Article 21 of the "Data Security Law" clearly stipulates that the state shall establish a data classification and hierarchical protection system. According to the importance of data in economic and social development, and once it is tampered with, destroyed, leaked or illegally obtained or used illegally, Based on the degree of harm caused to national security, public interests, or the legitimate rights and interests of individuals and organizations, data shall be protected by classification and level. The national data security coordination mechanism coordinates relevant departments to formulate important data catalogs and strengthen the protection of important data.
Implementing data classification and classification is a prerequisite for ensuring data security and is also an extremely important part of the data security management process. This article provides some ideas and suggestions for data classification and classification based on collecting and sorting out regulatory requirements and combining best practices.
01 Overview of data classification and grading
Data security refers to protecting the confidentiality, integrity and availability of data. The main protection objects currently concerned in the field of data security include personal information and important data.
Personal information refers to various information recorded electronically or by other means that can identify a natural person’s personal identity alone or in combination with other information, including but not limited to the natural person’s name, birth date, etc. Date, ID number, personal biometric information, address, phone number, etc.
Important data refers to data that does not involve state secrets but is closely related to national security, economic development and public interests, including but not limited to public communications and information services, energy, Information collected and generated by various institutions in important industries and fields such as transportation, water conservancy, finance, public services, and e-government during their business activities does not involve state secrets, but once leaked, tampered with, or abused, it will have negative consequences for national security, economy, and society. adverse impacts on development and public interest.
In order to better understand and understand what data classification and grading are, start from the aspects of data, data sources, data classification and data grading.
