statement
This article is a study note compiled by studying the report of the github5.com website . I hope that more people will benefit from sharing it. If there is any infringement, please contact us in time
Research Background
Driven by the two wheels of policy and technology, industrial control systems are increasingly connected to corporate intranets and the Internet, and combined with new service models, gradually forming an industrial Internet architecture. The Industrial Internet is the product of the deep integration of the industrial system and the Internet system under the digital wave, and is the key support for the new round of industrial revolution. On the one hand, the development of the industrial Internet has greatly promoted the improvement of production efficiency and service level, on the other hand, it has also made the originally closed system more and more open, resulting in increasing system security risks and intrusion threats, and network security issues have become increasingly prominent .
The Industrial Internet has been widely used in key information infrastructure fields such as electricity, transportation, petroleum, heating, and manufacturing. Once a security incident occurs, it will often cause huge losses and extensive impact. However, due to the particularity of the industrial Internet environment, traditional IT information security technologies cannot completely and effectively protect the security of industrial systems, and even many commonly used security technologies cannot be directly applied to the security protection of industrial networks. For the analysis and protection of industrial Internet security, some special methods and special technologies need to be used.
The National and Local Joint Engineering Laboratory of Industrial Control System Security (hereinafter referred to as the "Joint Laboratory") released the "IT/OT Integrated Industrial Information Security Situation Report" in 2017, summarizing and analyzing the new challenges brought about by IT/OT integration, and giving Industrial Information Security Recommendations and Outlook.
In order to provide reference and reference for government departments, scientific research institutions and industrial enterprises, the National and Local Joint Engineering Laboratory of Industrial Control System Security (hereinafter referred to as the Joint Laboratory) compiled the "Industrial Internet Security Risk Situation Report (2018)".
This report analyzes industrial Internet security vulnerabilities using a new type of vulnerability scoring system, which includes indicators that reflect the security characteristics of industrial control, such as visibility, controllability, and service status of vulnerabilities exploiting targets, into the scope of quantitative evaluation. Based on the vulnerability information related to industrial control systems collected in the joint laboratory vulnerability database, the report comprehensively refers to the vulnerability information released by the four major public vulnerability platforms of CVE, NVD, CNVD, and CNNVD, analyzes the security risk situation of the industrial Internet, and compiles the "Industrial Internet Security Risk Situation Report (2018).
In addition, this report analyzes the industrial control components and security threats exposed on the Internet, and finally puts forward recommendations for promoting industrial Internet security.
The content of the "Industrial Internet Security Risk Situation Report" was comprehensively included in the "IT/OT Integrated Industrial Information Security Situation Report (2018)" annual report. "IT/OT Integrated Industrial Information Security Situation Report (2018)" is a continuation of the "IT/OT Integrated Industrial Information Security Situation Report (2017)" released in 2017, summarizing and analyzing the industrial Internet IT/OT integration in 2018. New challenges, security status, industry development trends, major application cases, etc., give suggestions and prospects for industrial information security in 2019.
Finally, I hope this report can help readers have a more comprehensive and cutting-edge understanding of industrial Internet security.
Internet exposure of industrial control systems
The exposure of industrial control systems on the Internet is a fundamental issue in industrial Internet security. The so-called "exposure" means that we can directly access or query certain industrial components related to industrial control systems through the Internet, such as industrial control equipment, protocols, software, systems, etc.
One of the main reasons for the exposure of industrial control systems is the continuous convergence of "business network (IT)" and "industrial network (OT)". While the connectivity of IT and OT networks expands the development space of industrial control systems, it also brings about network security issues for industrial control systems. In recent years, in order to integrate management and control and achieve high efficiency and high benefits in production and management, enterprises have generally promoted production execution systems, realized data exchange between management information networks and control networks, and realized industrial control systems and management information systems. integration. In this way, if the necessary separate management and control work is not done well, the originally closed OT system will face the risk of various network attacks from the Internet side after it communicates and interconnects with the Internet through the management system.
