文章目录
前言
大多数企业服务器是通过远程登录的方式来进行管理的
当需要从一个工作站管理数以百计的服务器主机时,远程维护的方式将更占优势
SSH 为 Secure Shell 的缩写,由 IETF 的网络小组(Network Working Group)所制定;SSH 为建立在应用层基础上的安全协议。SSH 是较可靠,专为远程登录会话和其他网络服务提供安全性的协议。利用 SSH 协议可以有效防止远程管理过程中的信息泄露问题。SSH最初是UNIX系统上的一个程序,后来又迅速扩展到其他操作平台。SSH在正确使用时可弥补网络中的漏洞。SSH客户端适用于多种平台。几乎所有UNIX平台—包括HP-UX、Linux、AIX、Solaris、Digital UNIX、Irix,以及其他平台,都可运行SSH。
一:SSH远程管理
1.1:配置Open SSH服务端
1.1.1:SSH协议
为客户机提供安全的shell环境,用于远程管理
默认端口:TCP 22
1.1.2:OpenSSH服务
服务名称:sshd
服务端主程序:/usr/sbin/sshd
服务端配置文件:/etc/ssh/sshd_config
ssh_config:针对客户端
sshd_config:针对服务端

1.2 ssh功能
传统的网络服务程序,如:ftp、pop和telnet在本质上都是不安全的,因为它们在网络上用明文传送口令和数据,别有用心的人非常容易就可以截获这些口令和数据。而且,这些服务程序的安全验证方式也是有其弱点的, 就是很容易受到“中间人”(man-in-the-middle)这种方式的攻击。所谓“中间人”的攻击方式, 就是“中间人”冒充真正的服务器接收你传给服务器的数据,然后再冒充你把数据传给真正的服务器。服务器和你之间的数据传送被“中间人”一转手做了手脚之后,就会出现很严重的问题。通过使用SSH,你可以把所有传输的数据进行加密,这样"中间人"这种攻击方式就不可能实现了,而且也能够防止DNS欺骗和IP欺骗。使用SSH,还有一个额外的好处就是传输的数据是经过压缩的,所以可以加快传输的速度。SSH有很多功能,它既可以代替Telnet,又可以为FTP、PoP、甚至为PPP提供一个安全的"通道"
1.3 SSH提供两种客户端级别的安全验证。
1.3.1第一种级别(基于口令的安全验证)
只要你知道自己帐号和口令,就可以登录到远程主机。所有传输的数据都会被加密,但是不能保证你正在连接的服务器就是你想连接的服务器。可能会有别的服务器在冒充真正的服务器,也就是受到“中间人”这种方式的攻击。
1.3.2第二种级别(基于密匙的安全验证)
需要依靠密匙,也就是你必须为自己创建一对密匙,并把公用密匙放在需要访问的服务器上。如果你要连接到SSH服务器上,客户端软件就会向服务器发出请求,请求用你的密匙进行安全验证。服务器收到请求之后,先在该服务器上你的主目录下寻找你的公用密匙,然后把它和你发送过来的公用密匙进行比较。如果两个密匙一致,服务器就用公用密匙加密“质询”(challenge)并把它发送给客户端软件。客户端软件收到“质询”之后就可以用你的私人密匙解密再把它发送给服务器。
用这种方式,你必须知道自己密匙的口令。但是,与第一种级别相比,第二种级别不需要在网络上传送口令。
第二种级别不仅加密所有传送的数据,而且“中间人”这种攻击方式也是不可能的(因为他没有你的私人密匙)。
具体配置详解
一般ssh都是系统自带,默认端口号22 ,可以先查看程序端口有无运行
[root@ shanan ~]# netstat -ntap | grep 22
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 6802/sshd
tcp 0 0 192.168.100.55:22 192.168.100.1:51468 ESTABLISHED 7300/sshd: root@pts
tcp 0 52 192.168.100.55:22 192.168.100.1:52631 ESTABLISHED 7406/sshd: root@pts
tcp6 0 0 :::22 :::* LISTEN 6802/sshd
[root@ shanan ~]#
[root@ shanan ~]# which sshd
/usr/sbin/sshd
[root@ shanan ~]# cd /etc/ssh
[root@ shanan ssh]# ls
moduli sshd_config ssh_host_ecdsa_key.pub ssh_host_ed25519_key.pub ssh_host_rsa_key.pub
ssh_config ssh_host_ecdsa_key ssh_host_ed25519_key ssh_host_rsa_key
[root@ shanan ssh]# vi /sshd_config

此端口号并不固定,可随意修改,但是如果修改了,那么在其他终端登录时,需要指定一下端口号
举例:如果将端口号 改成123 ,主服务器地址为192.168.100.55
那么在其它终端登录就要如此:登录时要用
[root@sha ~]# ssh -p 123 root@192.168.100.55
二 . 普通口令登录操作
2.1 普通的口令登录方式
下面看一下默认的的22端口,普通的口令登录方式,本服务器IP192.168.100.55
在客户机上远程登录
[root@sha ~]# ssh root@192.168.100.55
The authenticity of host '192.168.100.55 (192.168.100.55)' can't be established.
