Introduction | In the digital age, network security has become the top priority of enterprise development. Through systematic security construction, enterprises can calmly deal with increasingly complex network security challenges. Today, we specially invited Mr. Tan Xiaosheng, the TVP of Tencent Cloud and the chairman of Cyberyingjie Technology. He will explain how to plan enterprise network security construction with architectural thinking from the perspective of senior technical experts, and provide inspiration and thinking for current and future network security construction. .
About the Author

Tan Xiaosheng, Tencent Cloud TVP, founder, chairman, and senior engineer of Beijing Saibo Yingjie Technology Co., Ltd., founder of Zhengqi Academy Network Security Entrepreneurship Camp, former 360 Group Technology President and Chief Security Officer, won the Ministry of Industry and Information Technology in 2020 The title of the first batch of network security innovation and entrepreneurship mentors in the Network Security Industry Development Center. In 2018, he was awarded the title of Network Security Outstanding Talent by the China Internet Development Foundation. He is the director and deputy secretary-general of the China Computer Federation (CCF), the secretary-general of CCF YOCSEF, and was awarded the Zhongguancun High-end Talent in 2012. The title of leading talent, a member of the Ministry of Education's Safety Science and Engineering Professional Teaching Advisory Committee.
1. Digital transformation promotes the improvement of cybersecurity legislation
Digitalization has become an irreversible development trend. In recent years, the Internet of Everything has become a mainstream trend. Digital transformation is no longer a partial application of technology, but has gradually evolved into a trend that affects the operation mode of the entire society.

Since 2016, the country has successively promulgated relevant laws and regulations such as the "Network Security Law", "Personal Information Protection Law" and "Data Security Law", especially the promulgation of the "Network Security Review Measures" promulgated last year, which means that the network Security-related legislation is gradually improving. With the promulgation of the more stringent "Personal Information Protection Law" and "Data Security Law", network security, as a sharp sword for government supervision, has ensured the security of more fields.

2. Enterprise architecture methodology guides network security construction
Although the above-mentioned legal and regulatory documents have clarified many regulations, responsibilities and obligations, the support at the technical and product levels is still insufficient, and the specific implementation methods are not clear enough, causing enterprises to still face many difficulties in building network security. In my opinion, The main difficulties in enterprise network security construction are as follows:
- Cloud computing, Internet of Things, and wireless Internet lead to the generalization of enterprise network edges, and the traditional border defense thinking becomes invalid;
- Widespread adoption of open source software raises software supply chain security concerns;
- The Internet of Things brings difficulties in terminal security protection;
- Security talents are scarce and costly, and effective data security solutions are lacking.
Under the current circumstances, especially for large enterprises, it becomes more urgent to build their own network security defense line. Due to the storage and sharing of large amounts of data and sensitive information, cybersecurity has become a crucial area in the development of enterprises. Only by implementing an overall network security strategy and adopting the latest network security technology, can enterprises ensure that their network systems are more secure and reliable, and gain advantages in possible security threats.
It is worth mentioning that the enterprise architecture methodology can play a very good guiding role in the construction of enterprise network security. In fact, the idea of enterprise architecture has experienced the development and evolution from Zachman proposed in 1987 to TOGAF, FEA and DoDAF and other enterprise architecture models, and these ideas have been widely used in traditional enterprise application development.

According to the TOGAF architecture development method, the construction of enterprise architecture needs to follow the following steps: first, start with business architecture, build information system architecture and technical architecture, and always pay attention to demand management. Throughout the process, it is also necessary to fully consider the corporate vision, mission, values and other aspects. This kind of thinking is consistent with the development of enterprise management thinking in the past 30 years. Enterprises need to pay attention to development goals and business scale, while informatization and security are also crucial.