The direct connection of industrial control systems to the Internet, also known as "exposure" on the Internet, should be viewed in two parts: on the one hand, the more industrial control systems in a certain area are exposed to the Internet, it often indicates that the industrial systems in that area are exposed to the Internet. The higher the degree of informatization, the more developed the industrial Internet; on the other hand, because the vast majority of industrial components do not actually need to be remotely operated through the Internet, the greater the proportion of exposure, it often means that the industrial system is under information At the same time, if the necessary isolation work is not fully done, the risk of the system encountering attacks and intrusions is also greater.
The monitoring data of the US security company Positive Technologies better reflects the exposure of industrial components on the Internet worldwide. In order to collect accessible industrial control system sites and components on the Internet, Positive technologies adopts a passive approach, using publicly accessible engines: Google, Shodan (shodan.io), Censys (censys.io) to conduct global industrial system searched. Among them, Shodan and Censys can search for the networking status of industrial servers, routers, dedicated cameras and other equipment.

According to Positive Technologies 2018 research data, the total number of exposed components in the current global industrial control system network is about 176,000. From the perspective of the country and geographical distribution of these industrial components, the networked industrial control components are mainly concentrated in the Americas and European countries, of which the Americas account for more than 40%. This is also the main reason why industrial Internet security incidents are mostly concentrated in developed countries such as Europe and America. From the perspective of specific countries, the United States has the most serious exposure to the Internet of industrial control system components, reaching 64,287; followed by Germany, with 13,242; France ranked third, with 7,759. China ranks fifth in the world, after Canada, with 6,223. The number and distribution of exposed industrial control system networking components in various countries are shown in the figure below.
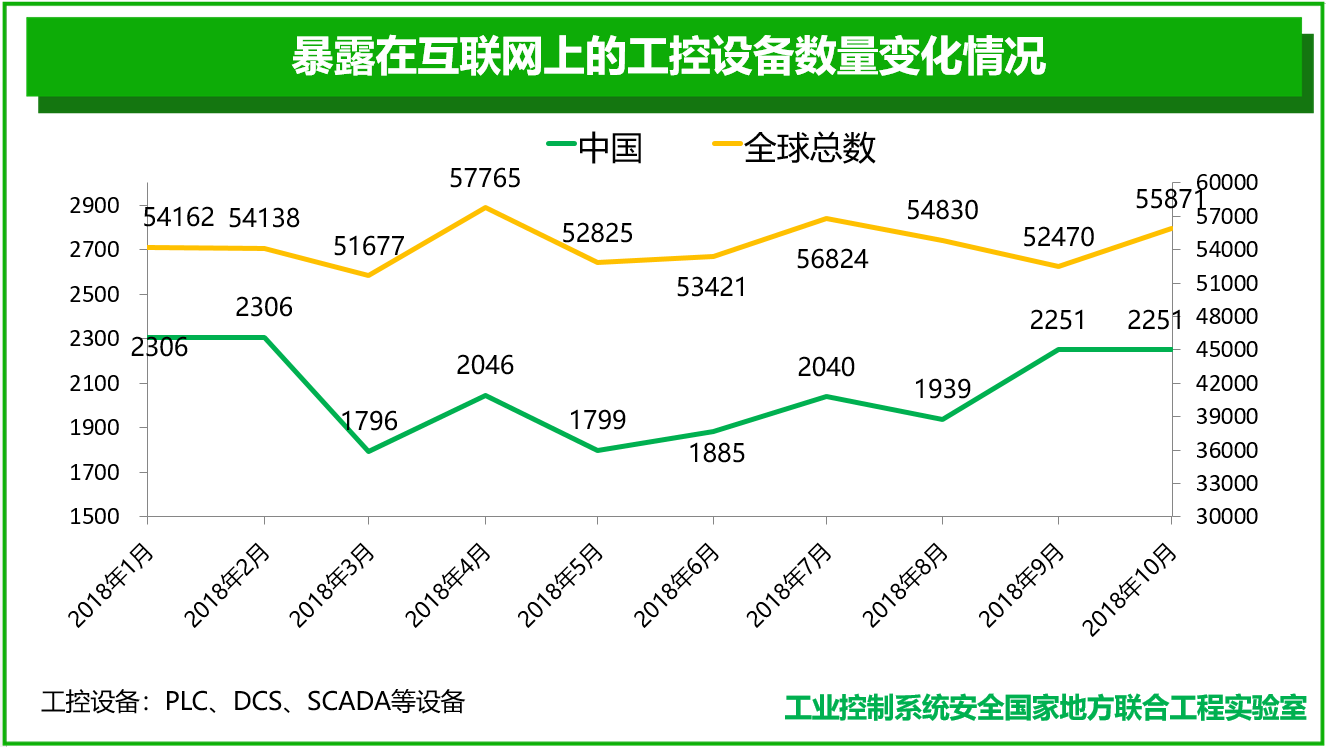
Of all the industrial control system components, the exposure of industrial control equipment is the most dangerous. The exposure of industrial control equipment means that attackers may launch attacks directly on the equipment itself. Based on national and global active detection, 360 Industrial Internet Security Big Data Analysis Platform - Hubble Platform has included the number of industrial control system devices exposed on the Internet in China and around the world in 2018. The industrial control equipment counted by the platform mainly includes PLC, DCS, DTU, SCADA and other equipment.
