关于OpenVPN的有关介绍及为何使用OpenVPN在此就不做赘述了,下面直接记录Centos7.2系统下部署OpenVPN环境的操作过程:
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
|
1) 先将本机的yum换成阿里云的yum源
[root@
test
-vm04 ~]
# wget -O /etc/yum.repos.d/CentOS-Base.repo http://mirrors.aliyun.com/repo/Centos-7.repo
[root@
test
-vm04 ~]
# yum clean all
[root@
test
-vm04 ~]
# yum makecache
-----------------------------------------------------------------------------------------------------------
如果是centos5,则更换如下:
wget -O
/etc/yum
.repos.d
/CentOS-Base
.repo http:
//mirrors
.aliyun.com
/repo/Centos-5
.repo
如果时centos6,则更换如下:
wget -O
/etc/yum
.repos.d
/CentOS-Base
.repo http:
//mirrors
.aliyun.com
/repo/Centos-6
.rep
-----------------------------------------------------------------------------------------------------------
2)安装依赖的软件包
[root@
test
-vm04 ~]
# yum install -y lzo lzo-devel openssl openssl-devel pam pam-devel
[root@
test
-vm04 ~]
# wget http://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm
[root@
test
-vm04 ~]
# rpm -ivh epel-release-latest-7.noarch.rpm
[root@
test
-vm04 ~]
# yum install -y pkcs11-helper pkcs11-helper-devel
确认已经安装完成:
[root@
test
-vm04 ~]
# rpm -qa lzo lzo-devel openssl openssl-devel pam pam-devel pkcs11-helper pkcs11-helper-devel
pam-devel-1.1.8-18.el7.x86_64
pkcs11-helper-devel-1.11-3.el7.x86_64
pam-1.1.8-18.el7.x86_64
pkcs11-helper-1.11-3.el7.x86_64
lzo-devel-2.06-8.el7.x86_64
openssl-1.0.2k-8.el7.x86_64
lzo-2.06-8.el7.x86_64
openssl-devel-1.0.2k-8.el7.x86_64
3) 安装OpenVPN服务
下载openvpn的源码包
[root@
test
-vm04 ~]
# wget http://oss.aliyuncs.com/aliyunecs/openvpn-2.2.2.tar.gz
使用rpmbuild将源码包编译成rpm包来进行安装
[root@
test
-vm04 ~]
# rpmbuild -tb openvpn-2.2.2.tar.gz
执行上面这条命令以后就会正常开始编译了,编译完成以后会在
/root/rpmbuild/RPMS/x86_64
目录下生成 openvpn-2.2.2-1.x86_64.rpm 安装包。
[root@
test
-vm04 ~]
# ls /root/rpmbuild/RPMS/x86_64/
openvpn-2.2.2-1.x86_64.rpm
执行rpm -ivh openvpn-2.2.2-1.x86_64.rpm 以rpm包的方式安装:
[root@
test
-vm04 ~]
# rpm -ivh /root/rpmbuild/RPMS/x86_64/openvpn-2.2.2-1.x86_64.rpm
Preparing...
################################# [100%]
Updating / installing...
1:openvpn-2.2.2-1
################################# [100%]
Restarting openvpn (via systemctl): [ OK ]
4)配置OpenVPN服务(服务端)
初始化PKI
[root@
test
-vm04 ~]
# cd /usr/share/doc/openvpn-2.2.2/easy-rsa/2.0
进入到
/usr/share/doc/openvpn-2
.2.2
/easy-rsa/2
.0 目录下,找到 vars 证书环境文件,修改以下几行
export
定义的参数值
[root@
test
-vm04 2.0]
# vim vars
......
export
KEY_COUNTRY=
"CN"
//
所在的国家
export
KEY_PROVINCE=
"BJ"
//
所在的省份
export
KEY_CITY=
"BEIJING"
//
所在的城市
export
KEY_ORG=
"HUANQIU"
//
所在的组织
上述参数的值可以自定义设置,对配置无影响。
生成服务端的证书
清除并删除keys目录下的所有key
[root@
test
-vm04 2.0]
# ln -s openssl-1.0.0.cnf openssl.cnf
[root@
test
-vm04 2.0]
# ll openssl*
-rwxr-xr-x. 1 root root 7768 Oct 21 2010 openssl-0.9.6.cnf
-rwxr-xr-x. 1 root root 8325 Nov 24 2011 openssl-0.9.8.cnf
-rwxr-xr-x. 1 root root 8222 Nov 24 2011 openssl-1.0.0.cnf
lrwxrwxrwx. 1 root root 17 Sep 21 05:19 openssl.cnf -> openssl-1.0.0.cnf
[root@
test
-vm04 2.0]
# source ./vars
NOTE: If you run .
/clean-all
, I will be doing a
rm
-rf on
/usr/share/doc/openvpn-2
.2.2
/easy-rsa/2
.0
/keys
[root@
test
-vm04 2.0]
# ./clean-all
生成CA证书,刚刚上面已经在vars文件中配置了默认参数值,多次回车完成就可以:
[root@
test
-vm04 2.0]
# ./build-ca
Generating a 1024 bit RSA private key
.....++++++
...................................++++++
writing new private key to
'ca.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter
'.'