When using the TOGAF development method to design an enterprise architecture, the following steps need to be followed: First, clarify the vision and mission of the enterprise, determine the values and business of the enterprise, then formulate the business architecture, and then pass the corresponding information system architecture and technical architecture, and finally use the Requirements management is the center to manage it. These steps reflect the fundamental principles of enterprise management thinking, that is, first clarify the mission and goals of the organization, and then carry out informatization and security construction according to business needs. During this process, an organization can realize comprehensive planning and management from business to technical architecture according to the TOGAF development method system.
In addition to the TOGAF model, IBM's approach to architecture is similar, also emphasizing identifying an organization's capabilities and business architecture in support of the enterprise's vision, mission, and values. This approach helps enterprises plan informatization and security construction, and ensures that they can better support business needs.
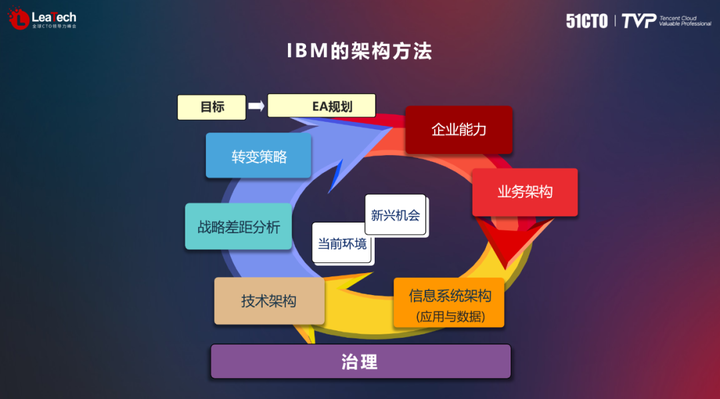
The refinement of the enterprise architecture includes determining the application and data architecture to support the information system architecture to better support business needs. Finally, it is necessary to consider the technical implementation plan and carry out governance work to ensure the effective implementation and continuous improvement of the enterprise architecture.
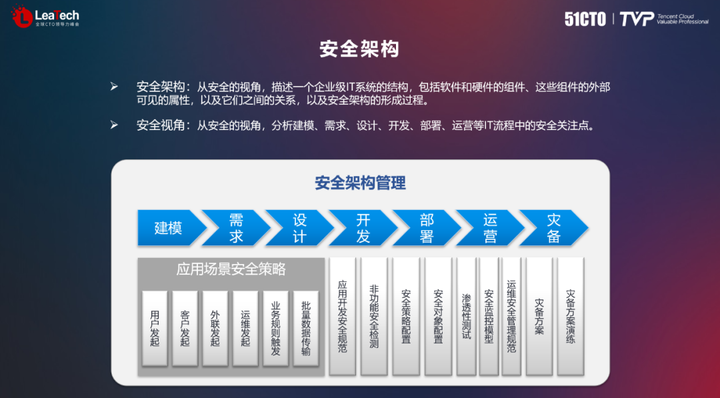
In today's large enterprises, security systems are facing increasingly complex situations, and it is necessary to consider how to effectively integrate and work together with security components, and conduct integration and operation and maintenance management. Enterprises should also treat security as a business, and view security architecture design as part of enterprise development for planning and implementation. Security architecture design includes modeling, requirements analysis, design development, deployment, and operation, etc. It needs to be planned and implemented in strict accordance with the standards of enterprise architecture design.
In my opinion, applying EA methodology to the field of network security and realizing the evolution from fragmented construction to systematic construction through planning is the top priority of building a new "capability-oriented, architecture-driven" security system. When we apply the enterprise architecture (EA) methodology to the field of network security, it needs to be regarded as a complete process, including the construction process of the architecture and the planning at the security strategy level. In this process, the left side of the figure below represents the process of EA architecture construction, while the far right represents the planning of security strategy, which is also an important part of enterprise architecture design.
