On June 27, 2023, the 2023 Big Data Industry Development Conference, sponsored by China Academy of Information and Communications Technology and China Communications Standards Association, organized by the Big Data Technology Standard Promotion Committee of China Communications Standards Association, and supported by the Data Security Promotion Plan-Data Security and High Quality The Development Forum was successfully held in Beijing.
The forum was chaired by Li Xueni, deputy director of the Big Data and Blockchain Department of the Institute of Cloud Computing and Big Data, China Academy of Information and Communications Technology. Experts from finance, telecommunications, automobiles, Internet, security manufacturers and other industries were invited to attend the meeting, aiming to strengthen data security ecological exchanges , to discuss the development trend of data security. Bai Xiaoyong, founder and CEO of Lianshi Network, was invited to attend and delivered a keynote speech on "Reshaping Data Security from a Business Perspective".

Follow gongzhonghao: " Refining stone is data security 057 " , you can package and download the high-resolution PDF version of the keynote speech "Reshaping Data Security from a Business Perspective".
In order to jointly promote the development of the data security industry, colleagues in the industry are welcome to join the “[Alchemy] Data Security Technology Circle” WeChat group to discuss technical experience and regulatory trends in the field of data security.

Today, data security construction is generally carried out in various industries, but the scope of data security is very wide. In the eyes of a thousand people, you will see a thousand kinds of data security. We choose to explore from a business perspective because we consider that data security starts and ends with business, which is closer to the essence of data security construction.
Data security begins with business and ends with business

Intrinsic risk and external compliance are driven by two wheels. At present, the development of my country's digital economy is entering a stage of rapid development. Ensuring that data elements are in a state of effective protection and efficient use, as well as the ability to ensure a continuous security state, is a key link in promoting the digital economy with high quality. The sources of data security requirements are internal risk-driven and external compliance-driven. The two are dialectically unified. During the collection, storage, use, processing, transmission, and provision of data, it faces different internal and external threats from internal risk personnel, commercial espionage, black and gray production, and even foreign forces. However, security incidents such as data leakage have the characteristics of economic external effects, that is, consumers and beneficiaries are inconsistent. As far as personal information protection is concerned, if there are no external compliance requirements, the most direct victims of personal information leakage are a wide range of individual users. , without substantial damage to the self-interests of companies and other personal information processors. This is likely to lead to a phenomenon that data security construction is placed in a "secondary position" by enterprises, mainly manifested in the insufficient proportion of security investment, security construction lagging behind business construction, and serious threats to information system security, etc., which need strong guidance through compliance Enterprises implement data security construction. In recent years, under the guidance of the national "14th Five-Year Plan" and the strategic report of the 20th National Congress of the Communist Party of China, "Network Security Law", "Cryptography Law", "Data Security Law", "Personal Information Protection Law" and "Four Laws" have been implemented successively . "Regulations on Classified Protection (Draft for Comments)", "Regulations on the Security Protection of Critical Information Infrastructure", "Regulations on the Management of Network Data Security (Draft for Comments)", and the "Regulations on Commercial Encryption Management" that have been fully revised and approved recently . Regulations and supporting regulations have been refined to the provincial and ministerial level, technical standards have been refined to the scenario level, and data security compliance requirements have been raised to a new level. Intrinsic risks bring together the powerful potential energy of data security construction, while external compliance transforms this potential energy into kinetic energy, jointly driving the vigorous development of data security construction.
