Author: BSXY_19 Jike_Chen Yongyue_Updated in July 23
BSXY_School of Information_v:CwJp0403
Note: Reposting any content without permission is prohibited
Notes description: Currently there are only notes, and other resources will be
updated in the near future .

Note: For software sharing and resource description, please see the preface and resource download instructions
Soft test advanced network planning test notes (involving forms replaced by pictures_about 90,000 words)
- Preface and Resource Download Instructions
- Chapter 1 Computer Basics
-
- 1. Data representation
- 2. Logic computer
- 3. Composition and system of computer system
- 4. Bus system
- 5. Command system
- 6. CISC and RISC instructions
- Seven, computer classification (Flynn)
- 8. Storage system
- Nine, disk array RAID
- 10. Cloud Computing and System Reliability
- 11. Computer software knowledge
- Chapter 2 Principles of Computer Networks
- Chapter 3 Internet Protocol
- Chapter 4 Computer Network Planning and Design
- Chapter 5 Network Resource Devices
- Chapter VI Network Security
- Chapter VII Standardization and Legal Regulations
- Chapter 8 Network Product Solution
Preface and Resource Download Instructions
There are only notes at present, and other resources will be updated in the near future . (Note 5.5 is enough. If you are not sincere, you can go to other places to find it yourself. The verification message is: Advanced Network Planning)

Maybe you bought it from other places or other The various notes that come here are a few or even dozens of files that are not well-typeset for you to read and find slowly by yourself. There is only one file for the note here and it can be edited even if it is small in size. If you use WPS cloud document, you can also upload it to your own cloud document. The typesetting is also OK, and it can be read and viewed well even if it is printed out.
Chapter 1 Computer Basics
1. Data representation
(1) Fixed point, floating point and integer
- Numbers represented by fixed-point notation (called fixed-point numbers) are often divided into fixed-point integers and fixed-point decimals.
- In fixed-point notation, the decimal pointNoneed to occupy a storage bit
- Floating point representation withexponent codeandmantissato represent numbers, called floating-point numbers
- Given the same total number of digits, floating-point notation can representbiggernumber
- The maximum value of a fixed-point integer is: 2n-1-1
- The maximum value of fixed-point decimals is: 1-2-(n-1)
- Positive number: 0; Negative number: 1; Original code –> Binary value

- Original code and inverse code representation range: -127~+127 Complement code and shift code representation range: -128~+127
(3) Value range
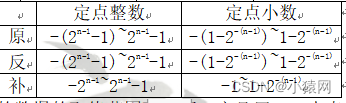
- Note: The value range of the data appearing above may not necessarily use n-1 to represent the data. In the above table, changing all n-1 to n may also appear, such as: the original/inverse range of the fixed-point integer is -(2n-1-1) 2n-1-1, at this time can also be transformed into -(2n-1) 2n-1
2. Logic computer
- Black box testing focuses on testing the functional requirements of the software. Black box testing tries to find the following types of errors:Function errors or omissions、interfacewrong data structure orexternal databaseAccess errors, performance errors, initialization and termination errors
- In white box testing, the white box can find: errors in the code path, infinite loops, logic errors
- The white box testing approach should be based on the program'sinternal logicandSpecified Coverage CriteriaDetermine test data
- In white box testing: statement coverage requires designing enough test cases so that each statement in the program is executed at least once. Compared with decision coverage, condition coverage increases the test of the condition that meets the decision and increases the test path. The disadvantage of decision coverage criterion is that it does not consider the combination of conditions
3. Composition and system of computer system
(1) Central processing unit CPU

- ALU arithmetic unit, general-purpose registers, status registers, program technology devices, accumulators and other components are all components in the CPU
- The CPU generates the operation signal of each instruction and sends the operation signal to the corresponding components for control
- In addition to storing the instruction address, the program counter PC,NoArithmetic/logic operation results can be temporarily stored
- The program counter PC is used toThe address of the unit where the next instruction is stored。
- The controller in the CPU determines the automation of the computer's running process
- The instruction decoder is a component in the CPU controller
- in the CPU fortrackThe register of the instruction address is == (program counter (PC) (belonging to the controller component of the CUP) ==
- general purpose registerIt is often used to temporarily store the data or operation results required by the calculator
- The address register (MAR) and the data register (MDR) are used for address and data temporary storage when accessing memory
- == Instruction Register (IR) == Used to temporarily store the instructions being executed
- In the CPU, it is often used forThe ALU performs arithmetic and logic operations to provide data and temporarily store the results of the operation in the register (accumulation register)
- The computer CPU accesses it the fastest (general purpose register)
- registers are used forTemporary storageInformation about addressing and calculation procedures. Divided into: accumulator, general-purpose registers, other registers
- Accumulator: It is a data register, which is always temporarilyStore operands and intermediate operation results. is a general purpose registerkind of
- General-purpose register set: It is a set of working registers in the CPU forscratch operand or address
- Other registers: flag register, instruction register
- adderIs a part of the arithmetic logic operation unit
- The purpose of the instruction system using different addressing modes is (Extends addressable controls and increases programming flexibility)
- In order to facilitate the realization of multi-level interrupt nesting, use (the stack) to protect breakpoints and live most effectively
- CPU interrupt response time refers to (From issuing an interrupt request to starting to enter the interrupt handler)
- The maximum throughput depends on the time required for the slowest segment of the pipeline
- If there is a break in the pipeline, the speedup ratio will drop significantly
- To maximize speedup and efficiency should use the same run time for all stages of the pipeline
- Pipeline adoptsAsynchronous control does not improve pipeline performance, but will increase the complexity of the control circuit
- CPU main frequency (working frequency) = FSB (external clock frequency) × frequency multiplier (multiple of main frequency and FSB) such as = 400MHzx3 = 1.2GHz.
- For database systems, it mainly includes CPU/memory usage, performance of query statements,Process thread usage status, log file size, etc.
(2) Composition principle
- I/O interface compilation is divided into: unified compilation and separate compilation.Unified compilationpassaccessInstructions from the memory unit access the I/O interface.Prepared separatelyneedSet special I/O instructions to access I/O interface
- The bus structure is adopted in the computer system, which facilitates the building block structure of the system, and at the same time (Reduce the amount of information transmitted)
- Pipelining cannot improveExecution of instructionsspeed
- The bus width refers to the number of lines of the bus, that is, the parallel transmission capability of data signals, and also reflects the physical space and cost occupied by the bus; the bus bandwidth refers to the maximum data transmission rate of the bus, that is, the total amount of data transmitted per second. The bus width and the clock frequency together determine the bandwidth of the bus.
- Bandwidth (MB/S) = clock frequency (MHz) / clock cycle × bus width (bit) / 8
- Parallel bus is suitable for short-distance high-speed data transmission
- Serial bus is suitable for long-distance data transmission
- The single-bus structure adapts to different types of devices on one bus, but cannot meet high performance requirements
- Dedicated bus designed to optimally match connected devices
- Intermediate code can be represented by trees and graphs
(3) Hardware foundation
- SSD is essentially (Flash) memory
- The common interfaces of SSDs are: SATA, PCle, M.2
- (associative memory) refers to memory accessed by content
- After the flash memory is powered off, the information will not be lost, and it is a non-volatile memory; the deletion operation is performed in units of blocks; it is used to replace the ROM memory in embedded systems
(4) Basics of computer systems
- Computer instructions generally include two parts: operation code and address code, which is an instruction for analysis and execution, among whichopcodeandaddress codeshould be stored in the Instruction Register (IR)
- The number of bits in the instruction register depends on (instruction word length).
- Instruction cycle: the time required to fetch and execute an instruction
- Bus cycle: the time it takes for the CPU to access a byte from memory or I/O interface
- Clock cycle: the smallest unit of CPU processing action
- Interrelationship: One instruction cycle can be divided into one or more bus cycles; one bus cycle can be divided into several clock cycles
- Main frequency (clock frequency): refers to the number of pulses output by the computer CPU per unit time. It largely determines how fast your computer will run. The unit is MHz
- Word length: Refers to the number of bits of binary data that can be processed simultaneously by the computing unit of the computer. The word length determines the computing precision of the computer.
- In project cost management, cost budgeting allocates total cost estimates to activities and work packages to establish a cost baseline.
(5) Equipment/project management
- If the I/0 interface and the main memory of a computer system are uniformly compiled, the input operation is completed through the == (memory access) == instruction
- The workflow of project risk management is (Risk identification, risk analysis, risk control, risk transfer)
- RUP (4 phases) emphasizes adoptioniteration and incrementway to develop software. The benefit: critical, high-impact risks can be addressed early in software development
- About agile: the agile method believes that individuals are better than tools; agile development is a people-centric, iterative, step-by-step development method; extreme programming is a well-known agile development method; agile methods are "adaptive" rather than " Presupposition”; Agile development method is an iterative and incremental development method
4. Bus system
- The bus system can be divided into:databus DB,addressBus AB,controlbus
- Broadly speaking, any wire that connects more than two electronic components can be called a bus. Generally can be divided into 4 categories:
- ① On-chip bus. Used for the connection of various parts inside the integrated circuit chip.
- ② component level bus. It is used for the connection of various components in a circuit board.
- ③Internal bus, also known assystem bus. It is used to form the connection of various components of the computer (CPU, memory and interface, etc.).
- ④External bus, also known as communication bus. Connecting or communicating with a computer to a peripheral or computer to computer.
- The bus connecting the processor, memory and other components of the processor belongs to the internal bus, which is divided into data bus, address bus and control bus according to the content transmitted on the bus
- The CPU responds to the DMA request by being ina bus cycleWhen it ends
- In DMA working mode, establish direct data communication between main memory and peripherals
- Bus: Parallel bus is suitable for short-distance high-speed data transmission; serial bus is suitable for long-distance data transmission; dedicated bus can be designed to achieve the best match with connected devices
5. Command system
1. The command is issued byopcodeandaddress codecomposition, the instruction length is divided intoFixed lengthandvariable lengthTwo kinds
2,address immediately: commandedaddress codeThe field given is notthe address of the operandbutthe operand itself. It is characterized byOne memory access removes both instructions and operands
3、Indexed addressing: the address of the operandby someoneThe contents of the index registeranddisplacement addition
4、Direct Addressing (Register Addressing): commandedaddress codefield givenThe address of the storage unit where the operand is located (register number)
5、Indirect addressing (register indirect addressing):the address of the operandyesContents of memory locations in main memory (registers)
6. CISC and RISC instructions

Seven, computer classification (Flynn)

8. Storage system
(1) Hard disk
- disk schedulingmanagement, usuallyFirstconductarm recoveryscheduling,Againconductto rotatescheduling
- There are two types of storage media for SSD solid-state drives. One is to use flash memory (FLASH chip) as the storage medium, which is the mainstream. The other is to use DRAM as a storage medium.
(2) Cache
- The function of Cache: increase the rate of CPU data input and output, break through the so-called "von Neumann bottleneck", that is, the bandwidth limitation of data transmission between CPU and storage system
- In the computer storage system, Cache is the fastest access level
- The basis for using Cache to improve system performance isThe principle of program locality
- If h represents the access hit rate of the Cache, t1 represents the cycle time of the Cache, and t2 represents the time of the main memory. Taking the read operation as an example, the average cycle of the system using "Cache+main memory" is t3, then:
- t3=h×t1+(1-h)×t2
- Where (1-h) is also called failure rate (miss rate)
- The design idea of Cache is to improve the hit rate at a reasonable cost
- The mapping exchange between Cache and main memory is done automatically by hardware.
(3) RAID technology
- RAID0 disk utilization is 100%
- RAID1 utilization rate is 50%,
- RAID3, disk utilization (n-1)/n, with specific parity disk, high reliability
- The RAID5 disk utilization ratio is (N-1)/N, and the minimum value of N is 3. There is no specific verification disk, and the verification data is stored scattered on each disk. High reliability.
- RAID6 disk utilization (N-2)/N, where the minimum value of N is 4.
- RAID10: the combination of RAID1 and RAID0, first mirroring and then striping
- RAID01: The combination of RAID0 and RAID1, striping first and then mirroring
(4) Main memory
- The main memory is referred to as the main memory or the internal memory. It is located in the host computer or on the motherboard, and is used to store the programs and data needed for the current operation of the machine in order to provide information to the CPU. Compared with external storage, it is characterized by small capacity and high speed.
- Main memory consists mainly ofmemory bank、Control lines, address registers, data registers and address decoding circuitsand other partscomposition。
- The main memory of a computer system is mainly composed of (DRAM)constitute
- The main purpose of using a hierarchical storage system for computers is to solve the contradiction between storage capacity, cost and speed
- There are two types of random access memory (RAM): static (SRAM) and dynamic (DRAM),SRAM比DRAM速度更快,但也贵得多。SRAM用来作为高速缓冲存储器(Cache),DRAM用来作为主存及图形系统的帧缓冲区。
- PROM是可编程ROM,只能够一次一次写入,需要特殊电子设备进行写入
- EPROM是电可擦除可编程只读存储器。
- E2PROM是电可擦除EPROM,可以写入,但速度慢
- 闪存存储器,其特性介于EPROM与E2PROM之间。但不能进行字节级别的删除操作
- CAM(相联存储器):是一种特殊的存储器,是一种基于数据内容进行访问的存储设备。其速度比基于地址进行读写的方式要快
- SAN是一种连接存储管理子系统和存储设备的专用网络。SAN分为FC SAN和IP SAN,其中FC SAN采用光纤信道技术互联;IP SAN采用以太网技术互联;SAN可以被看作是数据传输的后端网络,而前端网络则负责正常的TCP/IP传输
(五)存储系统/内部存储/外部存储:

- 常见的虚拟存储器由(主存-辅存)两级存储器组成
- 栈区和堆区也称为动态数据区,全局变量的存储空间时候静态数据区
- 一个运行的程序对应一个进程,需要相应的存储空间;一个进程可以包含一或多个线程
九、磁盘阵列RAID
- 可以同时对多个磁盘做读写动作,但不具备备份和容错能力,价格便宜,写入速度快,但是可靠性最差,磁盘利用率100%(条带)
- 优缺点/领域:不会占用太多CPU资源设计、使用和配置比较简单;无冗余,不能用于对数据安全性要求高的环境;视频生成和编辑、图像编辑
2、RAID1技术: - 使用磁盘镜像技术,使用效率不高,但是可靠性高,利用率为50%
- 优缺点/领域:具有100%数据冗余;开销大,空间利用率只有50%在写性能反面提升不大;金融、财务等高可用、高安全的数据存储环境

