background
We have deployed the NetInside traffic analysis system in the computer room of the hospital, using the traffic analysis system to provide real-time and historical raw traffic. The overall traffic analysis was planned on site this time, but abnormal traffic was found in the actual analysis, so we conducted investigation and analysis on this abnormal traffic.
Phenomenon
The analysis found that the traffic obtained by the NetInside system is very small, several megabytes per second (traffic interruption in the middle is the reason for the system restart), as shown in the figure below:

Log in to view through the ESXI system, and find that the size of the obtained traffic is different from that of NetInside, more than tens of megabytes per second, as shown in the figure below:
detailed analysis
In response to the above abnormal problems, we have adopted the following detailed analysis.
Flow distribution map analysis
From the traffic distribution diagram of NetInside, we can see that the system traffic is similar to the ESXI traffic. There are obvious traffic peaks at several time points. For one of the peaks, we analyze the data packet download.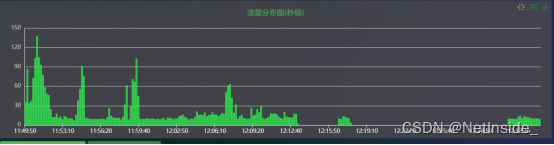
packet analysis
By downloading the 9-second data packet, it is found that all of this data packet is the outgoing ARP broadcast of LannerEL-XX:XX:79, and the number of packets sent within 9 seconds is 1.1 million times.
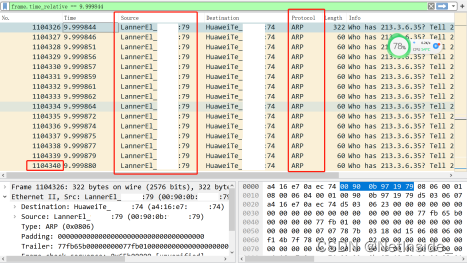
The specific IP address information corresponding to the MAC address is as follows.
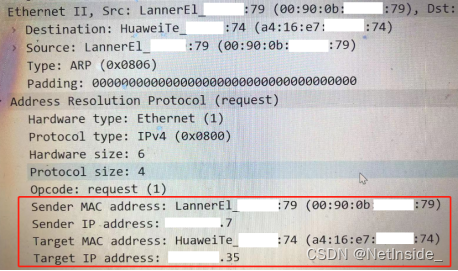
Analysis conclusion
Through the above system analysis, it was found that a large number of abnormal ARP broadcast packets appeared, and it was determined that a terminal was poisoned.
suggestion
Through the data analysis of the hospital, there are abnormal packets on the network, and it is recommended to conduct further analysis based on the actual situation of the network.