1. Data
Data refers to any electronic or other record of information. It also refers to a formal representation of information that can be reinterpreted so as to be suitable for communication, interpretation, or processing. The data can be processed by manual or automated means. It also refers to the result of facts or observations, which is a logical induction of objective things. It is an unprocessed original material used to represent objective things. It is an identifiable and abstract symbol.
Data types include structured data (such as RDD, SQL, JSON, NOSQL, tabular data, etc.), semi-structured data (such as log files, XML documents, JSON documents, emails, etc.), unstructured data (such as office documents, text , pictures, XML, HTML, various reports, images and audio/video information, etc.).
In layman's terms, we compare human blood to data and organs to various departments of a company. Only flowing data can convey information to various departments, allowing for better collaboration.
2, Number of original sources
The sources of data mainly come from three aspects:
The first originates from the own data generated within the enterprise, such as transactions, operations, finance, human resources and other departments.
The second comes from third-party data, such as network data, communication data, credit data, customer data, etc.
The third source is the collection of data, such as data received through sensors, images and videos, social media, the Internet of Things, etc.
No matter what kind of data it is, it will be regarded as the data asset of the enterprise and included in the scope of data classification and classification.
The following figure is a schematic diagram of the data source:
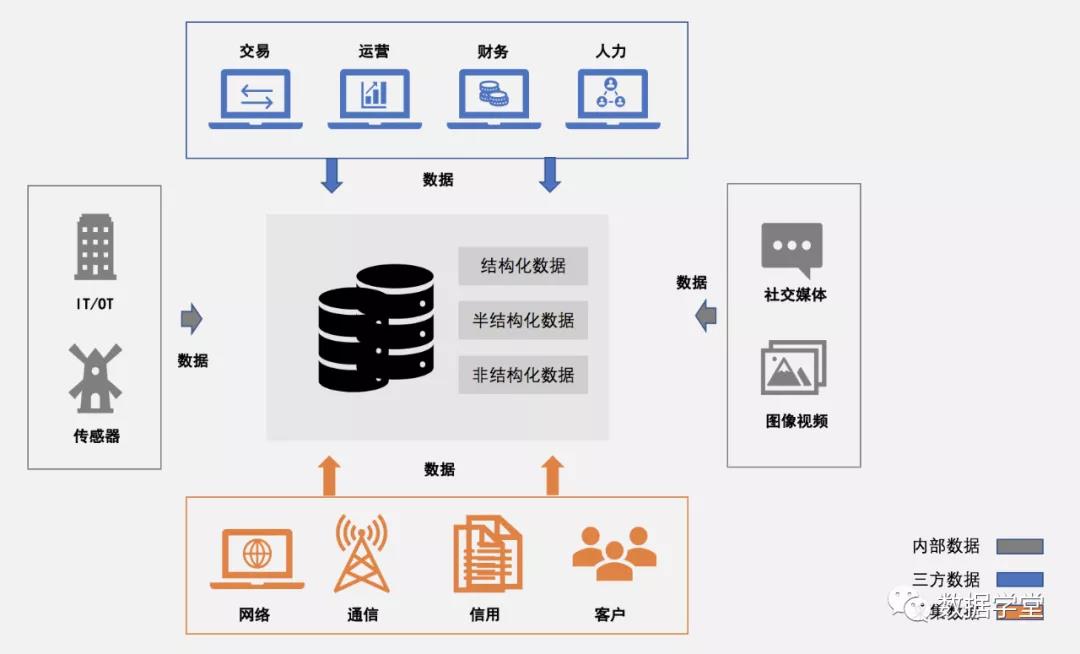
Figure 2 Source of data
3. Data classification
Data classification refers to the process of distinguishing and classifying organizational data according to certain principles and methods based on the attributes or characteristics of the organizational data, and establishing a certain classification system and arrangement order to better manage and use organizational data. Data classification is a key part of data protection work. It is the basis for establishing a unified, accurate, and complete data architecture, and the basis for achieving centralized, professional, and standardized data management.
