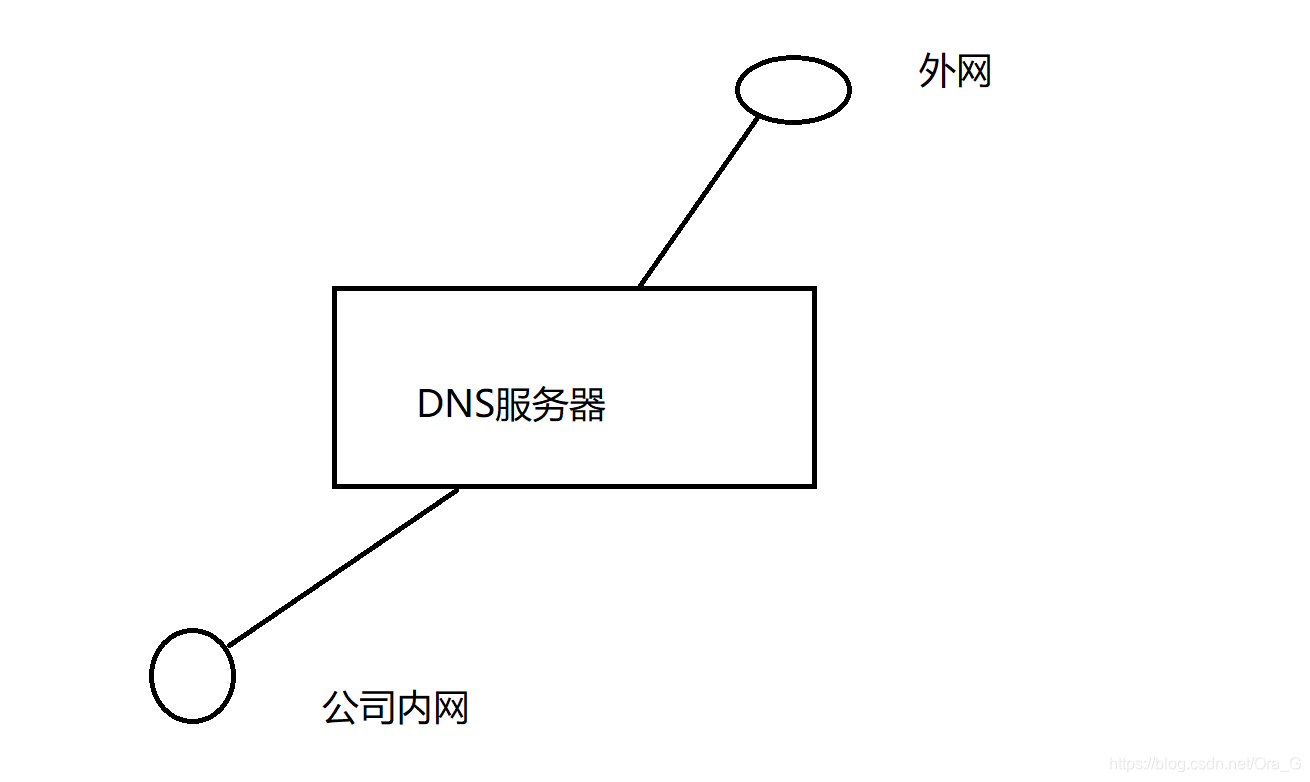
分离解析的作用就是一台连接内外网的服务器,在内网和外网输入域名访问的地址可以不一样
安装 DNS 程序
已安装:
bind.x86_64 32:9.11.4-16.P2.el7_8.6 作为依赖被安装:
bind-export-libs.x86_64 32:9.11.4-16.P2.el7_8.6
作为依赖被升级:
bind-libs.x86_64 32:9.11.4-16.P2.el7_8.6 bind-libs-lite.x86_64 32:9.11.4-16.P2.el7_8.6 bind-license.noarch 32:9.11.4-16.P2.el7_8.6 bind-utils.x86_64 32:9.11.4-16.P2.el7_8.6
dhclient.x86_64 12:4.2.5-79.el7.centos dhcp-common.x86_64 12:4.2.5-79.el7.centos dhcp-libs.x86_64 12:4.2.5-79.el7.centos
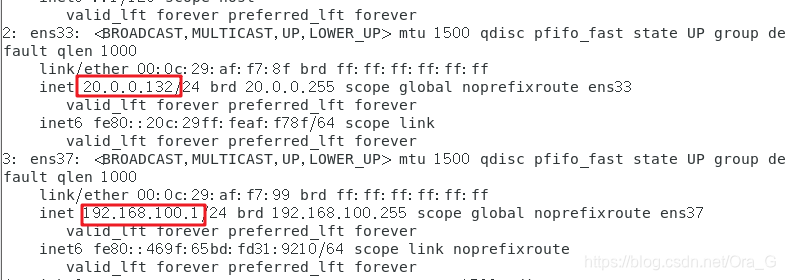
在该服务器上安装两块网卡,分别连接内网和外网,且充当网关
配置主配置文件
options {
listen-on port 53 { any; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
recursing-file "/var/named/data/named.recursing";
secroots-file "/var/named/data/named.secroots";
allow-query { any; };
配置区域文件
手敲的!!!
view "DNS.com.lan" {
match-clients { 192.168.100.0/24; };
zone "DNS.com" IN {
type master;
file "DNS.com.lan";
};
zone "." IN {
type hint;
file "named.ca";
};
};
view "DNS.con.wan" {
match-clients { 20.0.0.0/8; };
zone "DNS.com" IN {
type master;
file "DNS.com.wan";
};
};
**下面的都能删了!**
删除 主配置文件里的
zone "." IN {
type hint;
file "named.ca";
};
配置区域数据配置文件
[root@localhost named]# cp -p named.localhost DNS.com.lan
[root@localhost named]# vim DNS.com.lan
$TTL 1D
@ IN SOA @ rname.invalid. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS @
A 192.168.100.1
www IN A 192.168.100.20
[root@localhost named]# cp -p DNS.com.lan DNS.com.wan
[root@localhost named]# vim DNS.com.wan
$TTL 1D
@ IN SOA @ rname.invalid. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS @
A 20.0.0.132
www IN A 20.0.0.140
验证不同网段的域名解析
再开两台虚拟机,分别配置20网段和192网段
[root@localhost ~]# nslookup www.DNS.com
Server: 20.0.0.132
Address: 20.0.0.132#53
Name: www.DNS.com
Address: 20.0.0.140
[root@localhost ~]# nslookup www.DNS.com
Server: 192.168.100.1
Address: 192.168.100.1#53
Name: www.DNS.com
Address: 192.168.100.20
试验完成
注:若本机可以解析,但是其他客户端不能解析,看看是不是防火墙或者核心防护的问题
客户端DNS的地址和网关地址可以直接填该服务器,因为该服务器充当了DNS服务器和网关