 Written in front: video address
Written in front: video address
Successfully landed 360! 0 basic network security entry to entry yu, vulnerability mining - external network penetration testing process
Table of contents
4. Frequently asked questions about interviews
5. Penetration testing process
4. Vulnerabilities exploited to obtain webshell
1. Introduction:
Exploring the Cutting Edge of Technology - Offensive and Defense Weapons Laboratory
"Go through the external network penetration testing process"
do we count as family

2. Summary:
Work summary/ SUMMARY
| Extranet penetration testing process | involving experiments |
| Determine the target |
Experiment 1-7 |
| collect message | Experiment 8-12 |
| Vulnerability mining | Experiment 13 |
| Vulnerability utilization ---> get webshell | Experiment 14 |
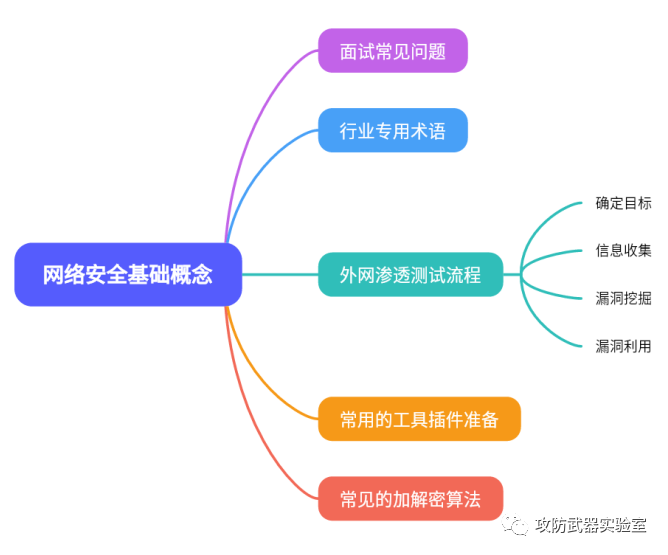
3. Knowledge map
4. Frequently asked questions about interviews
1. What is the basic idea of external network penetration testing?
Determine the attack target--->information collection--->vulnerability mining--->vulnerability utilization--->obtain webshell
(Expand and introduce each item)
2. How do you usually dig out the loopholes?
Supplier--->Developer's official website--->Case
target ---> all testable sites for that target
Reproduce known vulnerabilities ---> determine the characteristics of vulnerable sites ---> look for sites with the same characteristics
code audit
(Expand each item in detail, and explain some experiences + cases)
3. What are the methods to obtain website permissions?
Use the file upload vulnerability to upload the webshell, obtain administrator privileges, and then use various background functions to write the webshell in the background, use xpcmd to produce webshells, database compression functions, webshell files and databases with modified suffixes through database backup or modification functions Command execution, middleware vulnerabilities, etc.




5. Penetration testing process
1. Brief description:
Cybersecurity Law of the People's Republic of China_Baidu Encyclopedia (baidu.com)
According to the "Network Security Law of the People's Republic of China", it is necessary to obtain the authorization of the customer to conduct a penetration test on a website, and it is illegal to perform a penetration test on a website without authorization.
A flow chart to show you what is often referred to as digging --- the so-called external network penetration test
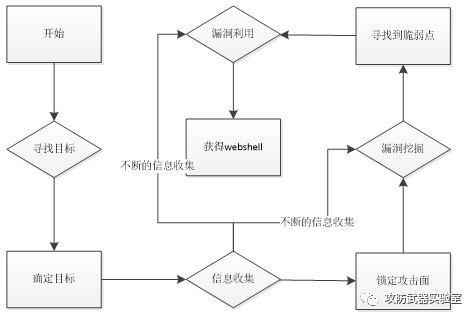
Does the general process seem particularly simple? There are only four simple steps to get a website’s webshell (that is, administrator privileges), but each step requires us to understand the detailed operation method.
We will explain in detail the steps of finding targets, collecting information, exploiting vulnerabilities, and obtaining webshells by exploiting vulnerabilities. This video at the end of the course will lead you to understand the specific process of digging holes, that is, the so-called external network penetration test. what does it look like
Determine the target--->information collection--->vulnerability mining--->vulnerability utilization--->obtain webshell
2. Find the test target
1. Find the test target
Black box test ---- simulate the scene of hacker attack (that is, don't know anything)
1. Start with the supplier of the product:
Supplier--->Case
By looking for these manufacturers that provide products, development and other services, and then looking for relevant product use cases on their official websites, then collecting these cases, testing these cases, and finding loopholes in a certain place, other products may also be If the same vulnerability exists, it can be run as a vulnerability poc
Experiment 1 :
Next, we will find a few service providers, and we will simply go in and see how their products are. We will not do any unauthorized testing and attacks here. It is emphasized that personal attacks and tests have nothing to do with the conclusion of this lesson.
(Note: here is only a simple demonstration of the function, without further actual testing and attack)
You can check which developers are available on edusrc (edusrc general education, products and solutions for government use)
https://src.sjtu.edu.cn/rank/company/
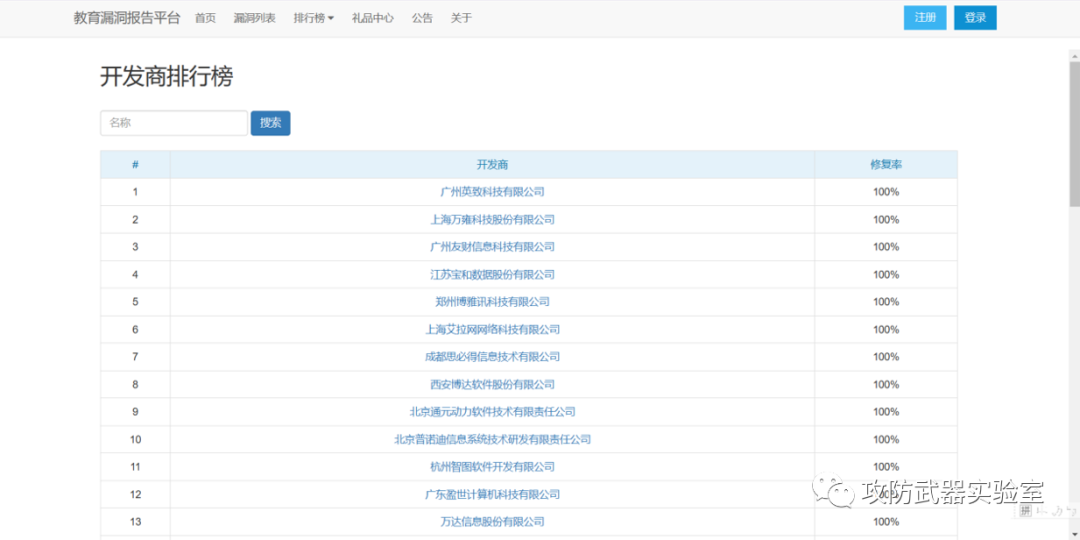
Then go to the official website of the developer to find the corresponding product case

2. Start with a single goal:
target ---> all testable sites for that target
1) same unit
Sometimes, we will conduct an authorized test for an enterprise or a certain unit. At this time, we need to collect more asset targets (such as websites, applets, apps, etc.) of this enterprise or unit to provide us with test Greater test coverage
Experiment 2 :
Determine the target ---> lock the attack surface of the target asset
(Note: here is only a simple demonstration of the function, without further actual testing and attack)
We randomly determine a target, and then conduct a deep search, the assets, information, etc. of this target unit.
2) Different units
Experiment 3 :
Determine the characteristics of vulnerable sites ---> look for sites with the same characteristics
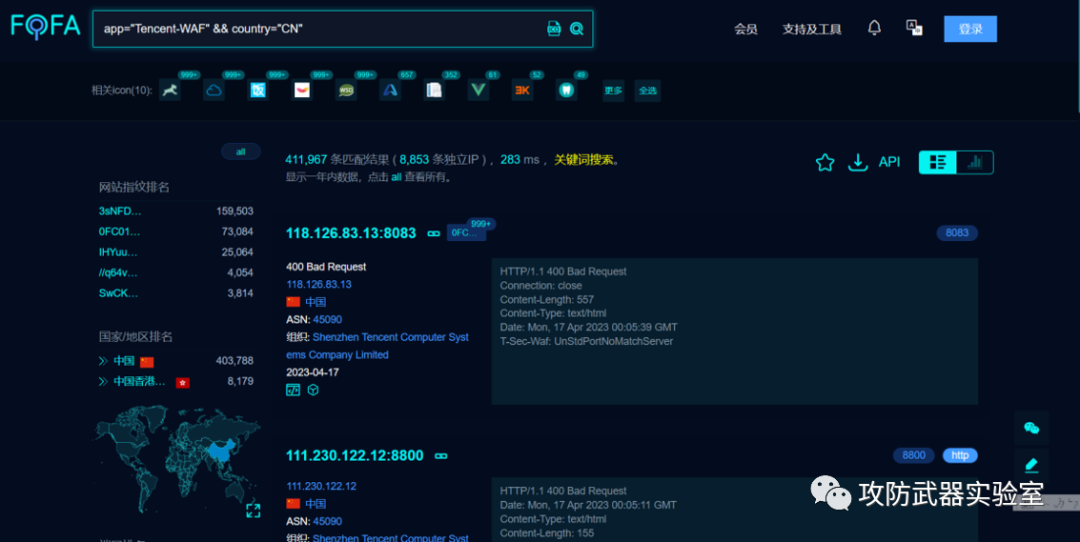
We can use Ctrl+U to view the source code of the front-end of the vulnerable site, and then find a few more useful features, such as some referenced paths, etc. Here we take the same path as an example
Then use platforms such as FOFA to search for sites with the same characteristics (it should be noted that the differences in the searched sites will vary greatly if the searched features are different, and this method requires a lot of testing)
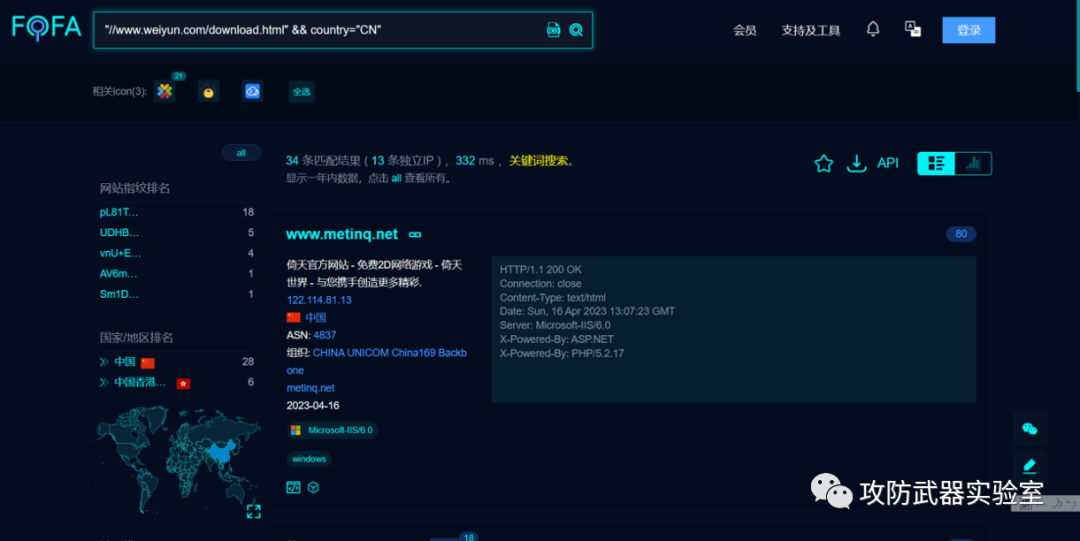
——————————
3. Start with vulnerable middleware:
1) Look for known vulnerabilities
When we discover the middleware used by a website, we can check whether the middleware is vulnerable
Experiment 4 :
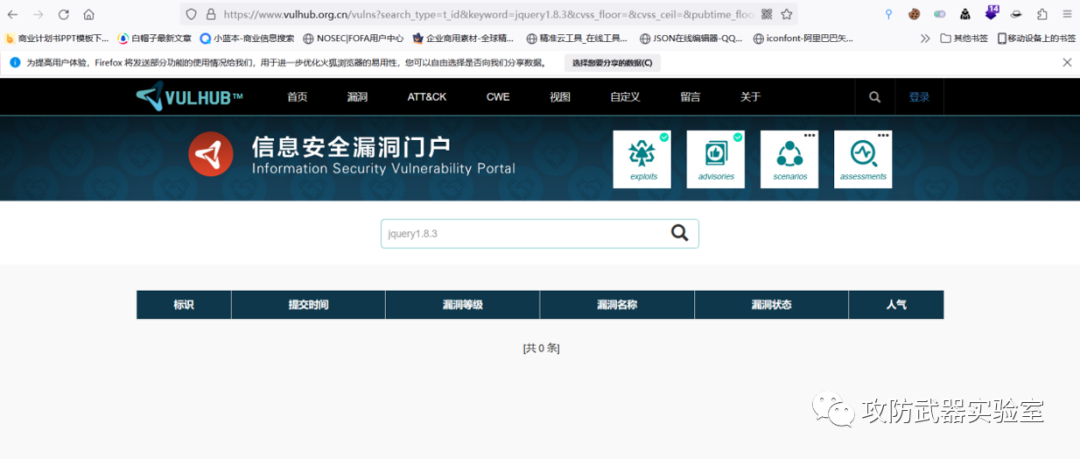
By using a scanner, or a plug-in, you can see that the jquery used is version 1.8.3
(Note: No scanners, or other testing techniques that compromise product safety)
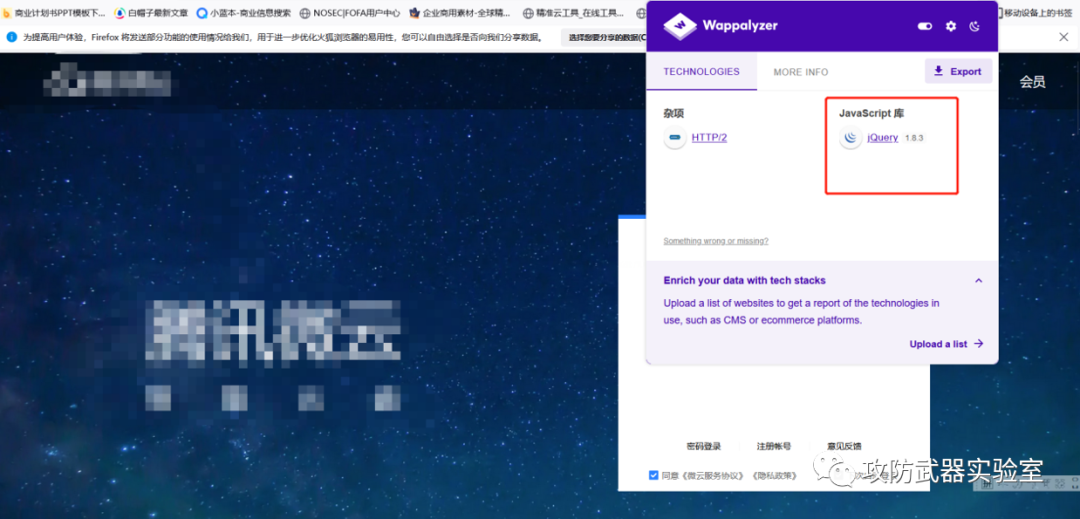
Then we can find out whether there is a corresponding version of the vulnerability on the Internet or on the vulnerability platform.
https://www.cnvd.org.cn/flaw/list?flag=true
https://avd.aliyun.com/search?q=jquery1.8.3
https://www.vulhub.org.cn/vulns?search_type=t_id&keyword=jquery1.8.3&cvss_floor=&cvss_ceil=&pubtime_floor=&pubtime_ceil=
2) Test the corresponding version through known version vulnerabilities
Experiment 5 :
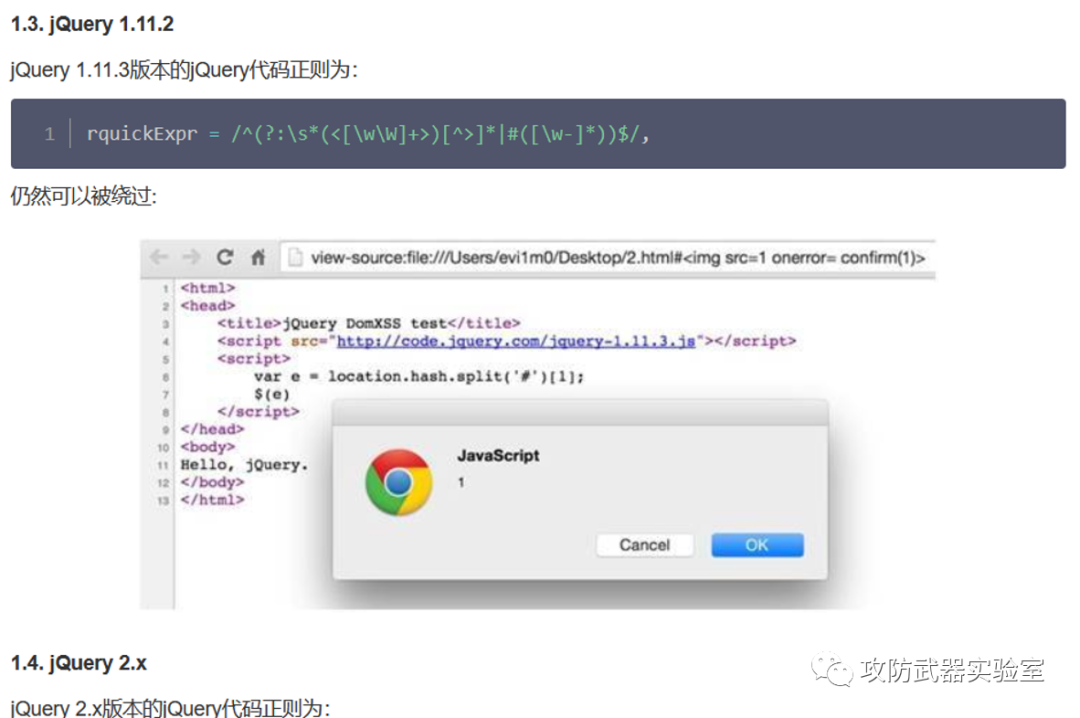
Next, let's take jQuery as an example,
jQuery is a JavaScript library, and JavaScript is often used for xss, resulting in XSS cross-site vulnerabilities
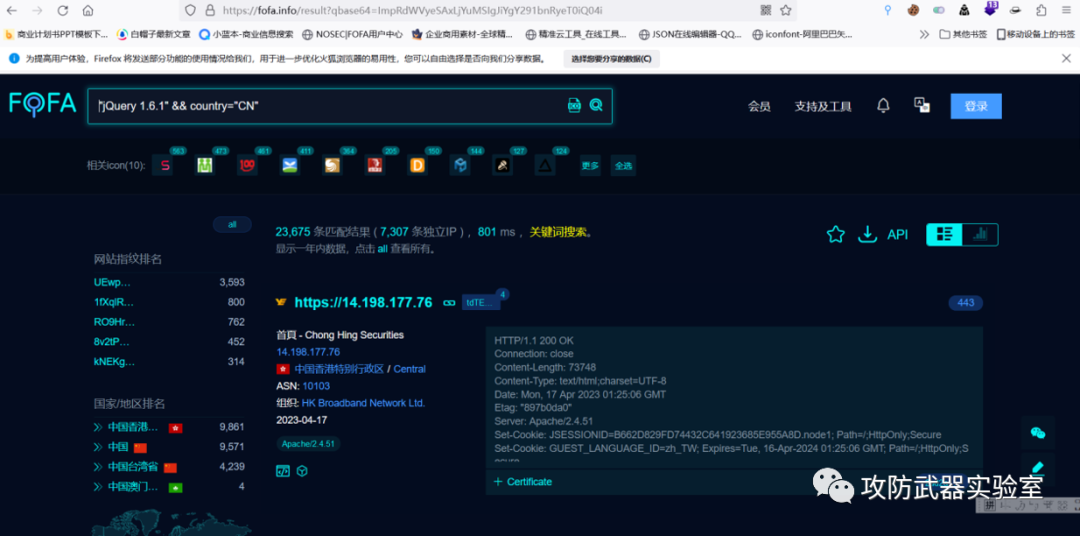
By finding the poc of the corresponding version, batch test the corresponding version
(Note: here is only a simple demonstration of the function, without further actual testing and attack)
You can find a large number of corresponding versions for testing
——————————
White box testing --- mining vulnerabilities in the case of known source code and its logical structure
3. Code Audit
White box testing is a test case design method. The box refers to the software under test. White box means that the box is visible. You know what is inside the box and how it works. The "white box" method fully understands the internal logical structure of the program and tests all logical paths.
In network security, white box testing, the things inside the box are equivalent to complete code + logical structure
By testing the logical structure of each code to find so-called program defects, or methods to bypass program protection, etc.
1) Front-end code
Experiment 6 :
Let’s find a site at random. Some people say that checking the source code of the page is a code audit. The source code here belongs to the source code of the client. Some vulnerabilities may be caused by client vulnerabilities. window. Generally, logic processing is carried out at the back end, but it does not rule out that there will be filtering and other processing at the front end.
(Note: here is only a simple demonstration of the function, without further actual testing and attack)
F12、Ctrl+Shift+I
(It can be dynamically debugged)
For example, search for some functions that may trigger vulnerabilities
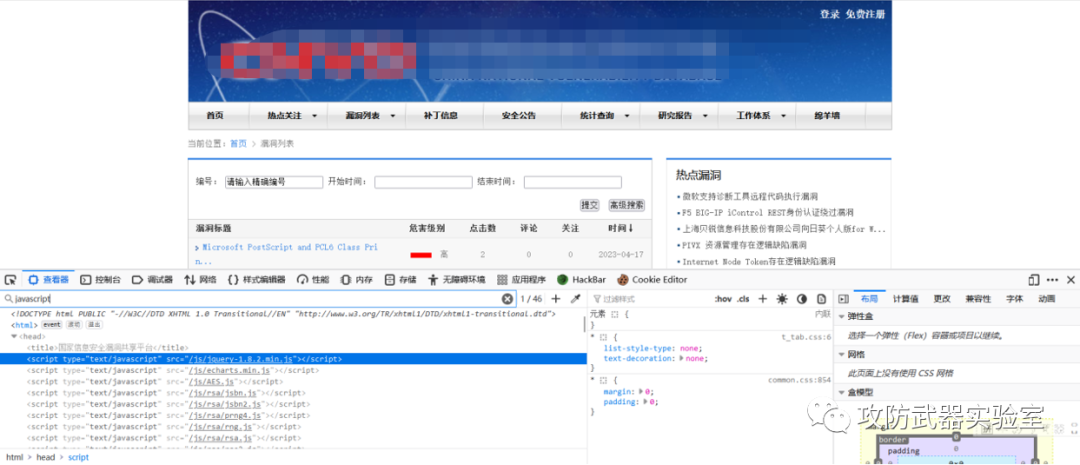
Ctrl+U
(static code)
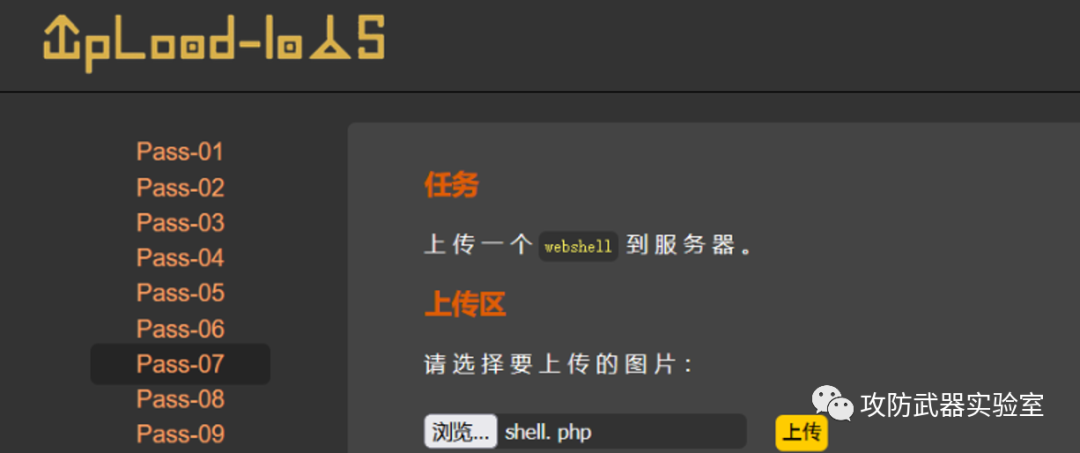
Experiment 7 :
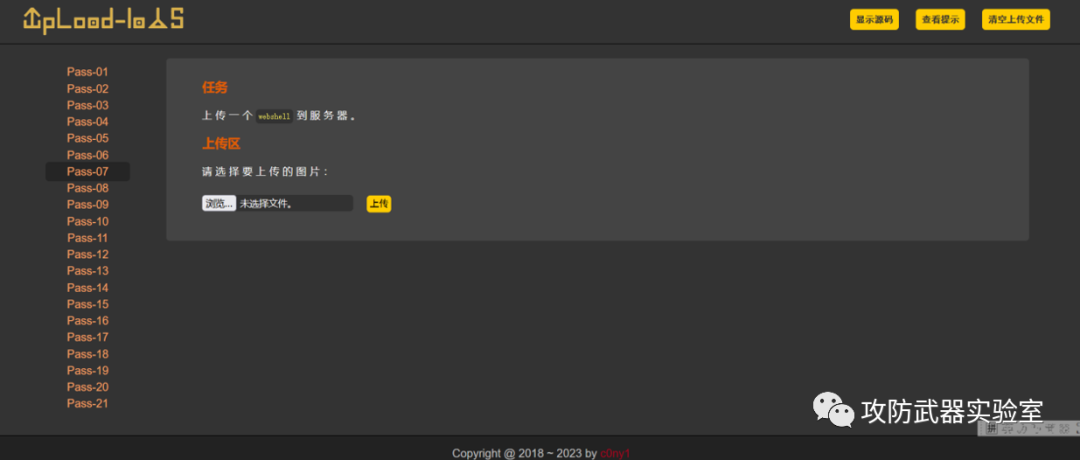
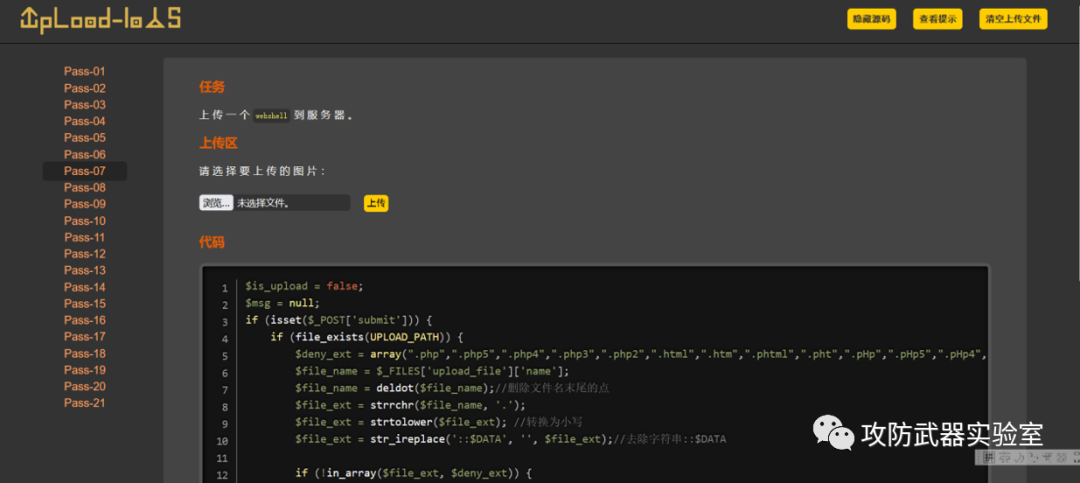
Take the upload-labs shooting range as an example here. At this time, on the interface, we will prompt that the upload failed. This is a black-box test. After the source code is displayed, it is a white-box test. The source code here is the code for logical processing.
By analyzing the code, it can be found that the code will filter the related suffixes uploaded, and the specified suffixes cannot be uploaded successfully.
black box:
White box:
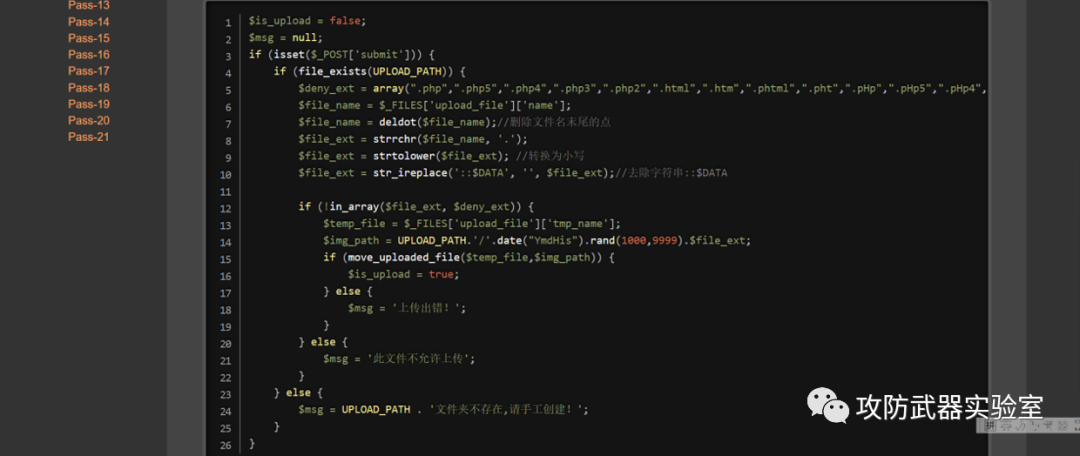
This is a very simple and clear code, it can be seen that it includes blacklist processing of uploaded files (array
blacklist list contained in the array), processing of uploaded files (as indicated in comments)
https://blog.csdn.net/qq_53079406/article/details/125846616
No whitespace, bypass blacklist


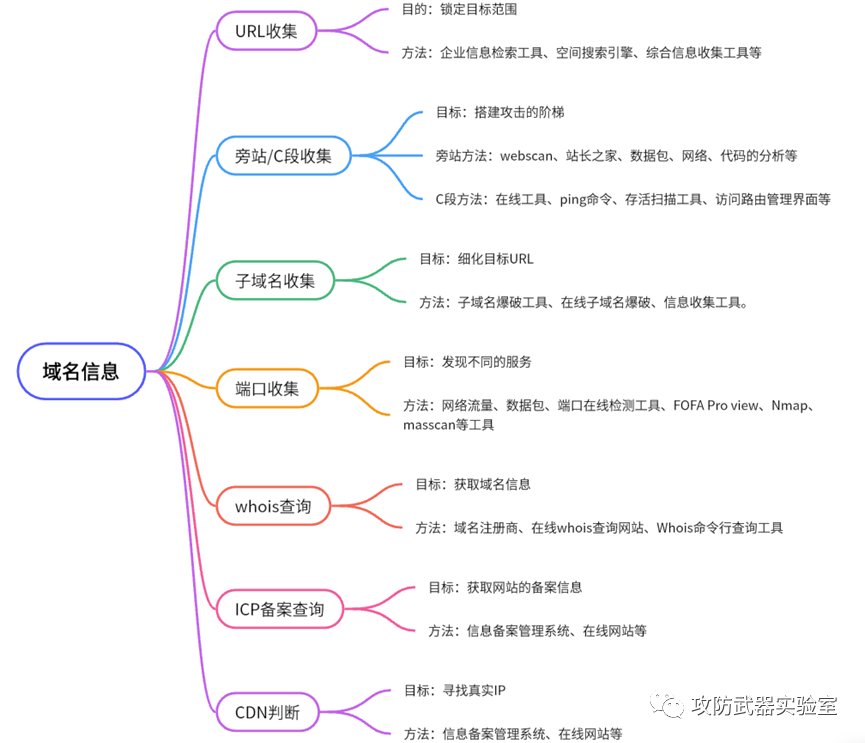
3. Information collection
1) Basic information collection
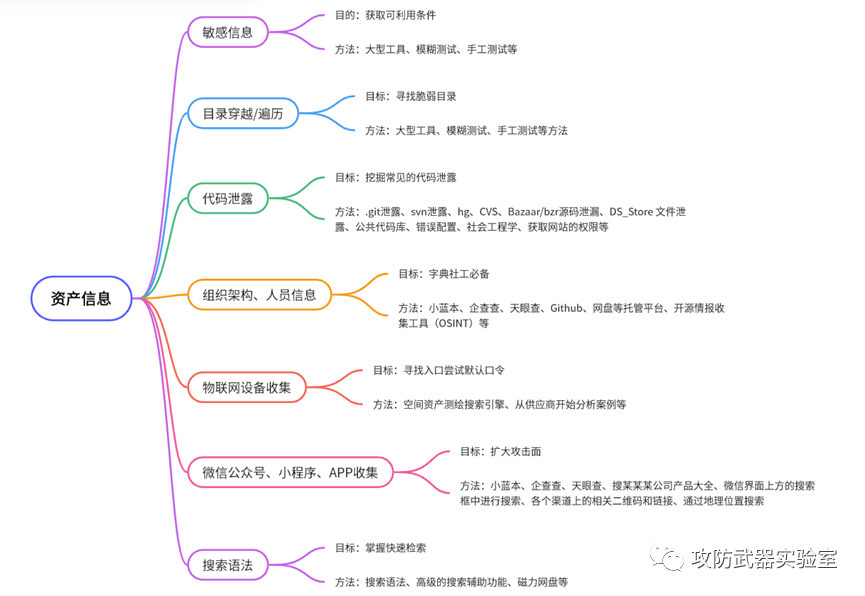
The purpose of information collection ---> expand the attack surface + obtain the available conditions
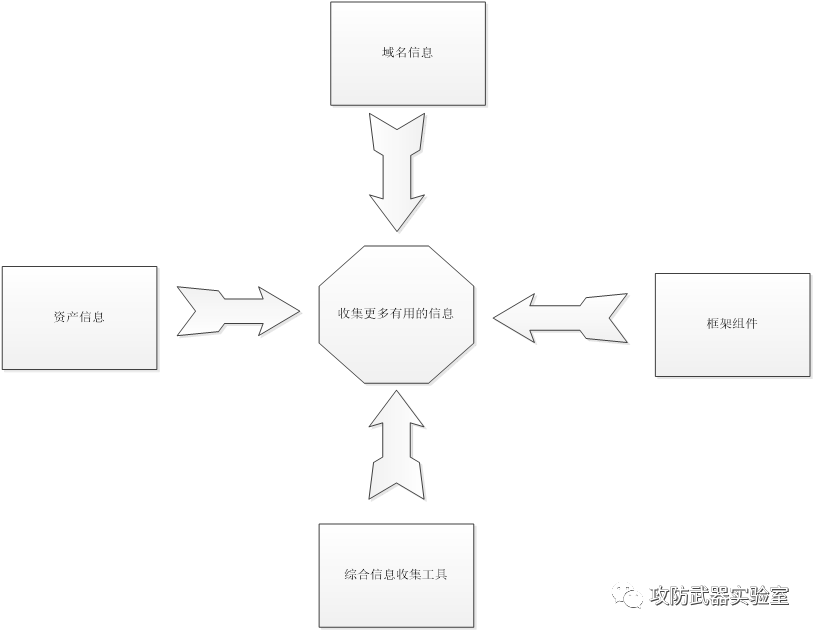
By collecting the information shown in the figure + more other information, the complete puzzle of a test target is completed
After determining the target of the test, collect information on the target, including some common collection methods, such as collecting relevant information such as the target's assets, so as to expand the level of attack (such as websites, small programs, apps, etc. various assets that can be tested).
There is also a collection of domain name information, we can get a registration information, email, port service, etc. that need to test the site and more useful information