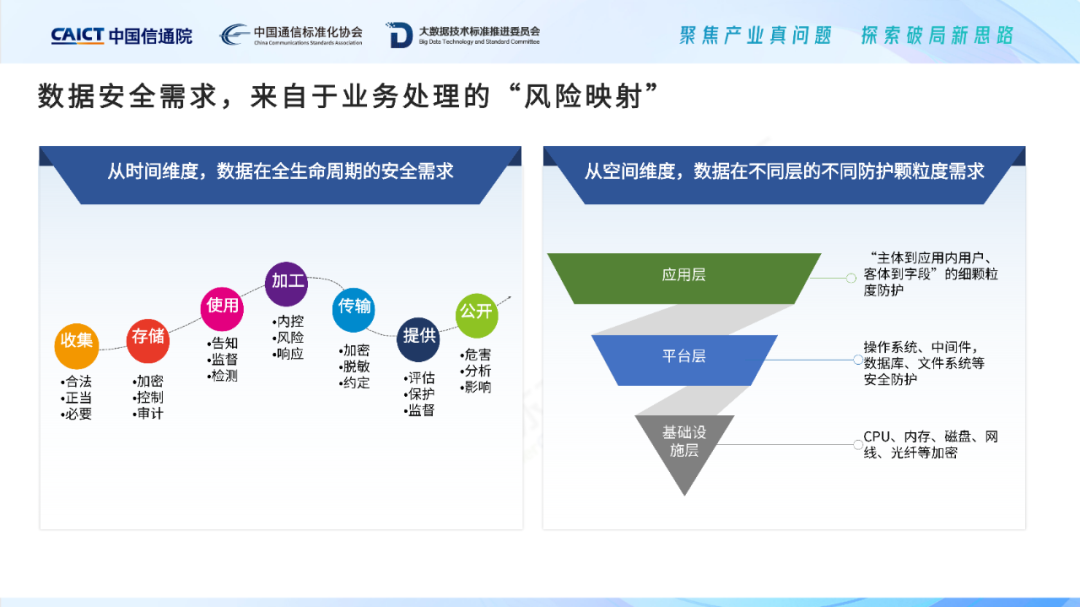
Rethink data security from a business perspective. Data, a new type of production factor, is the main carrier to realize business value. Data can only reflect value when it flows, and flowing data is bound to be accompanied by risks and risks are everywhere. Traditionally, security and business are related and sometimes antagonistic. But from another perspective, security is actually a business requirement. "Traditional business requirements" focus on "what you want to happen", while " security requirements" focus on "what you don't want to happen", so as to ensure "what happens". Data security requirements focus on confidentiality (to prevent theft), integrity (to prevent tampering) and authenticity. Among them, authenticity involves the authenticity of the original data, which is more prominent after the emergence of generative artificial intelligence. Combined with the information system of an enterprise or institution, data security comes from risk mapping in business processing. To implement data security, data security capabilities must be integrated into complex business processes. In the time dimension, data will have corresponding security requirements in the collection, storage, use, processing, transmission, provision, and disclosure of processing activities; in the space dimension, data flows between the infrastructure layer, platform layer, and application layer. Layers mean different granularity of protection requirements. Furthermore, static data itself has various security requirements. For example, the internal address book of an enterprise has its own information category, degree of disclosure, and personnel attributes. When data is shared, circulated, developed and utilized, dynamic data actually raises richer security requirements. It can be found that any business scenario with data transfer will have data security requirements. Since data security requirements are derived from the risk mapping of business processing, security boundaries also depend on business boundaries, and today's complex data processing scenarios have almost no boundaries, making data security requirements difficult to have boundaries and extremely complex.