十、云计算与系统可靠性
- 云计算的模式主要有三种:IaaS(基础设施即服务);SaaS(软件即服务);PaaS(平台即服务)
- 失效率:产生故障的概率。
- 平均无故障时间MTBF:相邻两个故障间隔时间的平均值,越大越好。
- 平均故障修复时间MTTR:修复一次故障所时间的平均值,越小越好。
- 可用性:系统的可靠性。
十一、计算机软件知识
- 对于数据库系统,主要包括CPU/内存使用状况、查询语句性能、进程/线程使用状态、日志文件大小等。对于应用系统,主要包括应用系统的可用性、响应时间、并发用户数、特定应用资源占用等。
- 垂直式重用:指在一类具有较多公共性的应用领域之间进行软件重用,大多数软件组织采用这种重用形式。
- 水平式重用:用不同应用领域中的软件元素,例如数据结构、分类算法、人机界面构件等。
- 喷泉模型描述的是面向对象的开发过程,反映了该开发过程的迭代和无间隙特征。
- 软件开发测试:
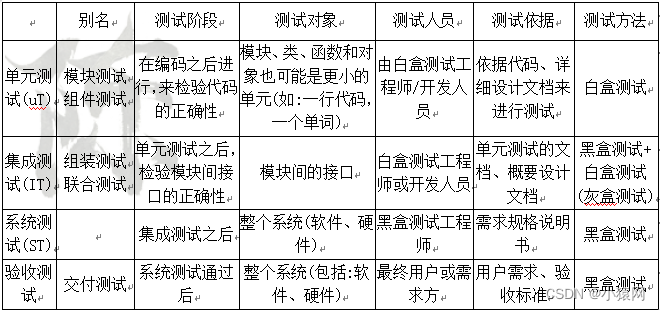
- 数据库事务四个特性:原子性;一致性;隔离性;持久性
第二章 计算机网络原理
一、计算机网络基础知识
(一)计算机网络概念与组成
1、计算机网络概念:计算机网络是指将地理位置不同的具有独立功能的多台计算机及其外部设备,通过通信线路连接起来,在网络操作系统、网络管理软件及网络通信协议的管理和协调下,实现资源共享和信息传递的计算
2、计算机网络与多终端系统的区别:传统的多终端系统是由一台中央处理器、多个联机终端及一个多用户操作系统组成。在多终端系统中,主机与其连接的终端或计算机之间都是支配与被支配的关系。终端只是主机和用户之间的接口,它本身并不拥有系统资源,不具备独立的数据处理能力。系统资源全部集中在主机上,数据处理也在主机上进行。计算机网络系统是以许多独立的计算机为基础。每台计算机可以拥有自己的资源,具有独立的数据处理能力。网络中的计算机可以共享网络中的全部资源。
3、计算机网络的组成可以分为三部分:硬件、软件、协议。硬件是计算机网络的基础(如服务器、客户机、网卡、调制解调器Modem、集线器Hub、交换机、路由器、网桥、中继器Repeter);软件主要有网络操作系统和各种工具软件;协议由语法、语义和时序三部分构成,语法规定了传输数据的格式,语义规定发出何种控制信息,完成何种动作及作出何种应答,时序规定了各种操作的顺序关系谁先谁后
4、计算机网络功能组成
1)从功能上,计算机网络由资源子网和通信子网两部分组成。资源子网完成数据的处理、存储等功能通信子网完成数据的传输功能资源子相当于计算机系统(硬件),通信子网是为了联网而附加上去的通信设备,通信线路等
2)从工作方式上,可以认为计算机网络由边缘部分和核心部分组成
(二)计算机网络的分类
1、按分部范围分类
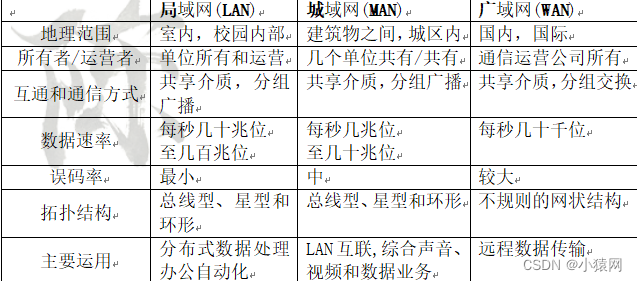
2、按拓扑结构分类:星型、环型、总线型、树型、网状型
1)总线型:用一根线把各计算机连接起来。优点:建网容易,增减节点方便,节省线路。缺点:重负载时通信效率不高。
2)星型:每个计算机或终端都以单独(专用)的线路与中央设备相连,中央设备一般是交换机。优点:结构简单,建网容易,延迟小,便于管理。缺点:成本高,中心节点对故障敏感。
3)环型:所有计算机和接口设备连接成一个环,可以是单环也可以是双环,环中信号是单向传输的。双环网络中两个环上信号的传输方向相反。适合实时控制的局域网系统
4)树型:节点组织成树状结构,具有层次性
5)网状型:每个节点至少有两条路径与其他节点相连。优点:可靠性高、可选择绝佳路径,传输延迟小。缺点:控制复杂,线路成本高。一般用于Internet骨干网或广域网的骨干网上
3、按交换机技术分类:线路交换网络、报文交换网络、分组交换网络。
1)线路交换:在源节点和目的节点之间建立一条专用的通路用于数据传送。典型的就是早期的电话网络。优点:数据直接传送延迟小。缺点:线路利用率低,不能充分利用线路容量,不便于进行差错控制。
2)报文交换:将用户数据加上源地址、目的地址、长度、校验码等辅助信息封装成报文,发送给下一个节点。下一节点收到后先暂存报文,带输出线路空闲时再转发给下个节点。因而这样的网络也叫存储—转发网络。其中的交换节点要有足够大的存储空间,用以缓冲收到的长报文。优点:充分利用线路容量;可以实现不同链路之间不同数据率的转换;提高了传输的可靠性。缺点:增加资源开销;增加缓冲延迟;缓冲区难以管理。
3)分组交换网络:也称包交换网络,将数据分成较短的固定长度的数据块,在每个数据块中加上目的地址、源地址和分组序号等辅助信息组成分组(包),按存储转发方式传输。具备报文交换网络的优点外,自身优点:缓冲区易于管理;包的平均延迟更小,占用的平均缓冲区更少;更易标准化。
4、按使用传输介质分类:有线、无线
1)有线又分为:双绞线网络、同轴电缆网络、光纤网络、光纤同轴混合网络等
2)无线又分为:无线电、微波、红外线等
5、常见的网络拓扑结构分为广域网拓扑结构和局域网拓扑结构。
6、广域网拓扑结构有集中式、分散式、分布式、不规则式结构
7、局域网拓扑结构有星状结构、环状结构、总线结构、树状结构和网状结构等
8、通常网络拓扑是由混合形式的、而非单一的拓扑结构
(三)网络体系结构模型
1、网络体系结构是一个指构成计算机网络的各组成部分及计算机网络本身所必须实现的功能的精确定义。(是计算机网络中层次、各层的协议以及层间的接口的集合)
2. The basic principles of layering:
1) The interface between each layer is clear, easy to understand, and the mutual communication is as little as possible
2) The definition of the function of each layer is independent of the specific implementation method
3) Maintain the independence of the lower layer from the upper layer, a single
3. OSI model: proposed by the International Organization for Standardization (ISO) in 1978, known as the Openamp System Interconnection Reference Model (OSI). Also divided into 4 layers
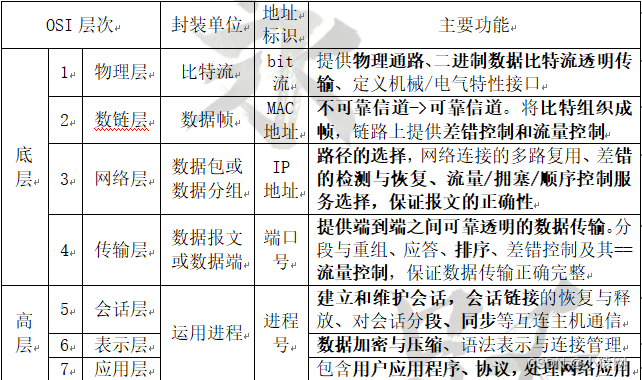
4, layered network system, each layer is throughservice access pointto provide services. And layer N can only provide service
5, interface, protocol and service
1) to layer N+1interfaceRefers to two within the same systemInteraction Rules Between Adjacent Hierarchies。
2)protocolrefers to communicationBoth sides achieve the same functionbetween the corresponding layersRules of Association, Protocol: Syntax, semantics, and timing are composed of three parts.
3)Serverefers to the function call provided for the immediately upper layer,Each layer can only call the services provided by the immediately adjacent lower layer. service throughService Access Point (SAP) provides. (For example, layer N can only provide services to layer N+1)
2. Basic knowledge of data communication
(1) Data connectivity
1. The concept of data communication:data communication iscomputerwith plancomputeror countcomputer and otherterminalbetweenA communication technology for storing, processing, transmitting and exchanging information.
2. Communication should not only transmit useful information without distortion and high efficiency, but also reduce or eliminate useless and harmful information in the process of transmission.
3.channelIt is the path of data transmission. In the computer network, the channel is divided intophysical channelandlogical channel.
4. According to the direction and time of information transmission, channel transmission can be divided into:Simplex, half duplex, full duplextransfer method. Simplex: only one direction, only one channel is needed; half-duplex: both parties in the communication can send information, but not at the same time; full-duplex communication: both parties can send and receive messages at the same time, such as telephone 5, channel bandwidth and channel
capacity : Channel bandwidth refers to the frequency range occupied by the signal transmitted in the channel without distortion, that is, the channel frequency band, expressed in Hz, and the channel bandwidth is determined by the physical characteristics of the channel. Channel capacity refers to the maximum number of bits that can be transmitted on the channel per unit time, expressed in bits per second.
6. Latency: refers to the time required for a message or packet to be transmitted from one end of the network to the other. Usually, the delay is composed of three parts: transmission delay, propagation delay and processing delay
(2) Data Communication Computing
1. Analog channel bandwidth calculation:W=f2-f1, where f1 is low frequency and f2 is high frequency. thingMade of reasonable media, the bandwidth is fixed2.
Digital channel bandwidth calculation: Nyquist law (noise-free):
W: bandwidth B: symbol rate, baud rate n: semaphore (bit) N: symbol type R: data rate (bit/ s)
- Code rate: B=2W
- Symbol type: n=log2N
- Data rate:R=Blog2N=2Wlog2N
- Logarithmic calculation: N=4, log24=log2(22)=2
3. Digital channel bandwidth calculation: Shannon's law (noise)
C: Data rate W: Channel bandwidth S: Signal average power N: Noise average power S/ B: Signal-to-noise ratio (generally expressed in dB) - Shannon's law:C=Wlog2(1+S/N)
- SNR formula:dB=10lg(S/N)
4、Data rate ® = X characters transmitted per second × (a+b+c+d); where, X characters transmitted per second = effective rate/b data bits; where B=1/T; 1s=106us; eg: period is 125us, that is, B=1000000/125=8000Hz
5. In digital communication using Manchester encoding, the baud rate is twice the data rate, Manchester encodingThere is no need to additionally transmit a synchronization signal, and there is a level flip in the middle of each bit.
6. Common unit conversion and data - 1B=8b
- 1s=103ms=106us
- Communication conversion rate 1000 1G=1000M Storage conversion rate 1024 1G=1024M
- Cable delay: 200m/us (70% of the speed of light 300m/us) (200km/ms, 200000km/s)
- Satellite delay: 270ms (round trip)
(4) Data modulation and coding
1. Analog channel modulation: divided intoAM ASK (high and low), FM FSK (density), phase modulation PSK (butt), quadrature amplitude modulation QAM
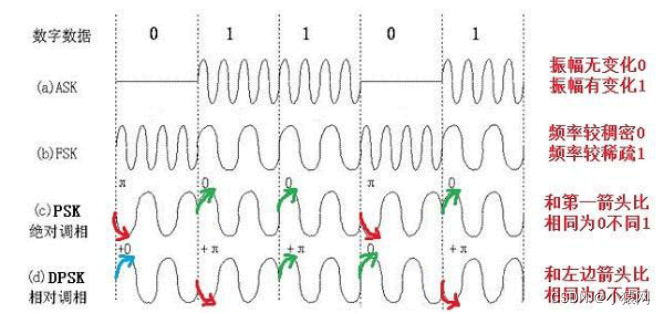
2. Amplitude shift keying (ASK): The amplitude change of the carrier is used to carry digital data, while the frequency and phase of the carrier remain unchanged.
3. Frequency shift keying (FSK): Use the frequency change of the modulated wave to carry digital data, while the amplitude and phase of the carrier wave remain unchanged.
4. Phase shift keying (PSK): The phase change of the modulated wave is used to carry digital data, while the frequency and amplitude of the carrier remain unchanged.
5. Common modulation technology symbol types/bits: ASK: 2/1; FSK: 2/1; PSK: 2/1; QPSK (4PSK): 4/2; 8PSK: 8/3; DPSK: 2/ 1; 4QAM: 4/2;
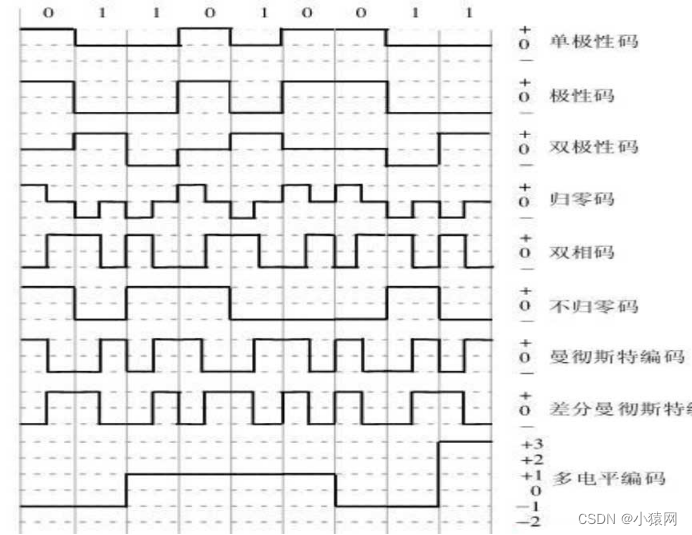
6. Digital channel coding: divided intoThree steps of sampling (2x), quantization (level), and encoding (binary)
7. Unipolar code: positive voltage means 1, another state means 0; polarity code: positive voltage and negative voltage means; return to zero code RZ, there are positive level, negative level, zero level, positive level Represents 1, negative level means 0; Manchester encoding: the jump from negative level to positive level means 1, vice versa means 0, and vice versa; differential Manchester encoding: no level jump at the beginning of the bit means 1, and there is a level jump Turning means 0; bipolar coding: zero level means 0, positive and negative levels mean 1, continuous 1 must jump
8, single-click code, polar code, bipolar code, return-to-zero code, bi-phase code, non-return-to-zero code, Manchester encoding (no additional transmission synchronization signal is required, used for not too fast Ethernet), differential Manchester encoding (generally used in token ring network)
9,E1The data rate of the channel is (2.048Mb/s),The control overhead of E1 accounts for 2/32, and the data overhead is 30/32, the transmission time of E1 basic frame is125us,inThe data rate of each voice channel is (64Kb/s), effective 54Kb/s; T1The data rate of the carrier is1.544Mb/s
10、各种编码效率:
- Manchester编码是一种双相码,==运用在不太快以太网中,提供了比特同步信息
- 4B/5B效率80%==用于百兆以太网,用于100Base-FX(采用的编码技术为4B/5B+NRZI)、100Base-TX、FDDI;==首先把4位分为一组的代码变为5单位的代码,再把数据变为NRZI编码
- ==8B/10B效率80% 用于千兆以太网
- 8B/6T:编码效率为80%,用于100Base-T4
- 曼码和差分曼码效率50%,曼码用于不太快的以太网,差分用于令牌环网
- BAMI:2/3
- NRZI:100%
(五)多路复用技术
1、频分复用FDM:不同的频率,子信道隔离频带防串扰,如CATV,WIFI。用于模拟传输
2、时分复用TDM:不同的时间,轮流占用,如手枪、手机。分为同步时分T1、E1;统计时分(STDM)——如ATM。用于数字传输
3、波分复用WDM:不同的波长,如光纤通信。
4、多路复用技术是把多个低速信道组合成一个高速信道的极速,可以有效提高数据链路的利用率,从而使的一条高速的主干链路同时为多条低速的接入链路提供服务。
5、TDM更浪费介质带宽,FDM可更有效利用介质带宽
6、多路复用最常用的两个设备:
- 多路复用器,在发送端根据约定规则把多个低带宽信号复合成一个高带宽信号;
- 多路分配器,根据约定规则再把高带宽信号分解成为多个低带宽信号。这两种设备统称多路器(MUX)
(六)数据交换方式

1、电路交换:是一种直接的交换方式,它为一对需要进行通信的装置(站)之间提供一条临时的专用通道。通信包括三个阶段:a.电路建立 b.数据传输 c.电路拆除。优点:独占性、实时性,传输延迟小,适合传输大量的数据;缺点:需建立一条物理连接,由于线路独享造成资源浪费,利用率低(Early telephone system)
2. Message exchange:Advantages: No need for dedicated access, high line utilization, store and forward nodes can check and correct errors; Disadvantages: There is communication delay, not suitable for interactive communication. For example, logistics package
3, packet switching:Advantages: higher utilization, optional paths, data rate conversion, support priority; disadvantages: delay, high overhead. The length of the datagram packet is fixed, and an end-to-end logical connection can be established, such as sending a letter by the post office. againdatagram and virtual circuit
- Packet datagram: one-way transmission, connectionless. as ordinary letter
- Packet Virtual Circuits: Interactive, Logical Links. Such as registered letter
4. Cell exchange: It is the exchange method adopted by Asynchronous Transfer Mode (ATM), which is largely based onvirtual circuitway to proceedpacket forwarding. What is different in ATM networks is that,Packet length is fixed, called a cell.The cell length is 53 bytes, the header is 5 bytes, and the payload is 48 bytes。
(7) Transmission medium
1. Twisted pair: Arrange two mutually insulated copper wires side by side, and then twist them together in a regular way to form a twisted pair.Twisting can reduce electromagnetic interference to adjacent wires, divided into unshielded (UTP), shielded (STP)
2. The twisted pair is divided intocrosstwisted pair andthroughtwisted pair;the same speciesdevice connectionwith a crossTwisted pair (PC and router, server and server, etc.);differentdevicedirect communicationCable (PC and switch, server and switch)
3. Coaxial cable: divided intoCoarse (baseband) withshaft cable,thin (broadband) withshaft cable. The transmission distance is long and the signal is stable. It is often used in TV monitoring systems and audio equipment to transmit sound. Transmission of digital signals (using baseband/coarse), transmission of analog signals (using bandwidth/thin)
4. Optical fiber (optical cable): divided into single-mode optical fiber SMF (using ILD laser diodes), multi-mode optical fiber MMF (using LED light-emitting diodes), Advantages of optical fiber: wide transmission frequency and large communication capacity; low loss, good electromagnetic insulation performance; light weight; reliable working performance; disadvantages: special equipment is required to accurately connect two optical fibers; comparison:Single mode: Noble and fine
5. Wireless channel: pointsradio waves and infrared light waves

