Yue Shi Feng Yun is a Huawei cloud information expert who is good at diversifying complex information. It produces a picture (Yun Tu Shuo), an in-depth blog post (Yun Xiao Le) or a short video (Yun Shi Hall) that can satisfy everyone. You can quickly get started with Huawei Cloud. For more great content click here.

Abstract: Ransomware is a kind of extremely destructive and spreading malware. The means of ransomware have gradually developed into multi-stage ransomware such as encrypting data, threatening to leak sensitive data, DDoS attack threats and supply chain attacks. Recently, a bank's U.S. subsidiary announced that it was attacked by a ransomware attack, affecting billions of dollars in business. Once blackmailed, it will seriously affect company operations, data security and company reputation.
This article is shared from the Huawei Cloud Community " Cloud Lesson | HSS Teaches You How to Deal with the LockBit Blackmail Incident " by Yue Shi Fengyun.

Recent hot blackmail incidents
On November 10, 2023, a bank's U.S. wholly-owned subsidiary issued a statement on its official website stating that it suffered a ransomware attack on November 8, causing some system interruptions. And on November 9, the LockBit ransomware organization publicly confirmed that it was responsible for the attack. LockBit is a ransomware family that first appeared in 2019 and has been upgraded to LockBit3.0. It has developed into a highly customized and complex ransomware and provides Ransomware as a Service (RaaS) capabilities. The most prolific ransomware organization in 2023, its victim list includes many world-renowned companies and institutions, covering financial services, food and agriculture, education, energy, government, healthcare, manufacturing and transportation, etc. If the victim does not pay the ransom, The files may be permanently lost or publicly leaked.
At present, a bank has not announced the results of the investigation. According to security expert Kevin Beaumont, the attacker is suspected of using the CVE-2023-4966 vulnerability of Citrix NetScaler Gateway/ADC products to launch attacks (Citrix NetScaler Gateway is a secure remote access solution that provides applications Level and data-level control capabilities to enable users to remotely access applications and data from any location. Citrix NetScaler ADC is an application delivery and security platform.) An unauthorized remote attacker can exploit this vulnerability to steal sensitive information such as cookies , thereby bypassing authentication.
LockBit ransomware operations follow a ransomware-as-a-service (RaaS) model, using affiliates to distribute the ransomware, which use different attack methods to infiltrate and deploy the ransomware.
initial invasion phase
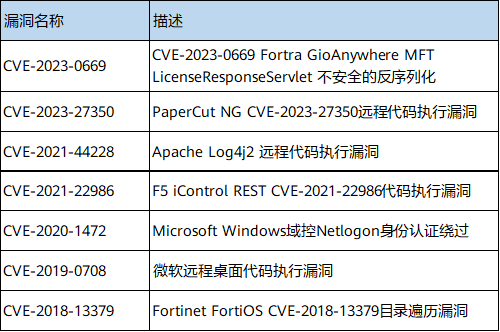
Possible attack methods used in ransomware intrusions include: Remote Desktop Protocol exploitation (RDP exploitation), Phishing Campaigns, Abuse of Valid Accounts, and Exploitation of Public-facing Applications ), typical vulnerabilities exploited by this ransomware family include:
Infection and Execution Phase
LockBit, like common ransomware, will perform operations such as persistence, privilege escalation, lateral movement, detection of sensitive data on the intranet, and disabling security software during the infection stage. Lockbit 3.0 can provide various parameters to control the behavior of the ransomware when it is actually executed in the victim environment. It can accept additional parameters for specific operations of lateral movement and encrypting specific directories on the endpoint. And it protects itself by using encrypted executable files to avoid detection and analysis.
