Article directory
1. Special IP address
Set all the hosts in the IP address to 0, and it becomes a network number, which represents the entire local area network. Set
all the hosts in the IP address to 1, and it becomes a broadcast address, which is used to send data to all hosts connected to each other on the same link. The IP address of package
127.* is used for native loopback, usually 127.0.0.1
2. Limitation on the number of IP addresses
The IP address is a 4-byte 32-bit positive integer. There are 2^32 IP addresses in total. The
TCP/IP protocol stipulates that every host needs an IP address.
However, due to the existence of special IP addresses, the number is less than 4.3 billion.
In order to solve the problem of insufficient IP addresses, there are three solutions
Option 1: Dynamic allocation of IP addresses
uses DHCP technology (subnets are divided by routers, and the IP addresses of all hosts in the LAN are applied for from the router). Suppose
that in your home, your mobile phone is connected to a hotspot. When the hotspot is disconnected, it is equivalent to being recycled at the router level
(it will be given to you when you use it, and it will be recycled when you don’t use it).
Option 2: NAT technology (will be discussed later)
Solution 3: IPV6
IPV6 uses 16 bytes and 128 bits to represent an IP address, but it is not popular yet.
3. Private IP address and public IP address
IRFC 1918 specifies private IP addresses for establishing local area networks
I10.* The first 8 digits are the network number
I172.16. To 172.31. The first 12 digits are the network number
192.168.* The first 16 digits are the network number
included in this range, which become private IP, and the rest are called global IP (public IP) network IP)
Why can't private IP appear on the public network?
The router at home can build a subnet through private IP.
Since each home router can build the same subnet, private IP can exist repeatedly.

src is used as the source IP address, and dst is used as the destination IP address.
You want to send it from the current host to the public network.

Since the current host does not know who the destination IP address is, it will be handed over to the home router.
Since the home router belongs to both your device and the operator's device, there are two IP
subnet IPs, which can also be called LAN ports. IP represents the equipment in your home.
WAN port IP represents the equipment of the operator.

It is found that the destination IP122...3 is a public network IP, so it is continued to be delivered to the operator's router.
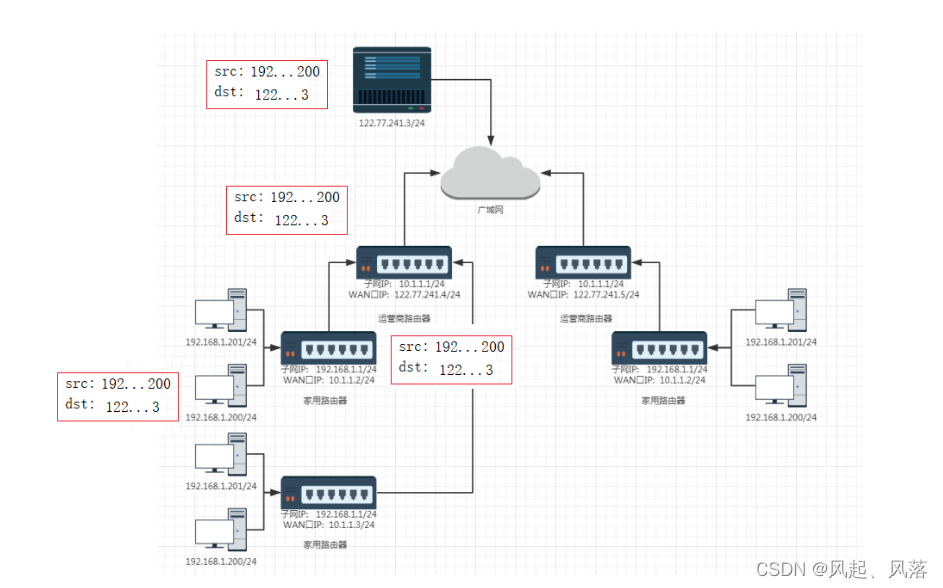
The operator's router continues to deliver the message upward to the corresponding host. The server receives the message request and responds to construct a response. When delivering downward, there is no way to deliver it downward
. The source IP address (src) is a private IP address
in the subnet. IP addresses can exist repeatedly, so private IPs cannot appear on the public network.
