With the popularity of Internet technology is growing, business computers, servers, network security requirements have become more sophisticated, it appears penetration testing technology is particularly important. Penetration testing is the process of assessing the security of user information. By operating and systematic analysis, found that active defects and weaknesses of various systems and networks that exist, such as design flaws and technical defects, operating system vulnerabilities are not patched in a timely manner, it will be exploited by attackers to seize control of the system, which If the case appeared on the enterprise server, the loss will be immeasurable. This also shows that penetration testing is a double-edged sword, is in the hands of an attacker hacking tools, the network administrator is the detection tool. I still hope that we take advantage of this penetration technology to work better. We start to understand some basic concepts penetration.
Penetration testing and no standard definition. Some foreign security organizations to reach a consensus of common parlance, penetration testing is simulated attacks by malicious hackers to evaluate a method for computer network security systems, this process includes an active analysis of the system any weaknesses, technical flaws, vulnerabilities.
Penetration testing and other evaluation methods are different. The usual assessment method is based on the known information resources or other objects to be evaluated, to find all the relevant security issues.
Penetration testing is based on the known security vulnerabilities available, to find out whether there is a corresponding information resources. In comparison, typically have a more comprehensive assessment methods for assessment, penetration testing and pay more attention to the severity of security vulnerabilities.
Penetration testing and black box testing and white box has two methods:
Black box testing: refers to tests carried out in the knowledge of the infrastructure;
White-box testing: refers to tests carried out in full knowledge of the structure.
Penetration testing usually has two particularly significant features:
penetration testing is a progressive and gradual deepening of the process;
penetration test is to select the test does not affect the normal operation of the business system attacks carried out.
Mainly used for penetration testing scenarios:
1. Corporate website and there is leakage of confidential information, user data leakage concerns;
2. User completion of the development of the new platform requires on-line;
3. the development process, the system requires local safety testing;
4. The presence of business systems business logic issue transactions such as financial systems.
We come to know several common penetration testing system:
kali Linux referred to as Kali, is the most popular penetration testing system, high frequency update its tool, using a wide platform, is the most common and advanced penetration testing tools release of the operating system.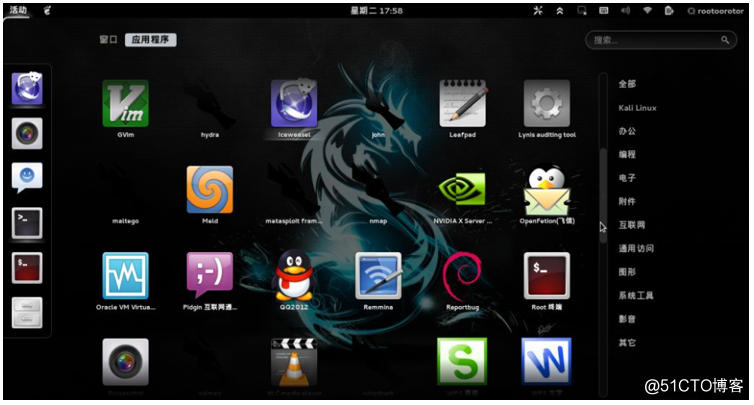
BackBox Linux -based Ubuntu distribution, developed network penetration testing and security assessment for power of this issue is that it's Launchpad, it has its own depot, the warehouse is always synchronized to the latest version of the tool.