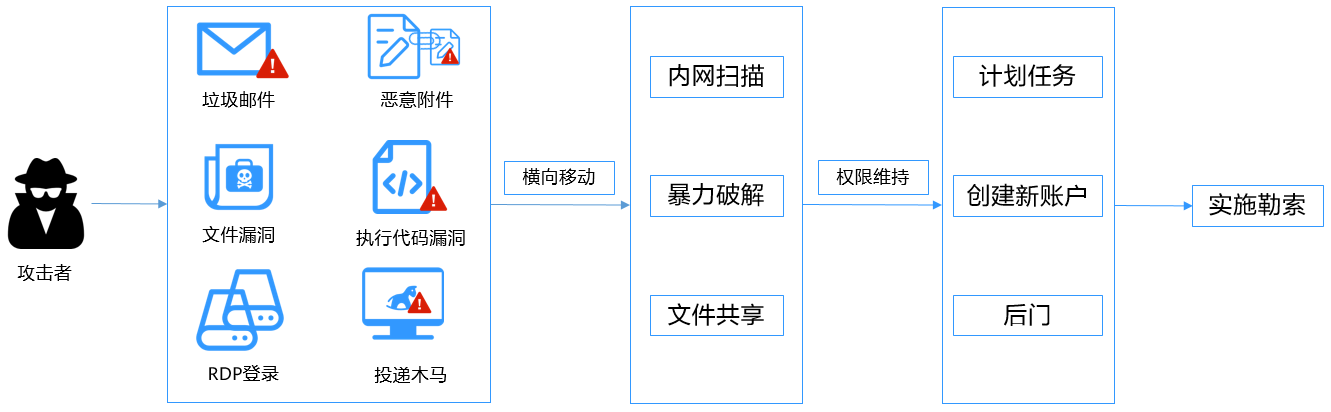
LockBit uses a double extortion strategy to steal some of the victim's files and then encrypts these files. LockBit3.0 continues to target Windows and Linux systems, using the AES+RSA algorithm to encrypt files (there is no corresponding decryption tool on the market), and at the same time changes the desktop wallpaper to prompt the user that the user has been blackmailed, and releases the file named [Random string].README .txt ransom note.

Data breach stage
LockBit ransomware will use its self-developed data exfiltration tool StealBit, or legitimate cloud synchronization tools (such as RClone, Mega, etc.) to upload stolen data.
Ransomware protection solution