Solution—Use of NAT technology
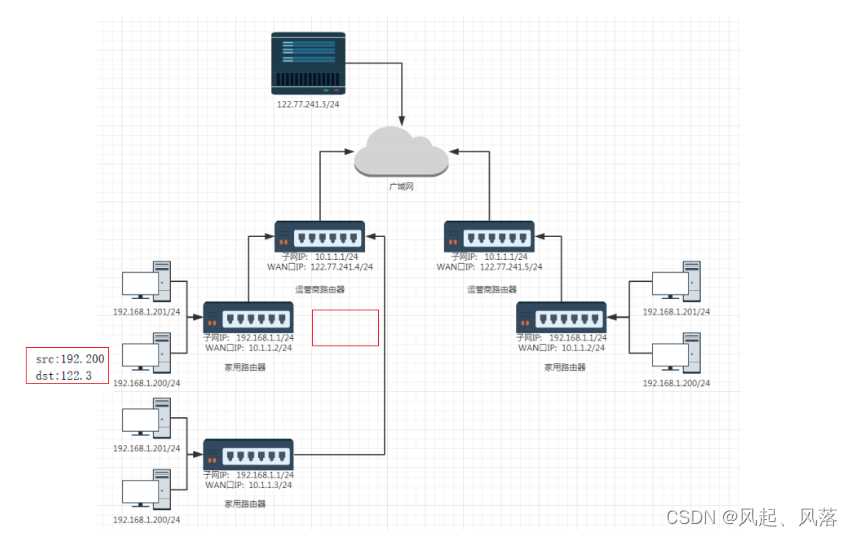
It is delivered from the 200 host to the home router. The home router finds that the destination address is a public IP and continues to deliver it upward.
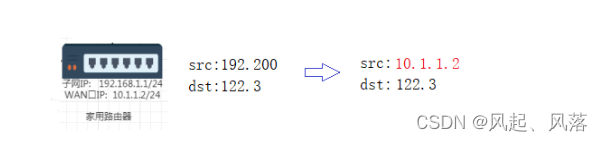
Before delivery, the LAN port IP (subnet IP) needs to be converted into WAN port IP
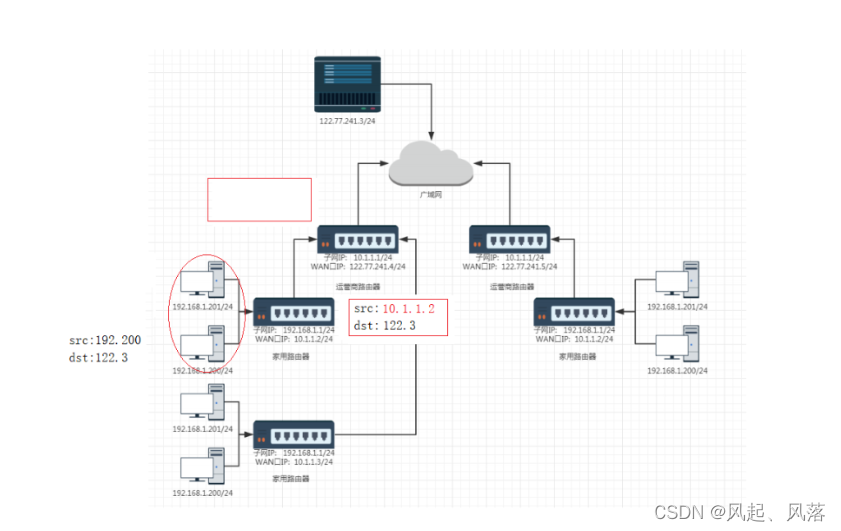
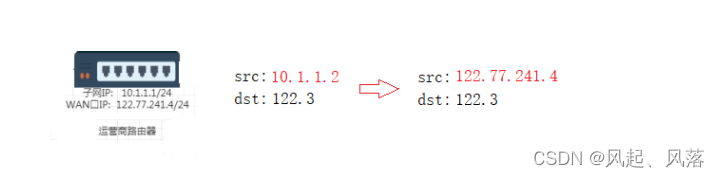
Replace the LAN port IP (subnet IP) with the WAN port IP again
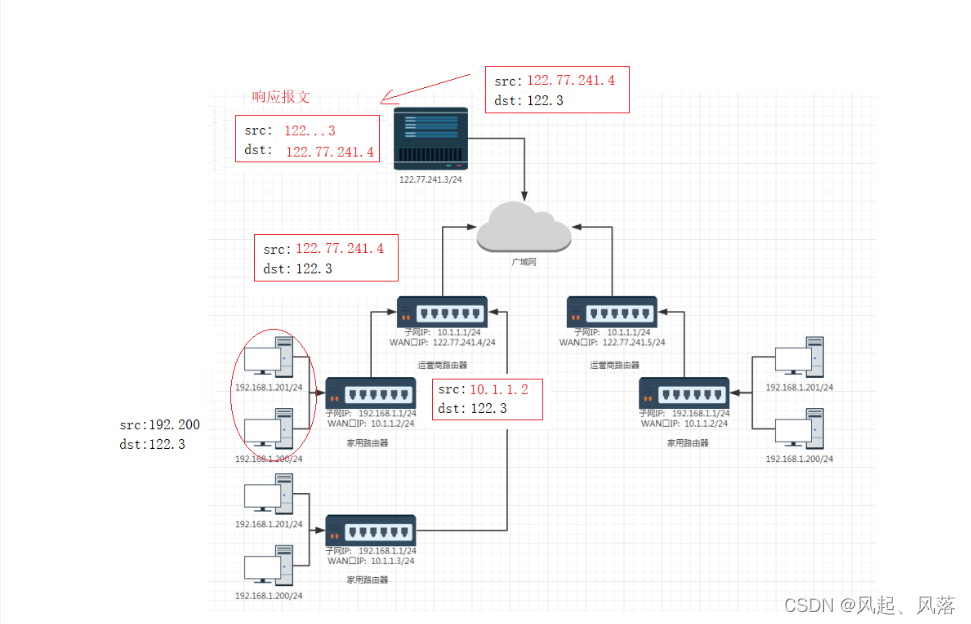
After receiving the message, the host constructs a response and forms a response message, which can be returned.
Since the destination IP address (dst) is not a private IP, it can be delivered downward.
The technology that continuously replaces the source IP in the intranet environment is called NAT (Address Translation) technology
4. Routing
Suppose you take a train to report at Tongji University in Shanghai. When you get off the train, you find that something is missing. Fortunately, you still have 20 yuan hidden on you. At this time, you don’t know
where you are at all. You only know that it is at the train station. You don’t know where Tongji University is,
so you have to Ask an uncle for directions and how to get to Tongji University.
In reality, the uncle may not know, or may refuse to answer your question.
If there is a router in the network environment, it doesn't know where the packet goes, but even if it doesn't know, it will find a way to help you.
According to the Internet, although I have never been there, I probably know that it is on that road, so I will give you a route to the nearby area.
When you arrived nearby, you didn’t know the way again, so you asked an uncle again about how to get to Tongji University, and finally arrived at Tongji University.
