IPSec穿越NAT
IPSec ×××有两种封装格式,一种是AH,一种是ESP,AH由于包含对数据包源目IP进行完整性校验,Nat是绝对不能部署的,否则,目的端在收到数据包由于完整性校验失败,而丢弃该数据包,而ESP可以部署Nat,却不能部署PAT,因为该数据包没有传输层报头,无法进行端口转化,而导致数据包被丢弃,Cisco 开发了一种Nat-traver(nat穿越)技术,用来解决这样的问题,通过在IKE phase1阶段协商的数据包中有个VID字段,用来表明该路由器是否支持Nat-traver,而在3,4个数据包通过交换NAT-D(一种由源IP和源端口或者由目的IP和目的端口号的Hash值),通过交换比较知道是否进行了Nat-traverse,从而在后续的数据包以后都会在IP包头后添加一个UDP/4500的报头,来实现PAT,以下是部署的配置实例!
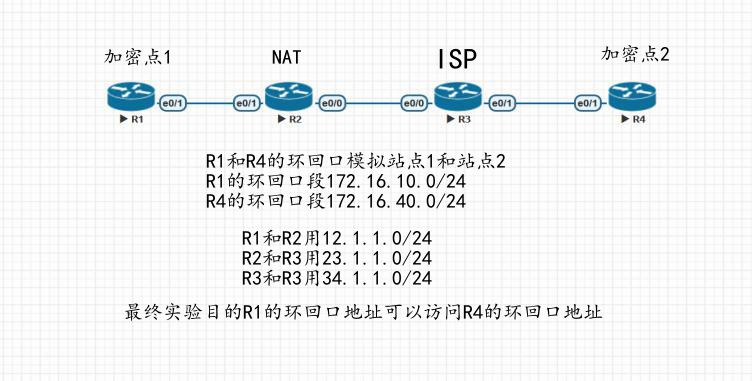
拓扑图
R1配置
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key nat address 34.1.1.4
ip access-list extended ipsec
permit ip 172.16.10.0 0.0.0.255 172.16.40.0 0.0.0.255
crypto ipsec transform-set ipsec esp-3des esp-md5-hmac
mode tunnel
crypto map ipsec 10 ipsec-isakmp
set peer 34.1.1.4
set transform-set ipsec
match address ipsec
interface Loopback0
ip address 172.16.10.1 255.255.255.0
interface Ethernet0/1
ip address 12.1.1.1 255.255.255.0
crypto map ipsec
ip route 0.0.0.0 0.0.0.0 12.1.1.2
R2
interface Ethernet0/0
ip address 23.1.1.2 255.255.255.0
ip nat outside
ip virtual-reassembly in
!
interface Ethernet0/1
ip address 12.1.1.2 255.255.255.0
ip nat inside
ip virtual-reassembly in
ip nat inside source list 1 interface Ethernet0/0 overload
access-list 1 permit any
ip route 0.0.0.0 0.0.0.0 23.1.1.3
ip route 172.16.10.0 255.255.255.0 12.1.1.1
R3
interface Ethernet0/0
ip address 23.1.1.3 255.255.255.0
!
interface Ethernet0/1
ip address 34.1.1.3 255.255.255.0
R4
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key nat address 23.1.1.2 #是与NAT设备建立连接
crypto ipsec transform-set ipsec esp-3des esp-md5-hmac
mode tunnel
ip access-list extended ipsec
permit ip 172.16.40.0 0.0.0.255 172.16.10.0 0.0.0.255
crypto map ipsec 10 ipsec-isakmp
set peer 23.1.1.2
set transform-set ipsec
match address ipsec
interface Loopback0
ip address 172.16.40.1 255.255.255.0
interface Ethernet0/1
ip address 34.1.1.4 255.255.255.0
crypto map ipsec
ip route 0.0.0.0 0.0.0.0 34.1.1.3
在R1设备上查看ipsec配置
R1#show crypto session
Crypto session current status
Interface: Ethernet0/1
Session status: UP-ACTIVE
Peer: 34.1.1.4 port 4500
IKEv1 SA: local 12.1.1.1/4500 remote 34.1.1.4/4500 Active
IPSEC FLOW: permit ip 172.16.10.0/255.255.255.0 172.16.40.0/255.255.255.0
Active SAs: 2, origin: crypto map
R1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
34.1.1.4 12.1.1.1 QM_IDLE 1001 ACTIVE
在R2设备上查看nat转换
R2#show ip nat translations
Pro Inside global Inside local Outside local Outside global
udp 23.1.1.2:4500 12.1.1.1:4500 34.1.1.4:4500 34.1.1.4:4500
可以看到是重新封装的UDP4500端口
在R1进行测试,完成实验
R1#ping 172.16.40.1 source l0 repeat 10
Type escape sequence to abort.
Sending 10, 100-byte ICMP Echos to 172.16.40.1, timeout is 2 seconds:
Packet sent with a source address of 172.16.10.1
!!!!!!!!!!