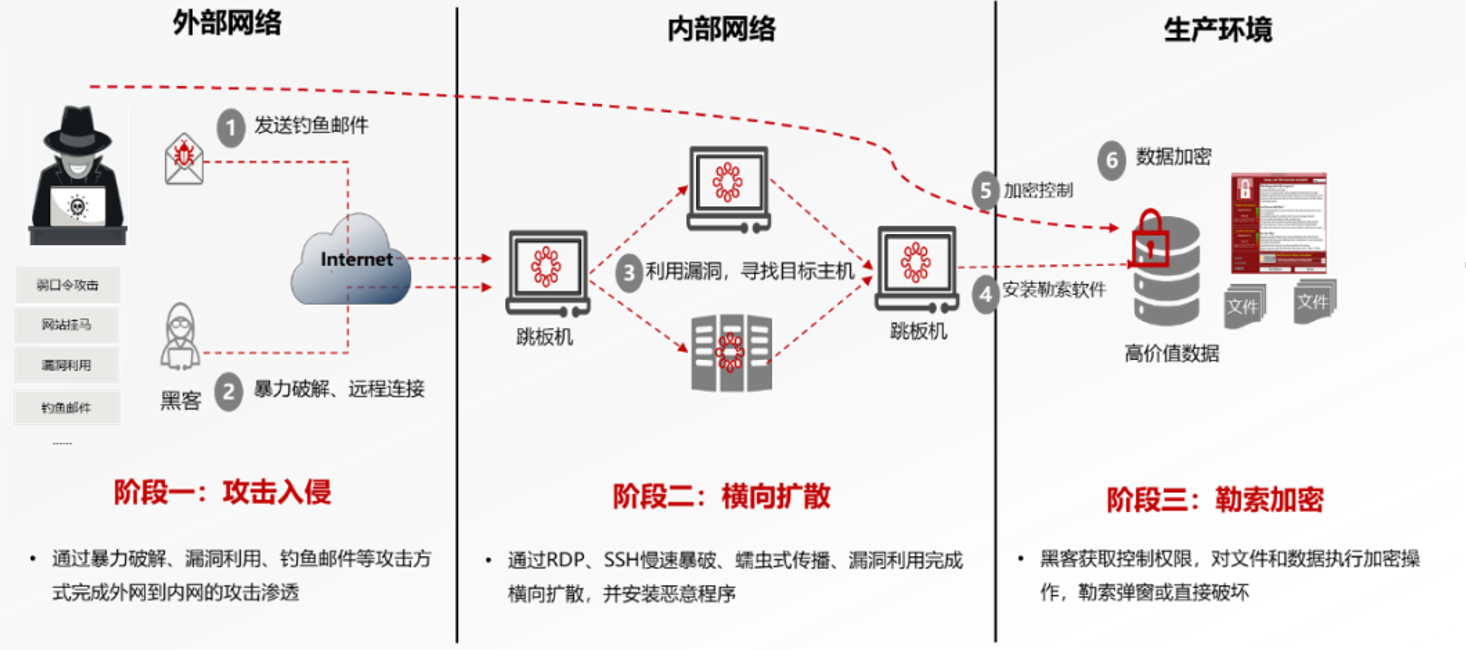
Carry out targeted protection according to the three stages of ransomware attacks. The attack stages include: attack intrusion, lateral diffusion and ransomware encryption.
Analysis of common ransomware attack paths:
Huawei cloud host security service can prevent risks before attacks and intrusions, provide alarms and block attacks when attacks occur and move laterally, and perform data recovery and security reinforcement after ransomware encryption occurs.
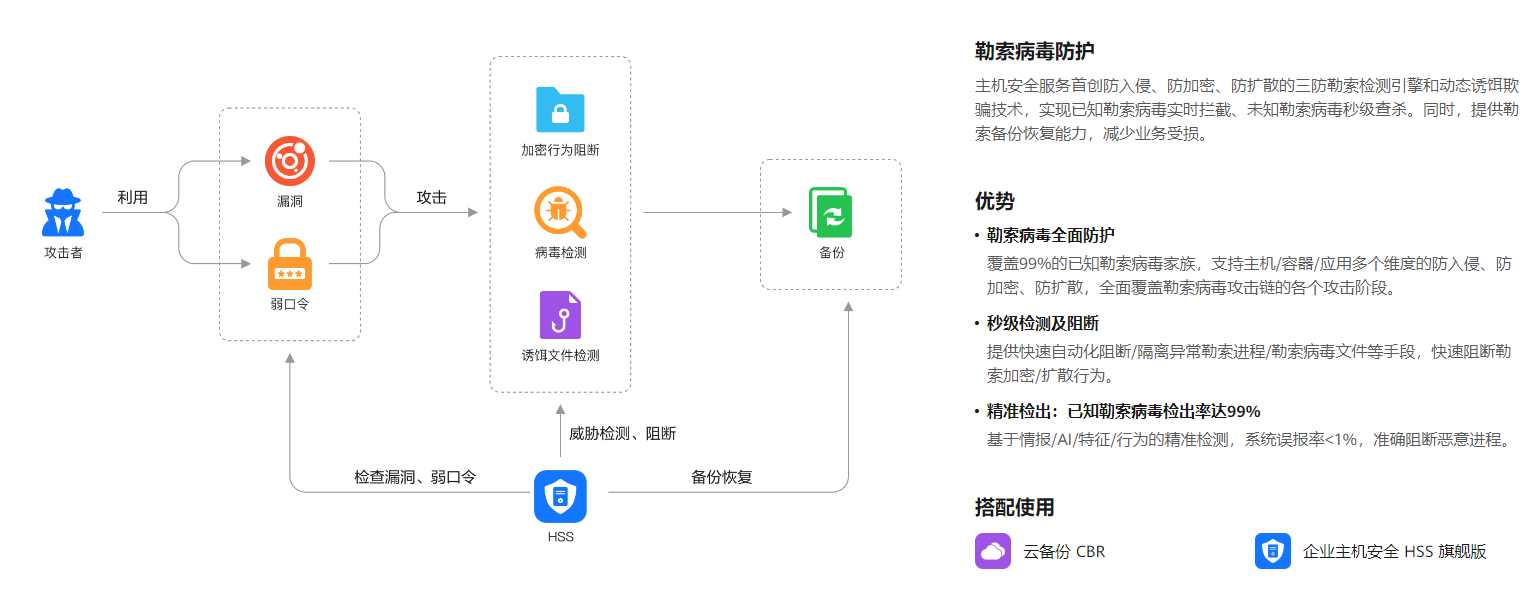
risk prevention
Huawei Cloud Host Security HSS provides full-link security protection against ransomware attacks. Before an attack, you can use the risk prevention