4. Data classification
Data classification refers to using standardized and clear methods to distinguish the importance and sensitivity differences of data on the basis of data classification, and grading them according to certain classification principles, thereby providing information for the formulation of security policies for the opening and sharing of organizational data. The process of support.
02 Data classification and grading method
The first step in developing data security is to identify data and classify and classify data based on business characteristics. The accuracy of data classification and classification is the basis for subsequent data protection strategy deployment.
The general data classification and grading process includes: Develop data classification and grading standards, prepare data samples, establish sensitive data rule bases, scan target storage devices, and automate data mapping.
01 Develop data classification and grading standards
Develop enterprise data classification and classification standards/specifications based on relevant national standards, industry-related standards, and combined with enterprise business characteristics, such as:
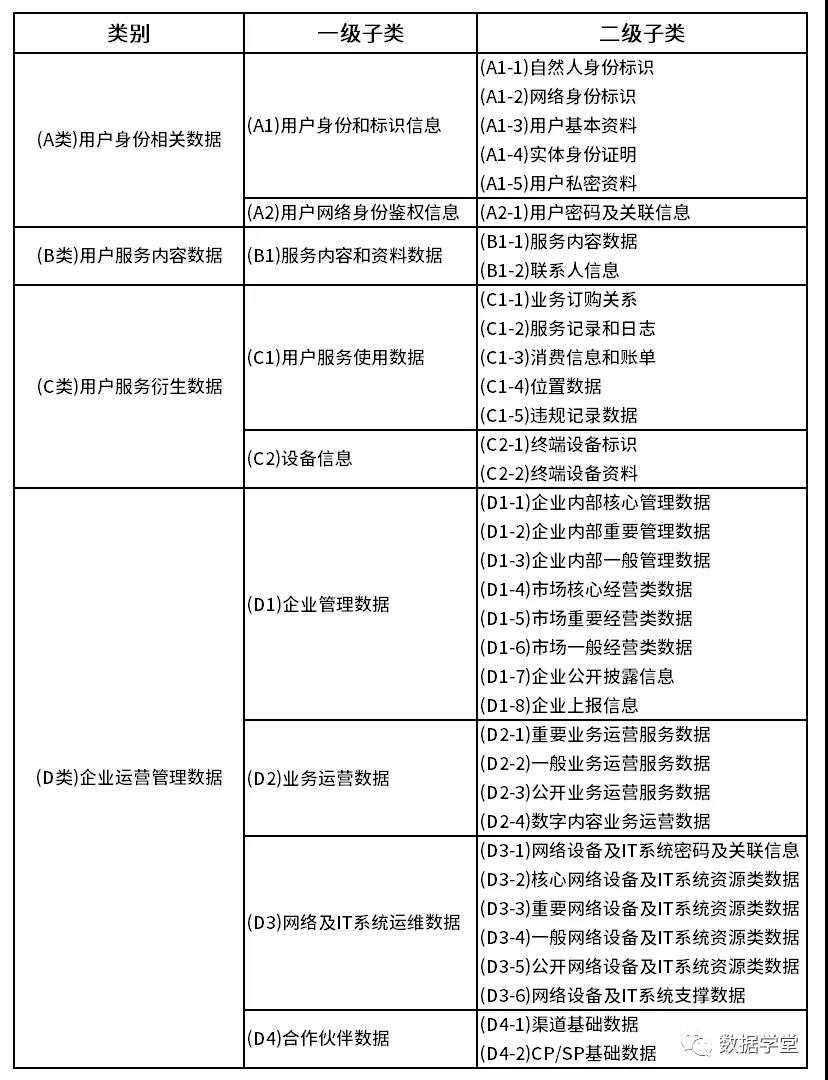
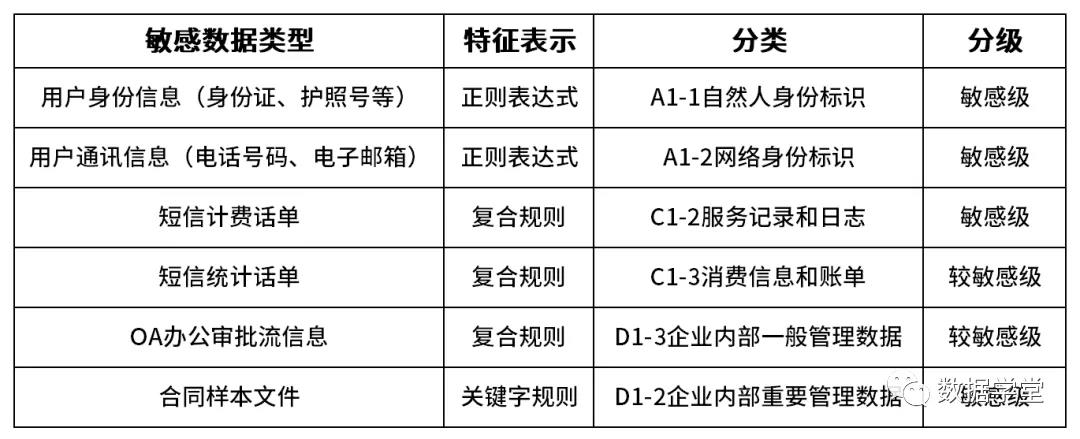
02 Prepare data samples and establish sensitive data rule base
03 Scan target storage devices and automate data mapping
Professional data classification and grading equipment scans structured/semi-structured/unstructured data to automatically discover the size, quantity and other attribute information and storage location of sensitive data, forming a mapping of data assets.

03 Several typical application scenarios of data classification and grading
01Usage scenarios for enterprise users
general needs
Enterprise users do data security construction work: first sort out the enterprise data assets, classify and classify them, formulate data management and control strategies based on the classification and classification results, implement control measures, display the data security situation in a panoramic manner, and continuously improve operations.
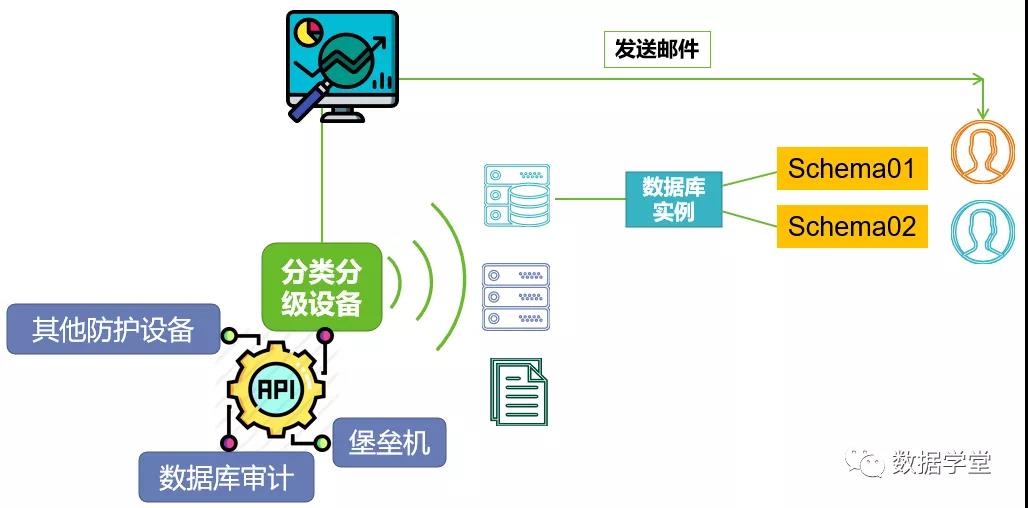
(1) Open API interface, allowing other data security protection devices to read sensitive data information to configure and deploy data security protection strategies.