, the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [BJ]:
Locality Name (eg, city) [BEIJING]:
Organization Name (eg, company) [HUANQIU]:
Organizational Unit Name (eg, section) [changeme]:
Common Name (eg, your name or your server's
hostname
) [changeme]:
Name [changeme]:
Email Address [[email protected]]:
生成服务器证书
如下huanqiuvpn是自定义的名字,一直回车,到最后会有两次交互,输入y确认,完成后会在keys目录下保存了huanqiuvpn.key、huanqiuvpn.csrl和huanqiuvpn.crt 三个文件。
[root@
test
-vm04 2.0]
# ./build-key-server huanqiuvpn
Generating a 1024 bit RSA private key
........................................++++++
......++++++
writing new private key to
'huanqiuvpn.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter
'.'
, the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [BJ]:
Locality Name (eg, city) [BEIJING]:
Organization Name (eg, company) [HUANQIU]:
Organizational Unit Name (eg, section) [changeme]:
Common Name (eg, your name or your server's
hostname
) [huanqiuvpn]:
Name [changeme]:
Email Address [[email protected]]:
Please enter the following
'extra'
attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Using configuration from
/usr/share/doc/openvpn-2
.2.2
/easy-rsa/2
.0
/openssl-1
.0.0.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:
'CN'
stateOrProvinceName :PRINTABLE:
'BJ'
localityName :PRINTABLE:
'BEIJING'
organizationName :PRINTABLE:
'HUANQIU'
organizationalUnitName:PRINTABLE:
'changeme'
commonName :PRINTABLE:
'huanqiuvpn'
name :PRINTABLE:
'changeme'
emailAddress :IA5STRING:
'[email protected]'
Certificate is to be certified
until
Sep 19 09:52:18 2027 GMT (3650 days)
Sign the certificate? [y
/n
]:y
1 out of 1 certificate requests certified, commit? [y
/n
]y
Write out database with 1 new entries
Data Base Updated
[root@
test
-vm04 2.0]
# ls keys/
01.pem 02.pem 03.pem ca.crt ca.key huanqiuvpn.crt huanqiuvpn.csr huanqiuvpn.key index.txt index.txt.attr index.txt.attr.old index.txt.old serial serial.old
创建vpn登陆用户的秘钥与证书
如下,创建用户名为kevin的秘钥和证书,一直回车,到最后会有两次确认,只要按y确认即可。完成后,在keys目录下生成1024位RSA服务器密钥kevin.key、kevin.crt和kevin.csr 三个文件。
[root@
test
-vm04 2.0]
# ./build-key kevin
Generating a 1024 bit RSA private key
...................++++++
.........++++++
writing new private key to
'kevin.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter
'.'
, the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [BJ]:
Locality Name (eg, city) [BEIJING]:
Organization Name (eg, company) [HUANQIU]:
Organizational Unit Name (eg, section) [changeme]:
Common Name (eg, your name or your server's
hostname
) [kevin]:
Name [changeme]:
Email Address [[email protected]]:
Please enter the following
'extra'
attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Using configuration from
/usr/share/doc/openvpn-2
.2.2
/easy-rsa/2
.0
/openssl-1
.0.0.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:
'CN'
stateOrProvinceName :PRINTABLE:
'BJ'
localityName :PRINTABLE:
'BEIJING'
organizationName :PRINTABLE:
'HUANQIU'
organizationalUnitName:PRINTABLE:
'changeme'
commonName :PRINTABLE:
'kevin'
name :PRINTABLE:
'changeme'
emailAddress :IA5STRING:
'[email protected]'
Certificate is to be certified
until
Sep 19 10:00:46 2027 GMT (3650 days)
Sign the certificate? [y
/n
]:y
1 out of 1 certificate requests certified, commit? [y
/n
]
CERTIFICATION CANCELED
[root@
test
-vm04 2.0]
# ls keys/
01.pem ca.crt ca.key huanqiuvpn.crt huanqiuvpn.csr huanqiuvpn.key index.txt index.txt.attr index.txt.old kevin.crt kevin.csr kevin.key serial serial.old
------------------------------------------------------------------------------------------------------------------------------------------------
如果创建用户证书时报错,可以将keys整个目录删除,然后从
source
.
/vars
这一步开始重新操作(慎重,否则之前在keys目录里的用户数据就会都删除)
------------------------------------------------------------------------------------------------------------------------------------------------
生成Diffie Hellman参数
[root@
test
-vm04 2.0]
# ./build-dh
Generating DH parameters, 1024 bit long safe prime, generator 2
This is going to take a long
time
.....+..............+..+..............................................................................+...................................................................................................+............................+................+............+..+...................+..............+........................................................................+............................................+.......................................................................................................................................+.....................................................+............+.......................+.......................................+............................................................................................................................................++*++*++*
执行了.
