httpd]# ss -tnl | grep -E "80|443"
LISTEN 0 128 [::]:443 [::]:*
LISTEN 0 128 [::]:80 [::]:*
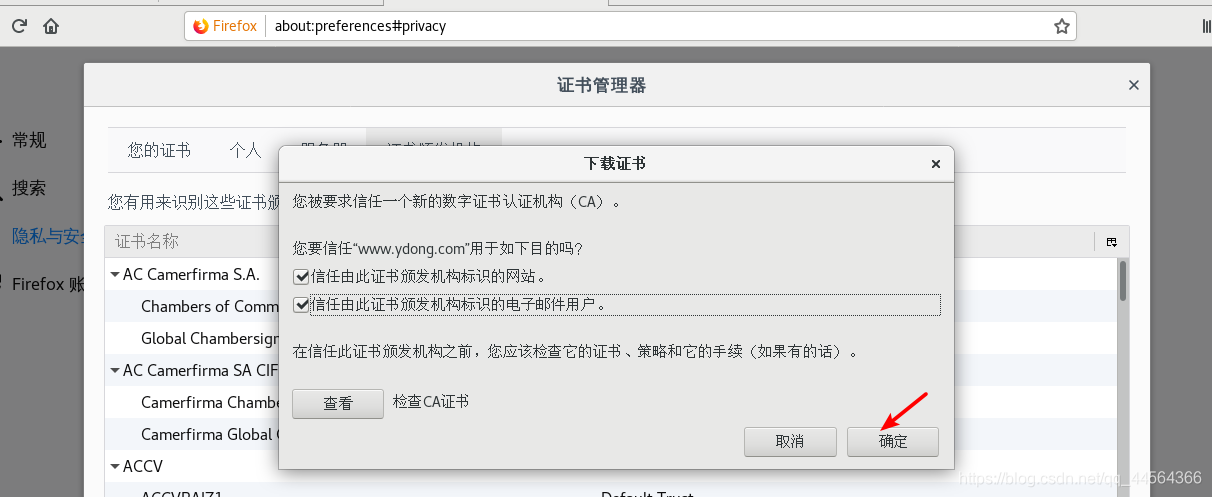
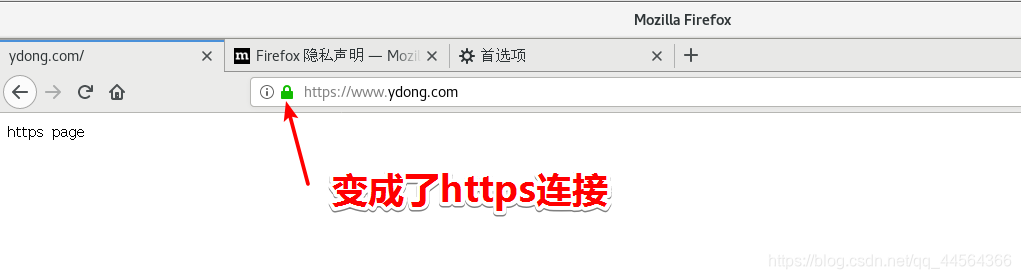
http重定向https实现
使用Redirect实现。
[root@httpd httpd]# cat conf.d/test.conf
<VirtualHost *:80>
<Directory /var/www/html>
Options none
AllowOverride none
Require all granted
</Directory>
Redirect temp "/index.html" "https://www.ydong.com/index.html"
</VirtualHost>
temp:是临时重定向,意思就是也许以后之前的网址还会在用。只是临时的重定向
状态码是302
[root@httpd httpd]# cat conf.d/test.conf
<VirtualHost *:80>
<Directory /var/www/html>
Options none
AllowOverride none
Require all granted
</Directory>
Redirect permanent "/index.html" "https://www.ydong.com/index.html"
</VirtualHost>
permanent:是301永久重定向。
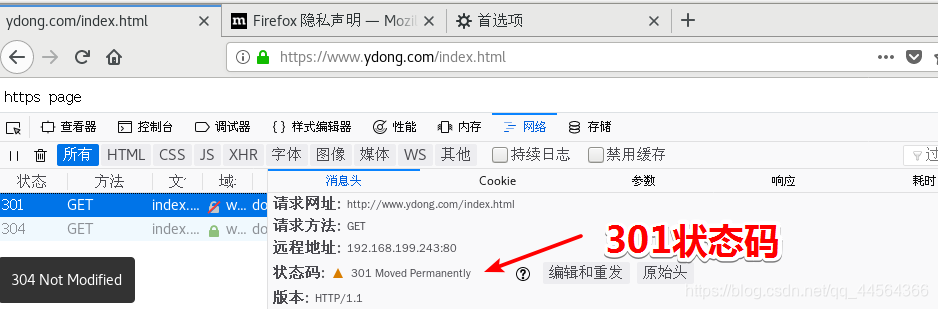
上述虽然可以进行跳转,但是也存在不安全的现象。因为它要先访问http,那么可不可以直接返回https,而不访问http呢?
HSTS就是用来解决这一问题的。
服务器端配置支持HSTS后,会在给浏览器返回的HTTP首部中携带HSTS字段。浏览器获取到该信息后,会将所有HTTP访问请求在内部做307跳转到HTTPS。而无需任何网络过程
[root@httpd httpd]# cat conf.d/test.conf
<VirtualHost *:80>
<Directory /var/www/html>
Options none
AllowOverride none
Require all granted
</Directory>
Header always set Strict-Transport-Security "maxage=31536000"
RewriteEngine on
RewriteRule ^(/.*)$ https://%{
HTTP_HOST}$1 [redirect=302]
</VirtualHost>