(2) Scan the Schema of the database and send the scan results to the Schema person in charge via email to notify them of follow-up processing.
solution
Professional data classification and grading equipment is used to identify and classify data assets across the entire network. It opens a common API interface and can be linked with the data security operation management platform and data security protection equipment respectively.
Linked with the data security operation management platform, the data classification and grading results are uploaded to the platform, and policies are uniformly distributed to each data security protection device through the platform.
Professional data classification and grading equipment or data security operation and management platforms send sensitive data results to each data asset administrator for rectification respectively, forming a closed loop of data security operations.
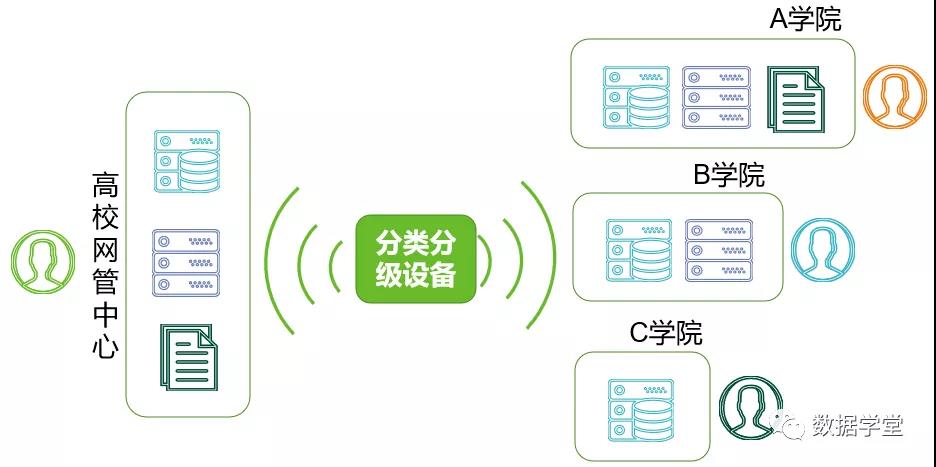
02Usage scenarios for university users
general needs
Professional data classification and grading equipment is uniformly maintained by the school's network management center. Specific sensitive data identification tasks are completed by each college, and the data of each college is isolated from each other.
solution
Professional data classification and grading equipment supports multi-user decentralized management, that is, the system administrator uniformly creates different user accounts, each user is allocated separate data space, and data is isolated from each other. Users can log in to the device through their own accounts to complete the classification and grading of the data assets they are responsible for.
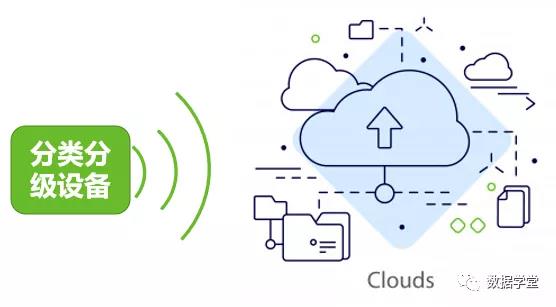
03Usage scenarios for cloud users
general needs
Business systems are deployed in cloud environments and need to support cloud data asset classification and classification.
solution
1. Professional data classification and grading equipment provides virtualization images, supports virtualization deployment, scans target data asset servers and provides data classification and grading.