ECDSA key fingerprint is SHA256:VI/UvpBRoUkYCL9Vpv3H374zuKtzA7KHns0qPXcVB8Q.
ECDSA key fingerprint is MD5:b9:01:85:51:fe:46:66:ce:01:e0:58:36:80:ed:c3:c9.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.100.55' (ECDSA) to the list of known hosts.
[email protected]'s password:
Permission denied, please try again.
root@192.168.100.55's password:
Last failed login: Sun Jul 12 11:02:44 CST 2020 from 192.168.100.50 on ssh:notty
There was 1 failed login attempt since the last successful login.
Last login: Sun Jul 12 10:55:02 2020 from 192.168.100.1
[root@ shanan ~]# cd /opt 登录成功后可以正常操作创建文件等
[root@ shanan opt]# touch 123.txt 创建文件123
在服务器处查看
[root@ shanan ssh]# ls /opt 在主机处查看
123.txt abc
[root@ shanan ssh]#
[root@ shanan opt]# exit
登出
Connection to 192.168.100.55 closed.
[root@sha ~]#
2.2 限制账号的登录
但是ROOT作为最高管理员,在其他设备登录有一定风险,我们需要对它进行限制登录
vi /etc/ssh/sshd_config

下面进行测试,在服务器端创建3个账号
创建用户
[root@ shanan ssh]# useradd test1
[root@ shanan ssh]# echo "123456" | passwd --stdin test 1
passwd:只能指定一个用户的名称。
[root@ shanan ssh]# echo "123456" | passwd --stdin test1
更改用户 test1 的密码 。
passwd:所有的身份验证令牌已经成功更新。
[root@ shanan ssh]# useradd test2
[root@ shanan ssh]# echo "123456" | passwd --stdin test2
更改用户 test2 的密码 。
passwd:所有的身份验证令牌已经成功更新。
[root@ shanan ssh]# useradd test3
[root@ shanan ssh]# echo "123456" | passwd --stdin test3
更改用户 test3 的密码 。
passwd:所有的身份验证令牌已经成功更新。
在客户端登录测试
再次使用ROOT登录,提示没有权限,之前的更改参数生效了
root@sha ~]# vi /etc/ssh/sshd_config
[root@sha ~]# ssh root@192.168.100.55
root@192.168.100.55's password:
Permission denied, please try again.
[email protected]'s password:
换个test1账户,提示登录成功,因为没有限制它
[root@sha ~]# ssh test1@192.168.100.55
test1@192.168.100.55's password:
[test1@ shanan ~]$
此刻,我们用su 命令切换ROOT,发现又登录上去了,只是以test1做跳板
[test1@ shanan ~]$ su - root
密码:
上一次登录:日 7月 12 11:02:50 CST 2020从 192.168.100.50pts/2 上
最后一次失败的登录:日 7月 12 11:24:27 CST 2020从 192.168.100.50ssh:notty 上
最有一次成功登录后有 2 次失败的登录尝试。
[root@ shanan ~]#
[root@ shanan ~]# 、
这时一个比较严重问题,突然想到之前的PAM安全认证,行动起来!
