目的:通过frida hook native方法,获取到对应方法的参数:
c++ 代码:
extern "C" JNIEXPORT jstring JNICALL Java_os_sdk_fridademo_MainActivity_stringFromJNI( JNIEnv *env, jobject /* this */) { std::string hello = "Hello from C++"; const char* key = "king"; jsb_set_key(key); return env->NewStringUTF(hello.c_str()); }
编译完成之后,运行到设备,我这里用的是蓝叠虚拟机:
在ida中打开对应的so库,找到导出的方法名称,
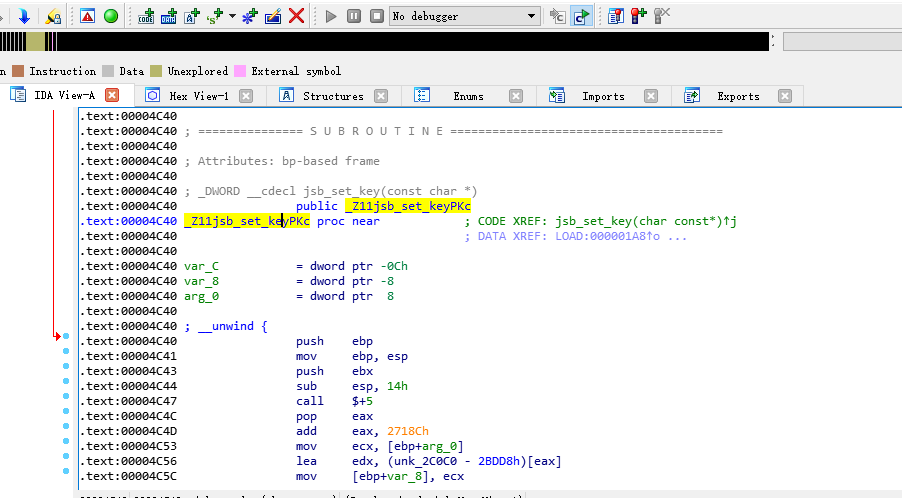
编写frida js脚本:frida_native.js
将找到的方法名称放入到下面的红色部分:
setImmediate(function() { Interceptor.attach(Module.findExportByName("libnative-lib.so","_Z11jsb_set_keyPKc"),{ onEnter:function(args){ send("open called! args[0]",Memory.readByteArray(args[0],256)); }, onLeave:function(retval){ } }) });
编写对应的python脚本:load_native.py
import frida,sys,time def on_msg(msg,data): print(msg) print(data) device = frida.get_device("emulator-5554") # pid = device.spawn(["packageName"]) # device.resume(pid) time.sleep(1) session = device.attach("packageName") with open("frida_native.js") as f: script = session.create_script(f.read()) script.on("message",on_msg) script.load() sys.stdin.read()
运行后
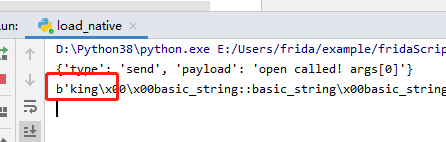
轻松搞定。
安利一波入门教程:
Android Application Security Study:https://github.com/r0ysue/AndroidSecurityStudy