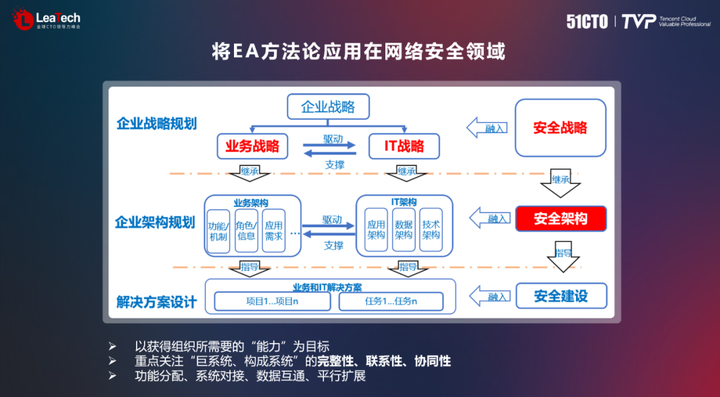
In order to achieve the goal of transforming from fragmented construction to systematic construction, the IT strategy of the enterprise needs to support the business strategy, and the integration of the security strategy is as important as the business construction. For example, when planning future security for a bank, we need to consider changes in future business requirements and open models, and we need to adopt cloud-native technology to ensure security testing in agile development.
In order to build a new "capability-oriented, architecture-driven" security system, we need to integrate technology, operation, and management capabilities, and form a new management, technology, and operation capability system to focus on demand management and formulate a new security system , decomposed into a number of key projects and initiatives.
In the design of security architecture, we should consider the principles of business-driven, service-oriented and security-oriented operations to achieve the requirements of agility, efficiency, cloud-native friendliness, usability, portability, flexibility and scalability, and balance the proportion of outsourcing and self-development , reuse the construction of the existing system, realize resource sharing and monitoring functions, and realize the collaborative linkage of the system.
3. Interpretation of the classic network security model
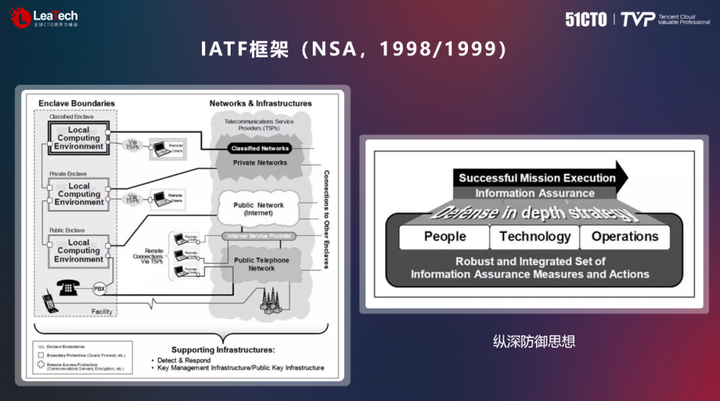
In the past two decades of development, a variety of models have emerged in the security industry, such as the P2DR model, the IATF framework (NSA, 1998/1999), etc. Among them, the classic P2DR model (Prevent, Protect, Detect, Respond) is Turn security into a protective behavior, including policy, protection, detection and response. The IATF model is a security model that adopts the idea of defense in depth. In addition, the NSA launched the CGS framework model in 2014, which mainly adopts the kill chain model and divides the network intrusion process into seven steps. According to this model, as long as the attack is detected or intercepted at any step in the attack process, the attack can be successfully prevented.