服务器端操作
[root@ shanan ssh]# vi /etc/pam.d/su

[root@ shanan ssh]# gpasswd -a test2 wheel
正在将用户“test2”加入到“wheel”组中
[root@ shanan ssh]# id test1
uid=1000(test1) gid=1000(test1) 组=1000(test1)
[root@ shanan ssh]# id test2
uid=1001(test2) gid=1001(test2) 组=1001(test2),10(wheel)
继续在客户端测试
下面再次尝试,发现test1 已经无法用su 命令切换了
[test1@ shanan ~]$ ssh test1@192.168.100.55
The authenticity of host '192.168.100.55 (192.168.100.55)' can't be established.
ECDSA key fingerprint is SHA256:VI/UvpBRoUkYCL9Vpv3H374zuKtzA7KHns0qPXcVB8Q.
ECDSA key fingerprint is MD5:b9:01:85:51:fe:46:66:ce:01:e0:58:36:80:ed:c3:c9.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.100.55' (ECDSA) to the list of known hosts.
[email protected]'s password:
Last login: Sun Jul 12 11:24:46 2020 from 192.168.100.50
[test1@ shanan ~]$ su - root
密码:
su: 拒绝权限
[test1@ shanan ~]$
[test1@ shanan ~]$ su - root
密码:
su: 拒绝权限
[test1@ shanan ~]$ su - test2
密码:
su: 拒绝权限
[test1@ shanan ~]$
Test2 因为加入wheel 组,所以有权限,可以使用SU命令
test2@192.168.100.55's password:
Last failed login: Sun Jul 12 11:36:30 CST 2020 on pts/3
There was 1 failed login attempt since the last successful login.
[test2@ shanan ~]$ su - root
密码:
上一次登录:日 7月 12 11:26:44 CST 2020pts/2 上
最后一次失败的登录:日 7月 12 11:36:17 CST 2020pts/3 上
最有一次成功登录后有 2 次失败的登录尝试。
[root@ shanan ~]#
2.3 密码错误尝试次数限制
在服务器上修改配置,开启密码错误尝试次数为6次
vi /etc/ssh/sshd_config

在客户机测试登录,发现才输错密码3次就不让尝试了
[root@sha ~]# ssh test1@192.168.100.55
test1@192.168.100.55's password:
Permission denied, please try again.
[email protected]'s password:
Permission denied, please try again.
test1@192.168.100.55's password:
Permission denied (publickey,gssapi-keyex,gssapi-with-mic,password).
[root@sha ~]#
这是为什么? 一番寻找原来是客户端自己本身限制了,一条命令解决它
我们输入以下命令,修改本地限制次数为8次,这次共计尝试了6次失败
[root@sha ~]# ssh -o NumberOFPasswordPrompts=8 test1@192.168.100.55
test1@192.168.100.55's password:
Permission denied, please try again.
[email protected]'s password:
Permission denied, please try again.
test1@192.168.100.55's password:
Permission denied, please try again.
[email protected]'s password:
Permission denied, please try again.
test1@192.168.100.55's password:
Permission denied, please try again.
[email protected]'s password:
Received disconnect from 192.168.100.55 port 22:2: Too many authentication failures
Authentication failed.
[root@sha ~]#
2.4 白名单和黑名单
vi /etc/ssh/sshd_config
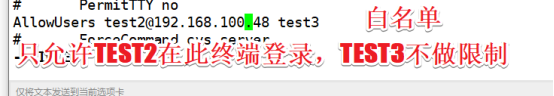
此时test2 在别的终端上已经登录不上了
[
root@sha ~]# ssh test2@192.168.100.55
test2@192.168.100.55's password:
Permission denied, please try again.