Parrot security OS in addition to containing the test and programming tools outside, Parrot release is a stable operating system, which is based on Debian 9 includes a custom version of the Linux 4.6 kernel reinforcement, look beautiful and powerful. Parrot Kali use the library, but it also has its own custom store all data in the private library.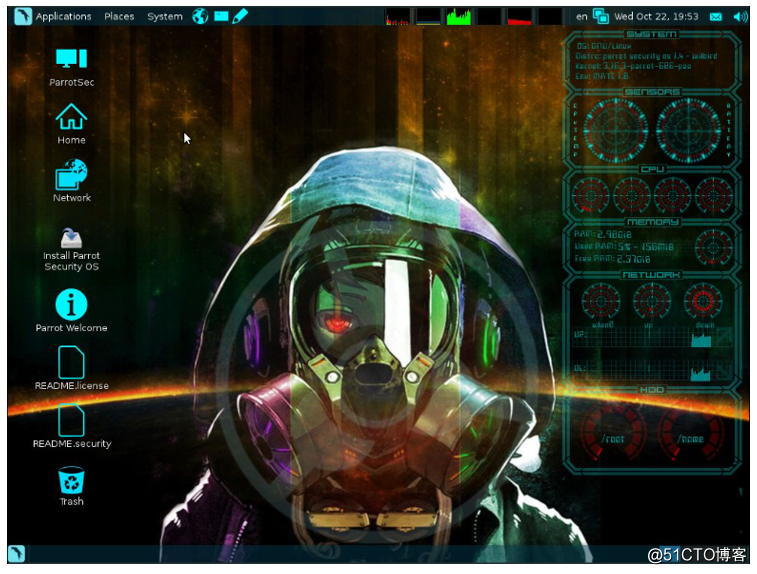
Linux DEFT DEFT also known as digital evidence and forensic toolbox is a custom XUbuntu from the start to run Linux. It is a set of easy-to-use system, including excellent hardware detection tool, as well as some open source software applications designed for emergency response and computer forensics.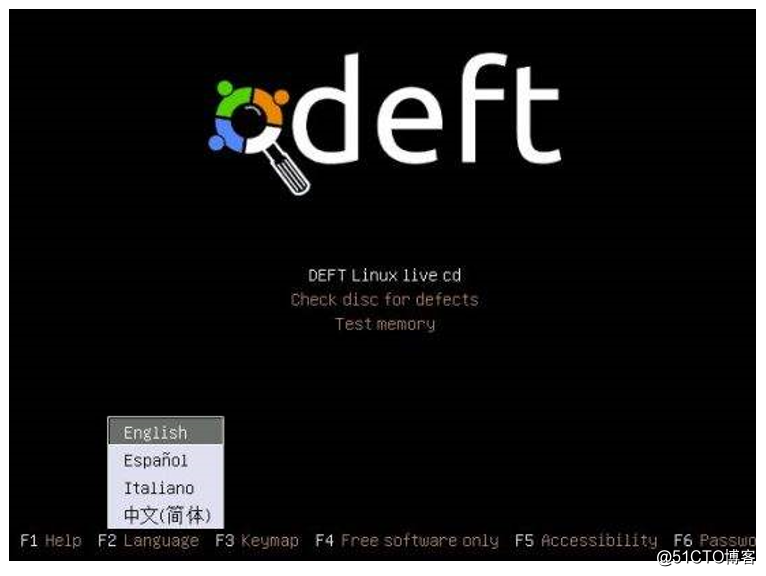
Live Hacking OS offers two modes, one mode is a complete Linux desktop, including the graphical user interface and easy to find start penetration tools menu; Another model is the mini mode, only the command line, so the hardware requirements are very less, this model demands on system memory is only 128MB.