2019-2020-1 20175325 "Information security system design basis" the third week of learning summary
First, the table of contents:
- Learning content: machine-level representation of the program
- Code debugging and problem solving in the process
- Last week, the wrong questions
- Code hosting
- PSP
Second, the learning content: machine-level representation of the program
- Assembly language is a language oriented processor, the machine instruction is a symbol.
- Use gcc compiler generate assembler code for:
gcc -Og -s xxx.c - View binary file disassembly code:
objump -d xxx.c - Run GCC compiler generates an assembler file code.s:
gcc -Og -S code.c - Use -c command option, GCC compiler and compile the code gets code.o:
gcc -c code.c - Generate an assembly file:
gcc -Og -S mstore.c - View the contents of the file that is disassembly:
objdump -d mstore.o - Processor Type:
- Program Counter:
(%rip)indicates the next instruction to be executed is the address in memory.- Integer registers: 16 contains the named location, 64-bit values are stored. Some used to record the status of certain documents, some used to store temporary data.
- Striped registers: an arithmetic or logic instructions stored in the latest execution state information.
- Floating point registers: can store one or more integers or floating point numbers.
- Calculation of the effective address:
Imm(Eb,Ei,s) = Imm + R[Eb] + R[Ei]*s Data transfer instructions
MOV:
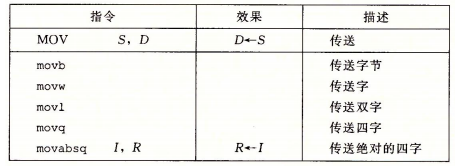
- Load effective address
leaqinstruction: actuallymovqinstruction modification Operand indicator:
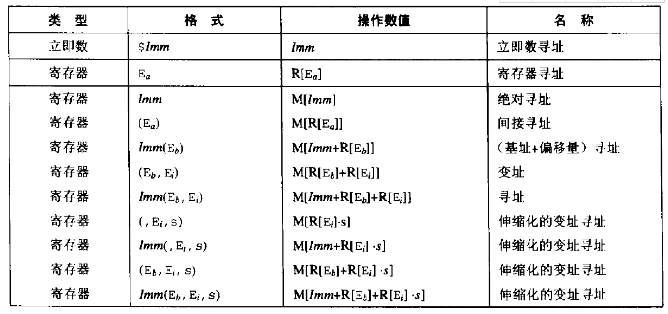
- Immediate (Imm): constant value indicates
$an integer expressed by a standard method C - Register: representing the contents of a register
R[ra] - Memory Quote: access to a memory location
Mb[Addr] Several special arithmetic operations:
- imulq signed a full multiplication
- mulq unsigned multiplication full
- clto converted to character
- Signed division idivq
- unsigned division divq
- Buffer overflow: buffer exceeds the capacity of the overflow data itself overlaid on a computer when the data valid bits to the data in the buffer is filled, the ideal situation is not allowed and the program checks the data length of the input character exceeds the buffer length, However, most programs will assume that the data length is always matched with the allocated storage space
- Push and pop the stack data:
pushq S: pressure Drawing
popq D: popped
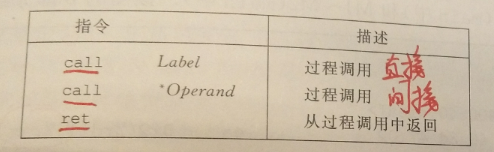
- Transfer control -
callandretcommands the general form:
Third, the problem of debugging the code and resolution
- Problems and Solutions:

Fourth, the wrong question last week:
A wrong question:
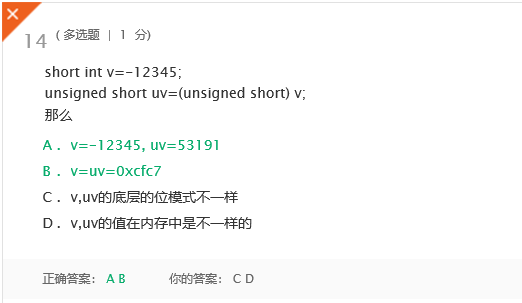
Answer:
P49, have converted in line with the number and unsigned, the value of different bit patterns change, to in-depth understanding of the "information bits = + context."Wrong question two:
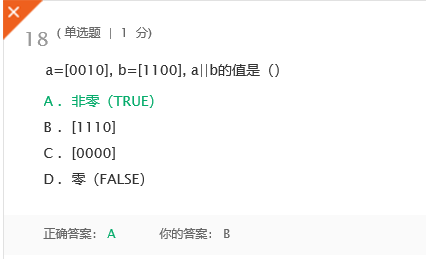
Answer:
P39 distinction bit arithmetic and logical operations.
V. code hosting:
Six, PSP:
| ——---- | The number of lines of code | Blog quantity | |
|---|---|---|---|
| aims | 5000 | 25 | 400 hours |
| The third week | 198/228 | 2/3 | 12/20 |