[email protected]'s password:
Test3 却可以,因为没有限制它
[root@sha ~]# ssh test3@192.168.100.55
test3@192.168.100.55's password:
Last failed login: Sun Jul 12 12:01:28 CST 2020 from 192.168.100.50 on ssh:notty
There were 3 failed login attempts since the last successful login.
[test3@ shanan ~]$
Test1 也不行,因为它没有加入白名单
[email protected]'s password:
Permission denied, please try again.
test1@192.168.100.55's password:
在指定的终端上 TEST2成功的登录
[root@sh ~]# ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.100.48 netmask 255.255.255.0 broadcast 192.168.100.255
inet6 fe80::20c:29ff:fe63:2b8e prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:63:2b:8e txqueuelen 1000 (Ethernet)
RX packets 832 bytes 76299 (74.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 697 bytes 61614 (60.1 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
device interrupt 19 base 0x2000
[root@sh ~]# ssh test2@192.168.100.55
test2@192.168.100.55's password:
Last failed login: Sun Jul 12 12:07:35 CST 2020 from 192.168.100.48 on ssh:notty
There were 3 failed login attempts since the last successful login.
Last login: Sun Jul 12 12:01:39 2020 from 192.168.100.50
[test2@ shanan ~]$
黑名单: Denyusers 禁止某用户或组等登陆
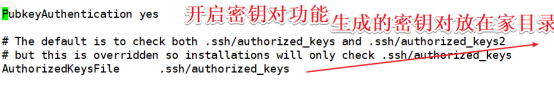
三 . 秘钥对登陆方式
vi /etc/ssh/sshd_config
3.1 客户端操作:
[caiwu@sha ~]$
[caiwu@sha ~]$ ssh-keygen -t ecdsa 椭圆曲线数字签名
[caiwu@sha ~]$ ssh-keygen -t ecdsa
Generating public/private ecdsa key pair.
Enter file in which to save the key (/home/caiwu/.ssh/id_ecdsa):
Created directory '/home/caiwu/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/caiwu/.ssh/id_ecdsa.
Your public key has been saved in /home/caiwu/.ssh/id_ecdsa.pub.
The key fingerprint is:
SHA256:BT7lRsil80pJsF0vfN7CBvAvG9nqVv35r6M37zg+TOM caiwu@sha
The key's randomart image is:
+---[ECDSA 256]---+
| ..oo= |
| =o@ . |
| . B O o |
| . B X . |
| S = B.. |
| . . *..+ |
| . o. + o.|
| .. Eo.|
| .. .++OB|
+----[SHA256]-----+
[caiwu@sha ~]$
将公钥推给主服务器的TEST3 ,并输入TEST3的密码
[caiwu@sha .ssh]$ ssh-copy-id -i id_ecdsa.pub test3@192.168.100.55
/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "id_ecdsa.pub"
/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
test3@192.168.100.55's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh 'test3@192.168.100.55'"
and check to make sure that only the key(s) you wanted were added.
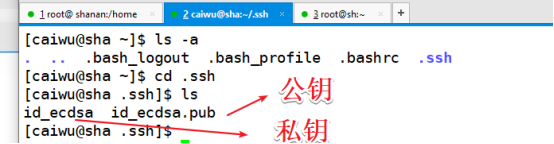
切到主服务器查看公钥文件
[root@ shanan test3]# cd .ssh
[root@ shanan .ssh]# ls
authorized_keys
[root@ shanan .ssh]# ls
authorized_keys
[root@ shanan .ssh]# cat authorized_keys
ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBI3hmW1+6+kPlChrx48jvIVNSyqATiee8v9/YpXEPh0IaVBW5IGk+OhCijrvCCWJo5/CZpWMCRf41IxC9UhEyS4= caiwu@sha
[root@ shanan .ssh]#
在客户端测试
测试登录,此时输入密钥对密码即可
[caiwu@sha .ssh]$ ssh test3@192.168.100.55
Enter passphrase for key '/home/caiwu/.ssh/id_ecdsa':
Last login: Sun Jul 12 12:05:29 2020 from 192.168.100.50
[test3@ shanan ~]$
[test3@ shanan ~]$
[test3@ shanan ~]$ exit
登出
再次登录,还是如此登录
Connection to 192.168.100.55 closed.
