OpenShift使用的是RBAC 身份以及权限验证的解决方案。首先:
集群管理员可以使用集群角色和绑定来控制谁对 OpenShift Container Platform 平台本身和所有项目具有各种访问权限等级。
开发人员可以使用本地角色和绑定来控制谁有权访问他们的项目。请注意,授权是与身份验证分开的一个步骤,身份验证更在于确定执行操作的人的身份。
几个重要概念:
规则: 是对资源的操作权限,比如能否创建、get、list pod 等资源
角色:是规则的集合,可以理解为规则的实体。
绑定: 用户和/组与角色之间的关联。
控制授权的 RBAC 角色和绑定有两个级别:
rolebinding:
称之为本地 namespace 基本的绑定
clusterrolebindings:
全局整个集群的绑定
下面是集群中默认的集群角色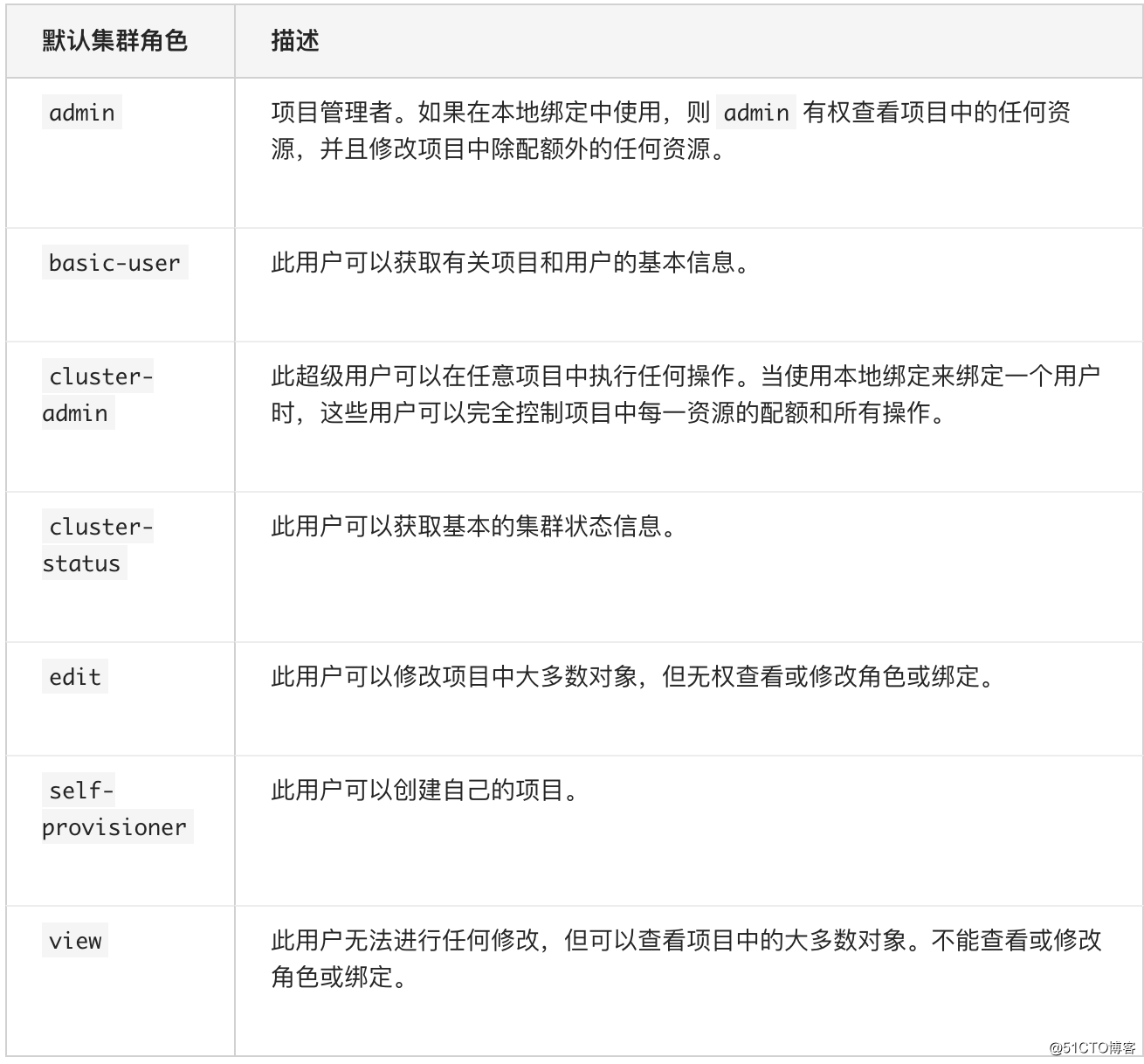
比如我们使用了 用户user1 通过roelbinding 绑定了admin 这个角色 该用户只能对当前的project 用于admin 权限,倘若我们使用clusterrolebinding 进行绑定则具有了整个cluster 的admin 权限
下图可以很好的解释清楚其中的关系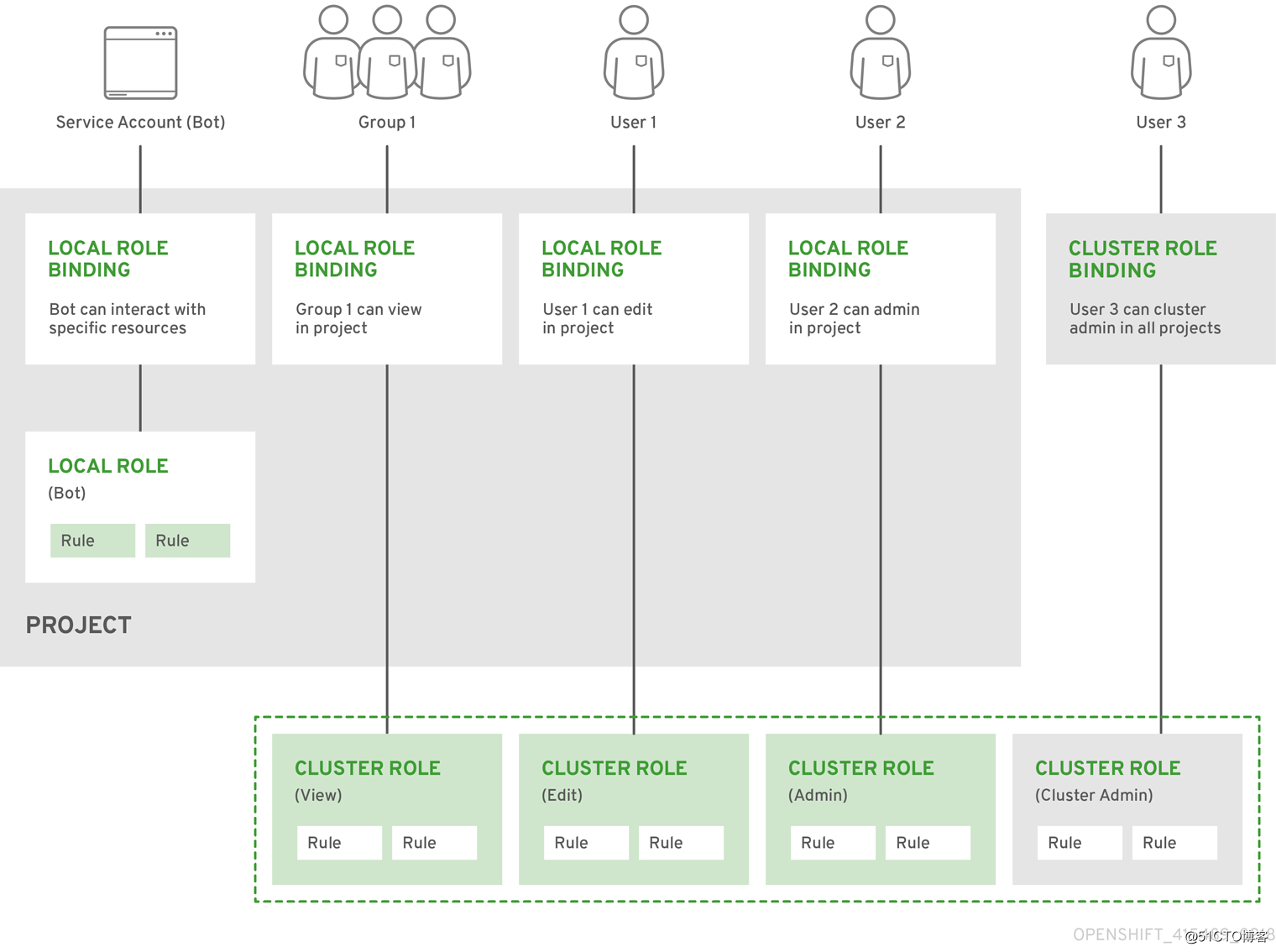
实验:
我们要创建一个rolebinding ,使其有get,list 等权限,并且绑定到用户dev上面
1、创建project 名为dev
oc create ns dev
2、创建一个rolebinding
[core@w1 ~]$ oc create role dev-rolebinding --verb=get,list,create,update,delete,watch --resource=pod,deployment -n dev --dry-run=true -oyaml
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
creationTimestamp: null
name: dev-rolebinding
rules:
- apiGroups:
- ""
resources:
- pods
verbs:
- get
- list
- create
- update
- delete
- watch
- apiGroups:
- extensions
resources:
- deployments
verbs:
- get
- list
- create
- update
- delete
- watch
[core@w1 ~]$ 以上并未真正执行,下面我们来真正创建下。
[core@w1 ~]$ oc create role dev-rolebinding --verb=get,list,create,update,delete,watch --resource=pod,deployment -n dev
role.rbac.authorization.k8s.io/dev-rolebinding created我们进行rolebinding和dev1 用户在dev 这个namespace 进行绑定
[core@w1 ~]$ oc adm policy add-role-to-user dev-rolebinding dev1 --role-namespace=dev -n dev
Warning: User 'dev1' not found
role.rbac.authorization.k8s.io/dev-rolebinding added: "dev1"