6、Pulse code modulation (PCM) is mainly used to solve the problem of transmitting analog signals on digital lines.
7. Optical cable: mainly composed of optical fiber (short for optical fiber), plastic protective sleeve and its plastic sheath, optical fiber is a part of optical cable
- The fiber optic cable is easy to break if the bending radius is too small
- If the bending radius of the optical cable is too small, it is easy to occurThe leakage of optical signal affects the transmission quality of optical signal
- During the construction process, the bending angle of the optical cable should not be less than 90 degrees.
(8) Error detection and error correction
1. Error detection code:The parity check looks at whether the number of 1s is odd/even. Can only detect errors but not correct them. Mobile communication is widely adopted.
2. The Hamming code is an error code that can correct errors; the cyclic redundancy check code can only detect errors, but cannot correct them; the parity check code cannot be detected when the parity of the number of 1s does not change. something went wrong.
3. The Hamming distance between a pair of valid codewords is (Number of bits that differ between two codewords)
4、Hamming Code: Add redundant parity bit k after data bit m to form information m+k, then satisfym+k<2k-1 can correct one bit error(Can be corrected one by one).Not only error detection but also error correction。
- Code distance d: also called Hamming distance, the minimum number of bits (number of bits) that differ between two codewords
- How many bit errors can be detected: ≤d-1
- How many bit errors can be corrected: <d/2
5,CRC code: Redundant Cyclic Check Code, is acyclic code, realize error detection through cyclic displacement, easy to realize by hardware, and widely used in local area network.Can only detect errors but not correct them
3. Network Layering and Functions
(1) Physical layer
1. The physical layer protocol needs to solve the interface problem between data terminal equipment such as hosts and workstations and communication equipment on communication lines.
2. InDTE(data terminal equipment)and DCE(data communication equipment)between the establishment of、maintainandRemove the physical linkThe relevant technical details of the connection are described by the International Telegraph and Telephone Consultative Committee (CCITT) and ISO with 4 technical characteristics: mechanical characteristics, electrical characteristics, functional characteristics, and procedural characteristics 1) Mechanical characteristics: specify the connection between DTE and
DCEConnector form(shape, size, number of leads)
2) Electrical characteristics: specifies the electrical characteristics of the transmitter and receiverGas parameters and their related circuit characteristics。Electrical characteristics determine transmission rate and transmission distance(For example, positive voltage represents 0 and negative voltage represents 1)
3) Functional characteristics: interface signals are roughly divided intoData Signals, Control Signals and Clock Signals. (Such as the function of each signal line)
4) Specification characteristics: stipulatesThe operation process of each interface signal line between DTE and DCE to realize data transmission(Operation sequence)
3. Requirements for interconnection of various networks at the physical layerThe data transfer rate is the same as the link layer protocol
4. For switches,The test tool generates 100% full line-speed traffic at the sending port; for HUB, the test tool generates 50% line-speed traffic at the sending end。
(2) Data link layer
1. The data link layer must haveFraming, error control, flow control, link management, MAC addressing and other functions.
2. Error control: In digital or data communication systems, anti-interference coding is usually used for error control, which is generally divided into 4 categories 1)
Forward error correction (FEC): In the information code sequence, redundant bits are added, called "Supervision element".suitable for high speed data, and needreal-time transmissionCase
2) Feedback Detection (ARQ): In non-real-time data transmission, the ARQ rubbing control method is commonly used. (An ACK message is returned when the message is received without error, and an ANK message is returned if there is an error) Advantages:Less redundant bits, strong error detection ability, and simple encoding/decoding. (only errors are found but not corrected)
3) Hybrid error correction (HEC): the combination of FEC and ARQ, inWithin the error correction capability, automatic error correction;When the error correction capability is exceeded, use the ARQ method to correct errors (retransmission).
4) Information feedback (IRQ): It is the simplest error control method. (The receiver sends the received information to the sender as it is and compares it with the original sending code. If there is an error, the sender resends it),It is only suitable for low-speed non-real-time data communication and is a relatively primitive approach.
3. The data link layer realizes the correct transmission of binary information groups between systems, and provides reliable and error-free data information protocols for the upper layer.
4. Among the optical fiber transmission test indicators,回拨消耗是指信号反射引起的衰减。
(三)网络层
1、是通信子网(物理/数链/网络)的最高层。其主要任务是:通过路由选择算法,为报文或分组通过通信子网选择最适当的路径。
2、该层控制数据链路层与传输层之间的信息转发,建立、维持和终止网络的连接。
3、主要功能:建立、维护和拆除网络连接;路由选择;流量控制;网络传输控制等
4、数据分组进行分片后,每个分片首部中的“总长度”字段是指每一个分片的数据长度和首部长度之和。
(四)传输层
1、下3层负责数据通信,上3层负责数据处理。传输层是通信子网和资源子网的接口和桥梁。
2、服务质量:根据通信子网提供的服务质量不同,分为A/B/C类网络服务
1)A类:是一个完整的、理想的、可靠的服务,所需传输层协议简单
2)B类:可靠的,有较好的数据服务(误码率低)和较差的连接服务(故障多)
3)C类:网络传输不可靠,可能会丢失分组或重复分组,网络故障率也高
3、常见的协议:TCP/IP中的TCP(面向连接的)和UDP(面向非连接的)协议;Novell网络中的SPX协议;微软的NetBIOS/NetBEUI协议
(五)应用层
1、会话层,是用户应用程序和网络之间的接口,主要任务是:向两个实体的表示层提供建立和使用连接的方法,组织和协调两个会话进程之间的通信,并对数据交换进行管理。用户可以按照半双工、单工和全双工的方式建立会话
2、会话层的功能:会话的管理、会话的流量控制、会话的寻址、差错控制
3、表示层:其主要功能是“处理用户信息的表示问题,如编码、数据格式转换、压缩/解压缩和加密解密”等。
4、应用层:是计算机用户、各种应用程序和网络之间的接口。其功能是直接向用户提供服务,完成用户希望在网络上完成的各种工作、实现各种服务。
5、协议如:HTTP、FTP、Telnet、SNMP、SMTP、NNTP、DNS
6、小结:从网络功能的角度观察:下3层主要提供数据传输和交换功能,即以节点到节点之间的通信为主;第4层作为上下两部分的桥梁;而上3层则以提供用户与应用程序之间的信息和数据处理功能为主。简言之,下4层主要完成通信子网的功能,上3层主要完成资源子网的功能。
7、安全电子邮件使用PGP协议
8、PGP是一种电子邮件加密软件包它提供数据加密和数字签名两种服务,采用(RSA公钥证书)进行身份认证,使用(IDEA)(128位密钥)进行数据加密,使用(MD5)进行数据完整性验证
(六)对等网(P2P)
1、对等网络(P2P):各个节点是对等的,具有相同的责任和义务,彼此互为客户端/服务器,协同完整工作。
2、P2P网络从集中化程度角度分类:集中式/分布式/半分布型P2P网络
3、P2P资源定位方式:集中方式索引、广播方式、动态哈希表的方式
四、网络设备
(一)网卡/网桥/中继/集线器
1、常用网络互联设备:
2、1层物理层:中继器、集线器
3、2层链路层:网桥、交换机
4、3层网络层:路由器、三层交换机
5、4层以上高层:网关
6、网卡:又称网络适配器。用于计算机和网络电缆之间的物理连接。
7、网卡完成物理层和数据链路层的大部分功能,包括网卡与网络电缆的物理连接、介质访问控制(如CSMA/CD)、数据帧的拆装、帧的发送与接收、错误校验、数据信号的编/解码(如曼彻斯特代码的转换)、数据的串、并行转换等功能。
8、中继器:工作在物理层设备。主要功能是通过对数据信号的复制、整形、放大再发送,来扩大网络传输的距离
9、集线器(Hub):具有中继器的功能,区别在于集线器能够提供多端口服务,也称==(多口中继器)。集线器是物理层设备。集线器不具备交换机所具有的MAC地址表==,所以它发送数据时是没有针对性的,而是采用广播方式发送。
10、网桥:数链层设备,网桥的功能有源地址跟踪、帧的转发和过滤协议转换、分帧和重组、网络管理等功能。通过这些功能提高网络的性能、可靠性和安全性
11、网桥的类型:生成树网桥、源理由选择网桥
(二)交换机
1、交换机:也称多端口网桥,工作在数据链路层,能够识别帧的内容。交换机在同一时刻可进行多个端口对之间的数据传输。每一个端口可以视为以为广播域,每一端口都可视为独立的网段,连接在其上的网络设备独自享有全部的带宽,无须同其他设备竞争使用。
2、交换机简介和分类:交换机(Switch)意为“开关”是一种用于电(光)信号转发的网络设备。它可以为接入交换机的任意两个网络节点提供独享的电信号通路。工作于第2层或3层。最常见的交换机是以太网交换机。下图是华为的Huawei S2700系列以太网交换机
3、按照VTP协议,交换机的运行模式有(服务器模式,客户机模式,透明模式)
4、网桥和交换机:都是软硬件结合,都有广播和冲突域,区别就是交换机比网桥的端口多,转发速度更快;(所以说交换机是多端口的网桥)
5. Aggregator (physical layer) and bridge (link layer): both can detect conflict domains;
6. The ability of switches to forward data packets is calledpacket forwarding rate, also known as port throughput, refers toThe ability of the switch to forward packets, the unit is pps, the switchBackplane bandwidth refers to the maximum amount of data that can be transmitted per unit time between the switch port processor and the data bus
7. Three functions of the switch:
1) Learning: The switch identifies the MAC address of the device connected to each port, and stores the mapping relationship between the MAC address of the device and the corresponding port in the MAC address table in its cache.
2) Forwarding/filtering: When the destination address of a data frame has a mapping relationship in the MAC address table, it is forwarded to the corresponding port instead of all ports (if the data frame is broadcast, the multicast frame is forwarded to all port).
3) Elimination of loops: When the switch includes a redundant loop, the switch avoids the generation of loops through the spanning tree protocol, while allowing the existence of backup paths.
8. Classification of switches:

9. If the switch needs to be interconnected with the access layer switch in workshop 1, itsConnection methods include stacking and cascading;into stackway canShared use of switch backplane bandwidth,cascadeway you can useTwisted pair wires connect the switches together.
10. Carry out port aggregation on the ports of the aggregation layer switches, and the portsThe default mode is access,conductport aggregationshould be configured astrunkMode
11. The switch adds the corresponding MAC address entry by reading the source address in the input frame.
12. The MAC address entry of the switch changes dynamically; the initial MAC address table of the switch is empty.
13. In the default configuration, the switchAll ports (belonging to the same VLAN), different VLANsThe data frame must pass (router)transmission.
14. The way for the switch to obtain the MAC address of the device connected to its port is to check the portsource address of the incoming packet, and record it in the address table.
15. If the scale of the storage area network expands, the originalInsufficient FC switch ports, you can passcascademode, multiple fiber optic switchesForm a large-scale Fabric, which is like a large, virtualFC switch.
16. The networking range of Layer 2 Ethernet switches is mainly limited by the bridge protocol.
(3) Router
1. Introduction and classification of routers:Routers are used to connect different LANs, and routers can learn and propagate various routing information.The router works at the layer 3 network layer,It has both LAN and WAN interfaces
2. Functions of the router: protocol conversion, routing selection, routing selection that can support multiple protocols, flow control, segmentation and grouping functions, network management functions 3. In the results of viewing routing information, the mark S
means static routing, and the mark C Direct connection, the mark R indicates the use of RIP routing protocol
4,Router factoryhour,defaultThe serial port encapsulation protocol isHDLC
5. The router is based onThe destination IP address in the IP datagram corresponds to the routing table in the router for routing
6. According to function, performance and application, routers are divided into:
- ①backboneRouter: backbone network interconnection, modularization, hot backup, dual power supply and other redundant technologies. likeNational, provincialbackbone network interconnection. Such as NE40E and above series
- ②enterpriseLevel router: used for the entrance and exit of an enterprise, providing multiple functions and completingEnterprise networking。Can realize data, voice, videoand other applications. Such as AR3600 series
- ③accesslevel routers: edge routers,small companies, or departmental networking.
For example , some common ports on AR2200 series 7 and routers: - ①SerialPort (synchronous serial port): high-speed synchronous serial port, withWanconnectableDDN, Frame Relay, X.25, PSTNand other networks (routingSFP portVia fiber optic connectionWan); The equipment CSU/DSU that links the terminal and the digital private line is integrated in the synchronous serial port of the router
- ②ConsolePort: Initially configure the console port, using a terminal emulation program such asHyperTerminal, SecureCRT on the routerlocalconfiguration
- ③RJ-45Port: Ethernet port, viaTwisted pair connection LAN, some marked as ETH, some marked as 10/100bTX (the router is connected to the Ethernet switch through RJ-45)
- ④TOPort (asynchronous serial port): remote configuration router, connectionModem
- ConsolePort: The Console port is connected to the serial port of the computer through a special cable, and the router is configured locally by using a terminal emulation program. router'sConsole port is RJ-45 port
- SFP port:passFiber optic connection to Guangcheng network, small rack pluggable device SFP is an upgraded version of GBIC, its function is basically the same as GBIC, buthalve the volume
- The interface connecting the router to the frame relay network is a Serial interface, and the interface connecting the twisted-pair Ethernet is an RJ-45 interface.
8. Broadcast domain and collision domain - Collision domain: Every node in the same collision domain can receive all sent frames. paySwitching separates collision domains. One collision domain per port
- Broadcast domain: A collection of all devices in the network that can receive broadcast frames sent by any device.Routers can separate broadcast domains. One broadcast domain per port

9. When there are multiple routes to choose, by comparing theShortcuts for managing distance10.
The communication between VLANs requires the support of the router.
11. When the router leaves the factory, the defaultserial portThe encapsulation protocol isHDLC
12. Composition of router
1) ROM used to store boot software
2) Flash used to store IOS system software
3) RAM used as main memory
4) NVRAM used to store startup configuration
(4) Gateway/Modem/Wireless Device
1. The gateway (application layer) is also calledprotocol converter, is a complex network connection device that can support the conversion between different protocols and realize the interconnection between different protocol networks.
2. Classification of gateways:
1) Protocol gateway: usually performs protocol conversion between network areas that use different protocols
2) Application gateway: a system that translates data between different data formats
3) Security gateway: a fusion of various technologies , has an important and unique protection function, ranging from protocol-level filtering to very complex application-level filtering.
3. The modem isTranslates a computer's digital signal into an analog signal that can be sent along ordinary telephone lines,在线路另一端的另一个调制解调器接收后,再把模拟信号翻译成数字信号的设备。
4、AP即无线接入点,单纯性无线AP就是一个无线的交换机,仅仅是提供一个无线信号发射的功能。理论上最大可达 300M,实际使用范围:室内 30M、室外 100M(无障碍物)AC 即无线控制器
(五)防火墙
1、防火墙的定义:来源于建筑物“防火墙”一词,位于两个或多个网络之间,执行访问控制策略,过滤进出数据包的一种软件或硬件设备,通过流经的数据流进行分析和检查,可实现对数据包的过滤、保存用户访问网络的记录和服务器代理功能
2、防火墙的要求:①所有进出网络的通信流量都必须经过防火墙。②只有内部访问策略授权的通信才能允许通过。③防火墙本身具有很强的高可靠性
3、防火墙的主要功能:①访问控制功能。②内容控制功能。③全面的日志功能。④集中管理功能。⑤自身的安全功能
4、防火墙的附加功能:①流量控制。②网络地址转换NAT。③虚拟专用网VPN
5、防火墙的局限性:①关闭限制了一些服务带来不便。②对内部的攻击无能为力。③带来传输延迟单点失效等。④还有其他局限
6、防火墙的技术分类:包过滤防火墙;代理防火墙;状态化包过滤防火墙3类等
7、防火墙的分类:个人/企业/软件/硬件防火墙
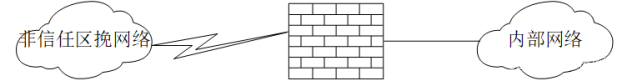
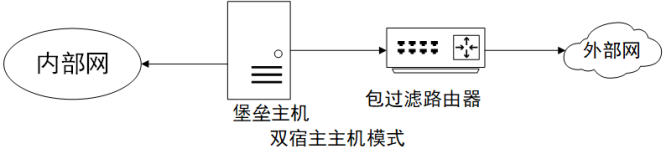
8、防火墙的体系结构:①双宿主机模式:防火墙具有两个网卡接口,通过包过滤代理访问网络。这是比较简单的一种结构。一般可以根据IP地址和端口号进行过滤
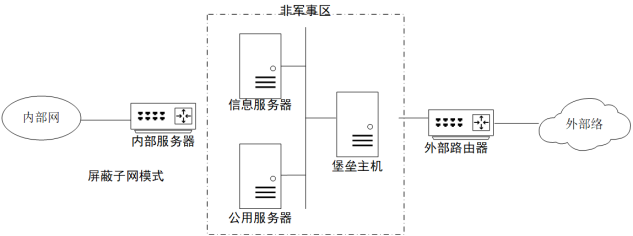
9、防火墙的体系结构:②屏蔽子网模式:又叫过滤子网模式,两个包过滤路由器中间建立一个隔离的子网,定义为DMZ网络,也称为非军事化区域。这是目前防火墙最常用的一种模式。可以有更高级的功能
10、防火墙设备中,配置双出口链路有提高总带宽、链路冗余、链路负载均衡作用。通过配置链路聚合来提高总带宽,通过配置策略路由来实现链路负载均衡(防火墙设备集成了传统防火墙与路由功能才行)
11、防火墙的工作模式:路由模式、透明模式、混合模式3种:
- 路由模式:如果防火墙以第三层对外连接(接口具有IP地址),则认为防火墙工作在路由模式下
- 透明模式:若防火墙通过第二层对外连接(接口无IP地址),则防火墙工作在透明模式下
- 混合模式:若防火墙同时具有工作在路由模式和透明模式的接口(某些接口具有IP地址,某些接口无IP地址),则为混合模式下
12、防火墙的访问规则:3种接口 - ①内网接口(Inbound)连接内网和内网服务器
- ②外网接口(Outbound)连接外部公共网络
- ③中间接口(DMZ)连接对外开放服务器
- 1、Inbound可以访问任何Outbound和dmz区域
- 2、dmz可以访问Outbound区域
- 3、Outbound访问dmz需配合static(静态地址转换)
- 4、Inbound访问dmz需要配合acl(访问控制列表)
13、防火墙工作层次越高,工作效率越低,安全性越高(高低高/地高低) - ①工作层次。这是决定防火墙效率及安全的主要因素。一般来说,工作层次越低,则工作效率越高,但安全性就低了;反之,工作层次越高,工作效率越低,则安全性越高。
- ②防火墙采用的机制。如果采用代理机制,则防火墙具有内部信息隐藏的特点,相对而言,安全性高,效率低;如果采用过滤机制,则效率高,安全性却降低了
五、局域网
(一)局域网基础知识
1. Ethernet: Ethernet is the earliest local area network used, and it is also the most widely used network product at present.
2. Ethernet transmission media include: coaxial cable, twisted pair and optical fiber. The naming format is such as "10Base-T", 10: indicates the rate (unit Mbps), Base: indicates the transmission mechanism, Base indicates the baseband, and Broad indicates broadband; T: the transmission medium, T indicates twisted pair, F indicates optical fiber, and the number indicates copper
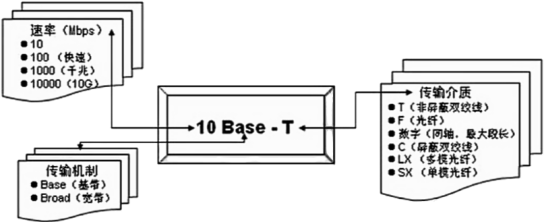
3. Ethernet time slot: Time is divided into discrete intervals called time slots . Frames are always sent immediately at the beginning of the slot. can be sent in one time slot0,1 or more frames,respectivelyCorresponding to the case of free slot, successful transmission and transmission collision。
(2) Medium access control method
1. Random access medium access control: CSMA protocol (Carrier Sense Multiple Access Protocol), there are many types:
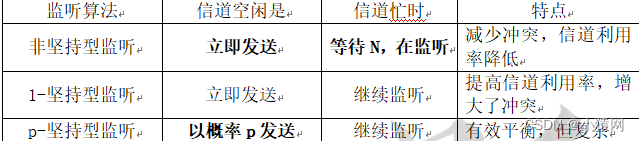
2. Conflict handling method of CSMA (Carrier Sense Multiple Access): continue to complete the transmission of the frame that has already started sending process until the response times out before processing.
3. (Improved) CSMA/CD (Carrier Sense Multiple Access with Collision Detection) conflict handling method:find conflictsending siteto the whole networksend aStop sending after reinforcing colliding noise frames, wait for a random long time and then re-enter the listening process.
4. The CSMA/CD access control method (carrier sense multiple access/conflict detection control) required the network to form a bus structure in the early days, and later the star LAN network using hubs and switches also used this method. 5. Token passing access control
method The conditions that require the network to meet are: the network forms a ring. When a physical ring cannot be formed, a logical ring must be formed, and signals are transmitted unidirectionally on the ring.
(3) Ethernet protocol (CSMA/CD)
1. LAN has only physical layer and data link layer. Divide the data link layer into topology-independentLogical link control sublayer (LLC layer) and medium access control sublayer (MAC layer) related to topology and access control mode。LLCresponsible forapplication interface,MACresponsible forMedia interface.
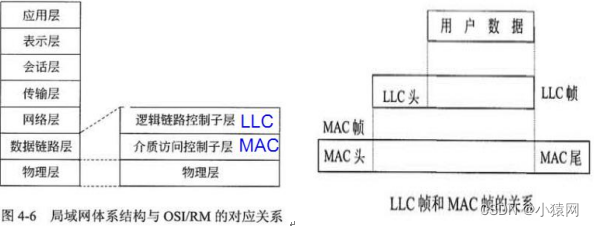
2. Physical layer: For LAN,physical layer is required, which is responsible for reflectingMechanical, electrical and procedural characteristics,byEstablish, maintain and tear down physical links,it提供在物理层实体间发送和接收位数据流的能力。
3、MAC子层:MAC子层对LLC子层提供媒体介质访问控制的功能服务,而且可以提供多个可供选择的介质访问控制方法,如: CSMA/CD、令牌总线、令牌环等多种。
4、LLC子层:LLC子层中规定了无确认无连接、有确认无连接和面向连接三E种类型的链路服务。
5、IEEE 802.3协议:规定了合法的MAC帧的最短帧长度为64字节,包含的数据字段最短为38字节。帧校验序列FCS字段是32位(4字节)的循环冗余码
6、IEEE 802.4协议:规定了令牌总线访问控制
7、IEEE 802.5协议:描述了令牌环网标准,令牌环用于环型拓扑的局域网
8、令牌环的特点:
- 由于只有收到令牌帧的站点才能将信息帧送到环上,所以令牌环不可能产生冲突,因此也没有最短帧长度的要求。
- 由于每个站点接收到令牌的过程是依次进行的因此对所有站点都有公平的访问权。
- 由于每个站点发送的最大长度可以加以限制所以每个站点传输之前必须等待的时间是可以确定的。
9、在以太网半双工共享式连接中,我们无需流量控制;而在全双工交换式连接中要考虑流量控制,其原因是,共享式连接中,CD(碰撞检测)起到了拥塞避免的控制机制。全双工中必须附加其他机制来完成
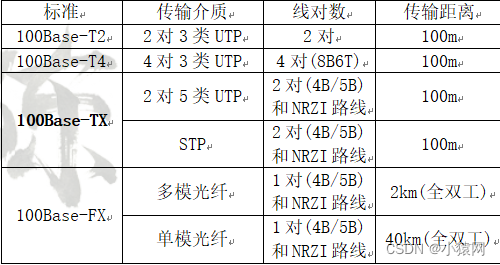
(四)快速/千兆/万兆以太网
1、快速以太网:802.3u标准,速率可到 100M,100Base-T/F规范。FLP快速链路脉冲;T表示非屏蔽双绞线,C表示屏蔽双绞线,F表示光纤,非屏蔽(UTP)屏蔽(STP)
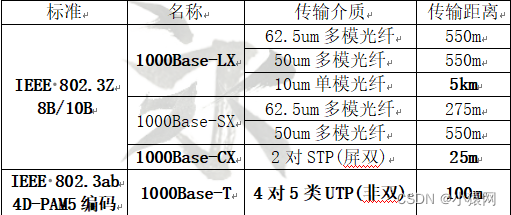
2、千兆以太网:802.3z标准,速率可到 1Gbps,兼容10M/100M以太网。帧突发。千兆以太网物理层包括编码/译码,收发器和网络介质三部分,其中不同的收发器对应不同的传输机制类型
3、万兆以太网:802.3ae标准,速率可达万兆(10Gbps),只支持光纤,只支持全双工,不再采用CSMA/CD,可用于城域网
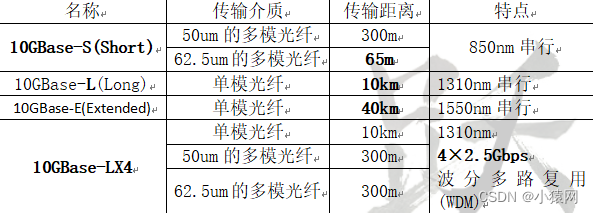
4、光以太网:利用光纤的带宽优势,结合以太网成熟的技术,为新一代的宽带城域网提供技术支持。光以太网具备的特征有:(1)能够根据用户的需求分配带宽;(2)具有认证和授权功能;(3)提供计费功能;(4)支持VPN和防火墙,保证网络安全;(5)支持MPLS,提供Qos服务;(6)方便快速灵活的适应用户和业务的拓展
(五)无线局域网(CSMA/CA)
1、无线局域网(WLAN)是以无线通信为传输方式的局域网,是实现移动计算机网络的关键技术之一。
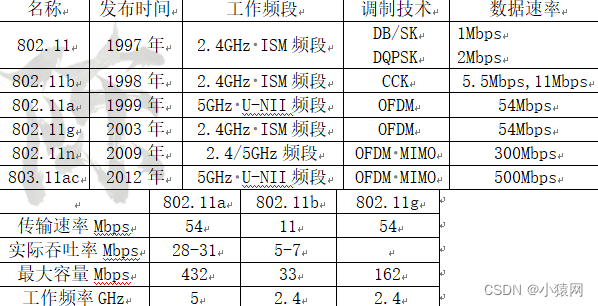
2、IEEE 802.11X的比较
3、蓝牙:蓝牙是一种支持设备短距离通信(10m内)的无线电技术。蓝牙的标准是IEEE 802.15,工作在2.4GHz频带,带宽为1Mbps.
4、无线局域网常用拓扑结构:(1)不使用AP的独立无线局域网(2)使用AP的独立无线局域网(3)组合方式的无线局域网
5、802.11的扩频技术就是:用伪随机序列对代表数据的模拟信号进行调频
6. 1G communication is mainly based on voice, and the modulation method is FDMA; 2G communication has developed short message transmission, and the modulation method is CDMA and TDMA; 3G communication also mainly uses CDMA and TDMA; 4G needs to transmit video information, mainly using OFDMA; 5G Then proposed SCMA sparse code division multiple access.
7. The key technologies adopted by my country's standard TD-SCDMA mainly include synchronous CDMA technology, smart antenna technology, joint detection technology, software radio technology, access switching technology, dynamic channel allocation technology, etc. Massive MIMO is a 5G technology.
8. Features of FM spread spectrum technology: (1) Good anti-interference performance; (2) Strong concealment and low interference; (3) Easy to implement code division multiple access; 9. Spread spectrum
technology: (1) Reduced frequency of spread spectrum communication (2) Each signal bit can be transmitted with N chip bits; (3) The spread of the signal to a wider frequency band reduces the probability of channel blocking; 10. The main function of spread spectrum
communication The idea is to spread the signal to a wider bandwidth to reduce the chance of blocking and interference
11. Wireless local area network WLAN: two structures: ① infrastructure network, ② special network Ad Hoc

12, wireless local area network WLAN: twoAP (the role of the digital link layer is wireless access)(Indoor 30m, Outdoor 150m)
- Fat AP (FAT) generally refers to wireless routing: Fat APs are mostly used in homes and small networks, and have relatively complete functions. Generally, one device canRealize access, authentication, routing, VPN, address translation, and even firewall functions
- Thin AP (FIT) generally refers to wireless gateway or bridge:Thin APs are mostly used in occasions with higher requirements
13 ,WLAN: Three techniques:① infrared, ② spread spectrum, ③ narrowband microwave - infraredLine (IR) is divided into:directional beaminfrared,omnidirectional broadcastinfrared,diffuse reflectioninfrared.
- spread spectrumDivided into:Frequency hopping FHSS, direct sequence DSSS.
- narrowbandMicrowave (RF)Divided into: ShenPlease license RF, license free RF
- CSMA/CA: Carrier Sense Multiple Accessconflict avoidance, == Solve the hidden terminal problem
- First detect == when transmitting data, if it detects that there is no data in the network, wait for an IFS time, and then randomly select a time slice to continue detecting, if there is no activity in the wireless network, send the data
- Before sending data, send a small request message to the target. After receiving the response from the target, send a large amount of data to ensure that there will be no collision.minimal overhead
14. Three kinds of framesInterval IFS: priority access control - DIFS (Distributed Coordinated IFS) longest,lowest priority
- PIFS (Point Coordinated IFS) medium length, medium priority
- SIFS (short IFS) shortest,highest priorityRespond immediately
- Superframe: point coordinationpoll terminal. Acknowledgment frame: Distributed
- DIFS is used in the CSMA/CA protocol. As long as the MAC layer has data to send, it will monitor whether the channel is idle. If the channel is idle, start sending after waiting for the DIFS period; if the channel is busy, continue to monitor until it can be sent.
15.Wireless encryption protocol WEP: Authentication and encryption, plaintext.Wireless Protected Access WPA/WPA2:802.1x authentication,RC4 encryption and TKIP data integrity
16. The encryption method usually used in wireless LAN is WPA2, whichThe security encryption algorithm is AES and TKIP
17. In order to make up for the security defects of the WEP protocol, the mechanism added to the WPA security authentication scheme isTemporary Key Integrity Protocol
18, Ad Hoc Network:peering between nodes. Each node is both a host,router again。MANET. The characteristics of MANET are: the network topology isDynamic changesof;Power supply energy limits the wireless terminal must use the most energy-savingwork in the same way; each node is both a host and a router.
19. Routing protocols in MANET:
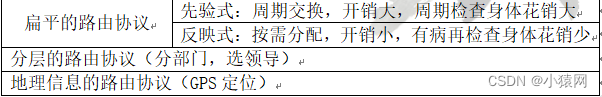
20.DSDVRouting Protocol:Distance Vector Protocol for Object Ranking, the flat type priori type, using the sequence number to solve the loop
21,AODVRouting Protocol:On-Demand Distance Vector Protocol, flat, reactive, low overhead, suitable for fast-changing networks.
22. Wireless network security: hide SSID, MAC filtering,WEP/WPA/WPA2、802.11iFour aspects
23, wireless network encryption protocol formulated by 802.11i standardWPAis a based onTKIP algorithm
24. Wireless network encryption protocolWRAPis a based onAESThe encryption scheme of the algorithm
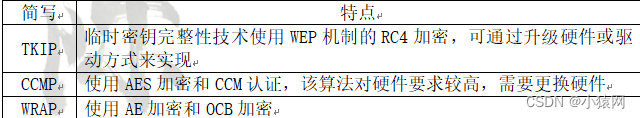
25, the three encryption mechanisms of WPA
26, the encryption algorithm adopted by 802.11i isAES
27. 802.11i: temporary key TKIP (RC4), mandatory encryption protocol CCMP (AES128), optional encryption WARP. 802.1x
28. 802.1X originates from the 802.11 standard. The original purpose is to solve the access authentication problem of wireless LAN users; if the authentication cannot be passed, the resources in the LAN cannot be accessed, which is equivalent to physical disconnection. 29. WEP:
RC4 Encryption, CRC-32 checksum, 24 initial vectors + 40-bit strings constitute a 64-bit WEP key, 24 initial vectors + 104-bit strings = 128; WPA design includes authentication, encryption and data integrity checks Three components. 48 initial vectors + 80 strings = 128 keys. RC4 encryption, compared with WEP, uses a temporary key to reduce security risks
30,WIFI6Supports full version of MU-MIMO; theoretical throughput up to9.6Gbps; follow protocol802.11ax; Compared with the previous WiFi5, inLarge bandwidth, high concurrency, low latency, low power consumption方面性能有显著提升。
31、漫游是由无线客户端主动发起的,决定权在无线客户端这一方面,而并不在无线设备(AP接入控制器、AC无线接入点)这一方面;漫游分为二层漫游和三层漫游;三层漫游必须在同一个SSID;客户端在AP间漫游,AP可以处于不同的VLAN
32、无线AP有两种工作模式,中继模式时网络SSID号均一致,而在桥接模式时网络SSID号不同
33、组播报文对无线网络空口的影响主要是(拥塞),随着业务数据转发的方式不同,组播报文的抑制分别在(AP交换机接口)和(AC流量模板)配置
34、AP发射功率的单位是dbm,天线增益的单位是dbi,这两个值越高,说明无线设备的信号穿透越强
35、蓝牙技术的特点:(1)全球范围适用。无需向申请许可证。(2)可同时传输语音和数据。(3)可以建立临时性的对等连接(Ad-hoc)。(4)具有很好的抗干扰能力。(5)蓝牙模块体积很小,便于集成。(6)低功耗。(7)开放的接口标准。(8)成本低。(了解即可)
36、GPRS接入时一种分组数据业务
(六)虚拟局域网VLAN
1、虚拟局域网VLAN概念:VLAN是指在局域网交换机里采用网络管理软件所构成的可跨越不同网段、不同网络、不同位置的端到端的逻辑网络。目前VLAN的主要标准是IEEE 802.1Q标准
2、不通VLAN在不同广播域,切割广播域,减少广播提高网络性能,增加网络安全,使网络易于维护,更具逻辑性,
3、在运营商中,一般会有多个用户和不同的业务流需要融合。运营商常用外层VLAN区分不同的业务流,在ONU或家庭网关处采用内层VLAN来区分不同的用户;这种处理方式要求运营商网络或用户局域网中的交换机都支持802.1qProtocol, at the same time through 802.1ad (operator bridge protocol) to achieve flexible QinQ technology
4, VLAN division method:①Static allocation of VLAN: based on port. ②Dynamic allocation of VLAN: based on MAC address (2 layers), network layer IP (3 layers), protocol division, rule strategy (high layer), etc.. No matter which method is used, an address and port can only be assigned to one VLAN.
5. The main methods of communication between VLANs are: (1) MAC address static registration (2) frame label (3) virtual link (4) routing method
6. VLAN experiment: When a bridge or switch receives a data frame from a computer workstation, it willAdd a label to this data frame,byIdentify which VLAN this data data frame comes from. The principles of labeling are: (1) Based on the data frame frombridge port(2) Based on data frameData link layer protocol source address(3) Based on data frameNetwork layer protocol source address(4) Based on data frameother fields or a combination of fields.
7. If the office users in the campus network do not need mobile office, use theswitch portThe VLAN division method is more reasonable; if some users need to move office, use theMAC addressThe VLAN division method is more appropriate
8.VLANDividedbenefit:① Control network traffic and suppress broadcast storms. ②Improve network security and control between different VLANs. ③Flexible network management, users can access the network anywhere to realize virtual workgroup
9. Communication between different VLANs: routers or Layer 3 switches are required
10.VLAN standard 802.1q (dot1q):Added 4B control information to the original Ethernet frame, which contains12 bitsVLAN identifierAT. 4094 VLANs are available.

11. Two VLAN ports:Access port Access (through a single VLAN) and trunk port Trunk (through multiple VLANs)
12. VTP(VLAN Trunk Protocol, VLAN trunk protocol): used to maintainVLAN的删除、添加、修改等管理操作的一致性
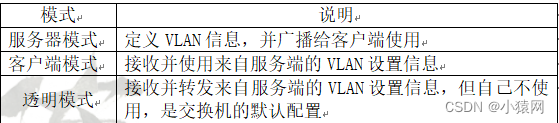
13、VTP的三种模式
14、双绞线与光纤:
- 双绞线:最大衰减值 回波耗损限值 近端串扰衰减值 开路/短路 是否错对
- 光 纤:最大衰减值 回波耗损限值 波长窗口参数 时延 长度
- 近端串扰仅用于双绞线测试
- ==波长窗口参数和回波损耗限值仅用于光纤的
- 最大衰减值既可是光纤也可是双绞线==
15、VLAN的一些叙述: - 一个新的交换机默认配置的是VLAN 1
- 一个VLAN能跨越多个交换机
- 各个VLAN属于不同的广播域(一个VLAN就是一个广播域)
- VLAN对分组进行过滤,增强了网络的安全性
16、WLAN接入安全控制中,采用的安全措施有SSID访问控制、物理地址过滤、WPA2安全认证、更改默认设置、更新AP
17、在缺省配置是交换机所有端口属于同一个VLAN中,
18、VLAN标记中 - 不同交换机之间的相同VLAN必须通过中继端口连接才能互相通信
- 交换机根据目标地址和VLAN标记进行转发决策
- 进入目的网段时,交换机删除VLAN标记,恢复原来的帧结构
- VLAN标记对用户是透明的
- VLAN简化了在网络中增加、移除和移动主机的操作
19、VLAN ID必填,由12bit表示,范围是1-4096,其中1是缺省VLAN,一直存在不能删除;1-1000可用于以太网,1002可用于FDDI和令牌环,1025-4096是扩展的VLAN ID
20、用于VLAN的以太帧的最大帧长是1522字节(由于用于VLAN的以太网帧的首部增加了4字节的VLAN标记字段,所以以太网最大帧长有原来的1518字节变为1522字节)
(七)冗余网关技术(HSRP/VRRP/GLBP)
1、当网络足够大的时候,网络规划师要考虑的不光是网络本身的性能问题,冗余技术也是必不可少的。常见的冗余网关技术有:a.热备份路由协议(HSRP);b.虚拟路由器冗余协议(VRRP);c.网关负载均衡协议(GLBP)
1)HSRP:思科的HSRP允许网络在一个路由器失效不能工作时,网络中的另一个路由器自动接管失效路由器,从而实现路由容错。
2)VRRP:是一种选择协议,它可以把一个虚拟路由器的责任动态分配到局域网上的VRRP路由器中的一台。控制虚拟路由器IP地址的VRRP路由器称为主路由器它负责转发数据包到这些虚拟IP地址。
3)VRRP:VRRP技术实现冗余备份和容错选择功能,交换机A与交换机B之间的连接线称为心跳线,其作用是为了防止VRRP协议报文(心跳报文)所经过的链路不通或不稳定,传递VRRP协议报文
4)GLBP:思科的,自动选择和同时使用多个可用的网关。和HSRP、VRRP不同的是,GLBP不仅提供冗余网关,还在各网关之间提供负载均衡,而HSRP、VRRP都必须选定一个活动路由器 ,而备用路由器则处于闲置状态。
六、广域网与接入网
(一)广域网与接入网
1、广域网概念:略
2、接入网由业务节点接口(SNI)和相关用户网络接口(UNI)通过Q3接口连接到电信管理网(TMN)。
(二)公用通信网
1、公用网技术包括:ISDN、BISDN、DDN、SDH、MSTP、移动通信网络、WiMAX网络、Ad hoc网络
2、综合业务数据网ISDN:基于电路交换,把数据、声音、视频信号三合一传输。
- ISDN两种速率:
N-ISDN基本速率BRI(2B+D)(主要是家庭)(144Kb/s)
N-ISDN基群速率(主速率接口)PRI(30B+D)(主要是企业)(2048Kb/s)(组成ISDN称为:B-ISDN PRI(宽带-ISDN-基群速率))(B代表宽带,N代表窄带) - B信道数据信道;D信道控制信道
2B+D=264+16=144Kb/s
30B+D=3064+64=1.984Mb/s(近似E1) - B信道一般用来传输话音、数据和图像,D信道用来传输信令或分组信息
3、数字数据网(DDN)是一种利用数字信道提供数据通信的传输网。
4、SDH(光同步数字传输网)网是一种全新技术体制,具有路由自动选择能力,上下电路维护控制、管理功能强,标准统一,便于传输更高速率的业务等优点。
5、MSTP(基于SDH的多业务传送平台)是指基于SDH平台同时实现TDM、ATM、以太网等业务的接入、处理和传送,提供统一网管的多业务节点。
6、WiMAX也叫802.16无线城域网或802.16。WiMAX是一项新兴的宽带无线接入技术,能提供面向互联网的高速连接
7、Ad hoc网络是一种特殊的无线移动网络。网络中所有结点的地位平等,无需设置任何的中心控制结点。网络中的结点不仅具有普通移动终端所需的功能,而且具有报文转发能力。具有以下特点:无中心、自组织、多跳路由、动态拓扑
8、Ad hoc网络一般有两种结构:平面结构和分级结构。
(三)接入网技术
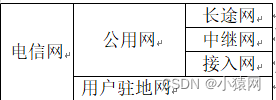
1、电信网
2、接入网技术可以分为有线接入技术和无线接入技术两类
3、有线接入技术包括:
- 基于双绞线的ADSL技术
- 基于HFC网(光纤和同轴电缆混合网)的Cable Modem技术
- 基于五类线的以太网接入
- 光纤接入技术
4、拨号接入:PSTN用户通过拨号在用户PC与Internet服务提供者(ISP)之间建立一条物理电路。
5、xDSL接入:数字用户线路(DSL)由于采用了先进的数据调制技术通过普通的电话线就可以达到非常高的吞吐量。xDSL是对所有不同DSL的总称。
6、DSL类型可分为:非对称DSL和对称DSL - 对称DSL:HDSL(时分复用)、SDSL、MVL及IDSL等
- 非对称DSL:RADSL、ADSL(频分复用)及VDSL(QAM和DMT)等
7、HFC网络的物理拓扑:包括局端系统(CMTS)、用户端系统和HF传输网络三部分 - HCF网络实现带宽接入时,==局端设备用于控制和管理用户的设备是CMTS,客户Cable Modem(大猫)
- CMTS一般在有线电视的前端,或在管理中心的机房,负责将数据信息与视频信息混合,送到HFC(经过64QAM调制,发送到用户端)。而上行时,CMTS负责将收到的经QPSK==调制的数据进行解调,传给路由器
- 用户端系统的Cable Modem,它不仅是Modem,还集成了协调器、加/解密设备、桥接器、网卡、以太网集线器等设备
- Cable Modem利用频分复用的方法将信道分为上行信道和下行信道
- 下行50Mbps,上行3Mbps
- ==采用HFC技术,光纤/同轴缆混合传输
- ==HFC是双向传输系统;由有线电视头端、长距离干线、放大器、馈线和下引线组成
8、ADSL(频分复用)的特点: - 采用DMT技术依据不同的信噪比为子信道分配不同的数据速率
- 采用回声抵消技术允许上下行信道同时双向传输
- 通过不同宽带提供上下行不对称的数据速率
- ADSL使用FDM和回波抵消技术实现频带分隔,线路编码为DMT和CAP
- ADSL2+技术可提供的最高下行速率达到24Mb/s
9、光网络接入:光纤通信,是指利用光导纤维传输光波信号的一种通信方法。
10、光纤通信的优点:传输频带宽,通信容量大;传输损耗小;抗电磁干扰能力强;线径细、重量轻
11、光纤接入网(OAN)从系统分配上分为:有源光网络(AON)、无源光网络(PON)
12、FTTx+LAN(光纤+局域网)实现宽带接入:许多小区宽带都是采用FTTx +LAN的模式提供服务的,其最终都通过光纤汇聚到汇聚层的核心交换机上,因此通常是星型拓扑结构。
13、FTTN(Node)是光纤到节点,根据光网络单元(ONU)的位置可以分为:FTTC(Curb)是光纤到路边,FTTH(Home)是光纤到用户,FTTZ(Zone)是光纤到小区,FTTB(Building)是光纤到大楼,FTTD(Desk)到桌面,FTTO(Office)到办公室,FTTF(Floor)到楼层
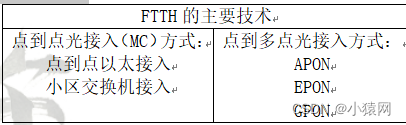
14、FTTH的主要技术:
15、无源光网络技术:PON是实现FFTB的关键性技术。其在光分支点不需要节点设备,只需安装一个简单的光分支器即可,因此具有节省光缆资源,带宽资源共享,节省机房投资,设备安全性高,建网速度快,综合建网成本低等优点。目前,PON技术主要有APON、EPON、GPON三种。
16、无源光网络的特点是: - 无源光网络由光线路终端(OLT)、光网络单元(ONU)和光分配网络(ODN) 组成
- 无源光网络一般其下行采用TDM广播方式、上行采用TDMA(时分多址接入)式
- PON无源光网络采用的网络架构是P2MP(点到多点)的网络架构. Optical fiber is used for data transmission, which has the characteristics of many access users, saving optical fiber resources and high-speed access.
- The passive optical network eliminates the active equipment between the central office and the user end, so that the maintenance is simple, the reliability is high, the cost is low, and the fiber resources can be saved.
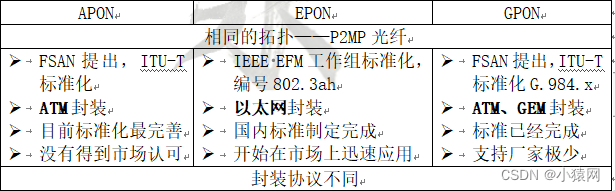
- Can be flexibly composed of tree, star, bus and other topological structures,Most suitable tree structure.
17. Comparison of three types of passive optical network
18. Traditional Ethernet technology does not belong to the category of access network, but belongs to the field of customer premises network. However, the application field of Ethernet is expanding to other public network fields including access network. The main reasons for using Ethernet as access means are as follows: 1)
Ethernet already has a huge network foundation and long-term experience knowledge.
2) All popular operating systems and applications are compatible with Ethernet
3) Good performance-price ratio, strong scalability, easy installation, activation and high reliability.
19. Briefly explain the advantages of GPON access compared with EPON access in supporting the development of "three networks in one":EPON is an Ethernet-based PON technology. It adopts point-to-multipoint structure, passive optical fiber transmission, and provides multiple services on Ethernet. GPON has a larger bandwidth than EPON. Its business bearer is more efficient and its optical splitting ability is stronger. It can transmit larger bandwidth services, realize more user access, and pay more attention to multi-service and QoS guarantees, but the implementation is more complicated, which leads to its The cost is higher than EPON.
20. The broadband access network based on Ethernet technology consists ofOffice side equipmentandUser side equipmentcomposition.Office side equipmentgenerally located inIn the community,User side equipmentgenerally located inResidential building;orThe office-side equipment is located in the commercial building, while the user-side equipment is located on the floor。The office side equipment provides the interface with the IP backbone network,The user side equipment provides the connection with the user terminal computer10/100Base-Tinterface, BureauThe side device has the function of converging the network management information of the user side device.
21. Features of Ethernet, ADSL, and GPON access methods: - The advantages of Ethernet access technology are very mature technology, standardization, low average port cost, high bandwidth, and low cost of client equipment. It is convenient and efficient to treat a community as a local area network.
- The characteristic of ADSL access is to use the existing telephone line as the transmission medium, without modification or rewiring, and easy to install. But the transmission data is asymmetrical, uplink 1Mbps, download maximum 8Mbps, suitable for use in a small range of 3-5KM.
- GPON is a passive optical network standard, composed of optical line terminal OLT, optical distribution network 0DN and client 0NT/ONU, the biggest feature is high bandwidth, high efficiency, large coverage, rich user interface, etc., which can be guaranteed by QoS Full-service access, good support for TDM services, simple and efficient adaptation and packaging, and powerful OAM capabilities.
22. Comparison table of some performance indicators of the three authentication technologies:
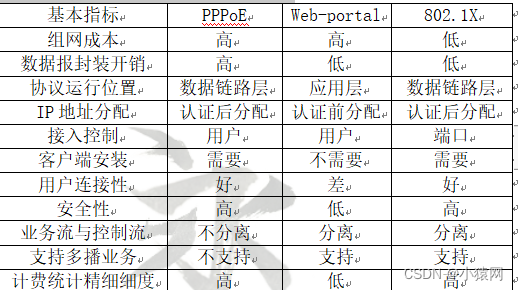
23. PPPoE and IPoE - The authentication mechanism of PPPoE is more complicated, and it has higher requirements on the processing capability and memory resources of the equipment. However, the traditional BRAS does not carry multiple services, so it is insufficient in terms of equipment scalability and reliability.
- IPoE authentication involves user equipment, network service systems, etc., and does not simply support dhcp. And IPoE authentication is not a point-to-point communication, the key issue that must be solved is the security issue, and the current standard is not uniform.
(4) Frame Relay FR
1. Frame Relay FR is an evolution and improvement of X.25.
- work on OSI'stwo floors belowphysical layer and link layer。
- Create a virtual circuit on the second layer(Same as X.25, it also supports permanent virtual circuit PVC and switched virtual circuit SVC) to carry data services, so the third layer is simplified.packet switching。
- Provides connection-oriented services; an efficient data link technology; utilizes the advantages of optical fiber communication and digital network technology
- FR only does error detection,no retransmission,no flow control,congestion control only,error detection and interleaving layer。
2. The main advantages of frame relay are
- based onTransparent transmission of packet (frame) switching,able to provideconnection-orientedservices
- variable frame length, the length can reach 1600~4096 bytes, and can carry data frames of various LANs.
- The data rate can be 2~45Mbps
- both can receiveneed to provide bandwidth,Can also handle bursty data transfers
- No flow control and retransmission mechanism,little overhead
- Fully exploit the advantages of optical fiber communication and digital network technology
(5) HDLC protocol
1、High-level Data Link Control Protocol HDLC: Bit-Oriented Synchronous Link Control Protocol. Usually use CRC-16, CRC-32 check. Frame Boundary 01111110 "Kicking the ball at both ends". The size of the user data field INFO. The sliding window protocol with an unfixed size is used in the HDLC of the data link layer.
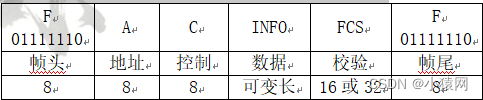
2. In the HDLC protocol, the frameThe number and reply are stored in the control field
3. In the HDLC protocol, if the SERJ response is used in the monitoring frame, it indicates that the error control mechanism isSelective Resend/Selective Reject ARQ
- 00–ready to receive (RR); 01–reject (REJ); 10–not ready to receive; 11–selection to reject (SREJ)
- When using the HDLC protocol for data transmission, RNR5 indicates the next received frame numbershould be 5,butReceiver is not ready, suspend receiving

4. Various frame formats in HDLC

- N(S): Send frame sequence number.
- N®: The frame sequence number expected to be received, and it is the confirmation of the frame before N®.
- S: Monitoring function bit.
- M: Unnumbered function bit.
- P/F: Inquiry/End (Poll/Final) bit, as the query bit when the command frame is sent, appears as the P bit; as the end bit when the response frame is sent, appears as the F bit.
5. Traffic mechanism in HDLC protocol - Only the control field of the information frame (I) contains the transmission sequence number N (S)
- The HDLC transmitter does not slide the window immediately after sending an information frame (I). The window will slide only after receiving an acknowledgment from the receiver
After the receiver successfully receives a frame, it moves the rear edge of its receiving window forward by one frame.
7. Internet connection
(1) Concept/method of network interconnection
1. Internetworking refers to the use of various network interconnection devices to connect the same type of network or different types of networks and their products to form a network with a larger geographical coverage and stronger functions. 2. Network interconnection
includes The following aspects:
1) Interconnection: refers to the network inphysical connection, provides the material basis and possibility for the data exchange of the two networks, but it does not guarantee that the two networks will be able to exchange data, it depends on whether the communication protocols of the two networks are compatible with each other 2) Interconnection: refers to the network in
physical And logic, especially logical connection
3) Intercommunication: refers to the exchange of data between two networks
4) Interoperability: refers to the ability of different computer systems in the network to transparently access each other's resources
3, according tonetwork levelThe structural model of the network interconnection level is as follows:
1)data link layerinterconnection. The interconnection device isbridge, allowing the data link layer and the physical layer protocol of the interconnection network to be the same
2)Network layerinterconnection. The interconnection device isrouter, allowing the network layer of the interconnection network and its protocols at each layer to be the same or different
3)high levelinterconnection. The interconnection between networks with different protocols at the transport layer and above layers belongs to the high-level interconnection, and its interconnection equipment isgateway. Many of the gateways used areapplication layer gateway, usually calledapplication gateway.
4. According to the classification of interconnected devices between networks
1)repeaterFinishphysical layerThe interconnection between them mainly plays the role of signal regeneration and amplification, extending the network distance
2)bridgeFinishdata link layerThe connection between two or more network segments can be connected. The bridge plays the role of data receiving, address filtering and data forwarding, and is used to realize data exchange between multiple network systems. mainConnect to the same LAN.
3) The router is the interconnection of the network layer, which mainly solves problems such as routing selection, congestion control, error handling and segmentation technology 4) The gateway
is a network connection device that works above the third layer, and its function is to connect multiple high-level protocols different networks so that they can communicate with each other.
5. The method of network interconnection: local area network-local area network interconnection (LAN-LAN); local area network-wide area network interconnection (LAN-WAN); wide area network-wide area network interconnection (WAN-WAN) 1) LAN-LAN
network Interconnected devices can beRepeaters, hubs, and bridges, or routers.
2) The interconnection of LAN–WAN occurs inNetwork layer. LAN–WAN is where interconnected devices arerouter
3) WAN–WAN interconnection occurs in the OSI/RMTransport layer and its upper layers. WAN – Interconnection of WANsdevice is a gateway, the gateway is used for heterogeneous network interconnection in the following occasions: a. heterogeneous LAN. b. interconnection between LAN and WAN. c. interconnection between WAN and WAN. d. interconnection between LAN and host (when the host When the operating system is not compatible with the network operating system, it can be connected through a gateway)
(2) Routing algorithm
1. Routing selection refers to the problem of which rule is used to determine which of the multiple routes between the source node and the destination node is used as the path for forwarding data packets when the communication subnet transmits data packets. Divided intostatic and dynamicAlgorithm
2. Some basic requirements that the path selection algorithm meets:Correctness, simplicity, robustness, reliability, fairness.
3. Whether the routing algorithm can follow the networkTraffic or Topology AdaptiveThe routing algorithm can be divided intoNon-adaptive routing algorithm (static)andAdaptive Routing Algorithm (Dynamic).
4. The static routing algorithm means that the route between the source and the destination ispredetermined, does not require the protocol to exchange the latest network conditions. The characteristics are: the algorithm is simple, the overhead is small, but the performance is poor and the efficiency is low.
5. In the dynamic routing mode, all nodes participate in routing selection, and determine the best routing according to the specified criteria.
6. The characteristics of the distance vector routing algorithm: very simple, the routing protocol (such as RIP) based on this algorithm is easy to configure, maintain and use, the biggest problem is slow convergence, and in the process of convergence, routing loops may occur Question
7. How to prevent loops in routing protocols
- Maximum hop count: When a routing entry is sent out, it will automatically add 1 hop, and the maximum hop count is 16 hops, which means unreachable
- Split horizon: a routing message is not sent to the source of the message(Do not send the routing information obtained from a neighbor node to the neighbor node)
- Split horizon for reverse poisoning: Set the routing information learned from a neighbor to 16 hops and send it to that neighbor. safer
- Suppressing timers and triggering updatesAlso prevents loops
- The router of the distance vector routing protocol updates its routing table according to the information sent by the neighbors
- In the distance vector routing protocol, the routing information received by each router comes from its neighbor routers.
8. Link state routing algorithm: LS routing algorithm for short. Each node participating in the algorithm is required to have complete network topology information, and they perform the following two tasks: a. Actively test the status of all neighboring nodes; b. Periodically propagate the link status to all other nodes (Or routing node)
9. Autonomous system (AS): From the perspective of routing, a system composed of a series of routers and networks with the same routing strategy and under the same management organization is called AS 10, intra-domain routing
and Inter-domain routing: Routers within an AS run the same routing protocol, namelyInterior Gateway Protocol (IGP), Interior Gateway Protocol is also called intra-domain routing protocol. The purpose of IGP is to find the shortest path between all routers in an AS.
11. Policy routing and routing strategy: - Routing Policy acts onrouting,mainImplemented functions such as route filtering and route attribute setting, which changes the path of network traffic by changing routing attributes (including reachability). Control the publication of routes, control the receipt of routes, and set the properties of specific routes.
- policy routing is inWhen the routing table has been generated, instead of forwarding according to the existing routing table, it is a routing selection mechanism based on user-defined policies, from more dimensions (incoming interface, source security zone, source/destination IP address, user, service, application) Decide how to forward the message,Increased flexibility in message forwarding control。
- Policy routing does not replace the routing table mechanism, but takes effect prior to the routing table, specifying the forwarding direction for some special services.
12. RealizeMulti-outlet load balancingBalance is usually based onsourceaddress andTargetAddress in two ways - Source address-based load balancing, according to the source address, requests from the same source address are forwarded to the same server or a specified link. It is suitable for classifying requests according to the source address, and then forwarding to the specified server or link.
- The load balancing of the target address is similar to that of the source address, but the basis of the decision is the target address.
Chapter 3 Internet Protocol
1. Network layer protocol
(1) Internet Protocol IP
1. Running at the network layer, it can realize the interconnection and intercommunication between heterogeneous networks. It is an unreliable, connectionless protocol. The IP protocol is the most basic part of the TCP/IP Internet design.
2. Fragmentation and reassembly: Under ideal conditions, the entire datagram is encapsulated in a physical frame, Efficiency on the physical network can be improved.
1) Fragmentation: The IP protocol uses fragmentation when encountering a network with a smaller MTU
2) Reassembly: After fragmentation, encounterNo reassembly for larger MTU networks, and keep small groups, knowing the purposeThe host reassembles at one time after receiving the complete。Firstfield isIDfield,secondfield isData length, which is the number of bytes.thirdfield isoffset value, that is, the position of the fragment in the original datagram is calculated as a multiple of 8 bytes.fourthone isM logo, which is used to identify whether it is the last fragment
3. The fragmentation and reassembly of IP datagrams need to use the header of the messageIdentifier, data length, segment offset value and M flagWait for four fields. inThe role of the identifier field is to identify each segment belonging to the same message