Sometimes, we need to collect the relevant component architecture and third-party plug-ins of the site, and look for breakthrough points that can be used.
In the process of information collection, we need to use a large number of tools for testing to obtain the maximum amount of information. At the same time, we will also use some comprehensive information collection tools, such as Lighthouse, Mizusawa, Goby, etc.
——————————
——————————
1) Collection of specific information
Experiment 8:
In the process of testing, we also need to understand the meaning + logic process represented by each parameter, so that we can fully understand the entire business logic
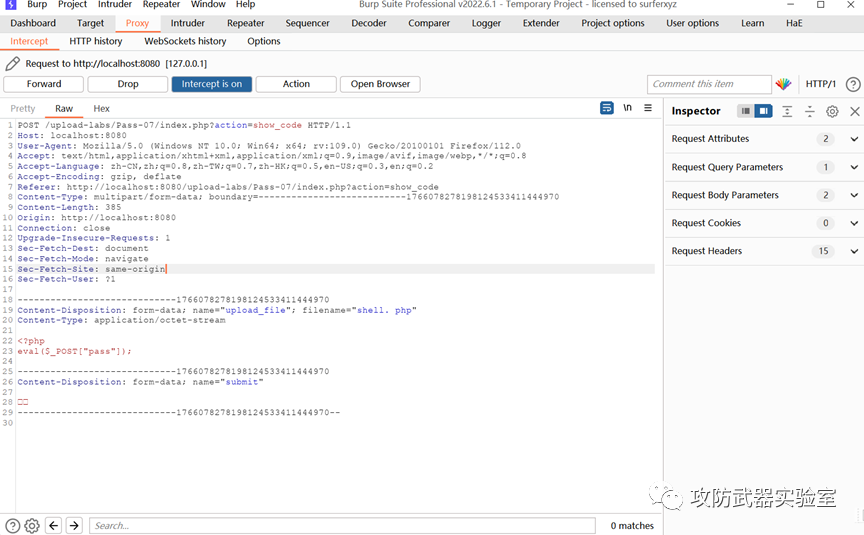
In actual situation
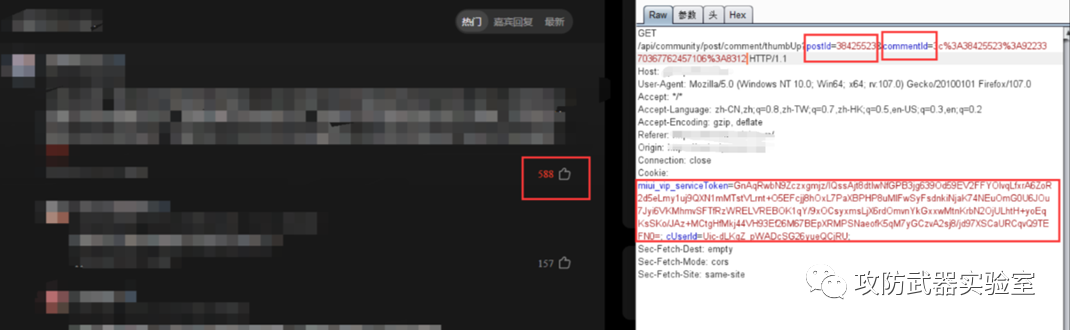
Next, we friendly intercept a request packet and watch its packet
(Note: No tests and attacks have been carried out)
——————————
——————————
2) Basic information collection
1. Domain name information collection:
For the collection of domain name-related information, such as the collection of URLs: in order to lock the target range, ... (content on the knowledge map)
Information collection is an important step in continuously improving information acquisition throughout the attack testing process. In each further test, we will obtain more information that is beneficial to our understanding of the target.
Experiment 9 :
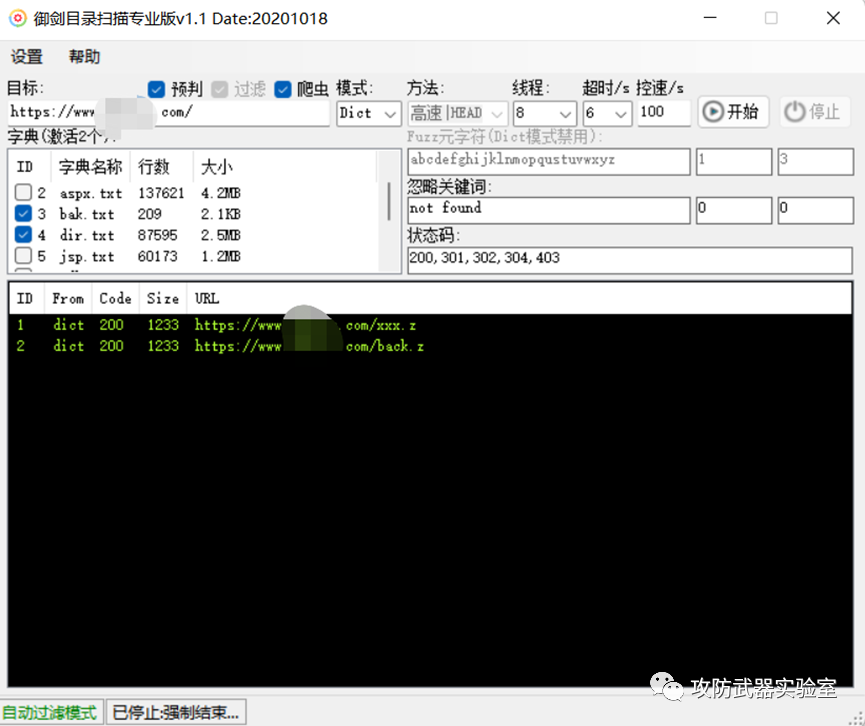
Yujian directory blasting tool, collect more URLs, thereby expanding the attack surface
(Note: here is only a simple demonstration of the function, without further actual testing and attack)
Find an enterprise src (in the spirit of contributing to the development of the enterprise, no direct malicious attacks and tests)
Open and make a simple configuration
Enter target URL
start digging
——————————
——————————
2. Collection of asset information:
For the collection of asset information, such as sensitive information: we can obtain some favorable conditions that can be used, ... (as shown in the knowledge map).
