问题
1)配置DHCP中继,让客户端从DHCP服务器获取地址。
2)客户机可以ping通R1。
使用eNSP搭建实验环境,如图 所示。
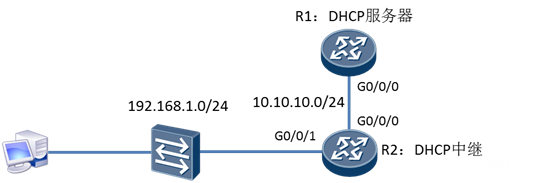
步骤
实现此案例需要按照如下步骤进行。
[R1]dis cu
[V200R003C00]
#
sysname R1
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
dhcp enable
#
ip pool pool_tedu
gateway-list 192.168.1.254
network 192.168.1.0 mask 255.255.255.0
lease day 3 hour 0 minute 0
dns-list 8.8.8.8
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface Ethernet0/0/0
#
interface Ethernet0/0/1
#
interface Ethernet0/0/2
#
interface Ethernet0/0/3
#
interface Ethernet0/0/4
#
interface Ethernet0/0/5
#
interface Ethernet0/0/6
#
interface Ethernet0/0/7
#
interface GigabitEthernet0/0/0
ip address 10.10.10.1 255.255.255.0
dhcp select global
#
interface GigabitEthernet0/0/1
#
interface NULL0
#
ip route-static 192.168.1.0 255.255.255.0 10.10.10.2
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
[R2]dis cu
[V200R003C00]
#
sysname R2
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
dhcp enable
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface Ethernet0/0/0
#
interface Ethernet0/0/1
#
interface Ethernet0/0/2
#
interface Ethernet0/0/3
#
interface Ethernet0/0/4
#
interface Ethernet0/0/5
#
interface Ethernet0/0/6
#
interface Ethernet0/0/7
#
interface GigabitEthernet0/0/0
ip address 10.10.10.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 192.168.1.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.10.10.1
#
interface NULL0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
主机获取的IP如图- 所示:
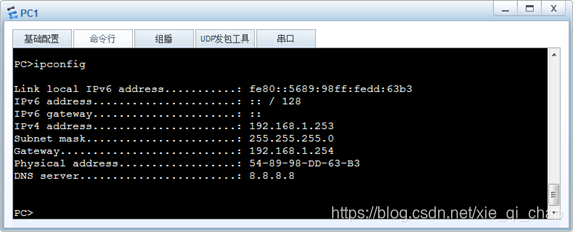
验证主机可以ping通R1,如图 所示:

