Github launched a measure to improve software security standards on 2023-03-09 . All developers who have contributed code on Github must complete 2FA (Two-factory authentication, two-factor authentication) before the end of the year . When I first heard about this, I didn’t take it seriously, because I knew about two-factor authentication before, which means that when logging in to an account, not only a password is required, but also additional authentication methods are required. The well-known SMS verification code is one of them.
2FA
But when I was about to enable 2FA for my Github account, I discovered that although Github provided the option of SMS/Text message, it did not support domestic mobile phone numbers, which meant that the verification code could not be received in mainland China. The two-step verification methods supported by Github are as follows:
- Authenticator app
- SMS/Text message
- Security keys
- Github Mobile
The mobile Github application can also be used for secondary verification, but for security reasons, my mobile phone is usually not equipped with scientific Internet software, and this item is also PASS. At this time, you can only use the Authenticator app, which uses the OTP (One Time Password, one-time password) algorithm.
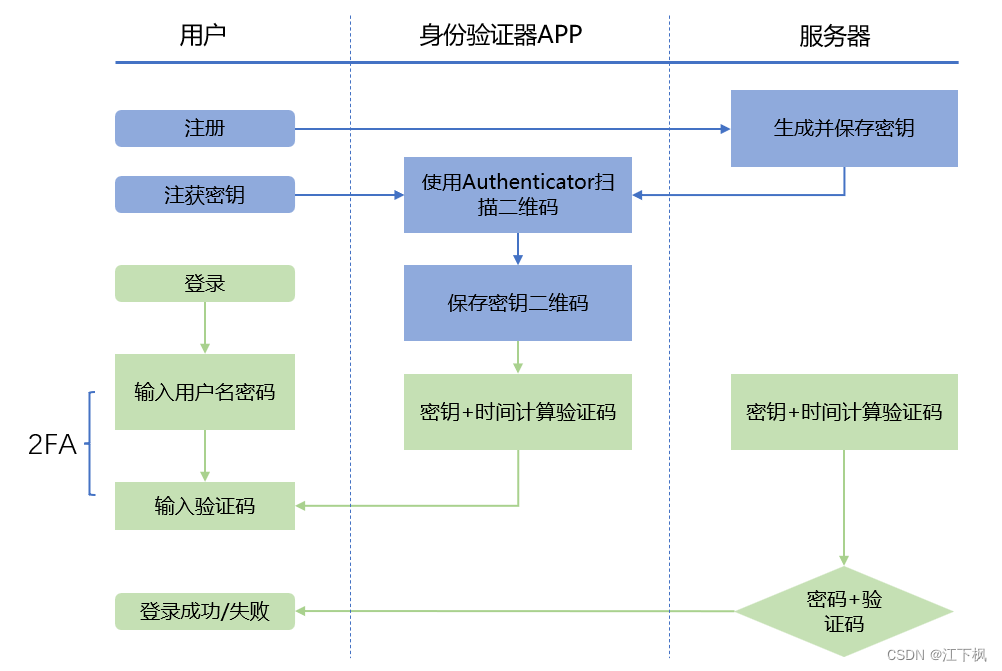
After introducing the 2FA scenario, we know that the principle of OTP is that when a user logs in or registers for the first time, the cloud not only saves the user's password, but also generates a key. The server usually uses a QR code to present it to the user. This key requires Users use the client to save, which means they need a program that supports OPT to scan the QR code. In this way, the cloud side and the end side have the same key and can generate the same one-time password based on the same algorithm. Usually this algorithm is TOTP (Time-based One-time Password, one-time password based on timestamp).
TOTP
TOTP is defined in RFC 6238. The appendix gives the JAVA code to implement TOTP, which readers can take for themselves. Its implementation algorithm is as follows
TOTP=HMAC-SHA-1(K, (T - T0)/X)
TOTP is based on OTP (one-time password) with a timestamp counter, where K is the shared secret key, T is the current timestamp, T0 is the starting timestamp, and X is the time step.
- Key generation: When setting up TOTP for an account, a unique key is generated. This key is shared between the user device and the authentication server.
- Time synchronization: User devices and authentication servers need to be synchronized to the same time source. The TOTP algorithm relies on the current time to generate one-time passwords.
- OTP generation: The TOTP algorithm combines the key with the current time and applies the Hash function to generate a one-time password. This password usually contains 6-8 digits and has a limited validity period, such as 30 or 60 seconds.
- OTP verification: When the user attempts to log in, they enter their regular password as well as a one-time password generated by the TOTP application or device. The authentication server then independently generates the expected OTP based on the shared secret key and the current time. If the OTP entered by the user matches the OTP generated by the server, access is granted.
2FA/OTP client
Github recommends paid clients, such as authy . If you are a wealthy person, please feel free to do so. Obviously I am not, so I spent some time collecting some useful tools, including browser plug-ins, APPs and desktop clients. Many password managers have the function of calculating OTP verification codes. While using them, we must also Consider security.
- Shensuo Offline Edition , a domestic startup company ten years ago, worked during the transformation period. I read some of the technology blogs they developed, and I still know a lot about security and customer privacy, and the privacy statement states that no personal data is collected.
- The security of WeChat mini program Authly is unknown. The advantage is that it can bind WeChat accounts and manage multiple passwords.
- Authenticator - Chrome plug-in, runs offline. It may be difficult to log in to Github on multiple devices.
- Microsoft Authenticator , an authenticator officially produced by Microsoft, can synchronize accounts. If you believe in the strength and security of big manufacturers, it is the best choice. The disadvantage is that it is too bloated (278.89MB).
- Google Authenticator , the official authenticator produced by Google, can synchronize accounts. Compared with Microsoft, it is not recommended to use Google products if you do not know how to surf the Internet.
Summarize
When the client is offline, the client can still generate a one-time password that is consistent with the server. This is because they initially agreed on a shared key, and the key + timestamp are calculated using the same algorithm. One-time passwords are a powerful complement to two-factor authentication, but of course one-time passwords can also be used in other areas, not just 2FA. For example, for smart door locks, we can use TOTP to generate temporary passwords to open the door for cleaners; the dynamic token generator of ICBC online banking can still generate dynamic passwords in offline scenarios.