So when asking others for directions, be sure to tell them where you are going.
Conclusion:
1. When a packet arrives inside a router and asks the router, it must first tell the router where it is going, so the IP header contains the destination IP.
2. When the uncle thinks about the route and gives the result, it is equivalent to looking up the routing table.
3. If you meet an old man who knows where to go to the next stop, or if you meet an old man who doesn’t know where to go, he will not reject you. He will introduce you to someone who knows the way. It is equivalent to a router that doesn’t know where you are going, but is sure that you are going. It is not necessary to be in the current network
4. When you arrive at the Tongji University security office, ask the Tongji University security guard how to get there. The uncle will tell you that this is the entrance router
equivalent to the target subnet.
In fact, I am not going to Tongji University, but to the No. 11 Dormitory Building of Tongji University to find a counselor. But when asking for directions, I will not ask where the No. 11 Dormitory Building of Tongji University is. On the way, I only need to ask where
Tongji University is. Anywhere
When you arrive at Tongji University, you will ask how to get to Dormitory Building No. 11 of Tongji University.
It is equivalent to asking where the target host of the router at the intersection is.
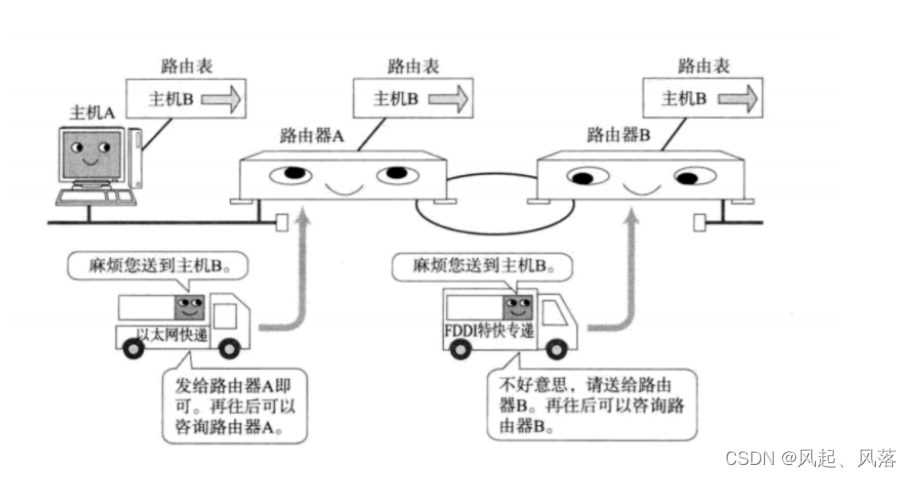
The entire message forwarding process:
first forward it on the road according to the road network, arrive at the intersection router of the target network, and then deliver it according to the target host
5. IP fragmentation problem
Why slice?