[core@w1 ~]$ 可以看到提示,dev1用户集群内没有这个user,下面我们来创建一个。
1、首先在装有httpd-tools 的机器上利用htpasswd 创建用户并且指定密码,并把用户文件copy到可以认证openshift 的机器上
[root@pub ~]# htpasswd -c -B -b /tmp/htpasswd-dev1 dev1 dev1
Adding password for user dev1
[root@pub ~]# scp /tmp/htpasswd-dev1 [email protected]:/tmp
htpasswd-dev1 100% 66 76.9KB/s 00:00
[root@pub ~]# 下面在openshift的机器上操作:
[root@m1 ~]# oc create secret generic htpass-secret-dev1 --from-file=htpasswd=/tmp/htpasswd-dev1 -n openshift-config
secret/htpass-secret-dev1 created
[root@m1 ~]# vi httpd-passwd.yaml
[root@m1 ~]# cat httpd-passwd.yaml
apiVersion: config.openshift.io/v1
kind: OAuth
metadata:
name: cluster
spec:
identityProviders:
- name: my_htpasswd_provider-demo
mappingMethod: claim
type: HTPasswd
htpasswd:
fileData:
name: htpass-secret-dev1
[root@m1 ~]# oc apply -f httpd-passwd.yaml
oauth.config.openshift.io/cluster configured
[root@m1 ~]#
此时使用dev1 用户尝试登陆
[core@w1 ~]$ oc login -u dev1
Authentication required for https://192.168.1.131:6443 (openshift)
Username: dev1
Password:
Login successful.
You don't have any projects. You can try to create a new project, by running
oc new-project <projectname>
[core@w1 ~]$
dev1 用户已经创建成功,再次赋权
[core@w1 ~]$ oc adm policy add-role-to-user dev-rolebinding dev1 --role-namespace=dev -n dev
role.rbac.authorization.k8s.io/dev-rolebinding added: "dev1"
[core@w1 ~]$
此时利用dev1 用户查看dev 这个project的pod
[core@m1 ~]$ oc get pod,deployment -n dev
No resources found in dev namespace.
[core@m1 ~]$
尝试查看default 这个project的pod,应该是拒绝的
[core@m1 ~]$ oc get pod,deployment -n default
Error from server (Forbidden): pods is forbidden: User "dev1" cannot list resource "pods" in API group "" in the namespace "default"