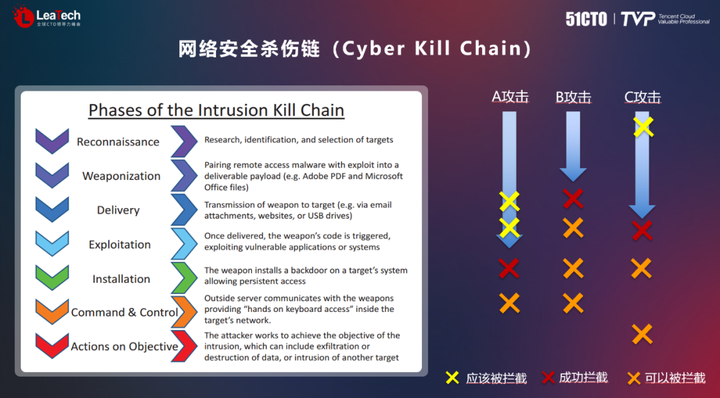
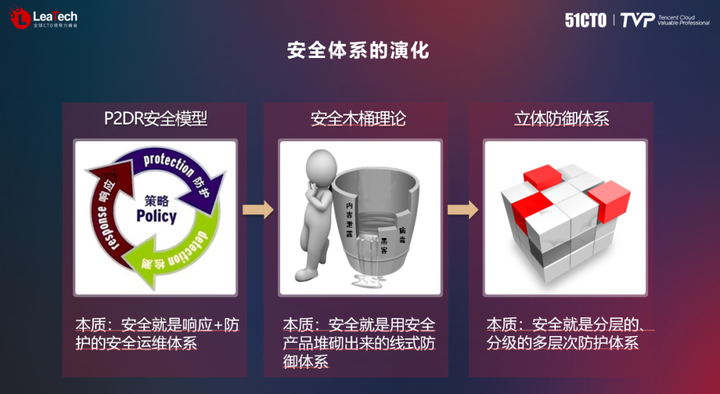
Today's various models have an important impact on the security field. From the P2DR model to the security barrel theory, the security field has experienced tremendous development. The 360 Information Security Department recruits hackers and engineers to build a defense line, and through effective network security operations, only a handful of security components are used to implement defense solutions. Therefore, when we choose a security defense solution, we need to consider the appropriate utilization of resources and cost-effectiveness to meet actual needs.
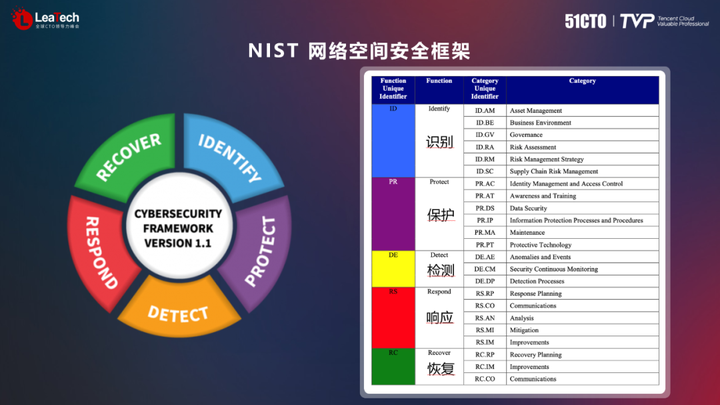
NIST subsequently proposed the CSF cyberspace security framework, which is a classic idea of three-dimensional defense. The framework divides cybersecurity efforts into five steps: identify, protect, detect, respond, and recover. This framework can be used to benchmark cybersecurity defense efforts, and under each step there are many subcategories to explore and find ways to implement measures.
ATT&CK (MITRE, 2013-) is a security model that enumerates various TTP (tactics, techniques, and procedures) means that an attacker can use. When defending, it can be compared with each attack method and strategy listed in the ATT&CK model to determine whether effective defense can be carried out in the defense line.

Gartner's security model - CARTA, emphasizes the need for a balance between business development speed and security, rather than the pursuit of absolute security. When facing risks, we need to assess whether we have sufficient coping capabilities, but we should not focus too much on risk defense, because this may slow down the speed of business development. In the CARTA model, it is emphasized that it is necessary to take appropriate defensive measures based on a dynamic assessment of current risks and find a balance between security and business development.

With the evolution of business development and operations, a whole new term "DevSecOps" has emerged. Under this idea, the development and operation and maintenance work is iterated periodically, and security is an important guarantee for the entire development and operation and maintenance process, emphasizing the close integration of security, development and operation and maintenance to achieve more efficient and safer business operations .