/build-dh
后,会在 keys 目录下生成 dh 参数文件 dh1024.pem。该文件客户端验证的时候会用到
[root@
test
-vm04 2.0]
# ls keys
01.pem ca.crt ca.key dh1024.pem huanqiuvpn.crt huanqiuvpn.csr huanqiuvpn.key index.txt index.txt.attr index.txt.old kevin.crt kevin.csr kevin.key serial serial.old
将
/usr/share/doc/openvpn-2
.2.2
/easy-rsa/2
.0
/keys
目录下的所有文件复制到
/etc/openvpn
下:
[root@
test
-vm04 2.0]
# cp -a /usr/share/doc/openvpn-2.2.2/easy-rsa/2.0/keys/* /etc/openvpn/
复制openvpn服务端配置文件 server.conf 到
/etc/openvpn/
目录下:
[root@
test
-vm04 2.0]
# cp -a /usr/share/doc/openvpn-2.2.2/sample-config-files/server.conf /etc/openvpn/
server.conf文件的配置
[root@
test
-vm04 2.0]
# egrep -v "^$|^#|^;" /etc/openvpn/server.conf
local
111.94.149.74
//
监听地址(内网或外网地址),最好填写openvpn服务器的公网IP地址(使用
"curl ifconfig.me"
命令查看)。或者这一行直接注释掉!(我在线上配置的就是注释这行)
port 1194
proto udp
dev tun
ca ca.crt
//CA
证书路径
cert huanqiuvpn.crt
//
此处crt以及下一行的key,请填写生成服务器端证书时用户自定义的名称
key huanqiuvpn.key
dh dh1024.pem
//
秘钥交换协议文件
server 10.8.0.0 255.255.255.0
//
给vpn客户机分配的地址池。最好别和openvpn部署机的内网ip在一个网段内
ifconfig
-pool-persist ipp.txt
push
"route 10.0.0.0 255.0.0.0"
client-to-client
keepalive 10 120
comp-lzo
user nobody
group nobody
persist-key
persist-tun
status openvpn-status.log
log openvpn.log
verb 3
5)设置iptables
先设置转发
[root@
test
-vm04 2.0]
# vim /etc/sysctl.conf
net.ipv4.ip_forward = 1
[root@
test
-vm04 2.0]
# sysctl -p //使内核参数生效
添加iptables规则,确保服务器可以转发数据包到外网:
[root@
test
-vm04 2.0]
# iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -j MASQUERADE
[root@
test
-vm04 2.0]
# service iptables save
[root@
test
-vm04 2.0]
# iptables -t nat -L
Chain PREROUTING (policy ACCEPT)
target prot opt
source
destination
Chain INPUT (policy ACCEPT)
target prot opt
source
destination
Chain OUTPUT (policy ACCEPT)
target prot opt
source
destination
Chain POSTROUTING (policy ACCEPT)
target prot opt
source
destination
MASQUERADE all -- localhost
/24
anywhere
6)启动OpenVPN
[root@
test
-vm04 2.0]
# /etc/init.d/openvpn start
Starting openvpn (via systemctl): [ OK ]
[root@
test
-vm04 2.0]
# lsof -i:1194
COMMAND PID USER FD TYPE DEVICE SIZE
/OFF
NODE NAME
openvpn 8547 nobody 5u IPv4 53264 0t0 UDP localhost:openvpn
如果1194端口启动不起来,可以通过查看
/etc/openvpn/openvpn
.log日志进行原因排查
-------------------------------------------------------------------------------------------------------------------------------
后续给同事开vpn账号,只需要下面几步(比如给zhangqiang同事开vpn)
[root@
test
-vm04 2.0]
# pwd
/usr/share/doc/openvpn-2
.2.2
/easy-rsa/2
.0
[root@
test
-vm04 2.0]
# ./build-key zhangqiang
[root@
test
-vm04 2.0]
# cp -a /usr/share/doc/openvpn-2.2.2/easy-rsa/2.0/keys/zhangqiang.* /etc/openvpn/
[root@
test
-vm04 2.0]
# /etc/init.d/openvpn restart
[root@
test
-vm04 2.0]
# lsof -i:1194
然后编写zhangqiang用户的config.ovpn客户端配置文件:
[root@
test
-vm04 2.0]
# vim /tmp/config.ovpn
client
dev tun
proto udp
remote 111.94.149.74 1194
//
注意这里的111.94.149.74是openvpn服务器端的外围ip。
resolv-retry infinite
nobind
mute-replay-warnings
ca ca.crt
cert zhangqiang.crt
key zhangqiang.key
comp-lzo
然后将ca.crt、config.ovpn、zhangqiang.crt、zhangqiang.csr、zhangqiang.key这五个文件放到zhagnqiang用户下
[root@
test
-vm04 2.0]
# mkdir /tmp/zhangqiang
[root@
test
-vm04 2.0]
# cd keys/
[root@
test
-vm04 keys]
# cp ca.crt /tmp/config.ovpn zhangqiang.crt zhangqiang.csr zhangqiang.key /tmp/zhangqiang
[root@
test
-vm04 keys]
# cd /tmp && tar -zvcf zhangqiang.tar.gz zhangqiang
然后将
/opt/zhangqiang
.
tar
.gz文件拷贝给用户zhangqiang,让他在客户机上进行openvpn的连接。
|
-----------------------------------------openvpn使用说明----------------------------------------
一、windows用户
1. 需要向管理员申请openvpn的配置及秘钥文件(总共包括5个文件:ca.crt证书、config.ovpn客户端配置文件、用户.crt、用户.csr、用户.key)。(其中,config.ovpn客户端文件是直接配置好拷贝给客户机的,这个文件在服务器端是不存在的,需要自己编写)
2. 软件安装包见文末
3. 如果你的电脑没有安装过TAP,安装过程中会有下面的提示,选择安装。
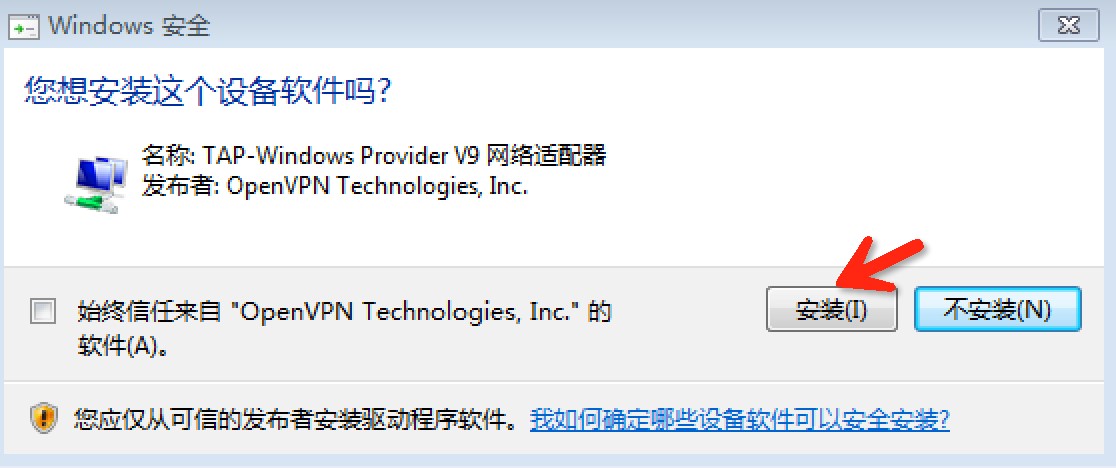
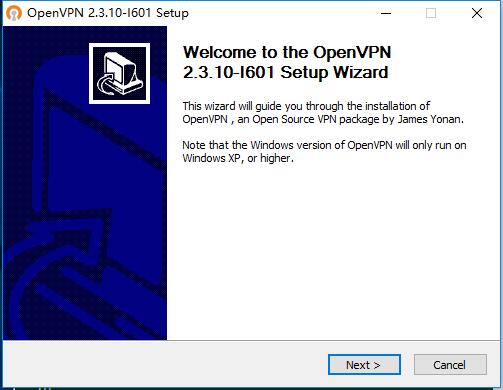

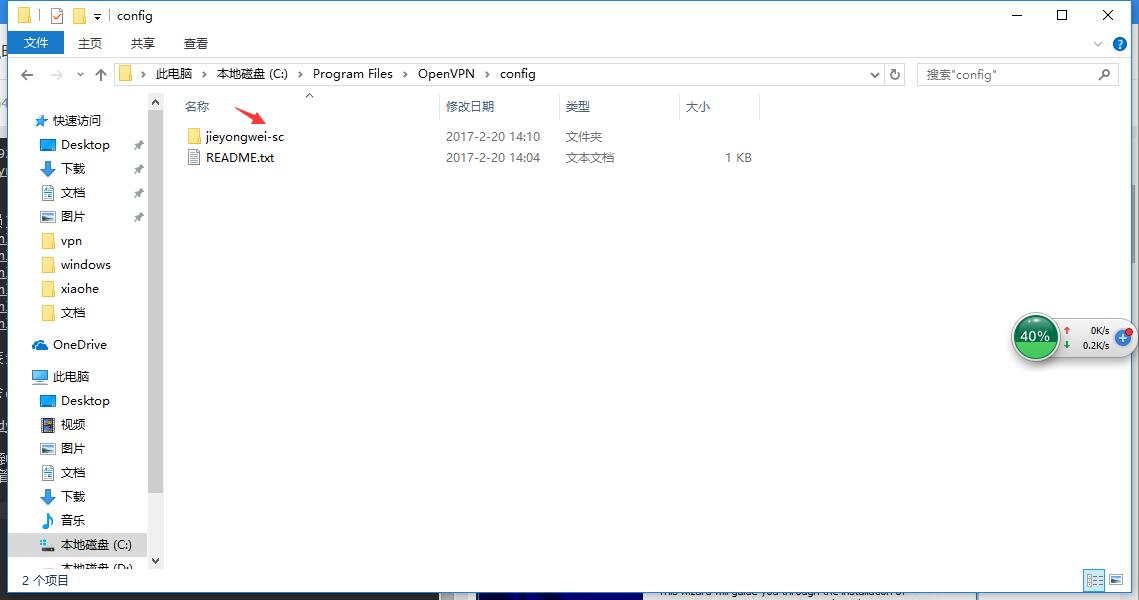
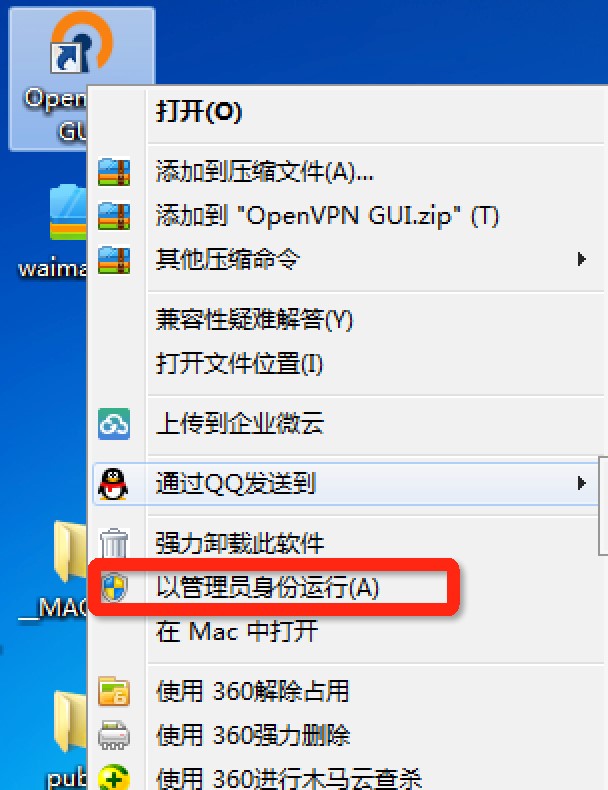
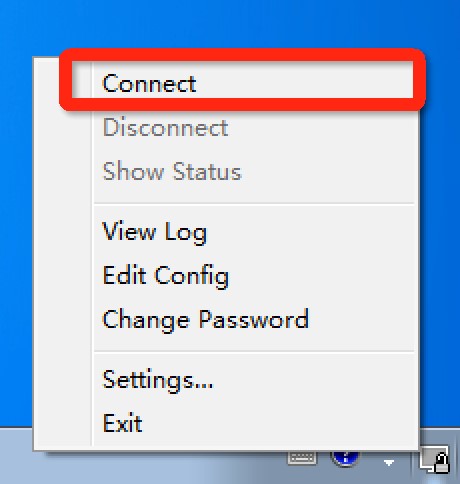