[caiwu@sha .ssh]$ ssh test3@192.168.100.55
Enter passphrase for key '/home/caiwu/.ssh/id_ecdsa':
Last login: Sun Jul 12 16:24:04 2020 from 192.168.100.50
[test3@ shanan ~]$
3.2 开启bash代理,免去重复输入秘钥的麻烦
一直输入秘钥比较麻烦,使用代理功能解决此问题
[caiwu@sha .ssh]$ ssh-agent bash 启动代理bash 功能
[caiwu@sha .ssh]$ ssh-add 添加秘钥口令
Enter passphrase for /home/caiwu/.ssh/id_ecdsa: 输入秘钥对秘钥
Identity added: /home/caiwu/.ssh/id_ecdsa (/home/caiwu/.ssh/id_ecdsa)
再次登录服务器TEST03,发现不需要口令了,直接切进去了
[caiwu@sha .ssh]$ ssh test3@192.168.100.55
Last login: Sun Jul 12 16:25:25 2020 from 192.168.100.50
[test3@ shanan ~]$
3.3 文件和 文件夹的拷贝
在客户端创建文件和文件夹
[root@sha ~]# cd /opt
[root@sha opt]# touch 123.txt
[root@sha opt]# mkdir -p /aa/bb
[root@sha opt]# echo "123455" > 123.txt
3.3.1 拷贝文件到主服务器
[root@sha opt]# scp 123.txt root@192.168.100.55:/home/ 将文件123 发给主服务器端
root@192.168.100.55's password:
123.txt 100% 7 3.9KB/s 00:00
[root@sha opt]#
然后切换到主服务器端查看
[root@ shanan home]# cat 123.txt
123455
[root@ shanan home]#
3.3.2将文件夹拷贝到主服务器
[root@sha opt]# scp -r /aa root@192.168.100.55:/home/
root@192.168.100.55's password:
[root@sha opt]#
在服务器端查看
[root@ shanan home]# ls
123.txt 456.txt aa test1 test2 test3
[root@ shanan home]# cd aa
[root@ shanan aa]# ls
bb
[root@ shanan aa]#
3.4 从服务器下载文件到本地
从主服务器处下载123 文件到本地
[root@sha opt]# sftp root@192.168.100.55
root@192.168.100.55's password:
Connected to 192.168.100.55.
sftp> ls
anaconda-ks.cfg
sftp> cd /home
sftp> ls
123.txt 456.txt aa test1 test2 test3
sftp> get 123.txt
Fetching /home/123.txt to 123.txt
/home/123.txt 100% 7 7.6KB/s 00:00
sftp> exit
3.5 从本地上传文件到服务器
[root@sha opt]# sftp root@192.168.100.55
root@192.168.100.55's password:
Connected to 192.168.100.55.
sftp> put 456.txt
stat 456.txt: No such file or directory
sftp> put 789.txt
Uploading 789.txt to /root/789.txt
789.txt 100% 7 7.5KB/s 00:00
sftp>
切换到服务器查看
[root@ shanan ~]# ls
789.txt anaconda-ks.cfg
[root@ shanan ~]# cat 789.txt
123455
[root@ shanan ~]#
四 . 其他参数的含义
[root@ shanan centos7]# vi /etc/ssh/sshd_config
Port 22 //端口号
#AddressFamily any
#ListenAddress 0.0.0.0 //监听端口 IPV4
#ListenAddress :: //监听端口IPV6
HostKey /etc/ssh/ssh_host_rsa_key 非对称秘钥
#HostKey /etc/ssh/ssh_host_dsa_key
HostKey /etc/ssh/ssh_host_ecdsa_key 椭圆曲线秘钥
HostKey /etc/ssh/ssh_host_ed25519_key
# Ciphers and keying
#RekeyLimit default none
# Logging
#SyslogFacility AUTH
SyslogFacility AUTHPRIV
#LogLevel INFO
# Authentication:
#LoginGraceTime 2m // 会话时间2分钟,远程一定要设置
#PermitRootLogin yes // 允许ROOT用户登录(慎用)