Application retrofit costs offset safety gains
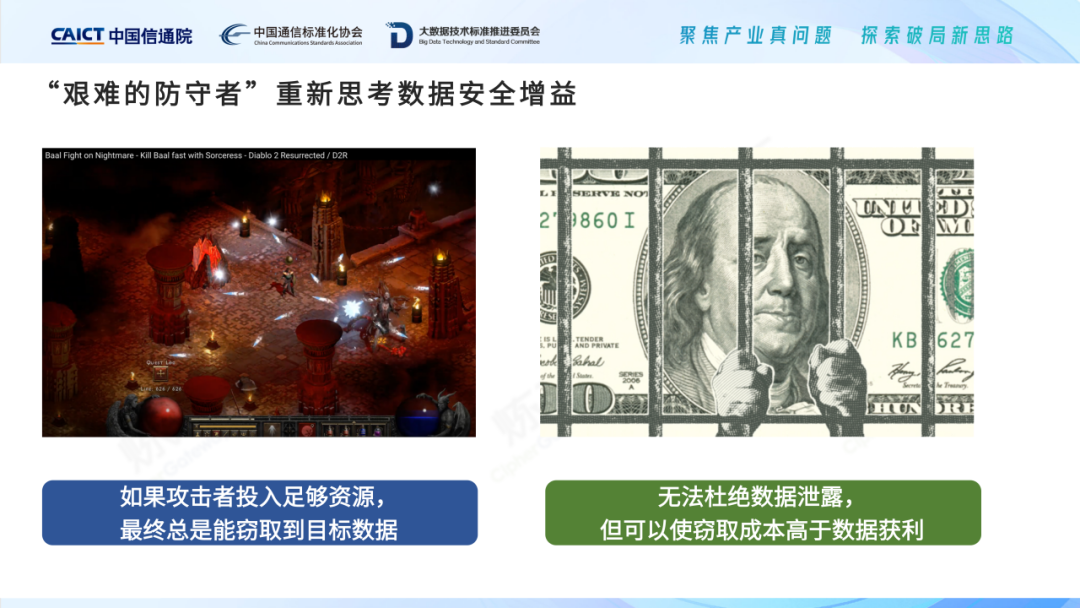
A look at data security gain through the lens of a tough defender. From the point of view of offensive and defensive confrontation, just like the highest-level boss in the game, it is impossible to escape the fate of being defeated by the player in the end . Can steal target data . Even taking a step back, assuming that the technology is impeccable, but there must be a brave man under the heavy money, and the data can also be leaked by artificial social workers. Therefore, tough defenders may never be able to build a "perfect line of defense". However, offensive and defensive confrontation is like a war. In fact, both sides consume resources. A good defense method is "enclose it in ten cases and attack it in five cases", creating local advantages to obtain a better battle loss ratio. The defender needs to evaluate the technical means, prioritize them, use less cost and consume more cost for the attacker. Furthermore, rethink the value of data protection based on reality. Although data leakage cannot be eliminated, technical protection measures can be actively adopted to make the attacker’s cost of stealing data higher than the profit of data, thus making the attacker meaningless. That's "effective data protection."
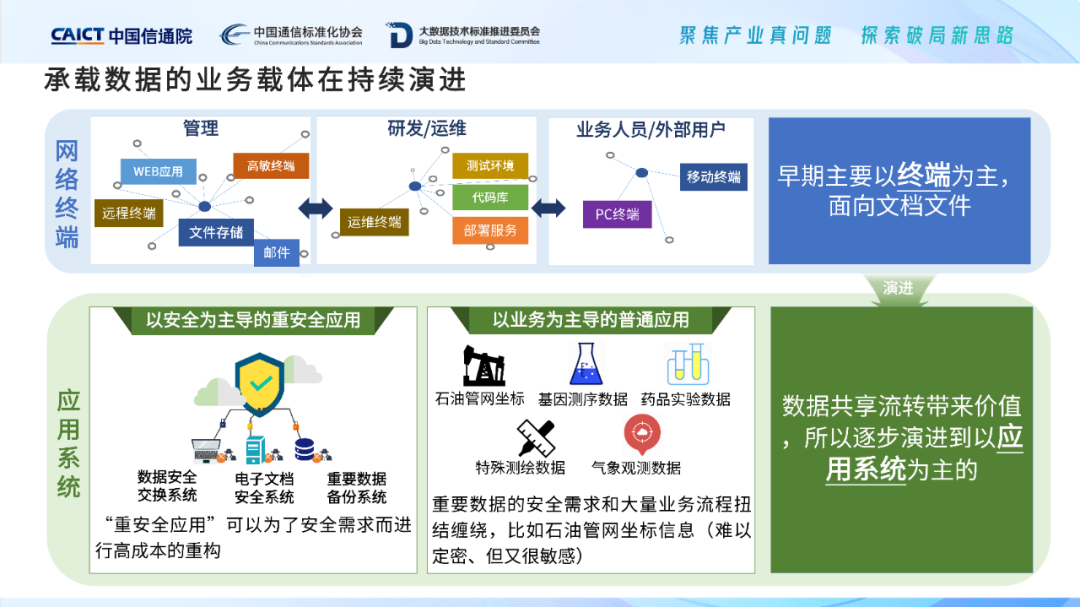
The service carriers that carry data are constantly evolving and upgrading. More than ten years ago, the business carrier of carrying data was mainly based on network terminals, which were oriented to documents and files. The focus of data security construction was to focus on networks and terminals. Today, informatization is booming, data sharing and transfer brings value, and business carriers have gradually evolved to be dominated by application systems, which will also occupy the largest proportion of the budget in the overall construction of enterprise informatization. Enterprise applications are generally divided into two categories, one is security-oriented "safety-heavy applications " , which need to be safe at all costs, and can be refactored at high cost only for security requirements; the other is business-oriented This type of application accounts for more than 90% of the "common applications " , and the security requirements are integrated into conventional business applications, and are entangled with a large number of business processes, such as the coordinate information of the oil pipeline network, which is very sensitive but difficult to identify. When carrying out data security construction for business-oriented common applications, whether it is encryption desensitization, detection response, or audit