Statistics show that throughout 2018, the number of industrial control equipment exposures in China and the world was basically stable. At the end of 2018, there was a slight increase compared with the beginning of 2018. In April 2018, industrial control equipment in China and the world showed a slight growth trend. The line chart of the number of exposed industrial control devices is shown below.
Analysis of Industrial Internet Security Vulnerabilities
The problem of security vulnerabilities is another persistent disease facing the industrial Internet. In particular, unlike general IT systems, due to the constraints of the production environment, many industrial system security vulnerabilities may not be able to be repaired even if they are known.
This section is mainly based on the vulnerability information related to industrial control systems collected in the joint laboratory vulnerability database, and comprehensively refers to Common Vulnerabilities & Exposures (CVE), National Vulnerability Database (NVD), China National Information Security Vulnerability Sharing Platform (CNVD) and The vulnerability information released by the National Information Security Vulnerability Database (CNNVD) analyzes the security threat situation and vulnerability of industrial control systems from the aspects of the annual change trend of industrial control vulnerabilities, level of hazards, vulnerability types, industries involved in vulnerabilities, and types of vulnerable devices.
The industrial control vulnerability risk assessment method in this report is based on the general vulnerability scoring system, and includes indicators that reflect the security characteristics of industrial control, such as visibility, controllability, and vulnerability utilization target service status, into the scope of quantitative assessment. This method uses an improved risk assessment algorithm for industrial control vulnerabilities, which can not only generate basic scores and life cycle scores for industrial control vulnerabilities, but also be used by security personnel to generate environmental scores based on the specific needs of actual industrial control security scenarios.
The number of security vulnerabilities is increasing rapidly, and the security situation is becoming increasingly severe
According to the latest statistics from the China National Information Security Vulnerability Sharing Platform (CNVD), from 2000 to 2009, the number of industrial control system vulnerabilities collected by CNVD has remained in single digits each year. But by 2010, that number had climbed to 32, before jumping to 190 the following year. This and the occurrence of the situation are directly related to the Stuxnet worm (Stuxnet virus) discovered in 2010 . Stuxnet virus is the world's first destructive virus written specifically for industrial control systems. Since then, the industry has generally paid attention to the security of industrial control systems, and the number of security holes in industrial control systems has increased rapidly.
However, from 2011 to 2015, the number of industrial control system vulnerabilities included in CNVD showed a continuous steady and declining trend. After the blackout in Ukraine from the end of 2015 to the beginning of 2016, the discovery of industrial control system vulnerabilities entered a period of rapid growth again: 191 in 2016; 351 in 2017; and 442 in 2018.

The diversity of security vulnerability types is obvious
Among the industrial control system vulnerabilities collected by the four major vulnerability platforms in 2018, the causes of the vulnerabilities are obviously diversified, and there are more than 30 technical types. Among them, denial of service vulnerabilities (103), buffer overflow vulnerabilities (54) and access control vulnerabilities (32) are the most common.
