nginx parsing vulnerability reproducibility
First, Vulnerability Description
The vulnerability has nothing to do with nginx, php version, users belong to parsing vulnerability caused by improper configuration
Second, the principle of vulnerability
1, due to the configuration nginx.conf leads to the nginx '.php' end of the file to fastcgi process, may be configured for this http: end //ip/uploadfiles/test.png/.php (url not necessarily ' .php ', any php file server that does not exist can be, for example,' a.php '), which is our test.png upload photo files containing PHP code.

2, but was found when processing fastcgi '.php' file does not exist, then the configuration file php.ini cgi.fix_pathinfo = 1 play a role in the repair path configured to, if the current path does not exist, using an upper layer path. For this reason referred to here fastcgi document processing becomes '/test.png'.
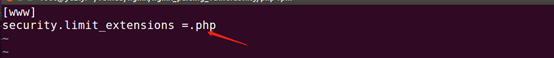
3, the most important point is that php-fpm.conf in security.limit_extensions fastcgi configuration items limits the types of analytical documents (ie what types of files designated as code analysis), this set is empty when it will allow fastcgi ' .png 'as a code analysis and other documents.

Note: Restrictions fpm allow extension script parsing. This setting can prevent erroneous web server configuration. Fpm should be limited only to resolve the extension .php, preventing malicious users from using other extensions run php code. Default value: .php
Third, the vulnerability environment to build and reproducibility
1, docker built environment vulnerability
2. Run the following command to run the environment
docker-compose up -d
3, browser access http://172.17.0.1/

4, upload a picture, burp capture, modify packets, add at the end of <php phpinfo ();??>
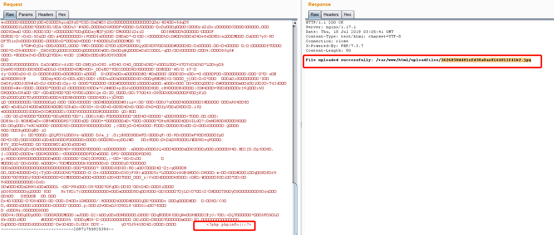
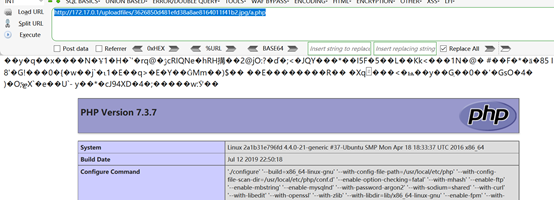
5, browser access http://172.17.0.1/uploadfiles/3626850d481efd38a8ae8164011f41b2.jpg/a.php
The following diagram see the successful implementation of the php code, indicating the presence Parsing Vulnerability
6, modify the configuration file php-fpm.conf
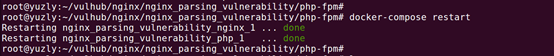
7, restart the service
docker-compose restart
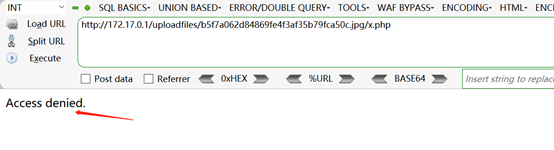
8、浏览器再次访问http://172.17.0.1/uploadfiles/b5f7a062d84869fe4f3af35b79fca50c.jpg/x.php,发现被拒绝,说明漏洞被修复
四、漏洞防御
1、 将php.ini文件中的cgi.fix_pathinfo的值设置为0,这样php再解析1.php/1.jpg这样的目录时,只要1.jpg不存在就会显示404页面
2、 php-fpm.conf中的security.limit_extensions后面的值设置为.php