traceability, it is essentially an application-oriented functional security requirement, which needs to be integrated in the application. However, in actual deployment, it will be found that The coverage of data security is intertwined with the entire data processing process, and the cost of enhancing data security by transforming applications is extremely high and cannot be implemented. In particular, the transformation of a large and complex existing application system is like changing a tire for a high-speed car. It faces huge challenges of high risk, high cost, long cycle, and interruption of operation.

The construction idea turns to focus on data-centric security. The security centered on network attack and defense is turning to "emphasis on data-centered security", and the matching security technology has also evolved from "plug-in" to "embedded". The US Department of Defense Cloud Strategy white paper proposes that information security has historically focused on border defense, that is, restricting network border access, but because data is fully shared today, traditional borders have been broken, so the U.S. Department of Defense will secure security from the border Defense, shifting focus to protecting data and services. On the construction path, review the classic network security attack model MITER.ATT&CK, which stands for Adversarial Tactics, Techniques and General Knowledge. From the perspective of network attack and defense, it protects data by preventing and plugging loopholes. But today's network vulnerabilities are inevitable, so direct protection of the data itself is a more efficient mechanism. Benchmarking the ATT&CK framework, Lianshi tries to propose a DTTACK (data-centric tactics, technology and general knowledge) technical framework from a "data-centric" perspective. It is not a model of network, server or application security, but more emphasis on data Its own security , and the transformation from "responsive" protection to "active" protection of data, emphasizing the enumeration of data protection requirements from the perspective of business risk mapping, can provide data security capability reference for informatization construction and enterprise business architecture design . DTTACK selects six tactics as the basic structure: IDENTIFY (identification), PROTECT (protection), DETECT (detection), RESPOND (response), RECOVER (recovery), COUNTER (countermeasure), and governance as supplementary means. The two frameworks are interrelated, dependent, and superimposed to evolve, forming a "new security construction with equal emphasis on network and data", which has also become the mainstream idea of current enterprise security construction.