functions provided by HSS Host Security, including baseline inspection, vulnerability management, and container image security scanning, to sort out corporate assets and Conduct baseline checks on various server services, and perform vulnerability scans on various applications running on the server to repair vulnerabilities in a timely manner, converge the attack surface, and reduce the risk of server intrusion.
Step 1: Enter the "Baseline Check" page to deal with configuration risks, weak password risks, etc.
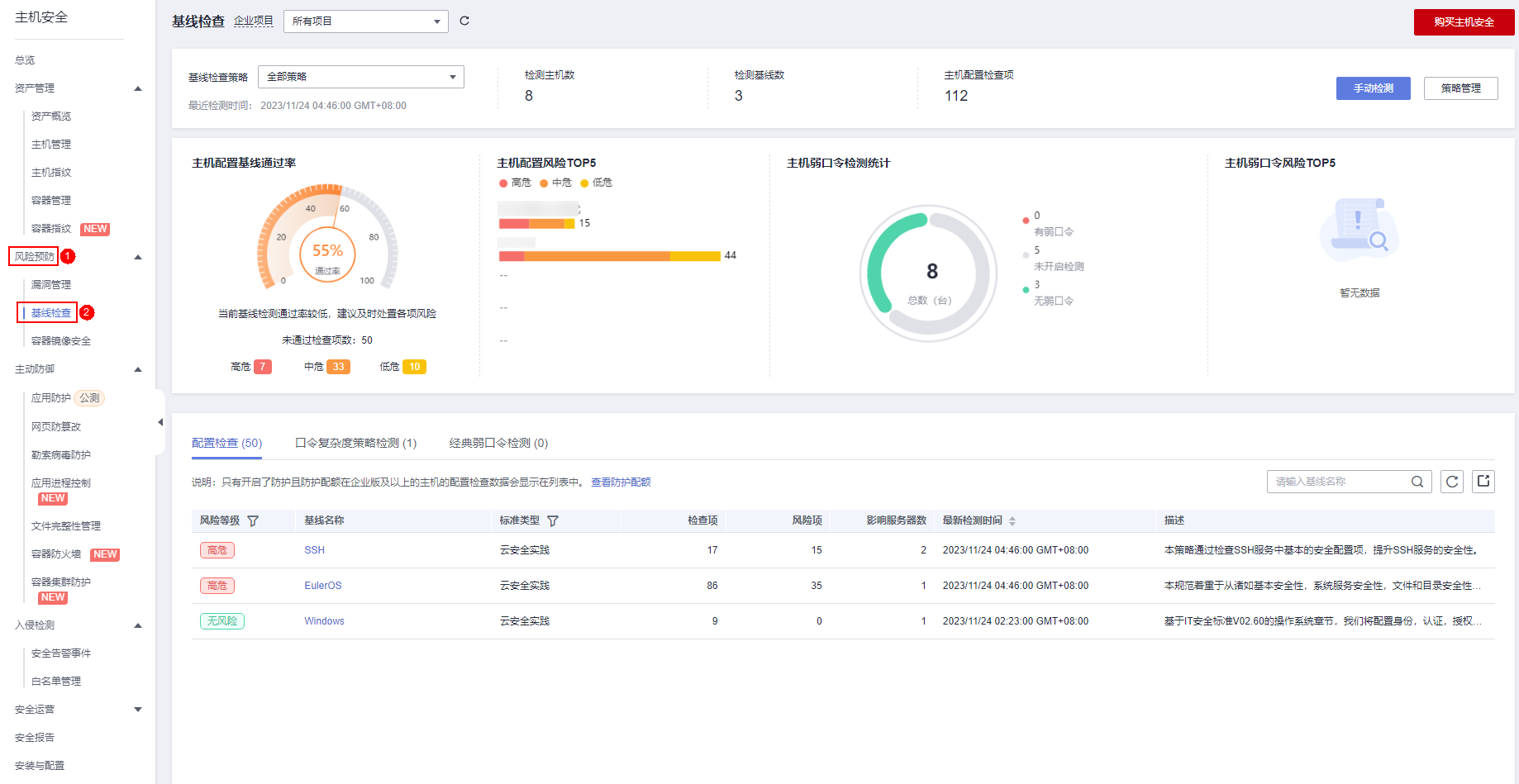
Step 2: Enter the "Vulnerability Management" page to scan and repair vulnerabilities.
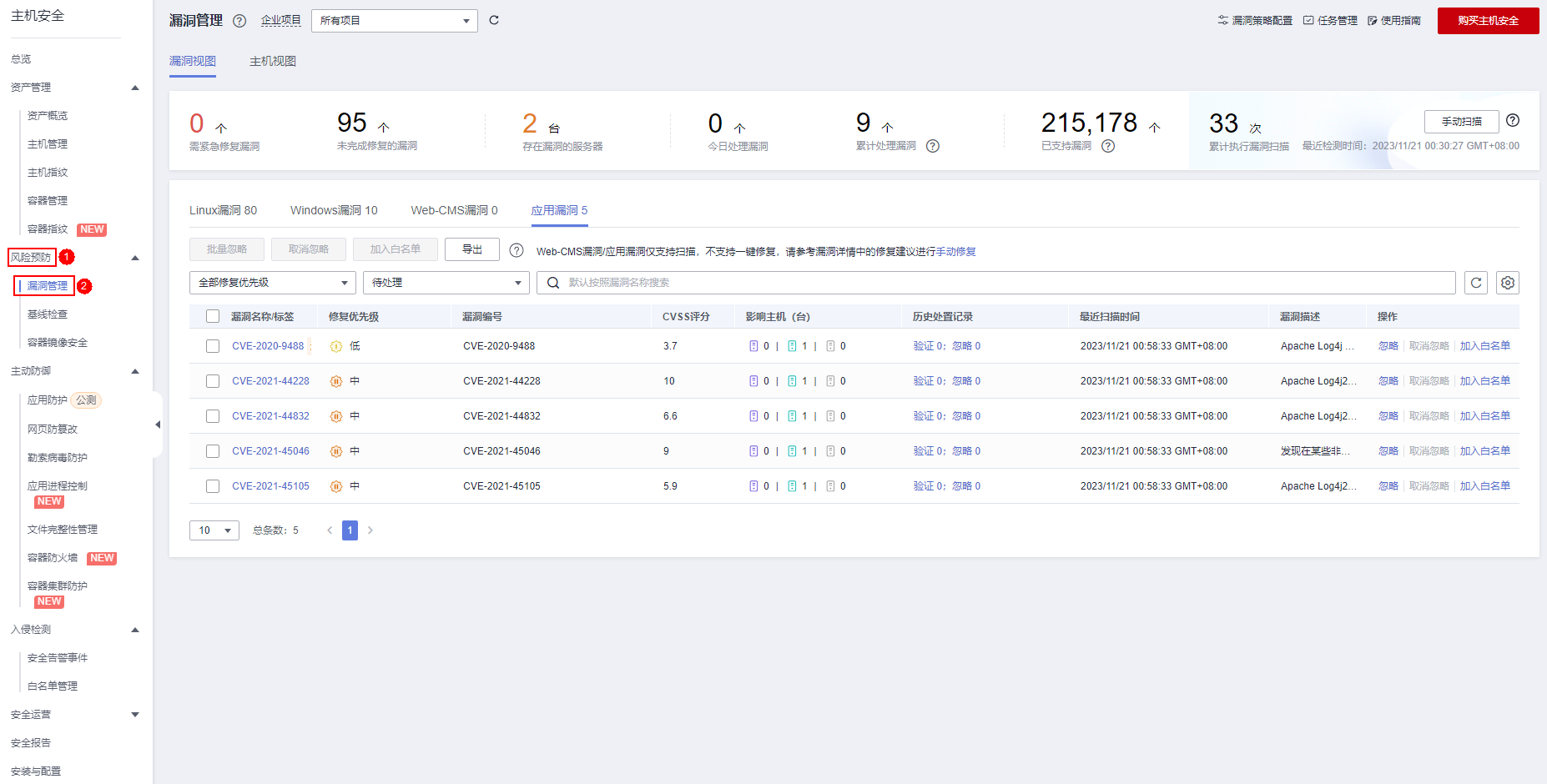
Intrusion detection and blocking