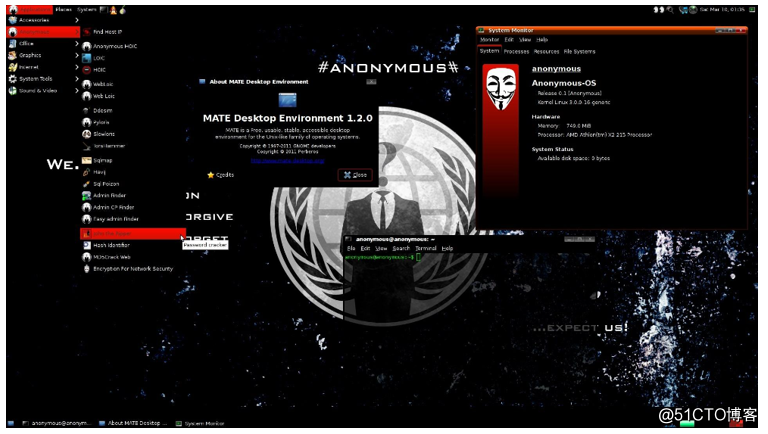
Cyborg Hawk是个基于Ubuntu的系统,Cyborg Hawk堪称是最完备的渗 透测试系统,其中包含了众多提供给白帽子黑 客使用的优秀工具。这套系统有700多种工具,还有很多针对移动安全和恶意软件分析的工具。但是,掌握其使用的难度也相对较大,系统使用的普及率也不如Kali Linux。
我们主要以Kali Linux为主,我们来认识Kail Linux,它的前身是Back Track Linux发行版,基于Debian的Linux发行版。它的特性主要有:
1.支持多语言多桌面环境;
2.兼容Debian工具;
3.支持ISO自定义;
4.支持多平台运行;
5.包含超多实用工具及全球最活跃社区。
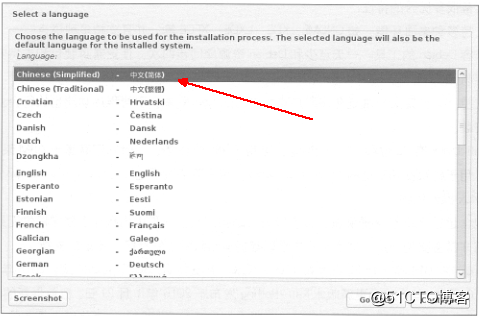
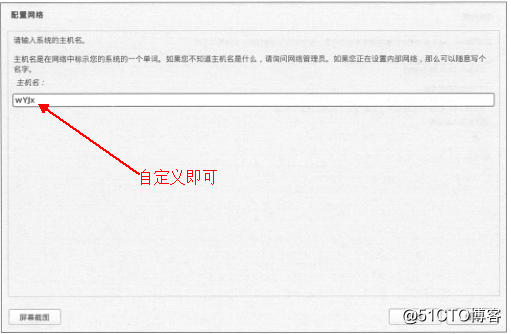
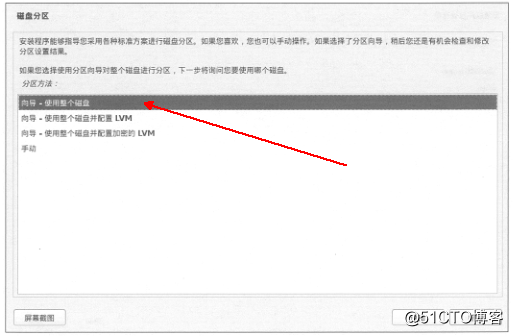
Kali Linux的安装方法相对来说还是比较简单的,我们简单认识一下:
插入光盘之后,




重启后输入管理员root,密码即可登录系统中。
开启系统后,还需要修改一些配置文件(vim /etc/apt/sources.list):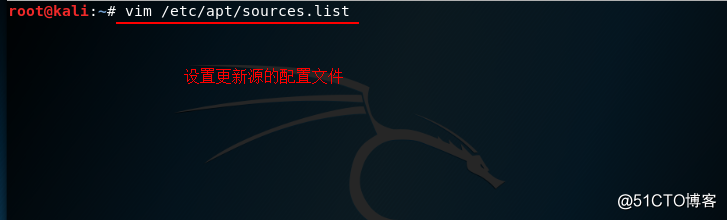
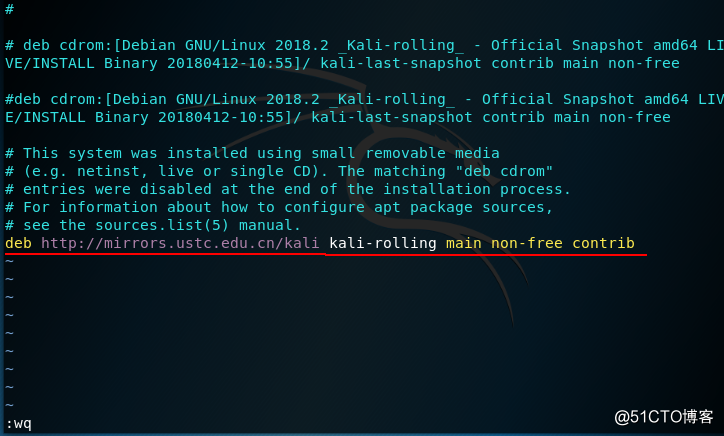

添加更新源以后对软件进行一次性整体更新,
root@kali:~# apt-get update & apt-get upgrade
#更新软件并更新已安装的软件版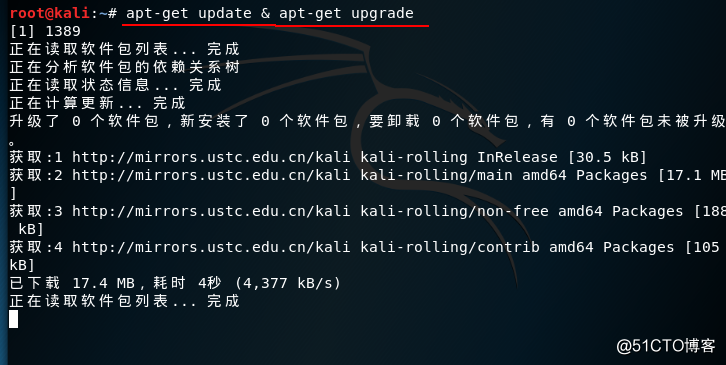
