http://www.securitysift.com/windows-exploit-development-part-6-seh-exploits/
SEH Example
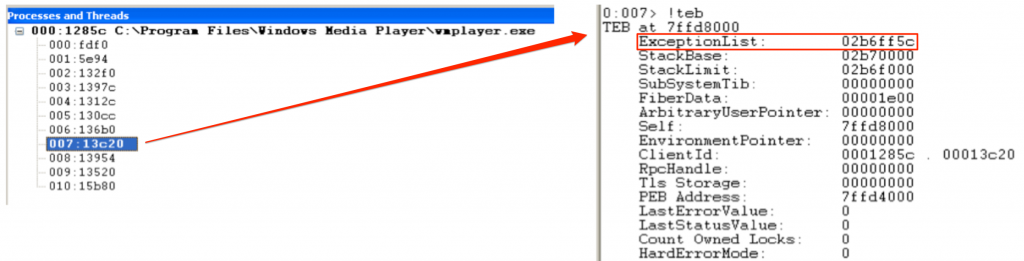
Let’s take a look at how SEH is implemented in practice, using Windows Media Player as an example. Recall from Part 1 of this exploit series that you can view the contents of the TEB using the !teb command in WinDbg. Here is a snapshot of the running process threads and a look at one of the associated TEBs for Windows Media Player (on a Win XP SP3 machine):
Notice the ExceptionList address. This is the address of the start of the SEH chain for that thread (yours may vary). In other words, this address points to the first _EXCEPTION_REGISTRATION_RECORD in the SEH chain. Let’s take a look at how to find this same information in Immunity Debugger.
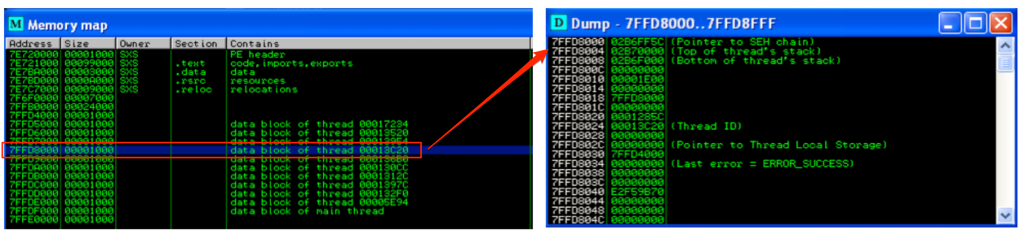
After attaching Windows Media Player to Immunity, you can hit Alt+M to view the Memory Modules. In this example, I’ll double-click the same thread examined in WinDbg (00013C20).
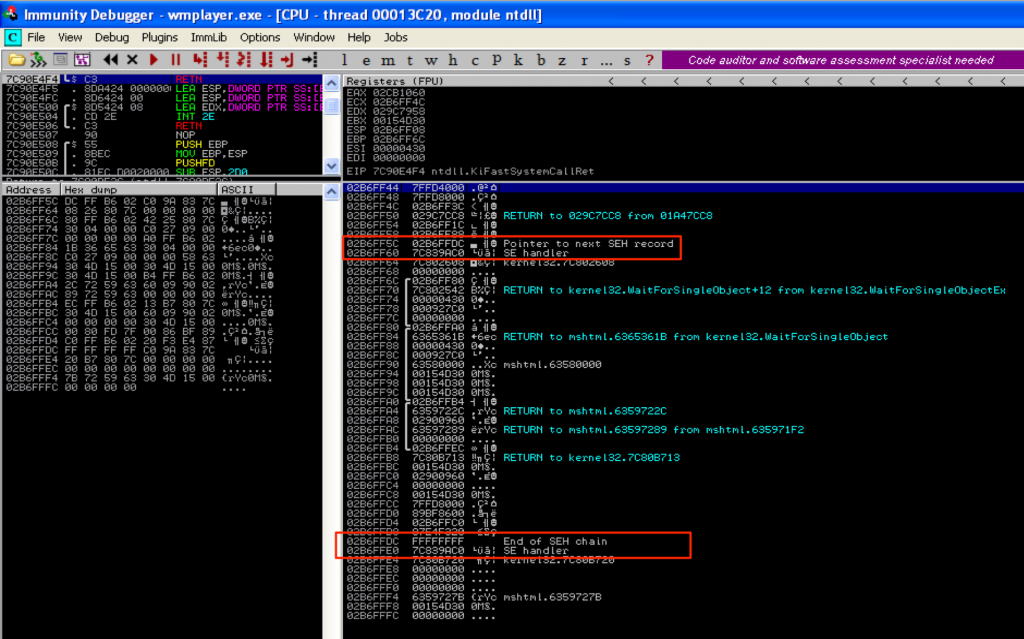
This opens up the Dump window for that thread, which you’ll notice is the TEB. Just as in WinDbg, you’ll see that the start of the SEH chain is located at 02B6FF5C.