To carry out blackmail, hackers first need to obtain the permissions of the border server and use a variety of attack methods to intrude during the attack process. Therefore, they need to promptly alert and block various intrusion attacks during the hacking process. Huawei Cloud Host Security HSS supports brute force cracking. , vulnerability exploitation, Webshell, rebound shell, virus, Trojan, Rootkit, etc. detection.
The list of common tactical behaviors of LockBit ransomware attacks and the corresponding detection capabilities of Huawei Cloud Host Security HSS are as follows. HSS provides detection of the entire attack path:
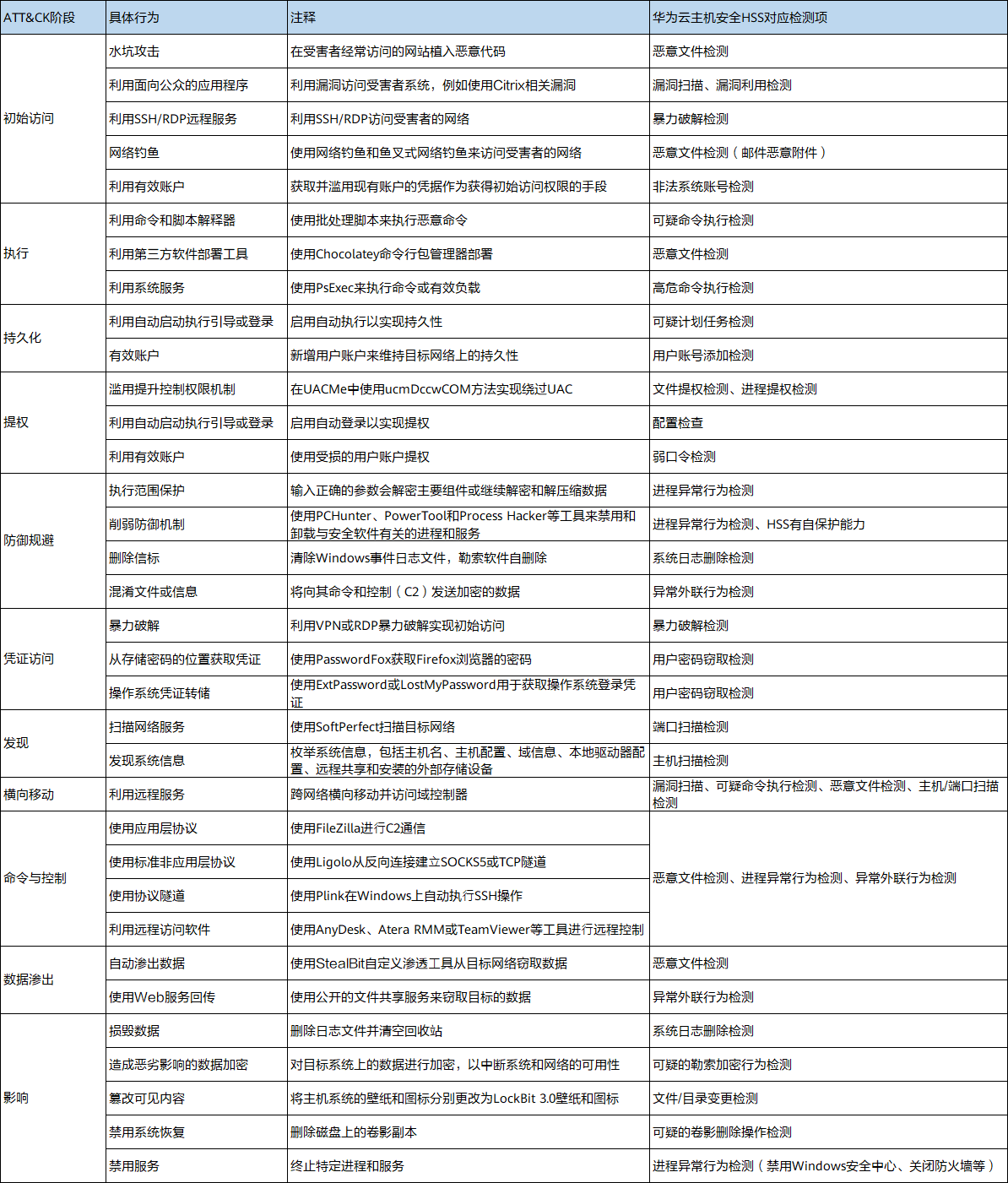