4. TCP/IP protocol cluster: divided into 4 levels; main protocol, STDD (UDP)
5. Loose routing and strict routing
- Loose routing:Must be specified by the source siterouter
- Strict routing: only through the router designated by the source end, and not through the router not designated by the source end.
6. Routing protocol management distance: - Direct port - 0
- Static Routing - 60
- OSPF——10
- IS-IS——15
- RIP——100
7. Commonly used protocol encapsulation and protocol number:
8. Common protocol port number of TCP/IP protocol
9.IP Protocol: Internet Protocol, the most important protocol at the network layer.connectionless, unreliable,packet switching
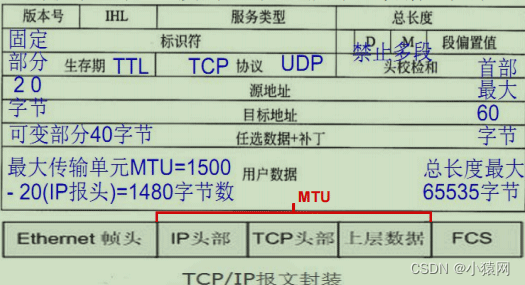
10. IP protocol data unit, several important fields - Identifier:Used for fragmentation and reassembly; the flag in it indicates whether there are still fragments。
- IHL: IP header length, 20 bytes (32 bytes)
- ==Service Type: Prioritization, Reliability
- Total length: including IP header (number of bytes) ==
- Header checksum: only checks the IP header, does not include data
- ==Source address: IP address; Destination address: IP address
- 生存期:路由器个数+1,超过定值丢弃,防止数据报在网络中无限转发
- 用户数据:MAC帧长1518,MTU1500,1518-14-4-20=1480,再-20=1460
11、IP私有地址:不能用于公网,只能在内部局域网使用,它们在Internet上也不会被路由,但可以通过NAT等技术与公网通信==。下表为标准A、B、C类私有IP地址块
12、几种IP特殊地址:具有特殊意义 - 0.0.0.0:不确切地址,一般设备刚启动尚无IP临时使用,表示本机。也叫默认路由地址
- 255.255.255.255:限制(受限)广播地址,==同一广播域内的主机,表示本网所有主机。“大广播”
- 127.0.0.1:回环(送)地址==,别名Localhost,向自己发送测试数据。用于测试。
- 169.254.x.x:自动专用地址,==找不到DHCP服务器,主机给自己分配的一个IP
- ==单播地址:单个IP、主机地址
- 网络地址:主机号各位全为0,表示本网络 整个网络,不分配
- 广播地址:主机号各位全为1,发送给特定 网络的所有主机,不分配。也叫直接广播地址,也叫子网广播地址,“小广播”
组播地址:224.0.0.1,从224.0.0.0到239.255.255.255,表示一个组内的主机
13、TCP/IP网络中最早使用的动态路由协议是(RIP)协议,这种协议基于(距离矢量)算法来计算路由
14、在交换网络中VTP协议的作用是==将VLAN信息传播到整个网络中,==让同一管理域中的所有交换机共享vlan配置信息
15、静态修剪就是手工剪掉中继链路上不活动的VLAN
16、动态修剪使得中继链路上所有共享的VLAN都是活动的
17、动态/静态修剪要求在VTP域中的所有交换机都配置成服务器模式
(二)IPv6协议
1、IPV6概念:下一代互联网NGI, currently version 6. An IPV6 packet consists of 1 fixed header, n extended headers (optional) and the payload of the upper layer protocol.
2. IPV6 fixedHeader (40 bytes, 320 bits in total): Each field explains the meaning:
- Version 0110, 4 digits, representing IPV6
- Communication type: 8 bits, IP packet priority, same service type
- Flow mark: 20 bits, marking specially processed packets
- Payload length: 16 bits, except fixed, extended and payload
- Next header: 8 bits, indicating the extension header or high-level protocol
- == Hop limit: 8 bits, the detection route loop minus 1 becomes 0 and discarded
- ==Source address: 128 bits, the address of the sender
- Destination address: 128 bits, the address of the receiving end
IPV6 extensionheadtype:6 options, the role is to retain the functions of some fields of IPV4, but only for special equipment to check and process, not for each
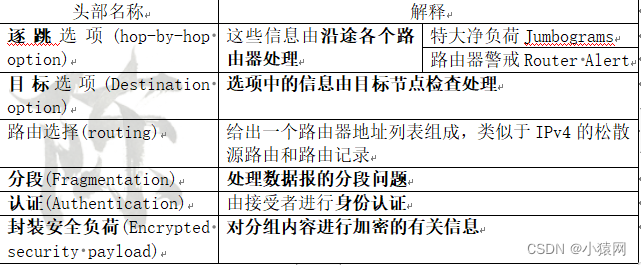
- IPV6 extended header format: the first byte: is the next header selector, indicating the type of the next header.0 hop-by-hop option, 60 destination option, 43 source routing, 44 segmentation, 51 authentication, 50 encapsulation security payload, 59 no next header
2nd byte:Extended header length. Counting in 8 bytes, excluding the first 8 bytes, if it is 8 bytes, the field is 0, if it is 16 bytes, the field is 1, if it is 24 bytes, the field is 2

- Optional part: encoded in TLV form, T type 1 byte, L length, V data.
4. IPV6 extended header groupingPackaging orderas follows:(IPv6 Job-hopping Notes) - (1) IPv6 header
- (2) Hop-by-hop option header
- (3) Target option header (information to be processed by the first target node)
- (4) Routing header
- (5) Segment header
- (6) Authentication header
- (7) Encapsulate the safety load head
- (8) Target option header (information to be processed by the last target node)
- (9) Upper layer protocol header
5, ipv6 common test prefix (The format prefix is used to indicate the address type or subnet address): - Global unicast prefix: 001
- link localPrefix: FE80(1111 1110 10)
- site localPrefix: FEC0(1111 1110 11)
- Uncertain address: 0:0:0:0:0:0:0:0 (cannot be assigned to any node)
- Loopback address: 0:0:0:0:0:0:0:1 (send ipv6 packets to itself)
- 2000::/3 global unicast address
- FC00::/7 unique local unicast address range
- FE80::/10 link-local unicast address range
- FF00::/8 multicast address range
- 2002::/16 is reserved for 6to4 tunneling technology
6. IPV6 addressClassification: ①Unicast address, ②Anycast address, ③Group (multi)cast address - Unicastaddress:identify an interface, packets whose destination address is a unicast address will be sent to the identified interface
- multicastaddress:Identify multiple interfaces, the packet whose destination address is the multicast address will be sent to the identified == all interfaces
- Anycast address: identifies multiple interfaces, packets whose destination address is anycast address will beSend to the nearest identified interface; cannot be used as a source address, only as a destination address ==,and can only be assigned to routers. Represents the identifier of a group of interfaces. Anycast addresses are allocated in the unicast address space and consist ofSubnet prefix + all 0
- IPV6 nodefinitionbroadcastaddress
- Unicastaddress:4 types: Aggregatable global unicast, link-local address, site-local address, special unicast address
- ① Aggregable global unicast (equivalent to public network IPv4): prefix 001(/3). 2000(/3)
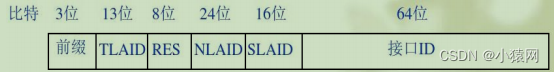
- ② Link-local address (equivalent to automatic dedicated IP): prefix 1111 1110 10 (/10 or /64),Used for communication between adjacent nodes on the same link. Link-local addresses are equivalent to Automatic Private IP Addresses (APIPA) in IPv4,can be used for neighbor discovery, and alwaysautomatic configuration, packets containing link-local addresses will not be forwarded by routers

- ③Site local address (equivalent to private IP): format prefix 1111 1110 11 (/10 or /48 or /64) is equivalent toPrivate network address in IPv4

- ③Site local address (equivalent to private IP): format prefix 1111 1110 11 (/10 or /48 or /64) is equivalent toPrivate network address in IPv4

- ④Special unicast address: uncertain address 0:0:0:0:0:0:0:0, loopback address 0:0:0:0:0:0:0:1.
7. Multicast address: format prefix 1111 1111(/8), also includes flag, range, group ID field

8,Anycastaddress:It is only used as a destination and is only assigned to routers. It can be used as a destination address, but not a source address. Represents a set of interface identifiers.By default router interfaces are assigned anycast addresses.subnet-router anycast address,The subnet prefix must be fixed, and the rest of the positions are all 0
9. An IPv6 packet can have multiple extension headers, and the extension headers should be as followsorder:Hop-by-Hop Options Header -> Routing -> Fragmentation -> Authentication -> Encapsulation Security Payload -> Destination Station Options
10.IPV6 addressconfiguration: The default auto-configuration has2 kinds: - ①Stateful auto-configuration: Dynamic Host Configuration ProtocolDHCPRealized automatic configuration of IP address
- ②stateless autoconfiguration:①get link-local address: link-local addressprefix1111 1110 after 10Add network card MACaddress, generate a link-local address, and issue an ICMPv6 request to confirm uniqueness. ②Obtain an aggregatable global unicast address: Request to all multicast ICMPv6 routers in the local link,Host gets unicast prefix 001After adding your own interface ID, automatically configure the unicast address
1, the comparison of IPV6 and IPV4
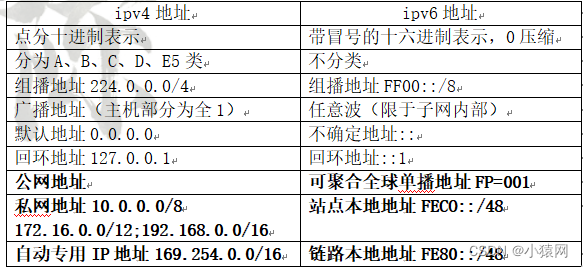
11,IPv6address compared toIPv4Improvement: 4 aspects: - ①Extended addressability: Extended to 128 bits, supports multi-level address hierarchy,Improve multicast, add anycast is more practical
- ②Simplified header format: The number of IP header fields is reduced from 12 to 8, and the number of intermediate routers is reduced from 6 to 4, improving efficiency
- ③Improved routing options:Routing options are placed in the extension header,Insert routing options only when needed, more flexible and smoother
- ④Provide stream markers: special treatment for some groups,Can provide special quality of service12.
IPv6 address auto-configuration: full state auto-configuration, stateless auto-configuration
13. Neighbor discovery and Qos support: Neighbor discovery protocol is a basic part of IPV6 protocol, which implements ARP in IPV4 The routing discovery part of /ICMP, all functions of the rerouting protocol, and has a neighbor unreachable detection mechanism. Five types of IPv6 control information packets are defined to implement various functions of the neighbor discovery protocol: (1) Router Solicitation (2) Router Advertisement (3) Neighbor Solicitation (4) Neighbor Advertisement (5) Redirection 14. IPv6
header middlepayload lengthIdentified by:The number of bytes in an IPv6 datagram excluding the basic header and the extended header。
(3) IPv6 transition technology
1、IPv6Transition to IPV4Technology: Yes3 techniques:
- ①tunnelTechnology: used to solve the problem of communication between IPV6 network nodes through the IPV4 network. (time Tunnel)
优点:充分利用现有网络投资,过渡初期实现方便。缺点:路由器隧道出入口负载重,实现复杂,不利于大规模应用
==技术:有6to4隧道、6over4隧道、ISATAP隧道
==6to4地址形式:2002:IPv4:子网ID::接口ID - ②协议翻译(NAP-TP)技术:使得纯IPV6节点之间和纯IPV4节点之间可以通信。(英汉互译)
优点:不需要升级改造,开启NAT-PT即可。缺点:转换不能完全保持原有含义,缺乏安全性
技术:有SIIT翻译、NAT-PT翻译、TRT翻译 - ③双协议栈技术:使得IPV4和IPV6共存于同一设备和同一网络中。(英汉双语)
优点:网络规划相对简单,可以充分发挥安全性、路由约束和流支持。缺点:对设备要求较高,维护大量协议和数据,升级改造投资大、建设周期比较长。
技术:有BIS双栈、BIA双栈 - 静态模式提供一对一的IPv6地址和IPv4地址的映射;动态模式也提供一对一的映射,==但是使用一个IPv4地址池;NAPT-PT(网络地址端口转换)==提供多个有NAT-PT前缀的IPv6地址和一个源IPv4地址间的多对一动态映射
(四)IPv6路由协议和移动IP协议
1、IPV6路由协议:定义了5种路由协议:
- RIPng:RIPv2的扩展,UDP521端口
- OSPFv3:OSPFv2的扩展,做了较大改进
- BGP4+:BGP4的扩展,用来支持IPV6
- ICMPv6:ICMP的扩展,集成了ARP功能
- IS-IS:中间系统到中间系统,IS-IS属于内部网关路由协议。IS-IS是一种链路状态协议,与TCP/IP网络中的OSPF协议非常相似,使用最短路径优先算法进行路由计算。
2、移动IP的概念:移动主机在移动的同时,能够在任何地方使用他的家乡地址进行联网
3、移动主机通过在无线通信网中漫游来保持网络连接
4. The principle of mobile IP: the mobile host assigns a home address as a permanent identifier. If assigned to a fieldcare-of address,Home address gets foreign care-of address
5. The key technology to realize is that the mobile host has a home network address and obtains a foreign care-of address.
6. Three entities of mobile IP: mobile node, home agent, and foreign agent (home/foreign agents are collectively referred to as mobile agents, which require go throughAgent discovery, registration, data transferThree stages)
7. During the stateless auto-configuration of IPv6 addresses, the hostFirst must automatically form a unique(link-local unicast address), and then send to the routerRouter Solicitationrequest message in order to obtain the address configuration information provided by the router.
(5) Address Resolution Protocol ARP/RARP
1. The ARP protocol is used to resolve a 32-bit IP address into a 48-bit physical address.ARP works at the data link layer, but belongs to the network layer protocol。
2、Address Resolution Protocol ARP (in Layer 2 Ethernet frame):IP query MAC address, a query/answer mechanism. ARP cache table, ARP spoofing, ARP virus, proxy ARP, reverse RARP
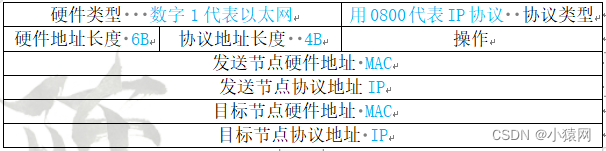
3, address resolution protocol ARP: cache table: start-run-cmd, enter arp -a (-s, -d, etc.) and press Enter
4, display all The ARP cache table is arp -a; the static addition is arp -s; the clear ARP cache is arp -d;
5. The ARP request usesbroadcast6. ARP Request is sent
by broadcast; ARP Response is sent by unicast
7. The ARP table is used to cache the correspondence between the IP address of the device and the Mac address. The advantage of using the ARP table is == (limit the number of network broadcasts) ==
8. Address Resolution Protocol ARP: GenerationARP management, a router acts as a third-party agent to perform ARP request/reply; (a router replaces the remote target to answer the ARP request)
9.The so-called "proxy ARP" refers to the (Router closest to source host) to pretend to be the target hostanswer source hostARP request
10,Reverse Address Resolution Protocol RARP: Find IP by MAC, a common phrasediskless workstation, the device has no hard disk,Unable to log IP, Send a broadcast when it is just started, and use MAC to obtain IP. == A RARP server is needed to record the correspondence between MAC and IP.
11. == ARP spoofing and ARP virus: If a fake ARP response message is sent to a certain host, so that the information it sends cannot reach the expected host or arrives at the wrong host, this constitutes an ARP spoof. For example: the network management software obtains the MAC addresses of the entire network. Viruses masquerade gateway MAC to collect information
(6) Control Message Protocol ICMP
1、ICMP protocol: Internet Control Message Protocol, a sub-protocol of the tcp/ip protocol family,The protocol of the network layer, the protocol number is 1. Send related communication control and error messages. Like investigators, spies.Encapsulated in IP packets,and thus unreliable。The checksum of ICMP is the entire ICMP and is also required
2. The functions of the ICMP protocol include (Report communication failure), when the network communication is congested, the router sends ICMP (source suppression) message.
3. To determine whether a network can be connected, the host should send ICMPecho request
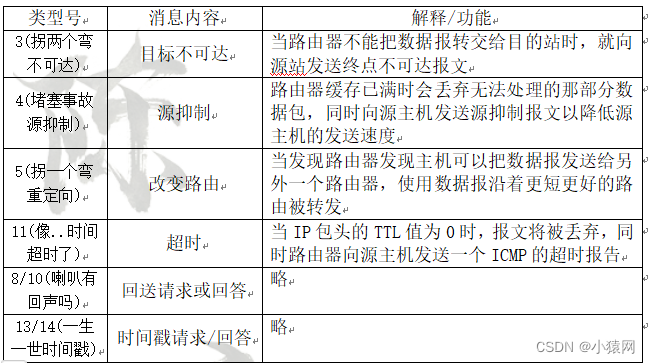
4. ICMP message format