|
1
2
3
4
5
|
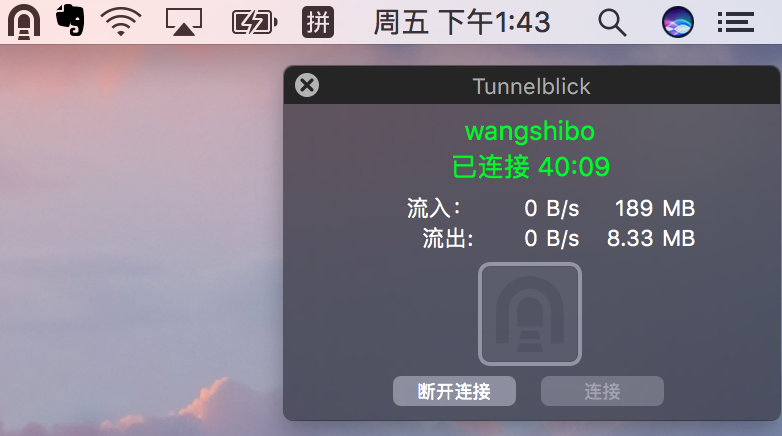
连接到openvpn后,查看本机分配的vpn地址:
localhost:
test
-vm kevin$
ifconfig
//
发现已经成功分配到上面定义的vpn地址范围内的地址了(10.8.0.10)
.......
utun1: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> mtu 1500
inet 10.8.0.10 --> 10.8.0.9 netmask 0xffffffff
|
|
1
2
3
4
5
6
7
8
9
10
11
|
client
dev tun
proto udp
remote 111.94.149.74 1194
resolv-retry infinite
nobind
mute-replay-warnings
ca ca.crt
cert wangshibo.crt
key wangshibo.key
comp-lzo
|
补充一下,下面的mac客户端是可用的,安装后会提示升级,升级后有可能会导致不能使用,没有特殊原因的话,就不用升级了,如果已经升级,删除后安装下面这个就行了.