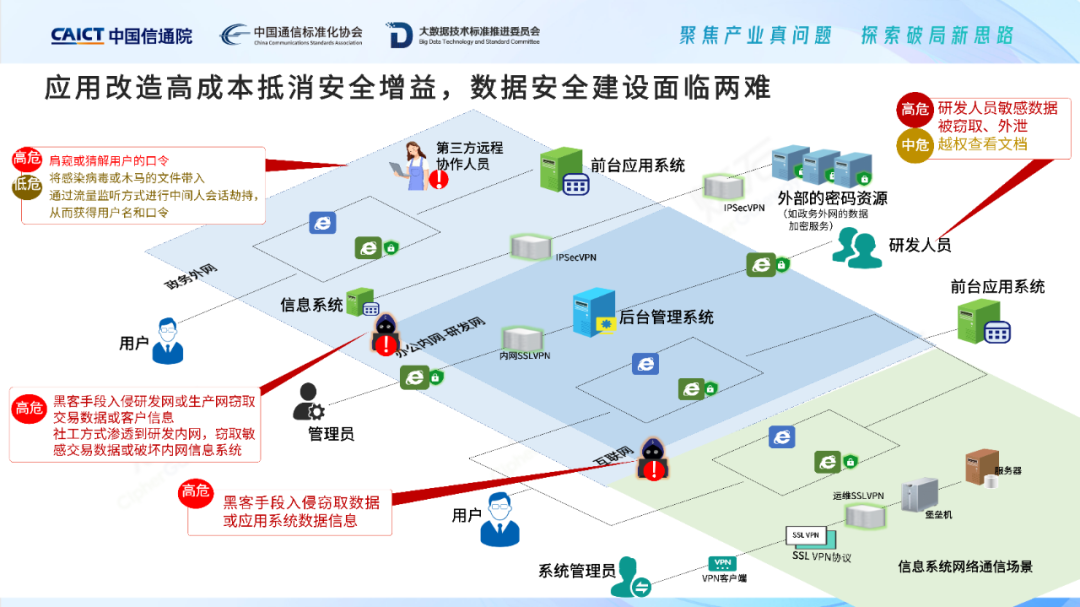
Applying retrofit costs to offset safety gains poses a dilemma. In the digital transformation and the development of the digital economy industry, not only the upgrade of basic software such as CPU, operating system, and database, but also the application software involving a wide range of industries urgently needs to be upgraded and replaced. This is a larger market space, such as PLM/MES/ERP software for manufacturing, Medical industry HIS software, financial industry application software, energy industry application software, transportation industry application software, etc. These huge stocks of application software generally lack built-in password security mechanisms, and lack effective means to enhance password security capabilities, because the failure to crack the development and transformation model is extremely costly, affects business continuity, and has technical feasibility challenges such as source code maintenance. This also means that the high difficulty, high risk, and long cycle brought about by application transformation, coupled with the superposition of complex data security capabilities, make the investment cost of enterprises offset the gains brought by security to a certain extent. There are risks in reforming, and the dilemma of forcing reforms will be fatal".
Sectional data security reshape the offensive and defensive situation

Face-to-face technology realizes the decoupling of security and business technology and the integration of capabilities. Aiming at the difficulties in application transformation when data security is implemented, Lianshi builds AOE face-to-face data security technology, rebuilds security rules on the facet of data flow, deploys security control points, avoids large-scale code modification, reduces costs, and realizes security and business in technology decoupling in terms of capabilities, but also in terms of capabilities. Transformation-free application data security solutions, a data security management platform will be deployed on the bypass road, and structured and unstructured data will be accurately controlled, identified and protected at the data flow control points on the main road. For structured data, transformation-free applications can prevent external data threats on the operation and maintenance side, store encryption to prevent internal DBAs, outsourcing, and hackers; prevent in-app data access threats on the user side, and dynamically desensitize beforehand to prevent unauthorized access by business personnel. In-process risk monitoring and early warning of business personnel’s risky operations, post-event auditing and traceability of business personnel’s data leakage, forming an integrated password security protection system. For unstructured data, the security control point can be deployed in the kernel mode or user mode, and through file-by-file and key-by-key file transparent encryption, the control over file reading and writing can be mastered, and disk encryption, disk reading decryption, and access audit can be realized wait.

Innovative transformation-free data protection capability matrix. Lianshi actively explores the concept and practice of data security defense in depth, adheres to original self-research and continuous iteration, and creates "one platform: main data security platform, multi-module: identification, protection, detection/response, recovery, audit/traceability and other security capability modules "The matrix of data security products covers data transformation-free control points in different processing links, enabling horizontal coverage of extensive applications and vertical superimposition of multi-level security capabilities. The innovative transformation-free data protection capability matrix can apply anti-bypass dynamic protection on data control points, and is committed to becoming an important support for users to improve their actual combat capabilities. On the one hand, it can realize user-oriented reconstruction of security rules. Only users who meet the authority can access the data they should use; combined with risk monitoring of business scenarios; high-confidence audit that can assign responsibilities to people. On the other hand, in order to reconstruct the data boundary for operation and maintenance, no one can obtain the plaintext information of sensitive data from the application background. In this way, attackers can neither directly obtain sensitive data from the operation and maintenance side nor obtain unauthorized sensitive data from the user side, so that both data flow and security protection can be achieved. At present, Lianshi has established a mature and standardized product and delivery system, which can meet the needs of business scenarios such as personal information protection, business secret protection, data security compliance transformation, and national secret compliance transformation.