5. In ICMP error report format, excepttype, code and checksumIn addition, also needAdd the first 64 bits of the error message so that the source host can locate the error message
Second, the transport layer TCP/IP protocol
(1) Transport layer protocol TCP
1、TCPprotocol:transmission control protocol,Sequential, connection, reliable, full-duplex oriented byte stream, variable sliding window, back-N frame ARQ protocol for error control, buffer accumulation transmission. Protocol number 6
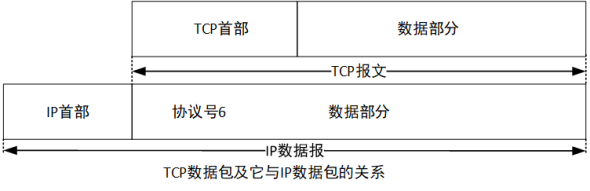
2. TCP protocol: Transmission Control Protocol, the following is the TCP segment (segment header), TCP header (transmission header), and TCP packet header (header) format: 3. TCP protocol: several important
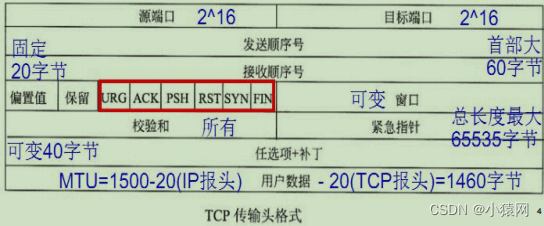
fields
- Source port, destination port: 16 bits, 2^16 (0-65535)
4.URG: The urgent pointer is valid, indicating that there is out-of-band data that needs to be transmitted
5、ACK: The response sequence number is valid
6、PSH: The push function is valid, indicating that the receiver should hand over the message to the upper layer protocol as soon as possible without waiting for the buffer to be full.
7、RST: reset to initial state, reconnect
8、SYN: Establish a synchronous connection
9、FIN: end release connection
10、Checksum: including TCP segment header, data, pseudo-segment header
11、TCPThree-way handshake and its protocol status:
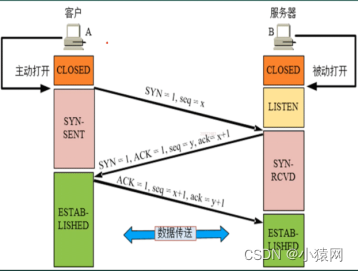
LISTENserverWaiting for connection status (passive open)
SYN_SENT The client initiates a connection (actively open), then if the SYN timeout or the server does not exist –> CLOSED
SYN_RCVD The server receives the SYN packetThis is the state when
ESTABLISHEDAfter completing the three-way handshake, enterconnection establishment status, indicating that data transmission can be carried out
12,SYNThe flag field is set to "1"happened atConnection request and response phase; when an error occurswrong connectionhourRSTThe flag field is set to "1";whenconnection termination requesthourFINThe flag field is set to "1”;ACKThe flag field is set to "1" indicates thatTCP segment with piggyback acknowledgment.
13. Termination of the TCP connection (4-way handshake): (1) The client sends a FIN termination connection message (2) The server sends an ACK confirmation message (3) The server sends a FIN termination connection message (4) The client sends ACK confirmation
14. TCP uses three handshakes to establish a connection, which can preventerror connection; The flow control protocol is a variable-size sliding window protocol.
15. TCP uses an error control mechanism to ensure the reliable transmission of data. The error control mechanism of TCP is mainly confirmation and retransmission.
16. In a TCP connection,If a party wants to close the connection,At this time, the response should be after receiving the message, after sending the message for positive confirmation, it should receive the application notification and then send the close connection message。
17、TCP congestioncontrol:The packet arrival rate is greater than the forwarding rate of the router, resulting in congestion. The solutions are:
①Retransmission timer
② Slow start (slow start)
③ Congestion avoidance
④ fast retransmission
⑤ Variable sliding window
⑥Select retransmission ARQ
TCP congestion control: timeout retransmission timer, retransmission is an important measure to ensure TCP reliability. Every time TCP sends a message segment, it sets a timer for this message segment. As long as the time set by the timer is up, but the confirmation has not been received, the segment will be retransmitted. The
retransmission time should be set reasonably, which is generally related to the round-trip time, average delay, and time deviation. Most of them estimate the round-trip time by observing the packet delay in the most recent period
TCP congestion control: slow start, the sender gradually expands the size of the window before receiving an acknowledgment. 1, 2, 4, 8, etc. double according to the exponential law, and finally reach the threshold threshold. When a timeout occurs, return the congestion window to 1, and start slow start again.
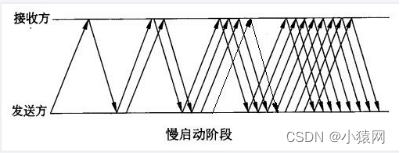
18. TCP congestion control:congestion avoidance,After the window reaches the threshold threshold, enter the congestion avoidance phase, TCPEnlarge the window with a linear increase method, increasing by +1。When congestion occurs, the threshold is halved. Happen again and halve again. Multiply and halve exponentially
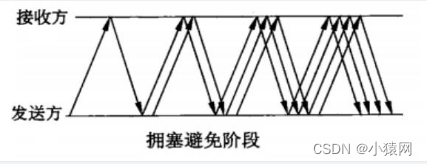
TCP congestion control:fast retransmit, == The sender retransmits after receiving 3 repeated ACKs in a row, without waiting for the timer
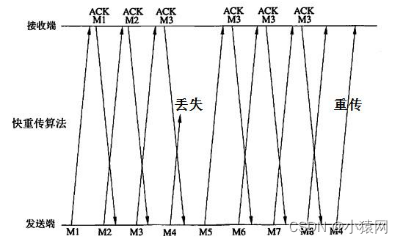
19. There is a possibility of deadlock in the TCP protocol. The solution is to set the timer.Send a detection message after the timer expires.
20. SYN Flooding attack: Use TCP three-way handshake to maliciously cause a large number of TCP semi-connections, exhaust server resources, and cause system denial of service 21. Forged
TCP serial number attack: Some operating systems cannot implement the TCP/IP protocol stack very well 22. Teardrop attack: When some operating systems implement the TCP/IP protocol
stack, they cannot handle the overlap of IP fragment packets well, causing the system to crash
23. Ping of Death attack: When some operating system protocol stacks process IP fragments, they cannot handle the reassembled very large IP datagrams well, resulting in buffer overflow and system crash
(2) Transport layer protocol UDP
1. UDP (User Datagram Protocol), which is mainly used for transmissions that do not require the arrival of packets in sequence.The inspection and sorting of packet transmission order is done by the application layer,carrySimple unreliable message transfer service for transaction oriented
2. UDP protocol (no sequence number):User Datagram Protocol,Connectionless, unreliable, sequence-unguaranteed, error-free flow control mechanism。Checksum includes: UDP header (8 bytes), data, pseudo-header。Protocol No. 17
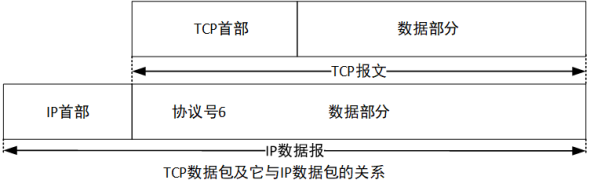
3. UDP protocol: UDP message format is as follows:small amount of data transferred,The high-level program is responsible for solving data sorting, Error control, etc.less overhead(header 8 bytes), often used in network management
4. Although the UDP protocol does not provide any error control mechanism, UDP uses checksums to ensure that UDP packets are sent to the correct destination
5.TCP (suitable for remote) supports data transmission, UDP supports audio and video transmission
6. The UDP protocol providesport addressing
7. The difference between the TCP protocol and the UDP protocol
- TCP protocol is connection-oriented, UDP protocol is connectionless
- The TCP protocol guarantees the order, but the UDP protocol does not.
- The TCP protocol guarantees data correctness, and the UDP protocol may lose packets
- The TCP protocol requires more system resources, while the UDP protocol requires less
- The transmission speed of the TCP protocol is slow, and the transmission speed of the UDP protocol is fast.
8. (Understanding) The NTP protocol is based on the 123 port of the UDP protocol. It is suitable for the application scenarios of time synchronization by NTP: network management; billing system; multiple systems collaborative processing same complex event; incremental backup between backup server and client; system time
3. Application Layer Protocol
1、DNS protocol: domain name resolution protocol, which is used to resolve the host domain name to the corresponding IP address. is a distributed database,C/SWay of working. mainly based onUDPprotocol, few useTCP,The port numberBoth are 53. Commonly used domain names are as follows
2. DNS protocol: DNS server,dedicated to domain name resolution, using C/S structure,One-to-one correspondence between domain name and IP。hierarchical namespace, for example: www.edu.xnsxy.com.
3. Divide domain name servers according to spatial hierarchy: root domain name, top-level domain name, authority domain name, local domain name
4. A legal domain name can only be composed of numbers, letters, and underscores, and cannot Start and end with an underscore
5, can be used fortest DNSThe commands for the service status areping、nslookup、tracert
6、windows中可通过DNS Client服务来阻止对域名解析cache的访问
7、DNS通知是一个种推进机制,作用是使得辅助域名服务器及时更新信息
8、DNS解析顺序:本地缓存记录-区域记录-转发域名服务器-根域名服务器
9、按照作用划分域名服务器
10、DNS协议:解析顺序工作原理:
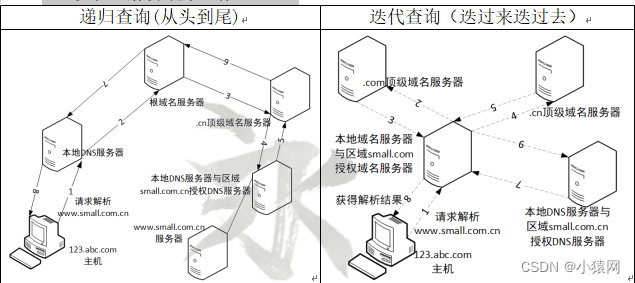
11、本地hosts>本地缓存>首选DNS>备用DNS>缓存DNS>主DNS>转发DNS>辅助DNS>根DNS,如果还是没有得到解析的话就是使用NetBIOS名字解析
12、根域名服务器采用的迭代查询,中介域名服务器采用的是递归查询
13、DNS记录类型:
- A:IP地址,主机地址(正向解析,域名->ip,指定主机名或域名对应的IP地址记录)(record type=1)
- NS:权威名称服务器(record type=2)
- CNAME:别名的正则名称(record type=5)==
- SOA:标记权威区域的开始,指明区域主服务器和管理员邮件地址(record type=6)
- PTR:域名指针(IP地址映射)(IP地址解析为主机名)(反向解析ip->域名)(record type=12)
- MX:邮件交换(record type=4)
- HINFO:记录提供电脑或操作系统的类型==(主机描述)(record type=13)==
- 正向解析:域名->ip地址
14、DNS服务的安全配置有: - ①转发器、高级选项卡等
- ②禁用递归、启用循环、启用网络掩码排序、保护缓存防止污染
- ③新建主机、新建别名等
15、DNS其他考点: - DNS查询方向:正向查询A,反向查询PTR
- DNS zone replication: primary and secondary: full replication, incremental replication
- DNS notification: promotion (primary→secondary), security mechanism (notification)
16. The DNS domain name space is a hierarchical domain name organized in a tree structure; the secondary domain name server regularly obtains update data from the primary domain name server; the forwarding domain name server is responsible for all non- Query of local domain names
17. Use of DNSdistributedTo handle the conversion of multiple hosts and IP addresses in the network
18. Linux DNS server BIND: - /etc/named.conf main configuration file
- /var/named/wl.com.bd forward zone file (name => address)
- /var/named/192.168.100.bd reverse zone file (address => name)
- /etc/resolve.conf client configuration file
(2) Network management and SNMP
1. Five management functions in network management:
- ①countFee management: calculate and charge users for using network services
- ②installFull management: Provide confidentiality, authentication and integrity of information
- ③sexPerformance management: performance testing, performance analysis, performance management
- ④matchConfiguration management: monitor and control the status and configuration of the network
- ⑤soFault management: find and correct network faults, maintain network
- normal operation. Including alarm, detection, positioning, testing, recovery, and log recording, etc.
2. According to different functions of network management software, it is subdivided into: - Network Fault Management Software
- Network Configuration Management Software
- Network Performance Management Software
- Network Service/Security Management Software
- Network billing management software
3.SNMP:Simple Network Management Protocol:application layer protocol,useUDP, will not increase the network burden, and UDP realizes high network management efficiency.UDP161 (proxy), UDP162 (management station)
4. The use of UD to realize network management will not increase the network load too much.
5. SNMPv1: Four kinds of messages ①GetRequest, ②GetNextRequest, ③SetRequest, ④Trap, ⑤GetResponse. Among them, ④ is used forEvent report ⑤ is used for agent stations. Group clear text authentication
6. The shortcomings of SNMPv1: it is not suitable for the management of real large-scale networks; it is not suitable for obtaining a large amount of data; the trap is unresponsive, so it may not be transmitted; the authentication is too simple; it does not support the communication between the management workstation and the management workstation. Communication7
, SNMPv2: Also known as SNMPv2c,Supports both centralized and distributed management: Enhancement and improvement in 3 aspects: ①manageExpansion of the information structure. ②Communication capability between management stations。③new agreementoperate.Get BulkRequest block operates a large number of data, InformRequestCommunication request (enhanced function)
8. SNMPv3: Unify management and agents as entities(including engine and application), and provide authentication and encryption. Based on the user's security model, security threats are divided into primary and secondary.View-based access control model, dividing security levels。(Enhanced security),Added authentication and encryption
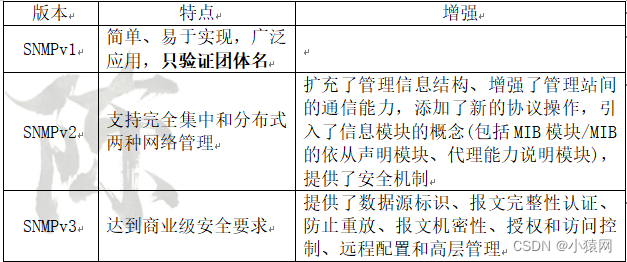
9. In the SNMP protocol, the agent receives a message from the management stationGETAfter request, ifNo value for this instance could be provided, it willreturn the value of the next instance
10. The main difference between RMON and SNMP is:RMONprovidedentire subnetmanagement information, andSNMPThe MIB contains onlylocal device11. The
message digest algorithm generates a message digest to prevent the sent message from being tampered with.
12. In the SNMP protocol, when the agent receives a GET request, if there is a value that cannot be provided or cannot be provided, it will return Shouldthe next value of the instance
13. The commands of the SNMP message from the agent to the management station are: trap, Get-Response; the SNMP messages from the management station to the agent include Get-Request, Get-Next-Request, and Set-Request
(3) Application layer protocol DHCP
1. DHCP protocol:Dynamic Host Configuration Protocol,Can automatically assign an IP address to the host in the LAN, if there is no response, the DHCP client will broadcast a total of4 timesRequest
2. Benefits of DHCP: ① Administrators can quickly verify IP addresses and other configuration parameters without having to check each host. ②DHCP will not lease the same IP address to two hosts from a range at the same time. ③Several options can be set for each DHCP range (or all ranges) (such as default gateway, DNS and WINS server addresses)
3. Working principle and process of DHCP protocol:
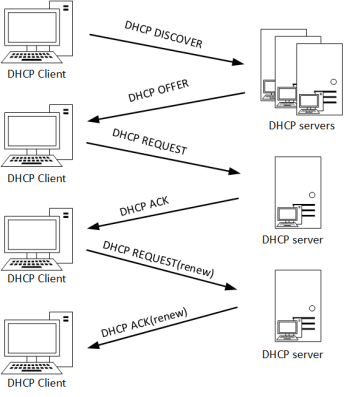
(1) When the DHCP client starts for the first time, the DHCP server send aDhcpDiscoverdata pack(broadcast)
(2) The DHCP server receives the Dhcpdiscover packet and provides (dhcpOffer (temporarily unassigned))
(3) The DHCP server sends an acknowledgment to the client ==(dhcpAck) (the default is 8 days) ==
(4) When the lease periodhalfway through(50% is 4 days to send Dhcprequest to the server, if the server agrees, it will send DHCPACK, if it does not agree, it will send DhcpNack),The client will renew its lease with the DHCP server that set its TCP/IP configuration.Pass87.5%hourcan'twith the original DHCP serverStop using this IP on contact
When the lease expires, the DHCP client sends a Dhcprequest to the server to re-lease the IP
4. When the DHCP server rejects the client's IP address request, it sends DhcpNack, and the client refuses to send DhcpDecline
5. DHCP scope:
- Scope: General and other tabs
- Scope options: configuration options (DNS, gateway, etc.)
6. ==Address pool: Create a new exclusion range (not included in distribution)
7. Reserve: Create a new reservation (distribute but will bind)
8. Filter: Specify accepted DHCP
9. == The gateway and DNS on the server are all empty and do not need to be set.
10. Lniux DHCP server configuration - DHCP serviceMain configuration file & path: /etc/dhcpd.conf
- The corresponding configuration file name for a Linux server isdhcpd.conf, the default directory of the file is ==/etc==
- ipconfig /all Obtain IP address automatically
- ipconfig /release release IP address
- ipconfig /renew Get new IP address again
11. The information that can be dynamically configured by DHCP protocol is: IP address, subnet mask, gateway address (local router address), DNS server address
(4) Others (HTTP/FTP/SMTP/telnet, etc.)
1. SMTP (Simple Mail Transfer Protocol): SMTP is currentlyThe de facto standard for transmitting E-Mail on the Internet, is a relatively simpletext agreement. The SMTP protocol belongs to the TCP/IP protocol family. It helps each computer find its next destination when sending or relaying a letter.
2. Email protocol:SMTP Simple Mail Transfer Protocol, responsible for sending mail touploadto the server, usingTCP port 25, C/S work.Send only ASCII text
3. Post Office Protocol (POP) is an e-mail protocol suitable for offline mode of C/S structure. It is a member of the TCP/IP protocol family and has now reached POP3. 4. E-mail
protocol:POP3 Post Office Protocol, responsible for sending mail todownloadto the client, usingTCP port 110,C/S work。After the user reads the mail from the server, the server deletes the mail
5. The Multipurpose Internet Mail Extensions (MIME) protocol defines the format of the message, attachment and other content of the transmission content, solves the difficulty of transmitting various types of information, and specifies the standard for the transmission of non-text email attachments through the SMTP protocol. MIME messages include text documents, images, sounds, videos and other special application data
6. E-mail protocol:S/MIME Multipurpose Internet Mail Extensions, responsible for securing multimedia emailsuploadto the server,Contains text, images, audio, video, and other application-specific data, and MIME cannot provide application-level security
7、互联网消息访问协议(IMAP)提供了有选择地从邮件服务器接收邮件的功能、基于服务器的信息处理功能和共享信箱功能。IMAP是更高级的用于接收消息的协议。目前版本为4,称为IMAP4。
8、电子邮件协议:IMAP4互联网消息访问协议,提供摘要浏览,选择下载。采用TCP的143端口,C/S工作。用户从服务器读取邮件后,服务器仍会保存该邮件,可以反馈服务器实现同步
9、HTTP是一个应用层协议,由请求和响应构成,是一个标准的客户端服务器模型。HTTP是一个无状态的协议。
10、HTTP协议特点:支持C/S模式;简单快速(由于http协议简单,使用http服务的程序规模小,因而通信速度很快);灵活(HTTP协议允许传输任意类型的数据对象);是无状态协议(指协议对于事务处理没有记忆能力)
11、超文本传输协议:HTTP,万维网WWW(Web)服务器提供全球的、分布的、动态的、多平台的、交互的、多媒体信息。TCP的80端口,B/S工作。统一资源定位器URL
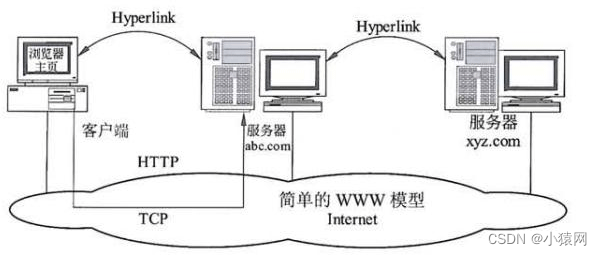
12、FTP是Internet传统的的服务之一,是用于从一台主机到另一台主机传输文件的协议
文件传输协议:FTP,负责文件通过服务器上下传送。采用TCP的两条连接:数据连接20端口,控制连接21端口,C/S工作。合法访问和匿名访问(anonymous)。

