1.基线
即安全基线配置,诸如操作系统、中间件和数据库的一个整体配置,这个版本中各项配置都符合安全方面的标准。比如在系统安装后需要按安全基线标准,将新机器中各项配置调整到一个安全、高效、合理的数值。
2.基线扫描
使用自动化工具、抓取系统和服务的配置项。将抓取到的实际值和标准值进行对比,将不符合的项显示出来,最终以报告的形式体现出扫描结果
有的工具将配置采集和配置对比分开,通过自动化脚本采集配置后再通过特别的软件转换为适合人类阅读的文档
3.自动化脚本
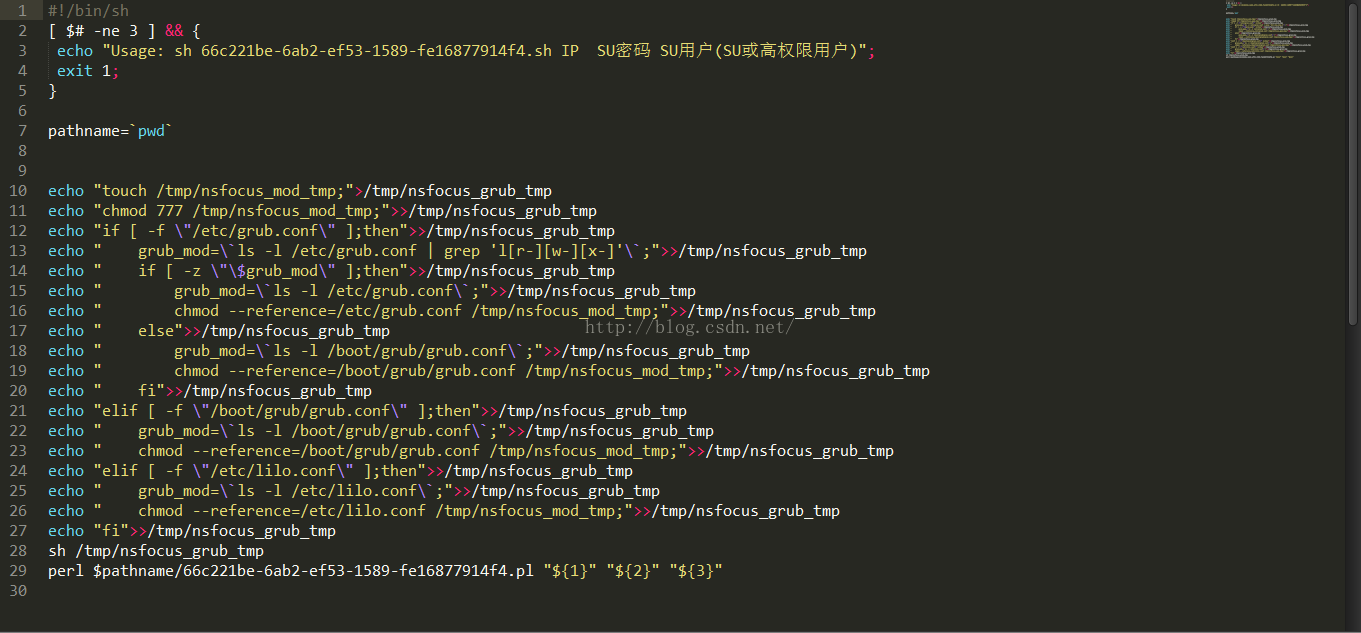
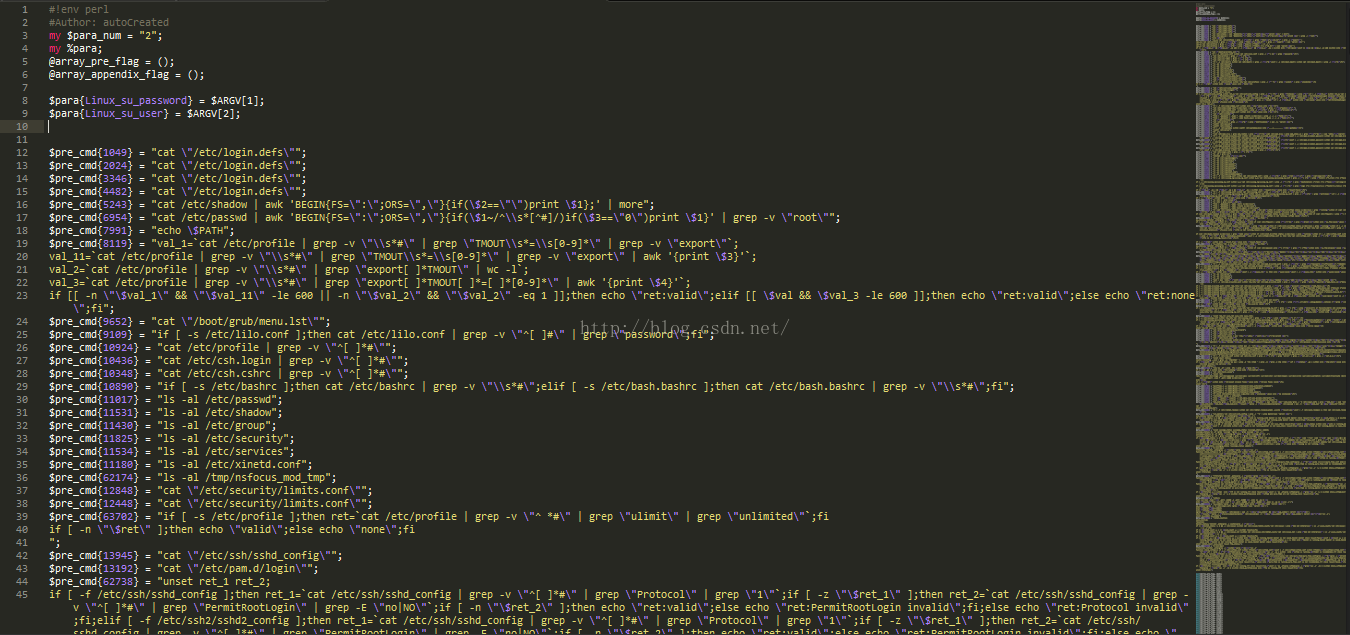
.sh文件为执行文件。而.pl文件则包含着检查命令。
下面给出两个文件的截图
4.Linux基线加固
下面对重要程度排名靠前的项进行脚本加固
基线加固脚本如下:
(*所有操作均在拷贝后执行)