#StrictModes yes // 权限验证
MaxAuthTries 6 //最大的验证尝试次数,一般客户端默认3次
#MaxSessions 10 // 允许10个不同的终端去连接
PubkeyAuthentication yes //允许公钥访问
# The default is to check both .ssh/authorized_keys and .ssh/authorized_keys2
# but this is overridden so installations will only check .ssh/authorized_keys
AuthorizedKeysFile .ssh/authorized_keys //密码对生成位置
#AuthorizedPrincipalsFile none
#AuthorizedKeysCommand none
#AuthorizedKeysCommandUser nobody
# For this to work you will also need host keys in /etc/ssh/ssh_known_hosts
#HostbasedAuthentication no
# Change to yes if you don't trust ~/.ssh/known_hosts for
# HostbasedAuthentication
#IgnoreUserKnownHosts no
# Don't read the user's ~/.rhosts and ~/.shosts files
#IgnoreRhosts yes
# To disable tunneled clear text passwords, change to no here!
#PasswordAuthentication yes
#PermitEmptyPasswords no
PasswordAuthentication yes
# Change to no to disable s/key passwords
#ChallengeResponseAuthentication yes
ChallengeResponseAuthentication no
# Kerberos options
#KerberosAuthentication no
#KerberosOrLocalPasswd yes
#KerberosTicketCleanup yes
#KerberosGetAFSToken no
#KerberosUseKuserok yes
# GSSAPI options
GSSAPIAuthentication yes
GSSAPICleanupCredentials no
#GSSAPIStrictAcceptorCheck yes
#GSSAPIKeyExchange no
#GSSAPIEnablek5users no
# Set this to 'yes' to enable PAM authentication, account processing,
# and session processing. If this is enabled, PAM authentication will
# be allowed through the ChallengeResponseAuthentication and
# PasswordAuthentication. Depending on your PAM configuration,
# PAM authentication via ChallengeResponseAuthentication may bypass
# the setting of "PermitRootLogin without-password".
# If you just want the PAM account and session checks to run without
# PAM authentication, then enable this but set PasswordAuthentication
# and ChallengeResponseAuthentication to 'no'.
# WARNING: 'UsePAM no' is not supported in Red Hat Enterprise Linux and may cause several
# problems.
UsePAM yes
#AllowAgentForwarding yes
#AllowTcpForwarding yes
#GatewayPorts no
X11Forwarding yes
#X11DisplayOffset 10
#X11UseLocalhost yes
#PermitTTY yes
#PrintMotd yes
#PrintLastLog yes
#TCPKeepAlive yes
#UseLogin no
109 #UsePrivilegeSeparation sandbox
110 #PermitUserEnvironment no
111 #Compression delayed
112 #ClientAliveInterval 0
113 #ClientAliveCountMax 3
114 #ShowPatchLevel no
115 UseDNS no
116 #PidFile /var/run/sshd.pid
117 #MaxStartups 10:30:100
118 #PermitTunnel no
119 #ChrootDirectory none
120 #VersionAddendum none
121
122 # no default banner path
123 #Banner none
124
125 # Accept locale-related environment variables
126 AcceptEnv LANG LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE LC_MONETARY LC_MESSAGES
127 AcceptEnv LC_PAPER LC_NAME LC_ADDRESS LC_TELEPHONE LC_MEASUREMENT
128 AcceptEnv LC_IDENTIFICATION LC_ALL LANGUAGE
129 AcceptEnv XMODIFIERS
130
131 # override default of no subsystems
132 Subsystem sftp /usr/libexec/openssh/sftp-server
133
134 # Example of overriding settings on a per-user basis
135 #Match User anoncvs
136 # X11Forwarding no
137 # AllowTcpForwarding no
138 # PermitTTY no
139 AllowUsers test2@192.168.100.48 test3 root //白名单
DenyUsers //黑名单
140 # ForceCommand cvs server