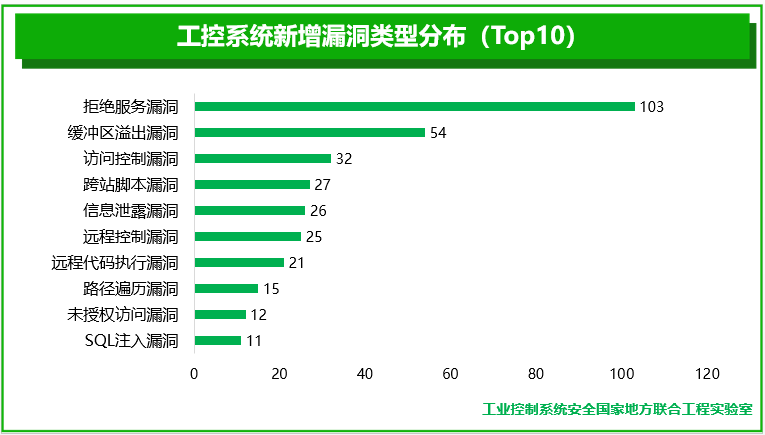
Attackers can use various vulnerabilities to obtain illegal control rights, bypass the verification mechanism through traversal, and send a large number of requests to cause resource overload and other security incidents. In fact, no matter what kind of vulnerability the attacker uses to cause abnormal operation of the production plant, it will affect the sensitivity and reliability of the industrial control system components and equipment, causing serious security problems.
High proportion of high-risk vulnerabilities
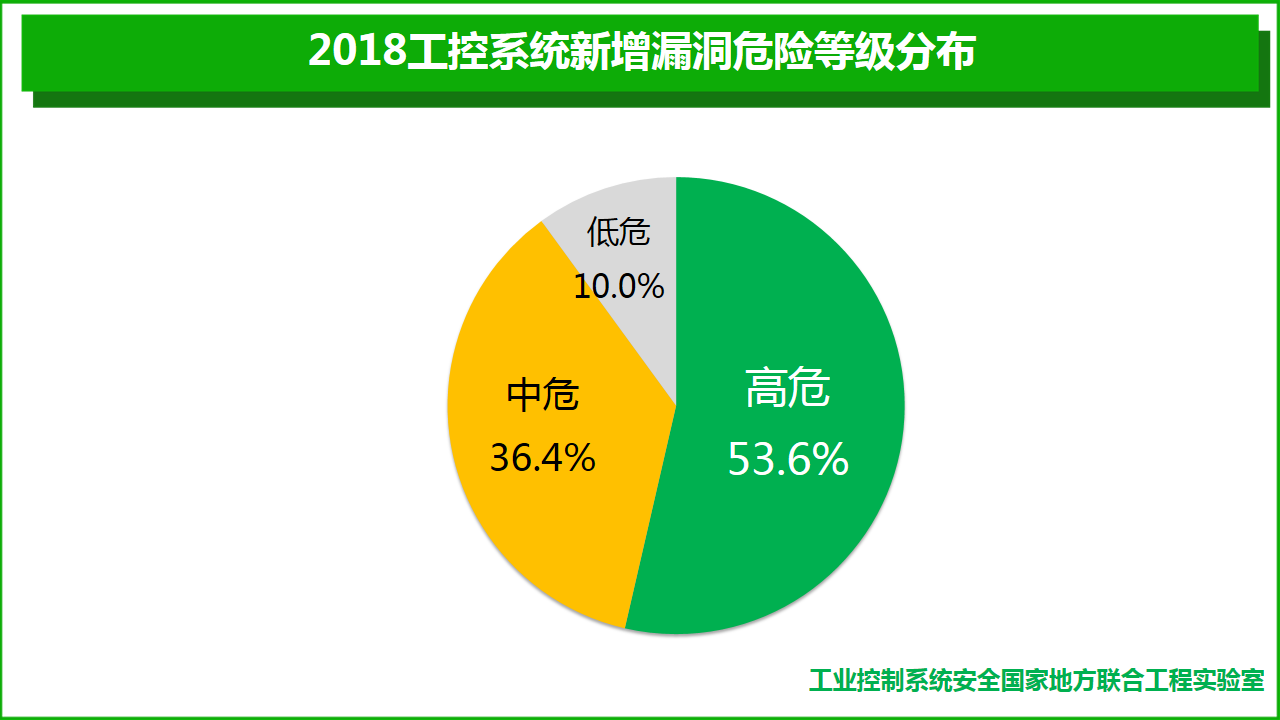
Among the industrial control system vulnerabilities collected by the four major vulnerability platforms in 2018, high-risk vulnerabilities accounted for 53.6%, medium-risk vulnerabilities accounted for 36.4%, and medium-high risk vulnerabilities accounted for 90%. Vulnerability hazard levels are distributed as follows:
Vulnerabilities involve mainly international manufacturers