Experiment 10 :
Next, let’s take an example of a common platform for code leakage. On Github and other hosting platforms, we can obtain a lot of code source programs, and these codes may be taken by the website as part of the logic code segment. Using github, we may also search for a lot of useful information, such as searching for some sensitive information.
(Note: here is only a simple demonstration of the function, without further actual testing and attack)
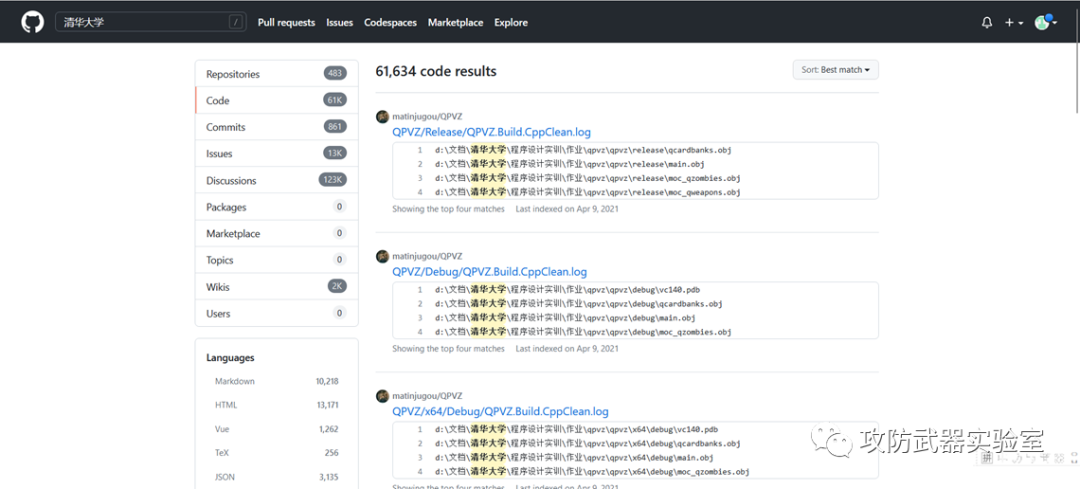
Repositories repository
code code
CommitsSubmit
Issues
DiscussionsDiscussions
Package package
Marketpalce market
Topics
Wikis
Users
LanguageLanguage
As you can imagine, we can not only search for sensitive code segments on the code hosting platform, but also search for some sensitive data, such as student ID, name, etc.
——————————
——————————
3. Frame components:
For the collection of framework components, such as the server operating system: through the type of website operating system we obtained, we can use specific commands and targeted vulnerability detection, ... (as shown in the knowledge map).
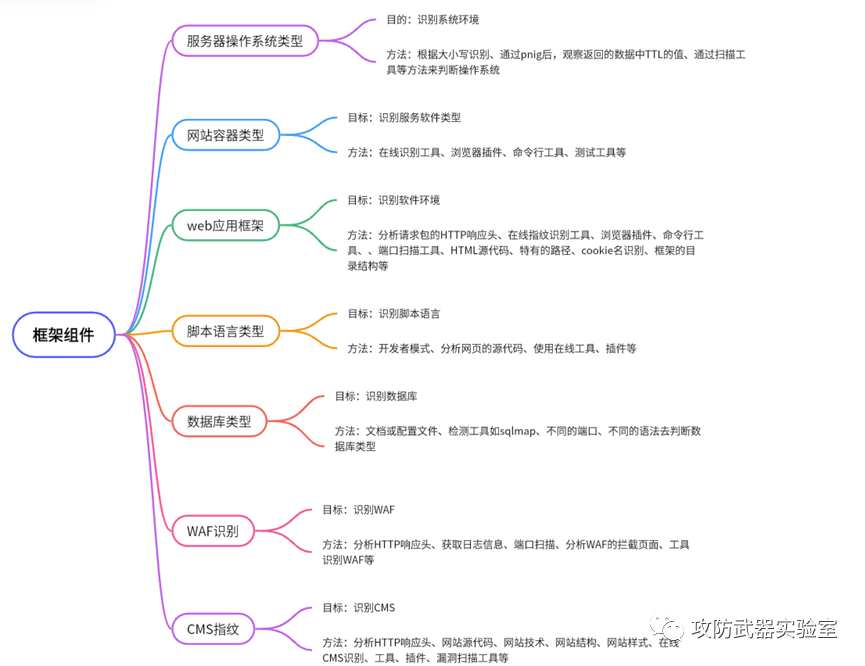
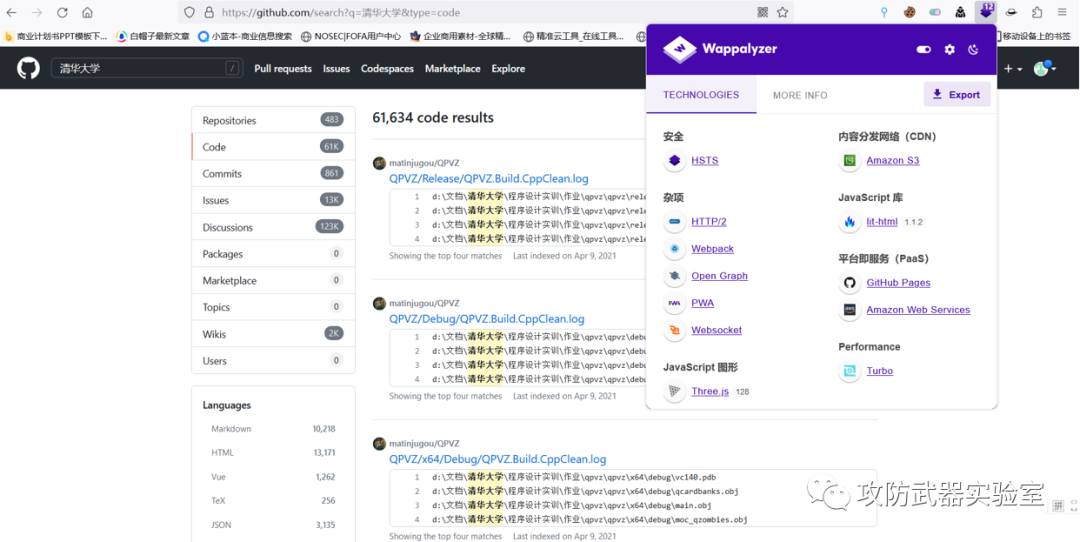
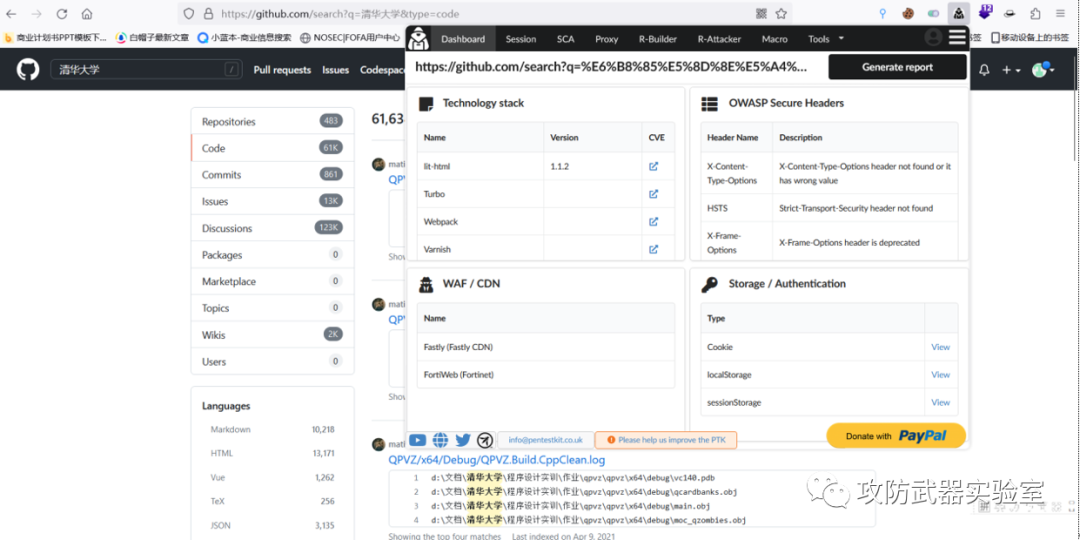
Experiment 11 :
Use some commonly used browser plug-ins and detection tools to detect the framework and language of the site
(Note: here is only a simple demonstration of the function, without further actual testing and attack)
Wappalyzer
Owasp penetration Testing Kit
——————————
——————————
4. Comprehensive information collection:
After we use some single information collection tools and manual testing, we need to use some comprehensive information collection tools to collect information in all aspects, and may have a built-in vulnerability detection function.
