1. General Framework Agreement formal safety analysis
Combining case multiple protocols formal analysis of the conditions necessary preparations in formal safety analysis of the agreement drew a mind map, you do not use sequence diagrams or hierarchical graph, because the analysis of a protocol in many ways go hand in hand, However, the security focus of the analysis protocol or standard analysis protocol agreement itself. This is the basis of the protocol analysis, no correct protocol specification analysis, subsequent communication session protocol is wrong. Then the follow-up work will not make sense.
Any agreement has its own protocol specification documents describe, covering protocols, security attributes, establish ways of communication, how to achieve data transmission. And the encryption algorithm used, the field specifically defined protocol structure, parameters, formats, and so on.
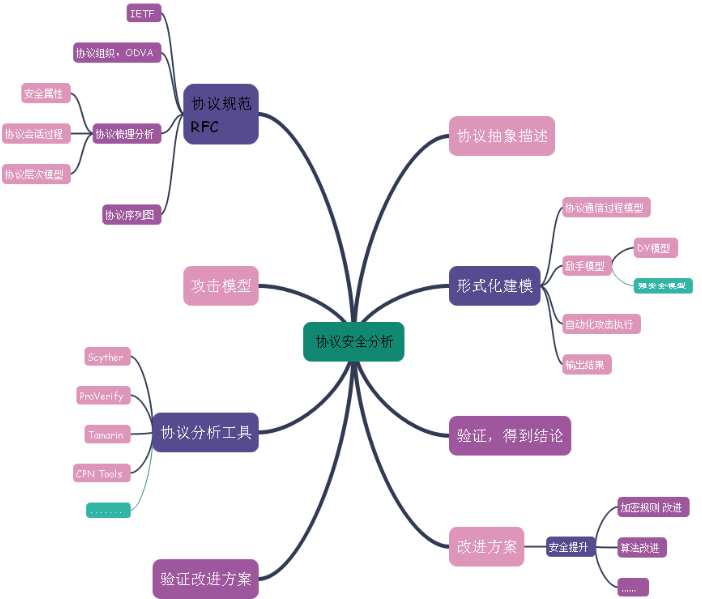
2, how protocol specification protocol abstraction into specific communication session
3, how to protocol formal analysis tool selection
4, abstract standard protocol analysis
5, agreements
3, industrial protocol analysis must be established in agreement protocol specification document
Security protocol analysis industry generally use the formal agreement abundance security analysis, modeling needs. The premise of the agreement is to be modeled to illustrate the protocol specification document according to the agreement
There are two problems here: the problem size formal abstract description of the first protocol
4, security protocol security analysis Formal analysis was generally used, need to model, analyze first session, wherein the security attributes protocol and the like according to the protocol specification document.
In the study of industrial safety when the underlying security must IPC protocol
references:
Wu Lijun, research Su Kai Lok security authentication protocol formal method [J] Computer Engineering and Applications, 2004 (17):... 152-155 (concept paper on the issue are three ways to review a more thorough analysis of the security agreement)