Analysis summary
The analysis summary is introduced from the following three points.
analysis content
Traffic collected by NetInside network traffic analysis equipment.
analysis time
The report analysis time range is: 2020-09-28 07:58:00-11:58:00, with a total duration of 3 hours.
Analysis purpose
The main purpose of this report is to find and locate hosts with suspicious phenomena, check the MAC of suspicious hosts,
Give solutions and suggestions.
analysis results
The following is an introduction from the list of suspicious hosts and the list of corresponding MAC addresses.
Suspicious host list
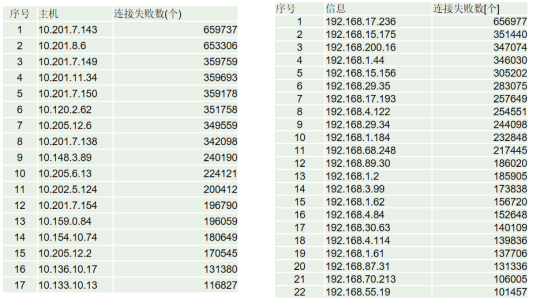
Suspicious behavior on the following hosts (39 machines in total).
Criterion for judging abnormality: hosts with more than 100,000 failures sent to the network within 3 hours.
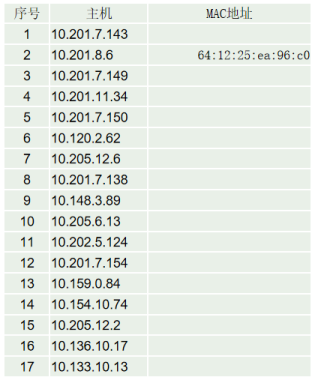
Suspicious host for MAC list
The following is a list of abnormal hosts and their corresponding MAC addresses on 10 network segments (17 machines in total).
The following is a list of suspicious hosts and their corresponding MAC addresses on the 192.168 network segment (22 machines in total).

Analysis process
The following analyzes are performed from the trend graph and data packets respectively.
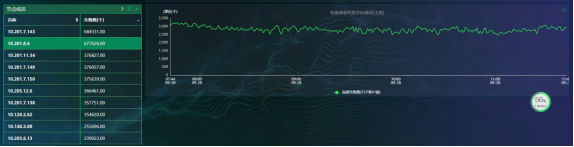
Trend Analysis
Take 10.201.8.6 as an example for detailed analysis. The host sends more than 3,000 failed connection requests to the network every minute. The figure below shows the distribution trend of failed connection requests for host 10.201.8.6.
packet analysis
Take 10.201.8.6 as an example for further detailed analysis. Through further analysis from the analysis system, the host sends a large number of connection requests to port 445 of other hosts, indicating that the host may be infected with a virus.

Methods and Recommendations
Solutions and reference suggestions are given below.
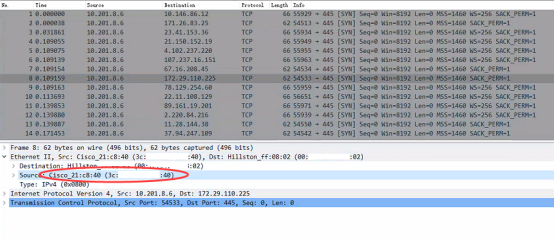
Position and display according to MAC
How to check the MAC address of a suspicious host, take 10.201.8.6 as an example. Open the data packet, click on any line, and you can see the source MAC at the Ethernet layer.
track progress
Enter the host with the problem, use the command netstat –anb to view the process connected to the external address port 445, confirm and perform corresponding operations.

Comprehensive killing
The system checks and kills the virus on the host. It is recommended to use anti-virus software to check and kill the abnormal host in an all-round way.