For ransomware, Huawei Cloud Host Security HSS provides multi-dimensional detection capabilities, including AV virus engine detection, bait file detection, and HIPS host intrusion rule detection. The AV virus engine detects ransomware based on its characteristics, the bait files are detected based on the ransomware encryption behavior, and the HIPS engine detects common abnormal behaviors of ransomware. After discovering the ransomware virus and ransomware encryption behavior, block the ransomware process to prevent the spread of the ransomware virus.
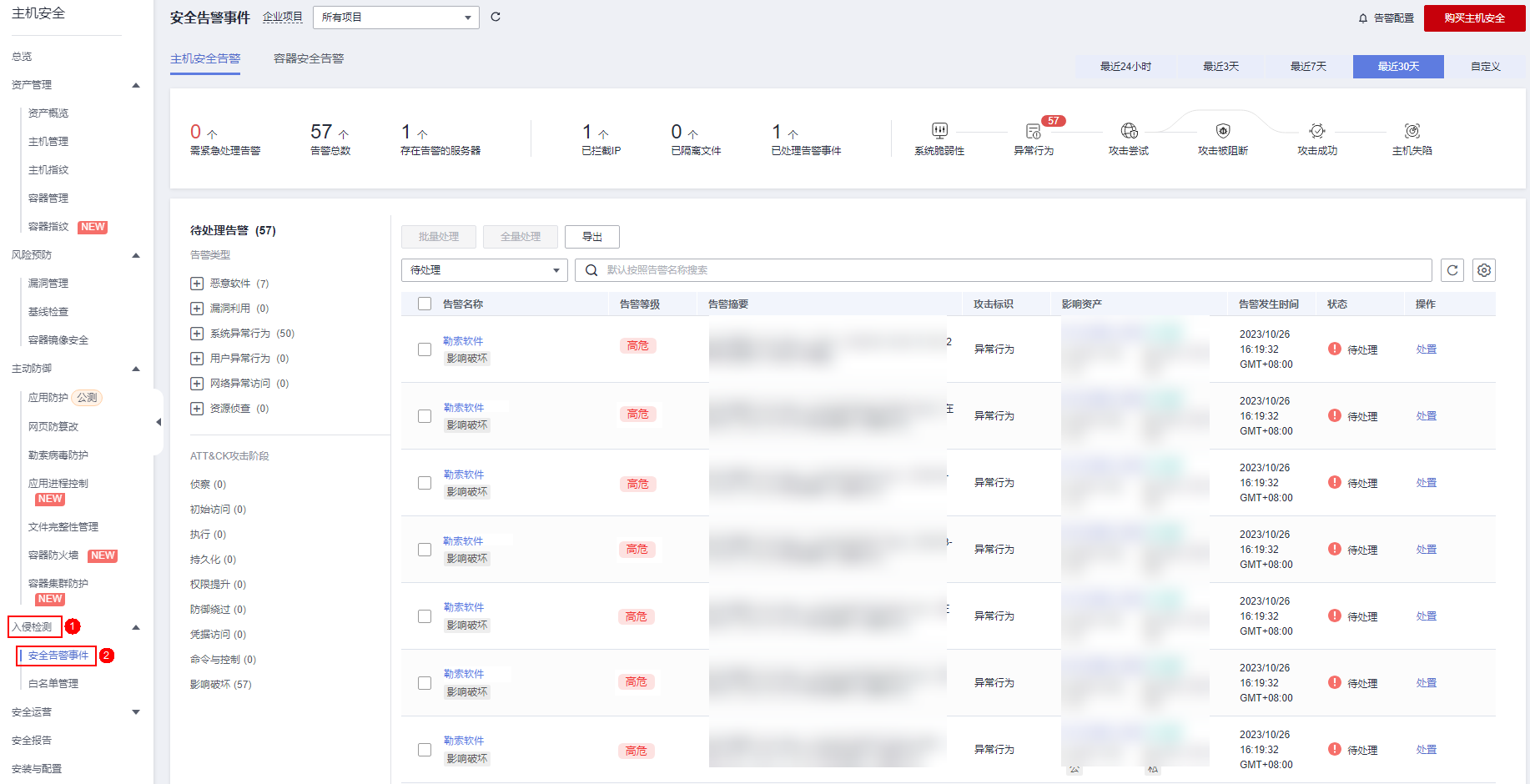
Data Recovery
If the server is encrypted by a ransomware virus, you need to restore the data through backup in a timely manner, analyze the reasons for the intrusion, and then perform security reinforcement to avoid being invaded and extorted again. Huawei Cloud Host Security HSS supports one-click data recovery. After turning on the ransomware virus protection policy, business data can be easily backed up. After the server is invaded by the ransomware virus, data can be restored through cloud server backup to reduce the losses caused by the ransomware virus. .
Click here to experience the anti-ransomware capabilities of Huawei Cloud Host Security Service!
Click to follow and learn about Huawei Cloud’s new technologies as soon as possible~
Spring Boot 3.2.0 is officially released. The most serious service failure in Didi’s history. Is the culprit the underlying software or “reducing costs and increasing laughter”? Programmers tampered with ETC balances and embezzled more than 2.6 million yuan a year. Google employees criticized the big boss after leaving their jobs. They were deeply involved in the Flutter project and formulated HTML-related standards. Microsoft Copilot Web AI will be officially launched on December 1, supporting Chinese PHP 8.3 GA Firefox in 2023 Rust Web framework Rocket has become faster and released v0.5: supports asynchronous, SSE, WebSockets, etc. Loongson 3A6000 desktop processor is officially released, the light of domestic production! Broadcom announces successful acquisition of VMware