root@kali:~# apt-get dist-upgrade
#更新系统本身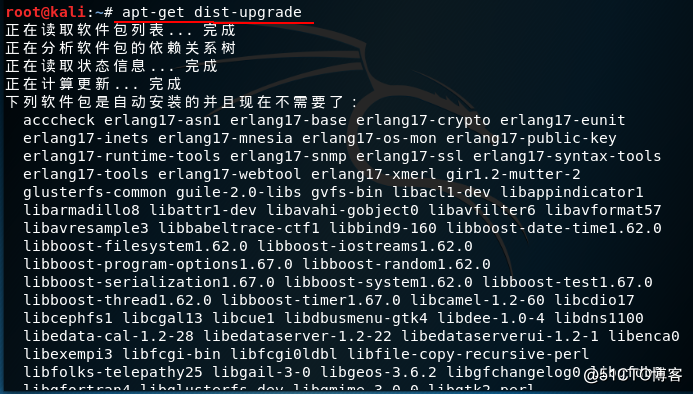
root@kali:~# apt-get clean
#删除已更新的软件包root@kali:~# lsb_release -a
#查看当前操作系统的所有版本信息,如果仅查看版本号,可以查看/etc/issue文件。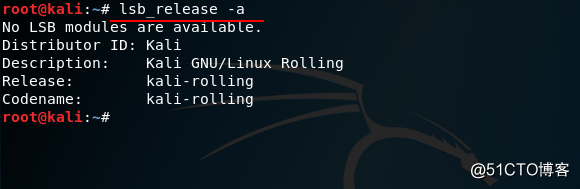
Kali method to accelerate the run: 
installing open-vm-tools-desktop:
VMware comes vmware-tools have failed in the new version of Kali, it is recommended to install open-vm-tools-desktop instead of vmware-tools to interact with the physical machine .
If you have previously installed the vmware-tools, you can directly enter "vmware-uninstall-tools.pl", delete the vmware-tools. Once you set up an update source, execute the command "apt-get install open-vm -tools-desktop fuse" for installation, after the installation is complete reboot the system.
It is first introduced here, we have the opportunity to share with you a lot of experience and methods!