老样子先检查一下
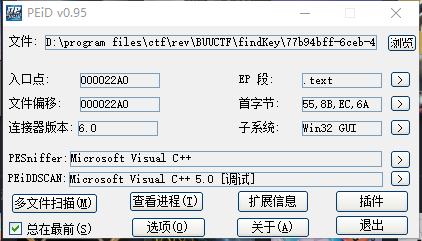
然后打开一下程序看看
没什么别的就几个菜单在待着,所以打开ida静态分析
这里面的自定义函数就不一一说了(自己看一下吧),跟你要的flag没有关系,还记得先前打开程序的时候的标题吗?叫find flag说明flag需要自己去找
按shirt+f12查看字符串

从flag开始到cjjb的这些字符串都很可疑
点进去,并且用交叉引用,在为其f5反编译的时候,会发现sp指针错误,所以说有东西在搞鬼,先前我写的题目里就认识到了花指令,虽然这次没意识到,但还是通过查阅资料找到了出现这种情况的原因。
但我也不知道要修改啥(自己的知识还有很多不足,这里是花指令看得少了),所以去看了看wphttps://www.dongzt.cn/archives/2019%E5%B9%B43%E6%9C%88%E5%AE%89%E6%81%92%E5%B9%B3%E5%8F%B0%E5%91%A8%E5%91%A8%E7%BB%83%E7%9A%84%E5%81%9A%E9%A2%98%E6%80%9D%E8%B7%AF%E5%88%86%E4%BA%AB.html#0x02findkey这位大佬写的,然后发现了有两个一样的指令,还连在一起,把它去一个就行了
然后f5反编译,如下所示
LRESULT __stdcall sub_401640(HWND hWndParent, UINT Msg, WPARAM wParam, LPARAM lParam) { int v5; // eax size_t v6; // eax DWORD v7; // eax int v8; // eax int v9; // eax const char *v10; // [esp-4h] [ebp-450h] CHAR *v11; // [esp+0h] [ebp-44Ch] int v12; // [esp+4h] [ebp-448h] int v13; // [esp+4Ch] [ebp-400h] UINT v14; // [esp+50h] [ebp-3FCh] CHAR v15; // [esp+54h] [ebp-3F8h] CHAR v16[2]; // [esp+154h] [ebp-2F8h] int v17; // [esp+157h] [ebp-2F5h] __int16 v18; // [esp+15Bh] [ebp-2F1h] char v19; // [esp+15Dh] [ebp-2EFh] char v20; // [esp+160h] [ebp-2ECh] char v21; // [esp+181h] [ebp-2CBh] __int16 v22; // [esp+25Dh] [ebp-1EFh] char v23; // [esp+25Fh] [ebp-1EDh] CHAR v24; // [esp+260h] [ebp-1ECh] CHAR String[4]; // [esp+360h] [ebp-ECh] int v26; // [esp+364h] [ebp-E8h] __int16 v27; // [esp+368h] [ebp-E4h] CHAR Text; // [esp+36Ch] [ebp-E0h] struct tagRECT Rect; // [esp+38Ch] [ebp-C0h] CHAR Buffer; // [esp+39Ch] [ebp-B0h] HDC hdc; // [esp+400h] [ebp-4Ch] struct tagPAINTSTRUCT Paint; // [esp+404h] [ebp-48h] WPARAM v33; // [esp+444h] [ebp-8h] int v34; // [esp+448h] [ebp-4h] LoadStringA(hInstance, 0x6Au, &Buffer, 100); v14 = Msg; if ( Msg > 0x111 ) { if ( v14 == 517 ) { if ( strlen((const char *)&pbData) > 6 ) ExitProcess(0); if ( strlen((const char *)&pbData) ) { memset(&v24, 0, 0x100u); v6 = strlen((const char *)&pbData); memcpy(&v24, &pbData, v6); v10 = (const char *)&pbData; do { v7 = strlen(v10); sub_40101E(&pbData, v7, v11); } while ( &v12 && !&v12 ); strcpy(&v20, "0kk`d1a`55k222k2a776jbfgd`06cjjb"); memset(&v21, 0, 0xDCu); v22 = 0; v23 = 0; strcpy(v16, "SS"); v17 = 0; v18 = 0; v19 = 0; v8 = strlen(&v20); sub_401005(v16, (int)&v20, v8); if ( _strcmpi((const char *)&pbData, &v20) ) { SetWindowTextA(hWndParent, "flag{}"); MessageBoxA(hWndParent, "Are you kidding me?", "^_^", 0); ExitProcess(0); } memcpy(&v15, &unk_423030, 0x32u); v9 = strlen(&v15); sub_401005(&v24, (int)&v15, v9); MessageBoxA(hWndParent, &v15, 0, 0x32u); } ++dword_428D54; } else { if ( v14 != 520 ) return DefWindowProcA(hWndParent, Msg, wParam, lParam); if ( dword_428D54 == 16 ) { strcpy(String, "ctf"); v26 = 0; v27 = 0; SetWindowTextA(hWndParent, String); strcpy(&Text, "Are you kidding me?"); MessageBoxA(hWndParent, &Text, &Buffer, 0); } ++dword_428D54; } } else { switch ( v14 ) { case 0x111u: v34 = (unsigned __int16)wParam; v33 = wParam >> 16; v13 = (unsigned __int16)wParam; if ( (unsigned __int16)wParam == 104 ) { DialogBoxParamA(hInstance, (LPCSTR)0x67, hWndParent, (DLGPROC)DialogFunc, 0); } else { if ( v13 != 105 ) return DefWindowProcA(hWndParent, Msg, wParam, lParam); DestroyWindow(hWndParent); } break; case 2u: PostQuitMessage(0); break; case 0xFu: hdc = BeginPaint(hWndParent, &Paint); GetClientRect(hWndParent, &Rect); v5 = strlen(&Buffer); DrawTextA(hdc, &Buffer, v5, &Rect, 1u); EndPaint(hWndParent, &Paint); break; default: return DefWindowProcA(hWndParent, Msg, wParam, lParam); } } return 0; }
找到先前我们怀疑的字符串位置

发现cmp类的函数,sub_401005函数经过分析后,只是一个异或,然后得出来的字符串c8837b23ff8aaa8a2dde915473ce0991是md5加密

然后在进行一次异或得到答案