Among the industrial control system vulnerabilities newly recorded by the four major platforms in 2018, seven of the top eight industrial control manufacturers involved are international manufacturers, and one is a Taiwanese manufacturer. These vendors are Siemens, Schneider, Advantech, Rockwell, Omron, Moxa, Fuji Electric and Cisco. Vulnerabilities involving major vendors are shown in the figure below:
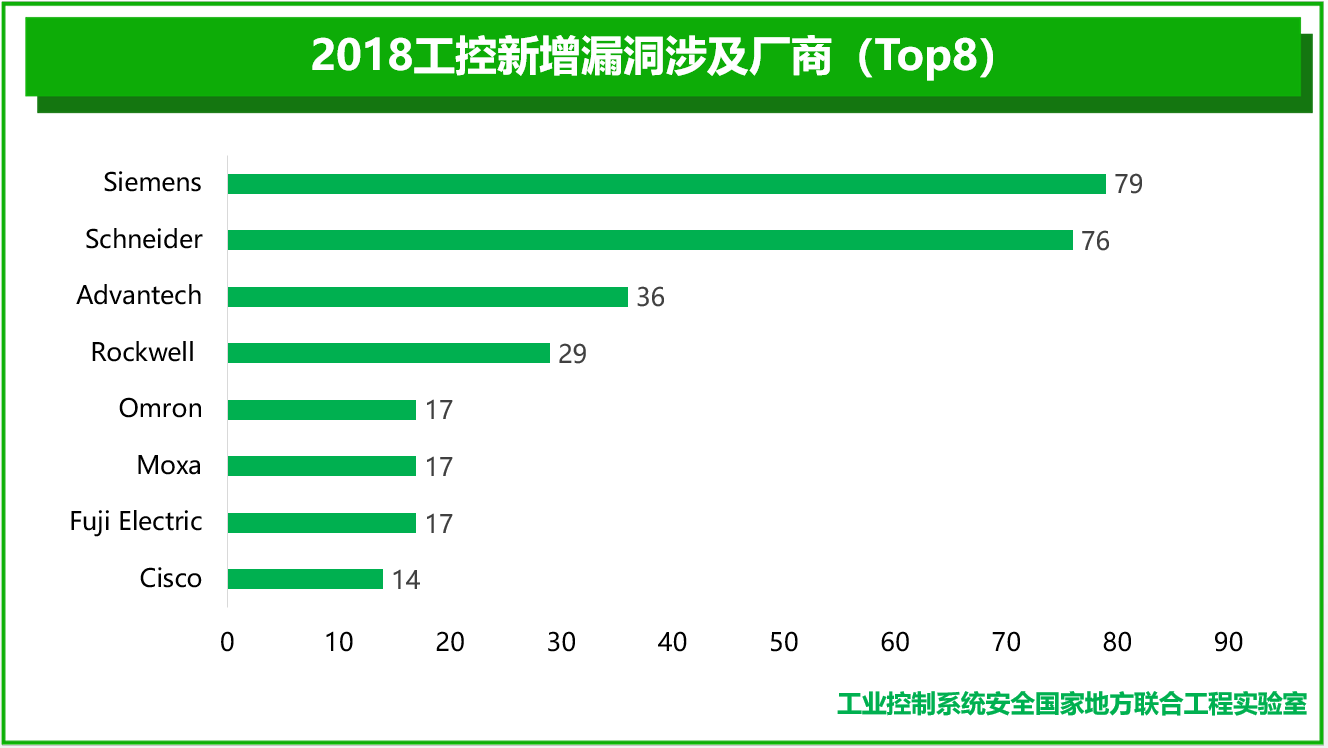
What needs to be explained is that although security vulnerabilities reflect the vulnerability of industrial control systems to a certain extent, it is not possible to judge the security of comparative manufacturers' products one-sidedly based on the number of reported security vulnerabilities of manufacturers. Generally speaking, the more widely used a vendor's products are, the more attention they will receive from security researchers, and therefore the greater the possibility of security vulnerabilities being discovered. To some extent, the vendor distribution of security vulnerability reports reflects the attention of researchers to a greater extent.