The data link layer stipulates that the payload of a single frame sent cannot exceed the MTU (maximum transmission unit 1500 bytes).
The size of the IP message is not decided by IP. The real size of the message is determined by TCP.
If TCP gives IP a large message but does not forward it at the data link layer,
IP can only fragment it because the size exceeds 1500 bytes.
Fragmentation can only be done by the current IP, and assembly can only be done by the other party's IP,
because only the IP protocol knows the fragmentation information.
How to do sharding and assembly?
16-bit identifier
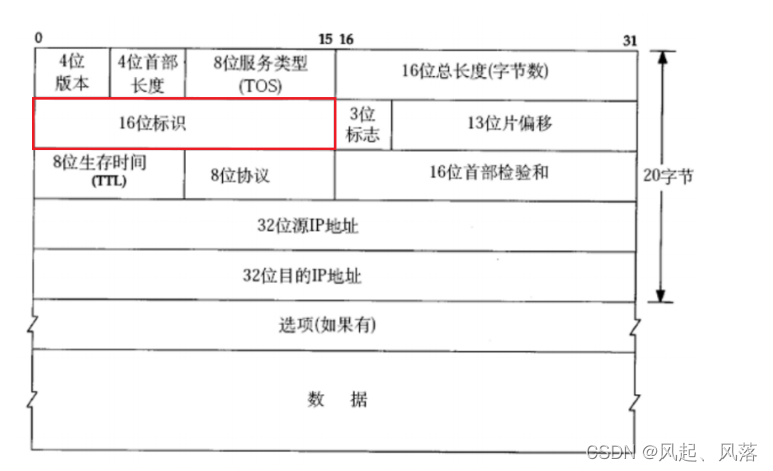
Therefore, there is a 16-bit identifier in the IP header.
The 16-bit identifier is a 16-bit integer to ensure that it and other packets are not repeated.
3-digit flag
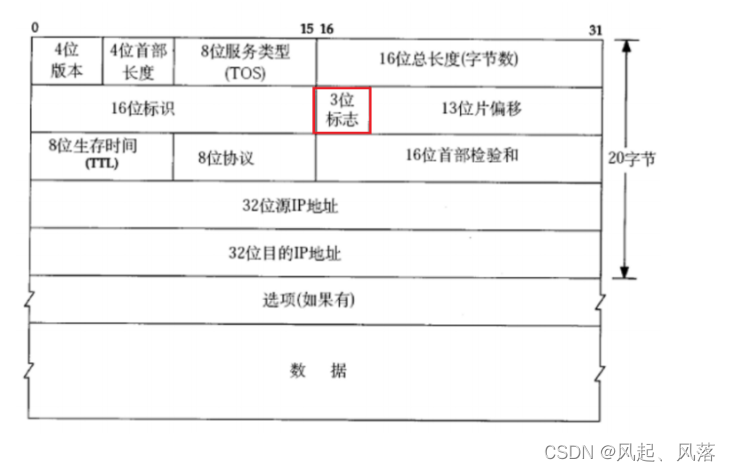
The 3-bit flag has a total of 3 bits.
The first bit is a reserved bit. This bit is not used and will be used later if needed.
The second bit
: If it is 1, it means fragmentation is prohibited. If the length of the message exceeds the MTU, the IP module will discard the message.
If it is 0, it means fragmentation is allowed.
The third bit indicates more fragments.
If fragmented, the last fragment is set to 0 and the others are 1.