mac 用户下载下面这个:https://pan.baidu.com/s/1sl3CnwT (提取密码:1j8g)
windows 用户下载下面这个:https://pan.baidu.com/s/1eS4E6Y2 (提取密码:fvkr)
关于OpenVPN的有关介绍及为何使用OpenVPN在此就不做赘述了,下面直接记录Centos7.2系统下部署OpenVPN环境的操作过程:
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
|
1) 先将本机的yum换成阿里云的yum源
[root@
test
-vm04 ~]
# wget -O /etc/yum.repos.d/CentOS-Base.repo http://mirrors.aliyun.com/repo/Centos-7.repo
[root@
test
-vm04 ~]
# yum clean all
[root@
test
-vm04 ~]
# yum makecache
-----------------------------------------------------------------------------------------------------------
如果是centos5,则更换如下:
wget -O
/etc/yum
.repos.d
/CentOS-Base
.repo http:
//mirrors
.aliyun.com
/repo/Centos-5
.repo
如果时centos6,则更换如下:
wget -O
/etc/yum
.repos.d
/CentOS-Base
.repo http:
//mirrors
.aliyun.com
/repo/Centos-6
.rep
-----------------------------------------------------------------------------------------------------------
2)安装依赖的软件包
[root@
test
-vm04 ~]
# yum install -y lzo lzo-devel openssl openssl-devel pam pam-devel
[root@
test
-vm04 ~]
# wget http://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm
[root@
test
-vm04 ~]
# rpm -ivh epel-release-latest-7.noarch.rpm
[root@
test
-vm04 ~]
# yum install -y pkcs11-helper pkcs11-helper-devel
确认已经安装完成:
[root@
test
-vm04 ~]
# rpm -qa lzo lzo-devel openssl openssl-devel pam pam-devel pkcs11-helper pkcs11-helper-devel
pam-devel-1.1.8-18.el7.x86_64
pkcs11-helper-devel-1.11-3.el7.x86_64
pam-1.1.8-18.el7.x86_64
pkcs11-helper-1.11-3.el7.x86_64
lzo-devel-2.06-8.el7.x86_64
openssl-1.0.2k-8.el7.x86_64
lzo-2.06-8.el7.x86_64
openssl-devel-1.0.2k-8.el7.x86_64
3) 安装OpenVPN服务
下载openvpn的源码包
[root@
test
-vm04 ~]
# wget http://oss.aliyuncs.com/aliyunecs/openvpn-2.2.2.tar.gz
使用rpmbuild将源码包编译成rpm包来进行安装
[root@
test
-vm04 ~]
# rpmbuild -tb openvpn-2.2.2.tar.gz
执行上面这条命令以后就会正常开始编译了,编译完成以后会在
/root/rpmbuild/RPMS/x86_64
目录下生成 openvpn-2.2.2-1.x86_64.rpm 安装包。
[root@
test
-vm04 ~]
# ls /root/rpmbuild/RPMS/x86_64/
openvpn-2.2.2-1.x86_64.rpm
执行rpm -ivh openvpn-2.2.2-1.x86_64.rpm 以rpm包的方式安装:
[root@
test
-vm04 ~]
# rpm -ivh /root/rpmbuild/RPMS/x86_64/openvpn-2.2.2-1.x86_64.rpm
Preparing...
################################# [100%]
Updating / installing...
1:openvpn-2.2.2-1
################################# [100%]
Restarting openvpn (via systemctl): [ OK ]
4)配置OpenVPN服务(服务端)
初始化PKI
[root@
test
-vm04 ~]
# cd /usr/share/doc/openvpn-2.2.2/easy-rsa/2.0
进入到
/usr/share/doc/openvpn-2
.2.2
/easy-rsa/2
.0 目录下,找到 vars 证书环境文件,修改以下几行
export
定义的参数值
[root@
test
-vm04 2.0]
# vim vars
......
export
KEY_COUNTRY=
"CN"
//
所在的国家
export
KEY_PROVINCE=
"BJ"
//
所在的省份
export
KEY_CITY=
"BEIJING"
//
所在的城市
export
KEY_ORG=
"HUANQIU"
//
所在的组织
上述参数的值可以自定义设置,对配置无影响。
生成服务端的证书
清除并删除keys目录下的所有key
[root@
test
-vm04 2.0]
# ln -s openssl-1.0.0.cnf openssl.cnf
[root@
test
-vm04 2.0]
# ll openssl*
-rwxr-xr-x. 1 root root 7768 Oct 21 2010 openssl-0.9.6.cnf
-rwxr-xr-x. 1 root root 8325 Nov 24 2011 openssl-0.9.8.cnf
-rwxr-xr-x. 1 root root 8222 Nov 24 2011 openssl-1.0.0.cnf
lrwxrwxrwx. 1 root root 17 Sep 21 05:19 openssl.cnf -> openssl-1.0.0.cnf
[root@
test
-vm04 2.0]
# source ./vars
NOTE: If you run .
/clean-all
, I will be doing a
rm
-rf on
/usr/share/doc/openvpn-2
.2.2
/easy-rsa/2
.0
/keys
[root@
test
-vm04 2.0]
# ./clean-all
生成CA证书,刚刚上面已经在vars文件中配置了默认参数值,多次回车完成就可以:
[root@
test
-vm04 2.0]
# ./build-ca
Generating a 1024 bit RSA private key
.....++++++
...................................++++++
writing new private key to
'ca.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter
'.'
, the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [BJ]:
Locality Name (eg, city) [BEIJING]:
Organization Name (eg, company) [HUANQIU]:
Organizational Unit Name (eg, section) [changeme]:
Common Name (eg, your name or your server's
hostname
) [changeme]:
Name [changeme]:
Email Address [[email protected]]:
生成服务器证书
如下huanqiuvpn是自定义的名字,一直回车,到最后会有两次交互,输入y确认,完成后会在keys目录下保存了huanqiuvpn.key、huanqiuvpn.csrl和huanqiuvpn.crt 三个文件。
[root@
test
-vm04 2.0]
# ./build-key-server huanqiuvpn
Generating a 1024 bit RSA private key
........................................++++++
......++++++
writing new private key to
'huanqiuvpn.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter
'.'