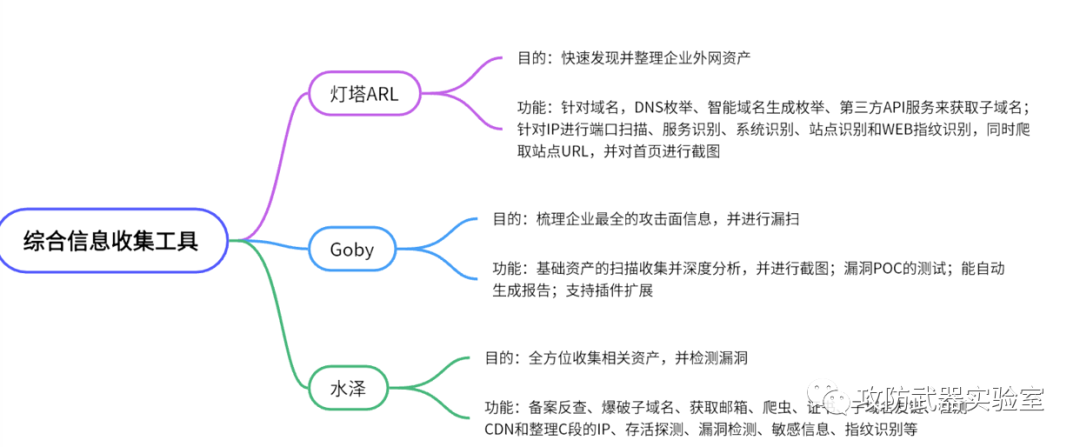
Experiment 12 :
Next, let's briefly demonstrate (in the information collection chapter, we will describe in detail, the collection method, tool usage and other detailed operations, here we will conduct a simple simulation test), the lighthouse asset collection tool, installed in On the kali virtual machine, after passing the relevant settings, we can collect some asset information in a targeted manner
(Note: here is only a simple demonstration of the function, without further actual testing and attack)
Lighthouses can be used for information gathering

3. Vulnerability mining
3. Vulnerability mining
After we have identified the target assets and collected as much information as possible, we need to dig out the vulnerabilities of the attack surface we collected, and we need possible breakthrough points
(In the vulnerability chapter later, we will explain each vulnerability. Here, we will only explain a process of external network penetration testing)
SQL injection vulnerability
XXE Vulnerability Vulnerabilities
command injection vulnerability
Remote Code Execution Vulnerabilities
Directory Traversal Vulnerability
Information Disclosure Vulnerabilities
Access Control Vulnerabilities
Authentication Vulnerabilities
File Upload Vulnerability
File Parsing Vulnerabilities
SSRF server request forgery
Business Logic Vulnerabilities
XSS Cross Site Scripting Vulnerability
CSRF cross-site request forgery
CORS cross domain resource sharing vulnerability
Clickjacking vulnerability
WebSockets Vulnerability
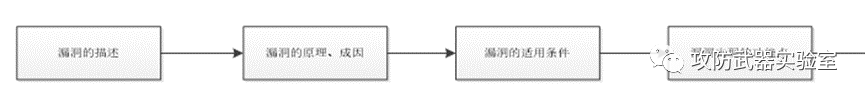

Later, we will learn the detailed principles, causes, applicable conditions, detection methods, utilization methods, etc. of each vulnerability.
Experiment 13 :
Here we take the sql injection vulnerability of a simple BP training ground as an example to explain a vulnerability mining process
SQL injection vulnerability
Targeted detection of SQL injection vulnerabilities is nothing more than detecting whether there is an injection point
Unauthorized access to sensitive data
1. Retrieve hidden data where you modify the SQL query to return additional results.
2. Subversion of application logic, where queries are changed to interfere with the logic of the application.
3. UNION attack, in which data is retrieved from different database tables.
4. Examine the database, where it extracts information about the database version and structure.
5. Blind SQL injection, controlled query results will not be returned in the application's response
First of all, we enter the college ---> learning path ---> sql injection vulnerability ---> enter the laboratory
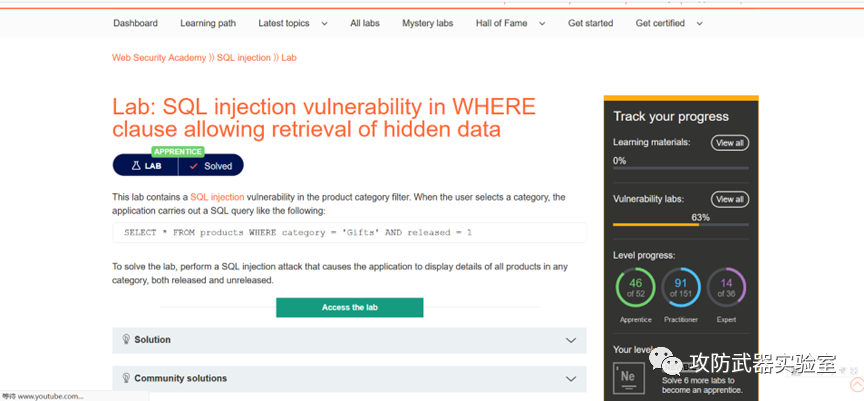
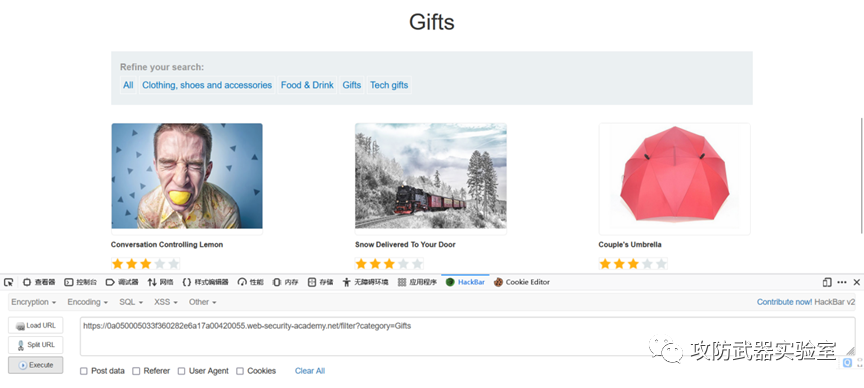
This is to control the classification according to the filter, and then perform a data retrieval
filter:
https://0a050005033f360282e6a17a00420055.web-security-academy.net/filter?category=Gifts
Entering a single quotation mark reports an error, indicating that the single quotation mark is brought into the database syntax for execution, so there is an injection point
The logic behind the comment:
Adjust the content comment behind the category, and a new product appears, indicating that there is another parameter to control whether the product is hidden or public
https://0a050005033f360282e6a17a00420055.web-security-academy.net/filter?category=Gifts'--
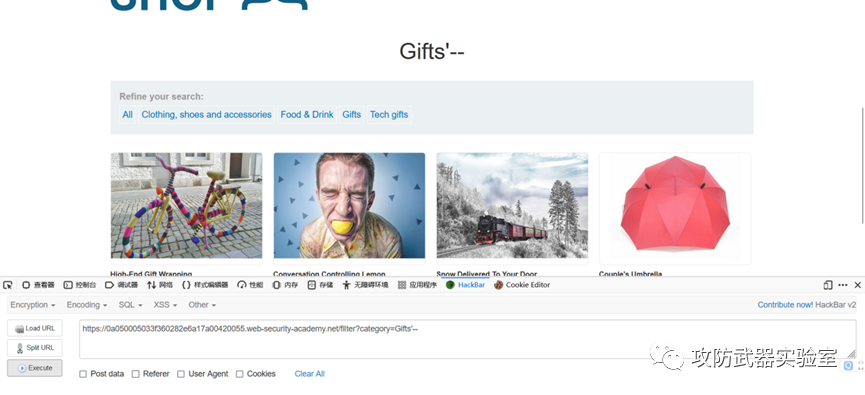
Get data using:
Use OR connectives, as long as one of them is established, all data will be returned, and adding 1=1 after or is always established
https://0a050005033f360282e6a17a00420055.web-security-academy.net/filter?category=Gifts'+or+1=1--
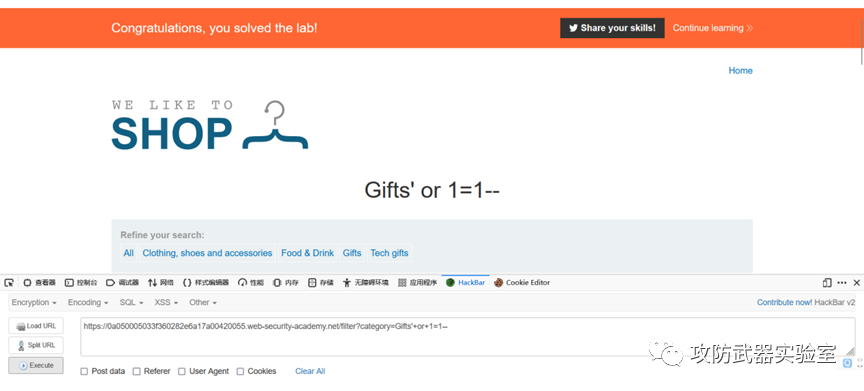
4. Vulnerabilities exploited to obtain webshell
4. Vulnerabilities exploited to obtain webshell
Vulnerabilities are divided into low-risk, medium-risk, high-risk, and serious, because depending on the degree of harm, the harm and quantity of information that may be obtained, as well as permissions, etc., will lead to different degrees of harm of the vulnerability.