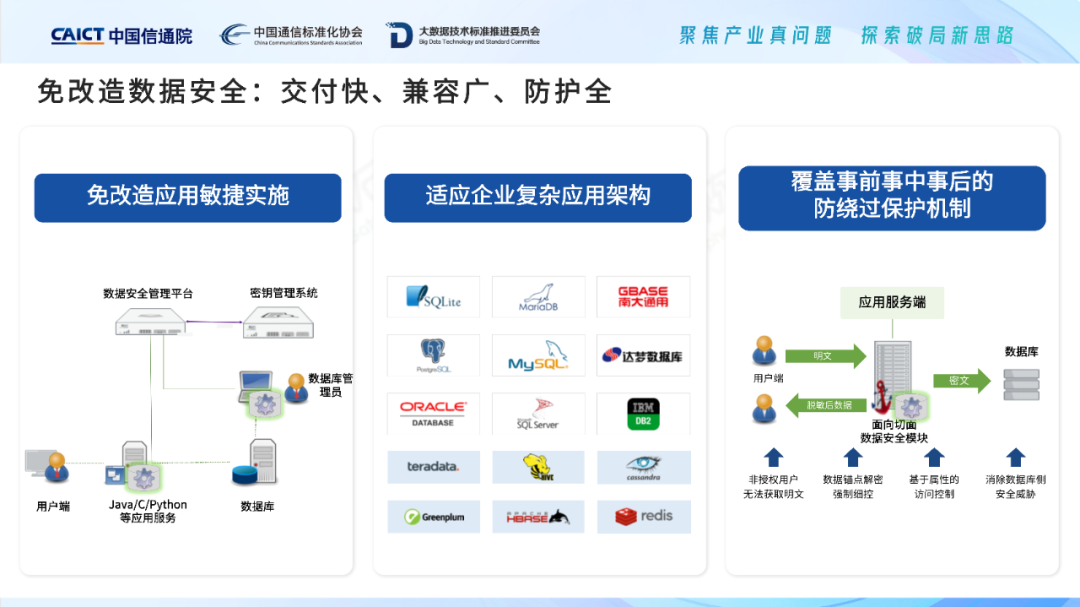
The smelting-free transformation solution has fast delivery, wide compatibility, complete protection, and accurate management and control. Delivery is fast , and data security protection capabilities are enhanced through transformation-free applications to achieve agile delivery. Wide compatibility , suitable for a wide range of application architectures, such as JAVA, C and other mainstream development languages, relational databases and non-relational databases compatible with open protocols, compatible with Linux/Xinchuang OS/Windows, etc. Complete protection , password security integration, Lianshi free of modification data security products are oriented to application systems, and use data as the starting point to realize data security protection at the application layer, achieving the actual protection of "password security integration". Accurate management and control , flexible adaptation to business data flow, Lianshi transformation-free data security products can create fine-grained protection with application as the unit; Lianshi data security control point module can flexibly configure encryption, decryption, desensitization, etc. according to business data flow direction Security rules can provide fine-grained data transfer authority control in complex data analysis scenarios such as OLAP; further, the product module can obtain the identity information of visitors in the current application, so as to realize "subject-to-person, object-to-field" fine-grained Granular access control.
In order to jointly promote the development of the data security industry, colleagues in the industry are welcome to join the “[Alchemy] Data Security Technology Circle” WeChat group to discuss technical experience and regulatory trends in the field of data security.

Follow gongzhonghao: Refining Stone Network CipherGateway, and reply the keyword " Stone Refining is Data Security 057 " in the background , you can package and download the high-definition PDF version of the keynote speech "Reshaping Data Security from a Business Perspective".