, the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [BJ]:
Locality Name (eg, city) [BEIJING]:
Organization Name (eg, company) [HUANQIU]:
Organizational Unit Name (eg, section) [changeme]:
Common Name (eg, your name or your server's
hostname
) [huanqiuvpn]:
Name [changeme]:
Email Address [[email protected]]:
Please enter the following
'extra'
attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Using configuration from
/usr/share/doc/openvpn-2
.2.2
/easy-rsa/2
.0
/openssl-1
.0.0.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:
'CN'
stateOrProvinceName :PRINTABLE:
'BJ'
localityName :PRINTABLE:
'BEIJING'
organizationName :PRINTABLE:
'HUANQIU'
organizationalUnitName:PRINTABLE:
'changeme'
commonName :PRINTABLE:
'huanqiuvpn'
name :PRINTABLE:
'changeme'
emailAddress :IA5STRING:
'[email protected]'
Certificate is to be certified
until
Sep 19 09:52:18 2027 GMT (3650 days)
Sign the certificate? [y
/n
]:y
1 out of 1 certificate requests certified, commit? [y
/n
]y
Write out database with 1 new entries
Data Base Updated
[root@
test
-vm04 2.0]
# ls keys/
01.pem 02.pem 03.pem ca.crt ca.key huanqiuvpn.crt huanqiuvpn.csr huanqiuvpn.key index.txt index.txt.attr index.txt.attr.old index.txt.old serial serial.old
创建vpn登陆用户的秘钥与证书
如下,创建用户名为kevin的秘钥和证书,一直回车,到最后会有两次确认,只要按y确认即可。完成后,在keys目录下生成1024位RSA服务器密钥kevin.key、kevin.crt和kevin.csr 三个文件。
[root@
test
-vm04 2.0]
# ./build-key kevin
Generating a 1024 bit RSA private key
...................++++++
.........++++++
writing new private key to
'kevin.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter
'.'
, the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [BJ]:
Locality Name (eg, city) [BEIJING]:
Organization Name (eg, company) [HUANQIU]:
Organizational Unit Name (eg, section) [changeme]:
Common Name (eg, your name or your server's
hostname
) [kevin]:
Name [changeme]:
Email Address [[email protected]]:
Please enter the following
'extra'
attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Using configuration from
/usr/share/doc/openvpn-2
.2.2
/easy-rsa/2
.0
/openssl-1
.0.0.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:
'CN'
stateOrProvinceName :PRINTABLE:
'BJ'
localityName :PRINTABLE:
'BEIJING'
organizationName :PRINTABLE:
'HUANQIU'
organizationalUnitName:PRINTABLE:
'changeme'
commonName :PRINTABLE:
'kevin'
name :PRINTABLE:
'changeme'
emailAddress :IA5STRING:
'[email protected]'
Certificate is to be certified
until
Sep 19 10:00:46 2027 GMT (3650 days)
Sign the certificate? [y
/n
]:y
1 out of 1 certificate requests certified, commit? [y
/n
]
CERTIFICATION CANCELED
[root@
test
-vm04 2.0]
# ls keys/
01.pem ca.crt ca.key huanqiuvpn.crt huanqiuvpn.csr huanqiuvpn.key index.txt index.txt.attr index.txt.old kevin.crt kevin.csr kevin.key serial serial.old
------------------------------------------------------------------------------------------------------------------------------------------------
如果创建用户证书时报错,可以将keys整个目录删除,然后从
source
.
/vars
这一步开始重新操作(慎重,否则之前在keys目录里的用户数据就会都删除)
------------------------------------------------------------------------------------------------------------------------------------------------
生成Diffie Hellman参数
[root@
test
-vm04 2.0]
# ./build-dh
Generating DH parameters, 1024 bit long safe prime, generator 2
This is going to take a long
time
.....+..............+..+..............................................................................+...................................................................................................+............................+................+............+..+...................+..............+........................................................................+............................................+.......................................................................................................................................+.....................................................+............+.......................+.......................................+............................................................................................................................................++*++*++*
执行了.
/build-dh
后,会在 keys 目录下生成 dh 参数文件 dh1024.pem。该文件客户端验证的时候会用到
[root@
test
-vm04 2.0]