2. Professional data classification and grading equipment is deployed in hardware and connected to the target cloud environment through switches to scan and provide data classification and grading.
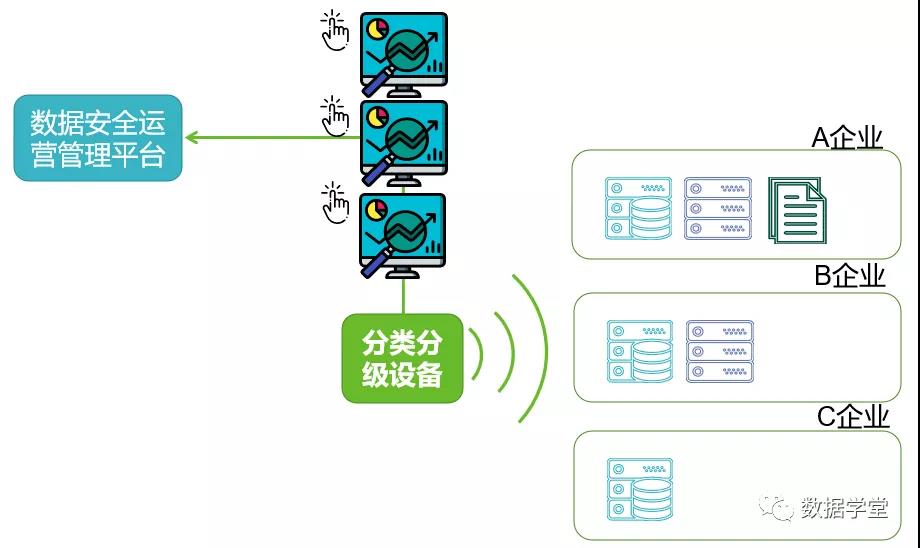
04Usage scenarios for regulatory agencies
general needs
1. Regulatory agencies need to conduct comprehensive data security risk assessments for big data enterprises/units, including data asset identification, data classification and classification, platform component security scanning, etc.
2. After each enterprise/unit completes the scanning inspection, upload the scanning results to the data security operation management platform.
solution
Professional data classification and grading equipment provides network-wide data asset mapping, intelligent data classification and grading, real-time data flow mapping, and platform component security scanning functions. It can regularly scan target data assets through the plan management mode and provide comprehensive data security risk assessment reports and rectifications. suggestion.
Professional data classification and grading equipment provides a common API interface, which can upload scan results to the data security operation management platform in real time or manually.
04 The significance of data classification and grading
1. Meet compliance requirements
Meeting compliance is the most basic requirement for the smooth operation of an enterprise. Article 21(4) of the "Cybersecurity Law", Article 21 of the "Data Security Law", Chapter 6 of the "Civil Code Law", as well as Class A and Standards There are requirements for regulations, etc. Enterprises should study them, implement them in accordance with the regulatory requirements of the industry, and use processes and technical means to effectively implement data classification and classification.
2. Satisfy self-development
With the in-depth application of new technologies such as big data, artificial intelligence, and cloud computing, the transformation into information-based assets has become an inevitable trend. As the level of informatization continues to improve, a variety of data will also be generated. If data management is not well planned in the early stage, the later maintenance cost will be higher.
3. Improve data usage value
How to better extract value from data and continuously provide enterprises with accurate data services. While improving operational capabilities, the refined management of data assets will definitely become a driving force or breakthrough point for enterprise business optimization and one of the competitiveness of enterprises. The recognition and measurement of data assets are very likely to be included in the company's balance sheet and become one of the company's assets.
4. Reduce data security risks
Adopting standardized data classification and grading methods can help enterprises clarify data assets, determine the importance or sensitivity of data, who can use it and how, which data can be disclosed and which data cannot be disclosed, etc., and take appropriate targeted measures. , reasonable management methods and security protection measures to form a set of scientific and standardized data asset management and protection mechanisms, thereby reducing the possibility of data being tampered with, destroyed, leaked, lost or illegally used.