H3C ipsec psk main mode配置
如图,配置RTA和RTB之间的ipsec主模式,实现内网互通,同时代理上网。
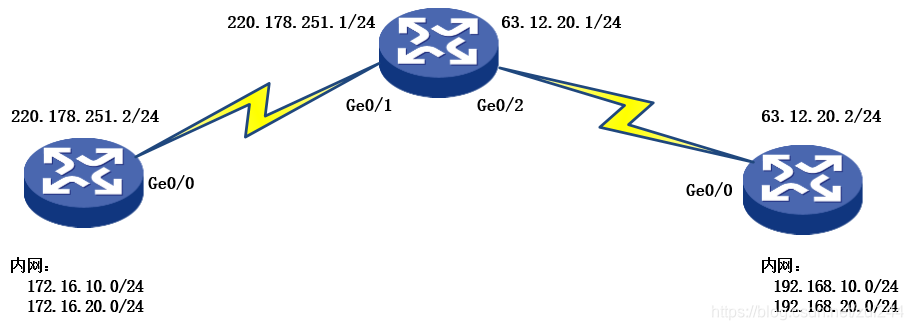
接口IP地址及路由配置略。
RTA配置:
1、配置第一阶段的ike对等体及共享秘钥
[RTA]ike keychain psk #创建名为psk的共享秘钥:ipsec123456
[RTA-ike-keychain-psk]pre-shared-key address 63.12.20.2 key simple ipsec123456
[RTA-ike-keychain-psk]quit
2、配置第二阶段的安全提议参数(封装模式、封装协议及认证加密算法等)
[RTA]ipsec transform-set proposal #创建名为proposal的ipsec安全提议
[RTA-ipsec-transform-set-proposal]encapsulation-mode tunnel #封装模式为隧道模式
[RTA-ipsec-transform-set-proposal]protocol esp #封装协议采用ESP
[RTA-ipsec-transform-set-proposal]esp authentication-algorithm sha1 #封装协议的验证算法
[RTA-ipsec-transform-set-proposal]esp encryption-algorithm 3des-cbc #封装协议的加密算法
[RTA-ipsec-transform-set-proposal]quit
3、配置IKE SA安全提议(第一阶段参数:目标地址、协商模式、共享秘钥等)
[RTA]ike proposal 1 #创建IKE协商
[RTA-ike-proposal-1]authentication-method pre-share #为IKE指定身份验证方法为共享密钥
[RTA-ike-proposal-1]encryption-algorithm 3des-cbc #指定IKE的身份加密算法为3des
[RTA-ike-proposal-1]authentication-algorithm md5 #指定IKE的身份验证算法为md5
[RTA-ike-proposal-1]dh group14 #modp2048
[RTA-ike-proposal-1]quit
[RTA]ike profile file #IKE协商的配置文件
[RTA-ike-profile-file]proposal 1 #绑定IKE协商号
[RTA-ike-profile-file]exchange-mode main #主模式
[RTA-ike-profile-file]keychain psk #指定共享秘钥名(前面已创建)
[RTA-ike-profile-file]match remote identity address 63.12.20.2 #远端对等体的地址
[RTA-ike-profile-file]dpd interval 100 retry 5 periodic #启用DPD检测线路
[RTA-ike-profile-file]quit
4、创建ACL配置第二阶段协商的兴趣流网段
[RTA]acl number 3000
[RTA-acl-ipv4-adv-3000]rule 5 permit ip source 172.16.10.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
[RTA-acl-ipv4-adv-3000]rule 10 permit ip source 172.16.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
[RTA-acl-ipv4-adv-3000]rule 15 permit ip source 172.16.20.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
[RTA-acl-ipv4-adv-3000]rule 20 permit ip source 172.16.20.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
[RTA-acl-ipv4-adv-3000]quit
5、创建ipsec策略手动协商参数
[RTA]ipsec policy ipsec 1 isakmp
[RTA-ipsec-policy-isakmp-ipsec-1]ike-profile file
[RTA-ipsec-policy-isakmp-ipsec-1]transform-set proposal
[RTA-ipsec-policy-isakmp-ipsec-1]security acl 3000
[RTA-ipsec-policy-isakmp-ipsec-1]remote-address 63.12.20.2
[RTA-ipsec-policy-isakmp-ipsec-1]quit
6、将配置好的策略匹配上接口
[RTA]interface GigabitEthernet 0/0
[RTA-GigabitEthernet0/0]ipsec apply policy ipsec
[RTA-GigabitEthernet0/0]quit
RTB配置:
[RTB]ike keychain psk
[RTB-ike-keychain-psk]pre-shared-key address 220.178.251.2 key simple ipsec123456
[RTB-ike-keychain-psk]quit
[RTB]ipsec transform-set proposal
[RTB-ipsec-transform-set-proposal]encapsulation-mode tunnel
[RTB-ipsec-transform-set-proposal]protocol esp
[RTB-ipsec-transform-set-proposal]esp authentication-algorithm sha1
[RTB-ipsec-transform-set-proposal]esp encryption-algorithm 3des-cbc
[RTB-ipsec-transform-set-proposal]quit
[RTB]ike proposal 1
[RTB-ike-proposal-1]authentication-method pre-share
[RTB-ike-proposal-1]encryption-algorithm 3des-cbc
[RTB-ike-proposal-1]authentication-algorithm md5
[RTB-ike-proposal-1]dh group14
[RTB-ike-proposal-1]quit
[RTB]ike profile file
[RTB-ike-profile-file]proposal 1
[RTB-ike-profile-file]exchange-mode main
[RTB-ike-profile-file]keychain psk
[RTB-ike-profile-file]match remote identity address 220.178.251.2
[RTB-ike-profile-file]dpd interval 100 retry 5 periodic
[RTB-ike-profile-file]quit
[RTB]acl number 3000
[RTB-acl-ipv4-adv-3000]rule 5 permit ip source 192.168.10.0 0.0.0.255 destination 172.16.10.0 0.0.0.255
[RTB-acl-ipv4-adv-3000]rule 10 permit ip source 192.168.10.0 0.0.0.255 destination 172.16.20.0 0.0.0.255
[RTB-acl-ipv4-adv-3000]rule 15 permit ip source 192.168.20.0 0.0.0.255 destination 172.16.10.0 0.0.0.255