# ls keys
01.pem ca.crt ca.key dh1024.pem huanqiuvpn.crt huanqiuvpn.csr huanqiuvpn.key index.txt index.txt.attr index.txt.old kevin.crt kevin.csr kevin.key serial serial.old
将
/usr/share/doc/openvpn-2
.2.2
/easy-rsa/2
.0
/keys
目录下的所有文件复制到
/etc/openvpn
下:
[root@
test
-vm04 2.0]
# cp -a /usr/share/doc/openvpn-2.2.2/easy-rsa/2.0/keys/* /etc/openvpn/
复制openvpn服务端配置文件 server.conf 到
/etc/openvpn/
目录下:
[root@
test
-vm04 2.0]
# cp -a /usr/share/doc/openvpn-2.2.2/sample-config-files/server.conf /etc/openvpn/
server.conf文件的配置
[root@
test
-vm04 2.0]
# egrep -v "^$|^#|^;" /etc/openvpn/server.conf
local
111.94.149.74
//
监听地址(内网或外网地址),最好填写openvpn服务器的公网IP地址(使用
"curl ifconfig.me"
命令查看)。或者这一行直接注释掉!(我在线上配置的就是注释这行)
port 1194
proto udp
dev tun
ca ca.crt
//CA
证书路径
cert huanqiuvpn.crt
//
此处crt以及下一行的key,请填写生成服务器端证书时用户自定义的名称
key huanqiuvpn.key
dh dh1024.pem
//
秘钥交换协议文件
server 10.8.0.0 255.255.255.0
//
给vpn客户机分配的地址池。最好别和openvpn部署机的内网ip在一个网段内
ifconfig
-pool-persist ipp.txt
push
"route 10.0.0.0 255.0.0.0"
client-to-client
keepalive 10 120
comp-lzo
user nobody
group nobody
persist-key
persist-tun
status openvpn-status.log
log openvpn.log
verb 3
5)设置iptables
先设置转发
[root@
test
-vm04 2.0]
# vim /etc/sysctl.conf
net.ipv4.ip_forward = 1
[root@
test
-vm04 2.0]
# sysctl -p //使内核参数生效
添加iptables规则,确保服务器可以转发数据包到外网:
[root@
test
-vm04 2.0]
# iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -j MASQUERADE
[root@
test
-vm04 2.0]
# service iptables save
[root@
test
-vm04 2.0]
# iptables -t nat -L
Chain PREROUTING (policy ACCEPT)
target prot opt
source
destination
Chain INPUT (policy ACCEPT)
target prot opt
source
destination
Chain OUTPUT (policy ACCEPT)
target prot opt
source
destination
Chain POSTROUTING (policy ACCEPT)
target prot opt
source
destination
MASQUERADE all -- localhost
/24
anywhere
6)启动OpenVPN
[root@
test
-vm04 2.0]
# /etc/init.d/openvpn start
Starting openvpn (via systemctl): [ OK ]
[root@
test
-vm04 2.0]
# lsof -i:1194
COMMAND PID USER FD TYPE DEVICE SIZE
/OFF
NODE NAME
openvpn 8547 nobody 5u IPv4 53264 0t0 UDP localhost:openvpn
如果1194端口启动不起来,可以通过查看
/etc/openvpn/openvpn
.log日志进行原因排查
-------------------------------------------------------------------------------------------------------------------------------
后续给同事开vpn账号,只需要下面几步(比如给zhangqiang同事开vpn)
[root@
test
-vm04 2.0]
# pwd
/usr/share/doc/openvpn-2
.2.2
/easy-rsa/2
.0
[root@
test
-vm04 2.0]
# ./build-key zhangqiang
[root@
test
-vm04 2.0]
# cp -a /usr/share/doc/openvpn-2.2.2/easy-rsa/2.0/keys/zhangqiang.* /etc/openvpn/
[root@
test
-vm04 2.0]
# /etc/init.d/openvpn restart
[root@
test
-vm04 2.0]
# lsof -i:1194
然后编写zhangqiang用户的config.ovpn客户端配置文件:
[root@
test
-vm04 2.0]
# vim /tmp/config.ovpn
client
dev tun
proto udp
remote 111.94.149.74 1194
//
注意这里的111.94.149.74是openvpn服务器端的外围ip。
resolv-retry infinite
nobind
mute-replay-warnings
ca ca.crt
cert zhangqiang.crt
key zhangqiang.key
comp-lzo
然后将ca.crt、config.ovpn、zhangqiang.crt、zhangqiang.csr、zhangqiang.key这五个文件放到zhagnqiang用户下
[root@
test
-vm04 2.0]
# mkdir /tmp/zhangqiang
[root@
test
-vm04 2.0]
# cd keys/
[root@
test
-vm04 keys]
# cp ca.crt /tmp/config.ovpn zhangqiang.crt zhangqiang.csr zhangqiang.key /tmp/zhangqiang
[root@
test
-vm04 keys]
# cd /tmp && tar -zvcf zhangqiang.tar.gz zhangqiang
然后将
/opt/zhangqiang
.
tar
.gz文件拷贝给用户zhangqiang,让他在客户机上进行openvpn的连接。
|
-----------------------------------------openvpn使用说明----------------------------------------
一、windows用户
1. 需要向管理员申请openvpn的配置及秘钥文件(总共包括5个文件:ca.crt证书、config.ovpn客户端配置文件、用户.crt、用户.csr、用户.key)。(其中,config.ovpn客户端文件是直接配置好拷贝给客户机的,这个文件在服务器端是不存在的,需要自己编写)
2. 软件安装包见文末
3. 如果你的电脑没有安装过TAP,安装过程中会有下面的提示,选择安装。













|
1
2
3
4
5
|
连接到openvpn后,查看本机分配的vpn地址:
localhost:
test
-vm kevin$
ifconfig
//
发现已经成功分配到上面定义的vpn地址范围内的地址了(10.8.0.10)
.......
utun1: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> mtu 1500
inet 10.8.0.10 --> 10.8.0.9 netmask 0xffffffff
|
|
1
2
3
4
5
6
7
8
9
10
11
|
client
dev tun
proto udp
remote 111.94.149.74 1194
resolv-retry infinite
nobind
mute-replay-warnings
ca ca.crt
cert wangshibo.crt
key wangshibo.key
comp-lzo
|
补充一下,下面的mac客户端是可用的,安装后会提示升级,升级后有可能会导致不能使用,没有特殊原因的话,就不用升级了,如果已经升级,删除后安装下面这个就行了.
mac 用户下载下面这个:https://pan.baidu.com/s/1sl3CnwT (提取密码:1j8g)
windows 用户下载下面这个:https://pan.baidu.com/s/1eS4E6Y2 (提取密码:fvkr)