It is worth noting that we can introduce the sliding scale model and the Cyber Defense Matrix (Cyber Defense Matrix) to improve the cyber security capabilities of enterprises. The sliding scale model divides network security defense into four steps:
- Infrastructure security: Including missed allocation and management of data resources and data assets.
- Defense in depth: install and configure security products, such as EDR, anti-virus software, and firewalls, to achieve automated defense.
- Situation awareness and active defense: participate in security operations, and judge and respond to system information.
- Threat intelligence: Obtain external threat intelligence, unite its own defense lines and actively respond.
- Countermeasures: Countering attackers, including actions such as joint law enforcement and condemnation.

In the sliding scale model, the farther to the left the enterprise can control and grasp to the greatest extent, while the farther to the right requires the support and intervention of external resources and government forces. The core idea of this model is to sort the work that the enterprise can control from left to right, and start from the leftmost when resources are limited. At present, the sliding scale model has been widely used and respected by many domestic security companies.
The Cyber Defense Matrix (Cyber Defense Matrix) is another tool to ensure enterprise network security. It is also called the CDM model. It combines the five steps of IDPRR with the five dimensions of equipment, applications, networks, data, and users to form A defense matrix with five rows and five columns and a total of 25 grids. The protection steps on the left are carried out before the identification, that is, the data assets are identified and the various lines of defense are established, and the three columns on the right are the detection, response and recovery steps that are carried out after the incident. This model, combined with a sliding scale model, provides a better understanding of the security efforts that need to be made.
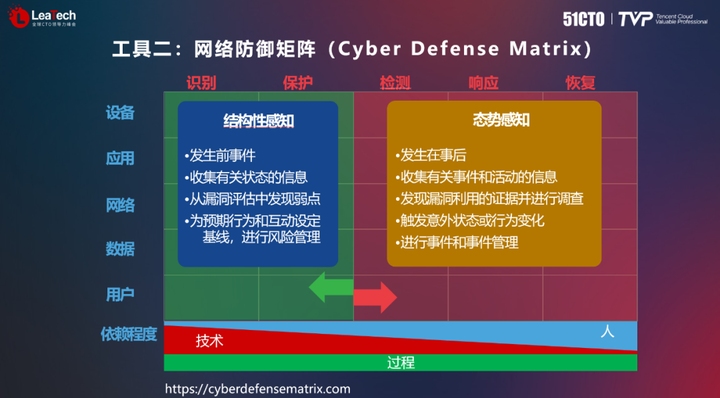
In network security work, network security capability components can be combined and abstracted to obtain more than 200 types of security capability components. complex. In order to make better use of these components, we try to extract capabilities that are quite different from other capabilities and categorize them into modules such as infrastructure security, defense in depth, active defense, and threat intelligence. These capabilities build a complete infrastructure security system.