(If you don’t understand, there are examples below to understand)
13-bit slice offset

If fragmentation is not performed, the starting offset of the corresponding packet in the original packet is 0.
example
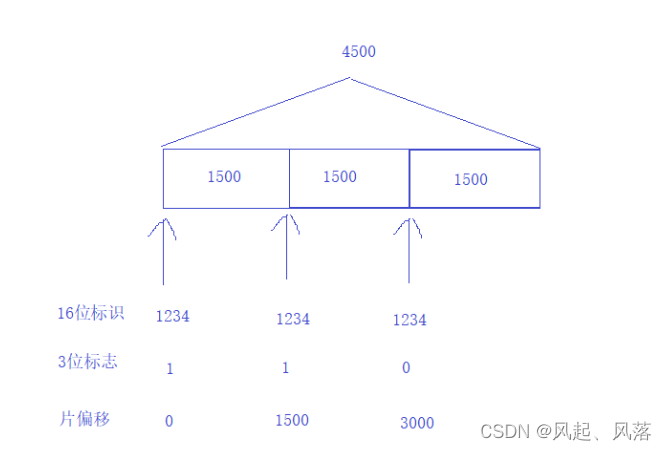
Fragment a 4500-byte packet into three 1500-byte packets.
Therefore, the three 1500-byte packets have the same 16-bit identifier, which is set to 1234.
A three-digit flag, set to 1 if there is a message following, and set to 0 if there is no message following.
The fragment offset of the first packet is 0, the fragment offset of the second packet is 1500, and the fragment offset of the third packet is 3000.
Details
How to distinguish different films?
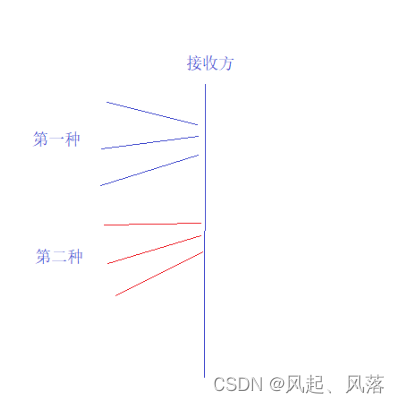
Assuming that you are the receiver of data and continuously receive packets.
If there are two clients sending packets, the packets of the first client may be fragmented, and the packets of the second client may also be fragmented. The two may be mixed. The source IP is carried in the same
packet, and the ability of different clients can be distinguished through the source IP.
How to know if it is sharded?
1. As long as the slice offset is not 0 (indicating that the fragmentation has been completed), extract the corresponding identifier.
2. If the slice offset is 0, and if more fragments are 1 (indicating that there are still fragments), it must have been fragmented.
How to judge whether it is the beginning message, the middle message or the end message?
If More Fragments is 1 and the fragment offset is 0, it is the beginning message.
If More Fragments is 1 and the fragment offset is not 0, it is an intermediate message.
If More Fragments is 0, the fragment offset is If it is not 0, it is the end message.
If more fragments are 0 and the fragment offset is 0, it is an independent message.
How to ensure that all shards are collected?
That is, how to ensure that the start message, middle message, and end message are not lost?
If the start message or the end message is lost, it can be known from the above judgment conditions
that the offset is sorted. The difference between each offset should be the same. If the difference is different, the intermediate message is lost. Got it
in conclusion
1. Fragmentation in the network, try to make it a rare occurrence
2. Why is network sharding not recommended?
When IP is sliced, part of it is lost, resulting in packet loss.
So whether it is TCP or UDP, when IP loses a message, it is really lost.
But TCP can timeout and retransmit a new message to IP
, while UDP does nothing.
Too many fragments can easily increase the packet loss rate
The rules are customized by the data link layer, and the data cannot exceed 1500 bytes.
When the message data from TCP is too large, IP will fragment it, but fragmentation will increase the packet loss rate,
but IP has nothing to do, IP is only used to execute orders
So all the problems lie in TCP.
Only TCP can reduce the packet loss rate by sending smaller data each time.
Therefore, the messages in the sending area of the sliding window are divided into multiple messages and delivered to IP.
3. How to reduce fragmentation?
Therefore, in the TCP protocol, try not to send data that is too large
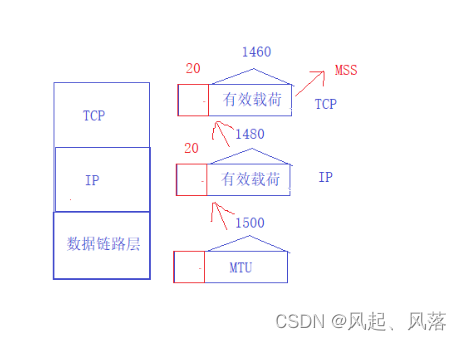
MTU (Maximum Transmission Unit 1500 bytes)
IP standard header is 20 bytes, payload is 1480
TCP standard header is 20 bytes, payload is 1460
Numbers like 1460 transmitted by TCP are called MSS (maximum segment size).