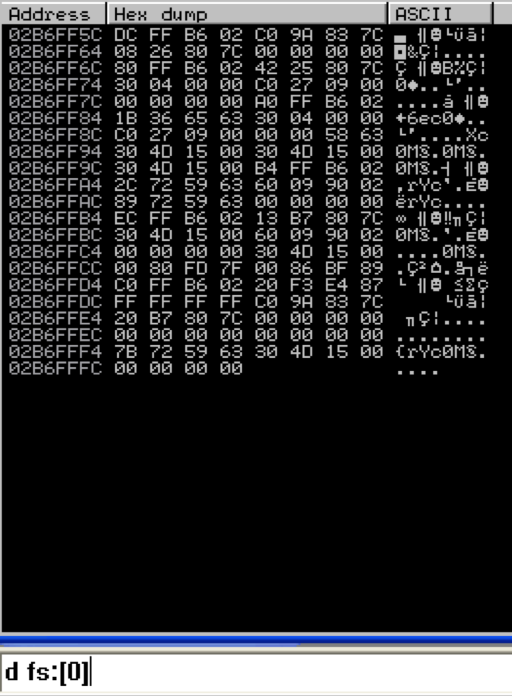
Another way to find the start of the SEH chain for the current thread is by dumping FS:[0] as follows:
Again, notice the first address is 02B6FF5C which in turn, points to 02B6FFDC (the start of the SEH chain).
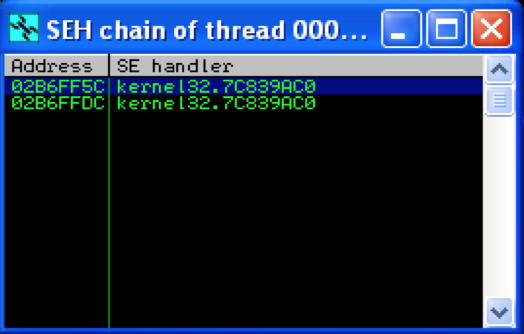
The final, and easiest method of viewing the SEH chain in Immunity is by hitting Alt+S:
No surprise, the first entry in the chain is 02B6FF5C. What this SEH chain window also clearly shows is that there are two _EXCEPTION_REGISTRATION_RECORDs for this thread (SEH chain length = 2) and they both point to the same exception handler function.
If you take a look at the stack for this thread (towards the bottom), you’ll be able to see this SEH chain, starting at 02B6FF5C.
Again, you can see both registration records in the SEH chain — the first is the start of the chain located at 02B6FF5C and the second is the default handler (as indicated by FFFFFFFF / “End of SEH Chain“) at 02B6FFDC.
Exploiting SEH
Now that you have an idea of how Windows SEH works and how to locate the SEH chain in Immunity, let’s see how it can be abused to craft reliable exploits. For this example, I’m going to use the basic C program example from Part 1 of this exploit series (original source: Wikipedia).
For demo purposes I’ve compiled it using MS Visual Studio Command Line with the /Zi switch (for debugging) and /GS- switch (to remove stack cookie protection). Running the program with an argument of 10 A’s (stack_demo.exe AAAAAAAAAA) you can see that by default there are two entries in the SEH chain (neither of which are explicitly defined in the application code itself).