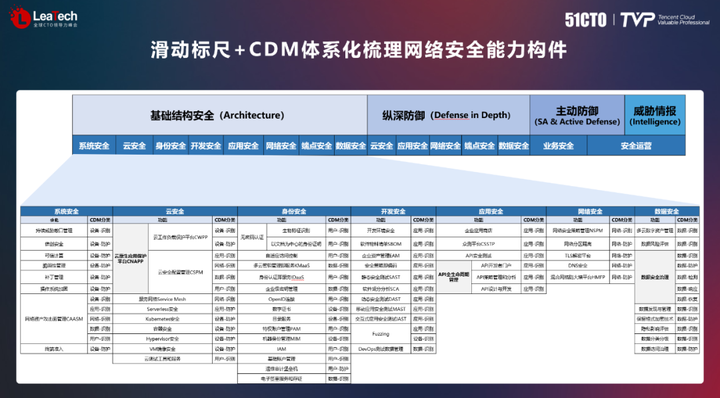
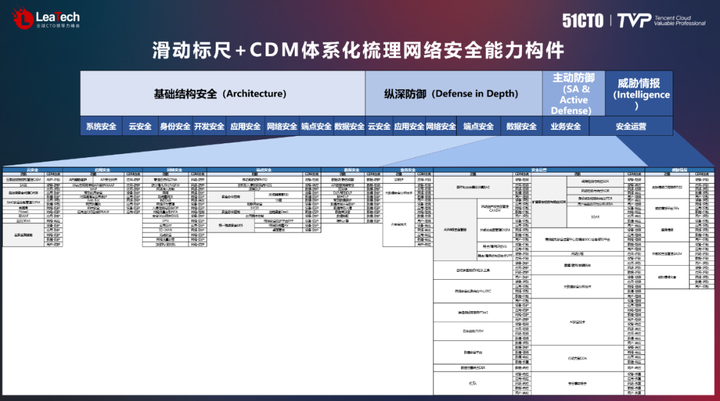
4. Explore the future of network security construction
In the past two years, network security operations have gradually received more and more attention from the industry. The CSMA security logical architecture proposed by Gartner is an architecture that can support network security operations. In the figure below, we can clearly see that it includes security analysis and intelligence on the left and various security products on the right. Large enterprises need to build their own security analysis and intelligence systems based on commercial customization. Various security products on the right need to enter the middle of security analysis and intelligence systems through standardized interfaces, and combine external threat intelligence and other third-party APIs for analysis. Ultimately achieve unified policy management.
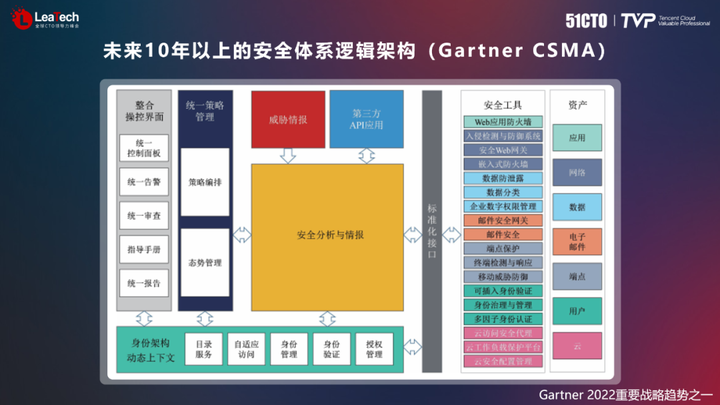
The foundation of the enterprise is the dynamic context of identity architecture, known as zero trust. Identity and context rights management and access control framework for policy requirements. At the end of 2022, the implementation plan of the zero trust strategy proposed by the U.S. Department of Defense has an eight-year time span, covering dozens of standard modules. In this framework, it is necessary to establish a dynamic context-based access control architecture and transform existing business systems. It was a complex and difficult task that required constant research and innovation during construction.
Network security construction trends in the past two years include: BizDevSecOps agile development, XDR extension detection response, intrusion attack simulation, attack surface management, security operation services, software supply chain development security, data security platform, cloud native application protection, secure access services Edge and API security protection, etc. These technical solutions can help enterprises effectively respond to various security threats and attacks, and protect critical properties and assets from unknown attacks.
With more data and sensitive information stored in the cloud, cybersecurity has become an important issue in the digital age. Enterprises must have a deep understanding of various security threats and attacks, and seek innovative network security technologies to counter these threats. Only in this way can enterprises ensure more security and reliability in the digital age, while maintaining the sustainability of their own business.
As the foundation and premise of the development of the digital economy, network security requires the joint efforts of the whole society and the cooperation of the government and enterprises to solve its problems. The government should strengthen network security supervision and legislation to promote the development of the network security industry. At the same time, enterprises should also strengthen network security investment and cooperation, improve the overall level of network security, and provide protection for the development of the digital age.