The message data sent by TCP should not exceed 1460.
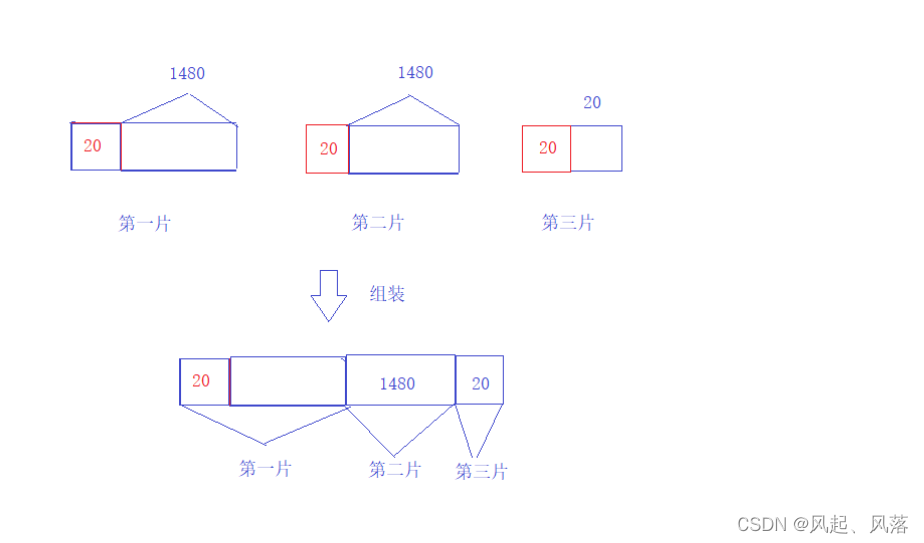
6. Do the sharding yourself
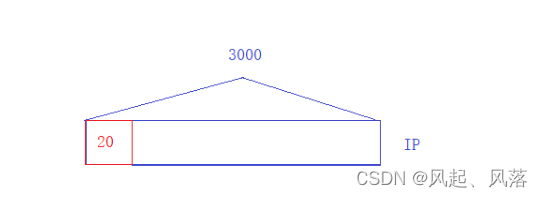
Assume that an encapsulated IP packet is 3000 bytes
After fragmentation, each piece is an IP packet, so it must carry a header,
so it should be divided into 3 pieces.
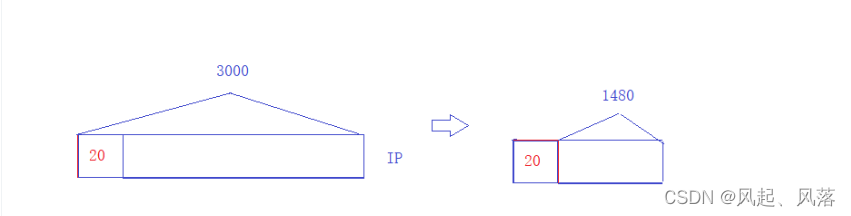
First, the first 1500 bytes are used as the start message, that is, 20+1480 and
its payload is 1480. If it does not exceed 1500,
it can be regarded as the first piece of the slice.
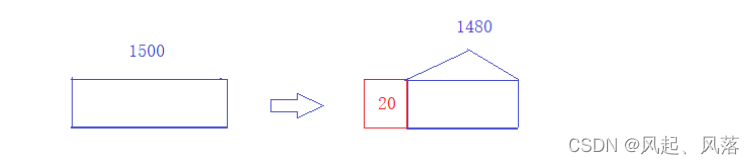
Split the remaining 1500 bytes of the IP message into 20 bytes, and re-add a 20-byte header in front of 1480 (which will be removed in the future), which
can be regarded as the second piece of the slice.
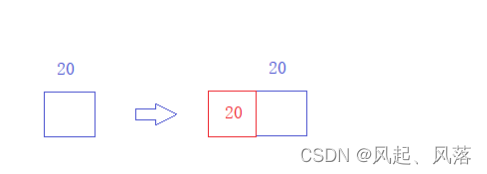
At this time, there are only 20 bytes left. Adding a 20-byte header in front of it (to be removed in the future)
can be regarded as the third slice of the slice.