Such as the common file upload vulnerability, through the file upload vulnerability, a Trojan horse file is parsed and executed, and then the control authority of the website is obtained through the connection
There are other methods such as: obtaining administrator privileges, uploading or writing or decompressing webshell code files through background functions, using xpcmd to generate webshells, database compression functions, database backup or modification functions, is a renamed webshell The file becomes the webshell executable suffix again, the database command is executed to write, and some middleware vulnerabilities are exploited, etc.
Experiment 14 :
File upload vulnerability, through the file upload function, upload the Trojan horse code file, and then use tools to connect to the Trojan horse code file, so as to obtain the management authority of the website (ie webshell)
By uploading the Trojan horse backdoor to the server of the other party, and analyzing and executing
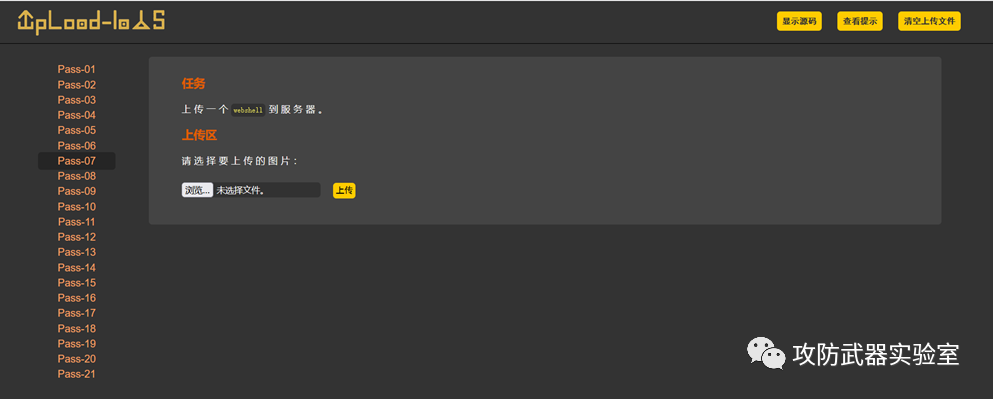
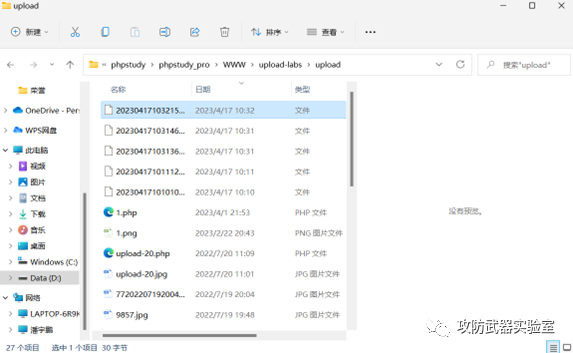
Then connect through the backdoor tool to achieve a site management authority
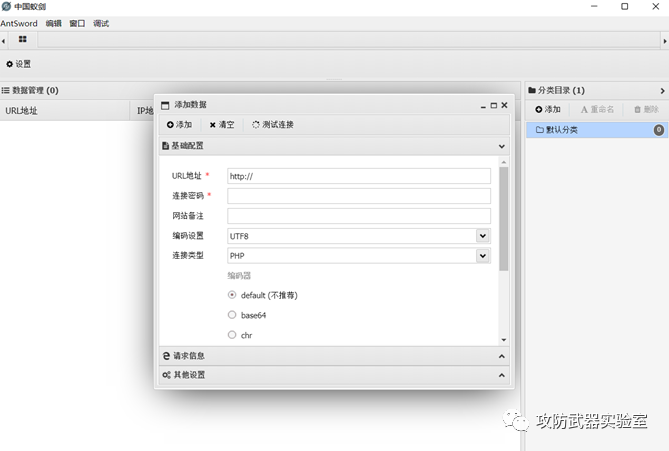
There are many ways to obtain the webshell of the site. You can first obtain more execution permissions by obtaining administrator privileges, and then write and import the webshell code file.
Access control loopholes (such as unauthorized access to an administrator's operation page, or bypassing the authentication of permissions, thereby possessing administrator permissions)
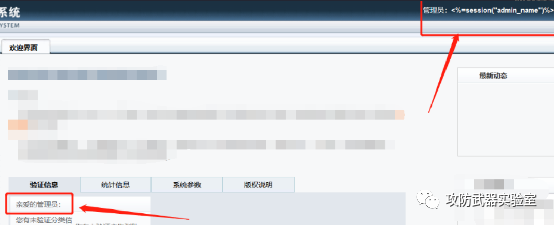
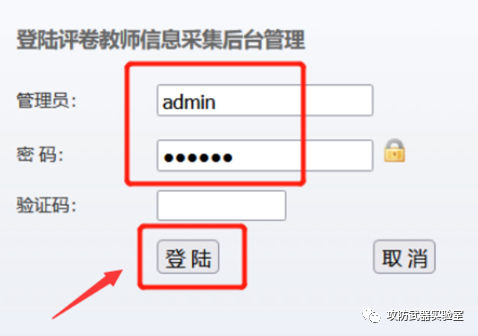
Weak password (if there is a weak password in the administrator account, you can test more function points with higher authority)
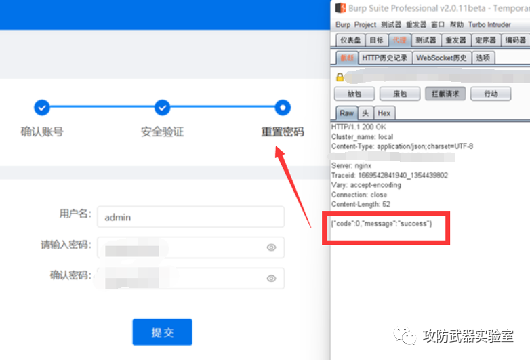
Password reset (reset the administrator's password, or jump directly to get more interfaces after reset, so as to have more test conditions)
There are more ways to get the webshell of the website, so I won’t explain them in detail here.