[RTB-acl-ipv4-adv-3000]rule 20 permit ip source 192.168.20.0 0.0.0.255 destination 172.16.20.0 0.0.0.255
[RTB-acl-ipv4-adv-3000]quit
[RTB]ipsec policy ipsec 1 isakmp
[RTB-ipsec-policy-isakmp-ipsec-1]ike-profile file
[RTB-ipsec-policy-isakmp-ipsec-1]transform-set proposal
[RTB-ipsec-policy-isakmp-ipsec-1]security acl 3000
[RTB-ipsec-policy-isakmp-ipsec-1]remote-address 220.178.251.2
[RTB-ipsec-policy-isakmp-ipsec-1]quit
[RTB]interface GigabitEthernet 0/0
[RTB-GigabitEthernet0/0]ipsec apply policy ipsec
[RTB-GigabitEthernet0/0]quit
手动流量触发,使得IPsec隧道建立成功:
[RTA]ping -a 172.16.10.254 192.168.10.254
Ping 192.168.10.254 (192.168.10.254) from 172.16.10.254: 56 data bytes, press CTRL_C to break
Request time out
56 bytes from 192.168.10.254: icmp_seq=1 ttl=255 time=15.978 ms
56 bytes from 192.168.10.254: icmp_seq=2 ttl=255 time=46.047 ms
56 bytes from 192.168.10.254: icmp_seq=3 ttl=255 time=40.687 ms
56 bytes from 192.168.10.254: icmp_seq=4 ttl=255 time=7.064 ms
[RTA]display ike sa verbose
-----------------------------------------------
Connection ID: 1
Outside VPN:
Inside VPN:
Profile: file
Transmitting entity: Initiator
-----------------------------------------------
Local IP: 220.178.251.2
Local ID type: IPV4_ADDR
Local ID: 220.178.251.2
Remote IP: 63.12.20.2
Remote ID type: IPV4_ADDR
Remote ID: 63.12.20.2
Authentication-method: PRE-SHARED-KEY
Authentication-algorithm: MD5
Encryption-algorithm: 3DES-CBC
Life duration(sec): 86400
Remaining key duration(sec): 86375
Exchange-mode: Main
Diffie-Hellman group: Group 14
NAT traversal: Not detected
Extend authentication: Disabled
Assigned IP address:
[RTA]display ipsec sa
-------------------------------
Interface: GigabitEthernet0/0
-------------------------------
-----------------------------
IPsec policy: ipsec
Sequence number: 1
Mode: ISAKMP
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Path MTU: 1444
Tunnel:
local address: 220.178.251.2
remote address: 63.12.20.2
Flow:
sour addr: 172.16.10.0/255.255.255.0 port: 0 protocol: ip
dest addr: 192.168.10.0/255.255.255.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 3470613151 (0xcedd5a9f)
Connection ID: 4294967296
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3527
Max received sequence-number: 4
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 908089754 (0x3620599a)
Connection ID: 4294967297
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3527
Max sent sequence-number: 4
UDP encapsulation used for NAT traversal: N
Status: Active
解决内网上网问题:
创建ACL与ipsec接口策略的ACL流量相反,目的是使得其他流量走NAT出去
[RTA]acl number 3001
[RTA-acl-ipv4-adv-3001]rule 5 deny ip source 172.16.10.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
[RTA-acl-ipv4-adv-3001]rule 10 deny ip source 172.16.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
[RTA-acl-ipv4-adv-3001]rule 15 deny ip source 172.16.20.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
[RTA-acl-ipv4-adv-3001]rule 20 deny ip source 172.16.20.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
[RTA-acl-ipv4-adv-3001]rule 100 permit ip
[RTA-acl-ipv4-adv-3001]quit
[RTA]interface GigabitEthernet 0/0
[RTA-GigabitEthernet0/0]nat outbound 3001
[RTA-GigabitEthernet0/0]quit
[RTA]ping -a 172.16.10.254 63.12.20.1
Ping 63.12.20.1 (63.12.20.1) from 172.16.10.254: 56 data bytes, press CTRL_C to break
56 bytes from 63.12.20.1: icmp_seq=0 ttl=255 time=4.281 ms
56 bytes from 63.12.20.1: icmp_seq=1 ttl=255 time=5.708 ms
56 bytes from 63.12.20.1: icmp_seq=2 ttl=255 time=5.865 ms
56 bytes from 63.12.20.1: icmp_seq=3 ttl=255 time=5.906 ms
56 bytes from 63.12.20.1: icmp_seq=4 ttl=255 time=39.115 ms