Error from server (Forbidden): deployments.extensions is forbidden: User "dev1" cannot list resource "deployments" in API group "extensions" in the namespace "default"
[core@m1 ~]$
至此roebinding 已经完成
下面试验下 clusterrolebinding
创建clusterrolebinding,并且和dev1 用户绑定
[core@w1 ~]$ oc create clusterrole clyster-rolebinding --verb=get,list,create,update,delete,watch --resource=pod,deployment,ns -n dev
clusterrole.rbac.authorization.k8s.io/clyster-rolebinding created
[core@w1 ~]$ oc adm policy add-cluster-role-to-user dev-rolebinding dev1
clusterrole.rbac.authorization.k8s.io/dev-rolebinding added: "dev1"
[core@w1 ~]$
下面再次利用dev1 用户查看用户
[core@w1 ~]$ oc whoami
dev1
[core@w1 ~]$ oc get pod -n default
NAME READY STATUS RESTARTS AGE
appv1-5d8bc7bc75-bh4nd 1/1 Running 0 15h
appv1-5d8bc7bc75-gbqcb 1/1 Running 0 7d1h
appv1-5d8bc7bc75-lslxz 1/1 Running 0 15h
hello-openshift-1-585zl 1/1 Running 0 15h
myapp-1-74f5dcc-5t4lv 1/1 Running 0 15h
myapp-1-74f5dcc-79slr 1/1 Running 0 15h
myapp-1-74f5dcc-bztkc 1/1 Running 0 7d21h
myapp-6d9dcf58d6-6r7sz 1/1 Running 0 15h
myapp-6d9dcf58d6-hl6n2 1/1 Running 0 7d21h
myapp-6d9dcf58d6-m5f7x 1/1 Running 0 15h
myapp-deploy-6965d5bd75-5s6kj 1/1 Running 0 15h
myapp-deploy-6965d5bd75-qgqhn 1/1 Running 0 6d16h
myapp-deploy-6965d5bd75-vt7x4 1/1 Running 0 15h
test-nginx-58bfbcc86d-nffgg 1/1 Running 0 15h
test-test-6f7947d649-jp2zj 1/1 Running 0 15h
[core@w1 ~]$
使dev1 用户成为集群管理员
[root@m1 ~]# oc adm policy add-cluster-role-to-user cluster-admin dev1
clusterrole.rbac.authorization.k8s.io/cluster-admin added: "dev1"