Vulnerabilities involve a wide range of industries, mainly manufacturing and energy industries
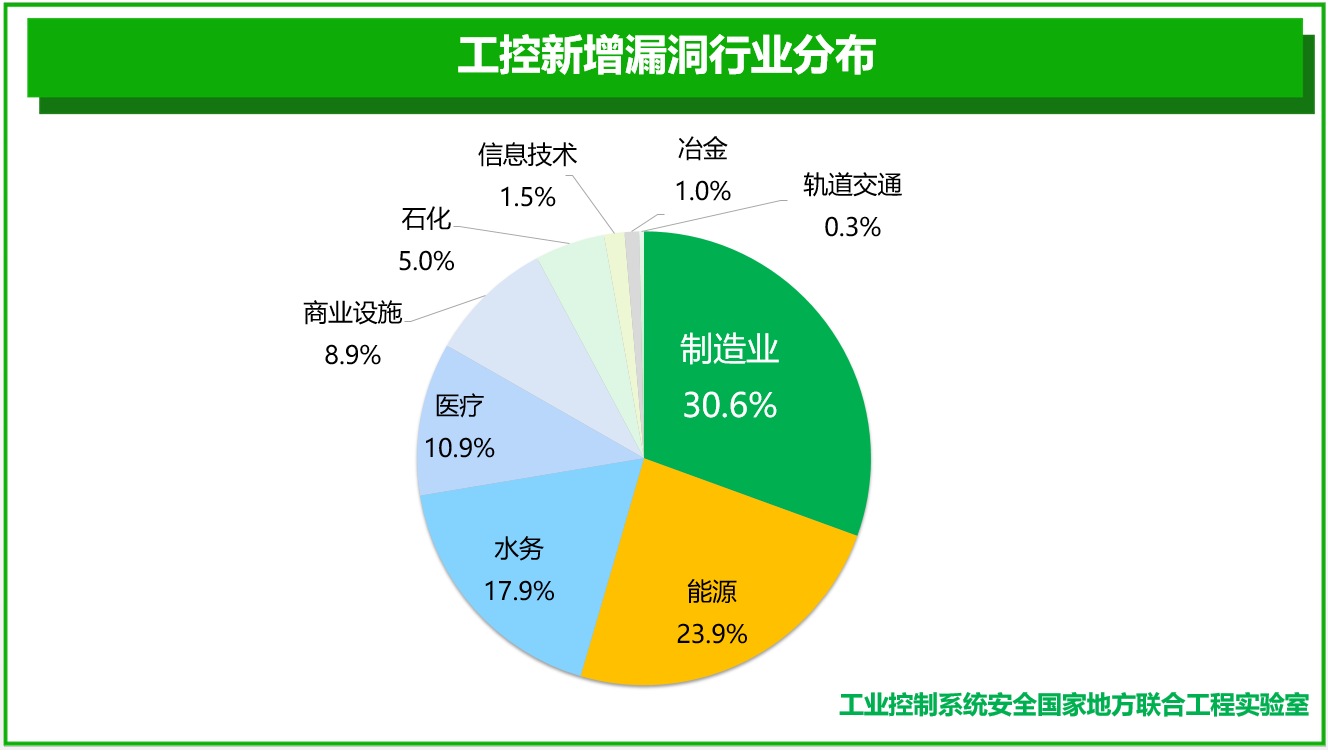
Most of the industrial control system security vulnerabilities newly recorded by the four major platforms in 2018 are distributed in key infrastructure industries such as manufacturing, energy, water affairs, medical care, food, petrochemical, rail transit, metallurgy, municipal administration, and information technology. The manufacturing industry accounted for the highest proportion, and the number of related vulnerabilities involved reached 30.6%, breaking the situation that the energy industry has been ranked first in recent years, and the number of related vulnerabilities involved in the energy industry was 23.9%. The industry distribution map of vulnerabilities is as follows:
Summarize
For more content, click to visit the report on the github5.com website for further study
contact us
DB35-T 1764-2018 Technical conditions for metal roofing in coastal areas Fujian Province.pdf