13、文件传输协议:FTP,有主动模式(PORT/Standard)和被动模式(PASV/Passive)。区别是:服务器主动20传数据,被动随机端口(主动爱你,被动随机)
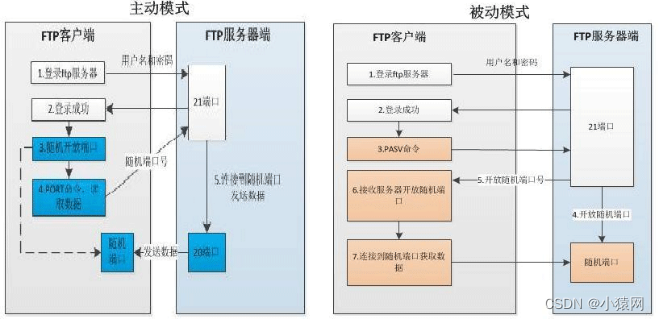
14、远程登录协议:Telnet,TCP/IP终端仿真协议,登录到远程主机上操作,网络虚拟终端NVT支持异构主机,采用TCP的23端口,C/S工作,采用NVT格式实现客户端和服务器的数据传输==
(五)网络管理工具和命令
1. Tracert is route tracking, which is used to determine the IP datagram access target; arp is used to display and modify the value in the arp cache; ipconfig displays the current TCP/IP configuration setting value; netstat can display the routing table 2, ipconfig
/ all: Display the detailed information of the host TCP/IP configuration; /release: The DHCP client manually releases the IP address; /renew: The DHCP client manually refreshes the new request to the server; /flushdns: clears the contents of the local DNS cache; /displaydns: Display Local DNS content
3. Ping, using ICMP messages to test network connectivity, packet loss, name resolution, etc. ping -a resolves the domain name; ping -f does not split the segment; ping -l specifies the packet size; ping -n specifies the number of times the datagram is echoed; ping -r record route; ping -t connectivity (continuous ping), until terminated
4. The netstat command is used to display the TCP connection, the syntax is as follows netstat [-a] [-e] [-n] [-o] [-p Protocol] [-r] [-s] [Interval]
- -a:Displays all active TCP connections, and TCP and UDP ports that are listening
- -e:show ethernet statistics
- -n:Displays active TCP connections, with addresses and port numbers represented numerically
- -o:Displays active TCP connections and the process ID corresponding to each connection. The application corresponding to the process ID can be found in the Windows Task Manager. This parameter can be used in conjunction with -a, -n and -p
- -p Protocol:Specify the protocol to display with the identifier Protocol, which can be TCP, UDP, TCPv6, or UDPv6. If used in conjunction with the parameter -s, the statistics of the protocols TCP, UDP, ICMP, IP, TCPv6, UDPv6, ICMPv6 or IPv6 can be displayed
- -s:Show statistics for each protocol. by default,Statistics TCP, UDP, ICMP and IPPackets sent and received by the protocol, packets with errors, number of times the connection succeeded or failed, etc. If used in conjunction with the -p parameter, you can specify the protocol to display statistics
- -r:Display the contents of the IP routing table, its roleequivalencein route print commandroute print
- Interval:Indicates the time interval for redisplaying non-messages, and type Ctrl+C to stop displaying.If this parameter is not used, it will only be displayed once
5、arp,Used to display and modify entries in the ARP cache。The -s parameter can bind IP and MAC to prevent ARP virus, such as arp -s 192.168.1.1 AA-00-4F-2A-9C. butwill be lost after reboot,If writing to the registry is a permanent solution - -a: Display the current ARP cache table for all interfaces
- -d: deleteARP cache entries
- -s: Bind ARP entries, such as IP and MAC binding
6. Proxy ARP means that the switch closest to the source host pretends to be the target host to answer the ARP request of the source host.
7. Other commands: - pathping: combine ping and tracert,Detection path, delay, packet loss rate
- nbtstat: Used to display the NetBIOS name cache
- route: Display the modified local IP routing table. add to add, delete to delete, change to modify, print to display the routing table (same as netstat -r)
- netsh: A command-line script that modifies a computer's network configuration
- net: Manage network services
- nslookup. used toTest DNS server domain name resolutionof. interactive and non-interactive
- tracerouteis the traceroute command forgroupEach router passed on the path to the destination
- netstatavailable for displayIP、TCP、UDP、ICMPStatistical data of other agreements;
- snifferwere ableUse network interface in miscellaneous mode, so thatIntercept packets in transit on the network
- winipcfgin windowsDisplay information about network adapters and hosts;
- tracertCanDiscover the router and arrival time that the data packet passes through to reach the target host. Usually used with -d
- Tracert, Netstat and Route printare availableGateway IPAddress information
- Nslookup is used to check the address of the server providing the domain name; ping plus the domain name address can test whether the domain name is successful or not; tracert can also be used for DNS fault diagnosis; arp is an address protocol for mapping IP addresses and MACs
4. Routing Protocol
(1) Internal Routing Protocol RIP
1. Network layer routing protocol: select forwarding data path
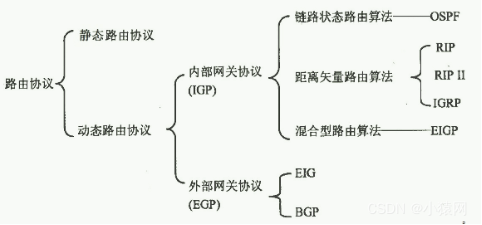
2. Routing information protocolRIP: distance vector algorithm, the earliest dynamic routing used in the TCP/IP network, calculate the number of hops, the maximum is 15 hops, and 16 hops are unreachable.30s update, 180s does not exist, 240s deletes "Mantra 168". Support equal-cost load balancing and link redundancy. useUDPThe 520 port.
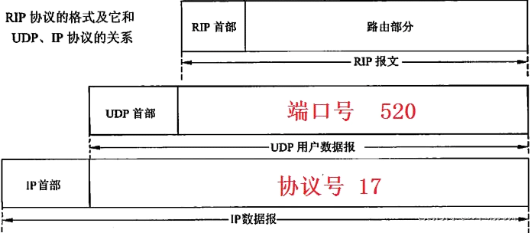
3. Two versions: RIPV1 and RIPV2 are different, suitable for small networks.

4. Routing information routing protocolRIP:Ways to prevent loops
- Maximum hop count: When a routing entry is sent out, it will automatically add 1 hop, and the maximum hop count is 16 hops, which means unreachable
- Split horizon: a routing message is not sent to the source of the message(Do not send the routing information obtained from a neighbor node to the neighbor node)
- Split horizon for reverse poisoning: Set the routing information learned from a neighbor to 16 hops and send it to that neighbor. safer
- Suppressing timers and triggering updatesAlso prevents loops
- The router of the distance vector routing protocol updates its routing table according to the information sent by the neighbors
- In the distance vector routing protocol, the routing information received by each router comes from its neighbor routers
5. Compared with RIPv2, the IGRP protocol adds some new features: - The router no longer takes the number of hops as the only factor, but also includes parameters such as bandwidth and delay
- Not only supports equal-cost path load balancing, but also supports load balancing of unequal-cost paths
- The maximum number of hops has been expanded from 15 to 55 to support larger networks
(2) Internal routing protocol OSPF
1. Open shortest path first protocolOSPF: link state algorithm, the routers are updated and established through the network interface state LSAlink state database (neighbor table),Including: connectivity, distance, delay, bandwidth and other states, Dijkstra'sSPF algorithm (calculate the shortest path). Link state algorithms are used to compute routing tables.Trigger updates, hierarchical routing. support for large networks,areaIDvalue ofThe range is 1~65535
2. The characteristics of the link state protocol:
- Provides a topology view of the entire network
- Calculate the shortest path to each target
- Event-triggered route update function
- In order to reduce the amount of flooded link state information, OSPF can divide the autonomous system into smaller areas.
3. Simplification principle: sendingHellomessageEstablishadjacency (neighbor table)-formLink State Database (Topology Table)—SPF(link state) algorithm to form a computer routing table
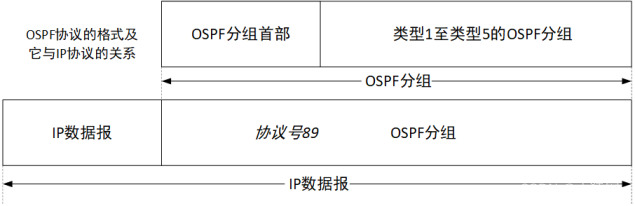
4、supportVariable length subnet mask (VLSM) and route aggregation function
5, OSPF should select a specifiedrouter(DR), the function of the designated router is to send link state announcements
6. OSPF adoptstrigger update,and30 minute cycle update。Support for discontiguous subnets and CIDR
7. A single OSPF network only has area 0
8. OSPF area type: backbone area (32 bits),Area 0.0.0.0orArea 0 to represent

9. Open Shortest Path First Protocol OSPF: According to the physical connection and topology, it is divided into the following network types:
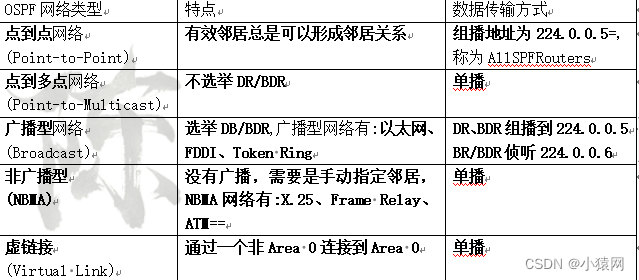
10. OSPF router classification: according to the functions between different areas: BR (backbone), IR, ABR (area border router) , ASBR (Autonomous System Boundary Router)

11, five types of OSPFmessage type:Hello message defaults to 10supdate once,40s failure,Destination address is 224.0.0.5 all routers. fordiscover build neighbors、It is also used to select the designated router DR and backup designated router BDR in the area(DR/BDR multicast address is 224.0.0.6)
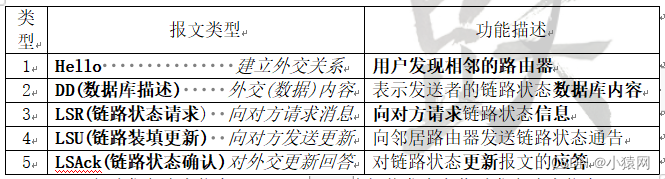
12. RIP regularly releases routing information, while OSPF releases routing information when the network topology changes; RIP routing information is sent to neighbors, while OSPF routing information is sent to the entire network router; both are internal routing protocols 13, DR in the OSPF
protocol The scope of action is a network segment
14. The OSPF protocol is relative toRIP1The advantages are: no limit on the number of hops, support for variable-length subnet masks (VLSM), support for large-scale networks, and fast convergence (if it is the same asRIP2In comparison, RIP2 supports variable-length subnet mask (VLSM))
15. In an area OSPF has a 32-bit area identifier; routers in an area do not know the network topology of other areas
16. Links in OSPF State "metrics" mainly refer to cost, distance, delay, bandwidth (no convergence time)
17. In OSPF, the link state of a router only involves the connectivity state with adjacent routers.
18. In OSPF, between ABR and ASBR
19. For a stable ospf network (single area), the Router ID of the router must be specified, and the link state database of all routers is the same
(3) Internal routing protocol IS-IS
1、IS-IS:intermediate system - intermediate system, the router is called the Intermediate System IS. Similar to the OSPF protocol, it belongs tointerior gateway routingprotocol, which is a link-state protocol.
2. Net-Entity:network entity. A router running IS-IS must be configured with a network entity address. The format is: SEL Service Access Point
3, IS-ISA two-level hierarchy within the routing domain。Backbone area and non-backbone area. It also defines three roles of routers: intra-area Level-1, inter-area Level-2, and both belonging to Level-1-2. The default router interface is Level-1-2
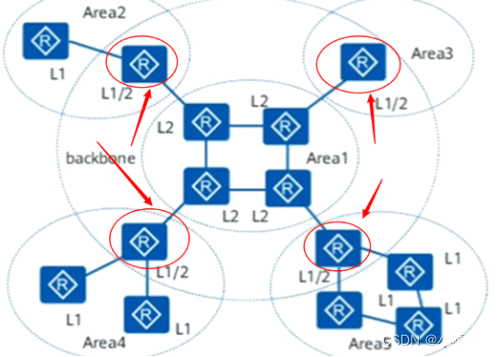
4. The concept of ISIS router:
- L2 routers, routers in the backbone area
- L1 routers, routers in the non-backbone area
- L1/2 routers are actually OSPFarea borderRouter
5, ISIS router function: - Level-2 LSDB is used for inter-area routing
- Level-1 LSDB is used for intra-area routing
- Level-1-2 routers maintain two LSDBs
. 6. The IS-IS routing protocol divides the autonomous system into backbone areas and non-backbone areas.
7. In the IS-IS routing protocol, Level-2 routers can communicate with Level-2 or Level-2 routers in different areas -2 The router forms a neighbor relationship
8. In OSPF, the backbone network area is fixed as Area0, and the non-backbone network area should be connected to the backbone network area (if there is no physical connection, a virtual link Vlink should be performed). But in ISIS - There can be multiple backbone areas, and the area ID is not fixed
- The non-backbone area must be physically connected to the backbone area (via L1/L2 routers)
- Non-backbone areas cannot be connected directly
(4) External routing protocol BGP
1、Border Gateway Protocol BGP: is the Exterior Gateway Protocol, the main function isControl Routing Policy,Between different autonomous systems AS,Find a better routing policy. passTCP port 179 establishes a connection。Support subnet VLSM and CIDR, is a path vector protocol. At present, the latest BGP4, while BGP4+ supports IPV6

2, four types of BGP packets:Open establishes a neighbor, and Keepalive periodically detects the survival of the neighbor. The BGP protocol uses keep-alive messages to periodically confirm the connectivity of neighboring stations. Each autonomous system must select at least one router as the "BGP spokesperson" of the autonomous system.Incremental update, supports authentication.Reliable transmission, loop prevention, and inter-area routing loop prevention. Autonomous communication, strategic routing. Supports classless and aggregation.
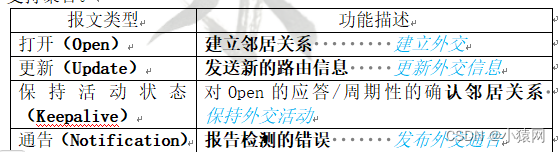
3. The meanings of several states of BGP
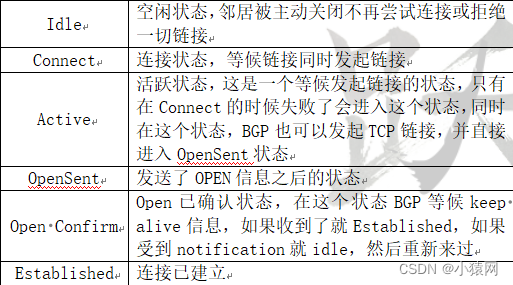
4. BGP uses keepalive to periodically send survival messages (60s) to maintain neighbor relationships
5. Compared with RIP, BGP4 has many advantages such as:
6.Neighborhood can be established across devices
7、Provides a wealth of routing attributes for routing
8、Can manage routers around the world
9. Features of BGP4:
- BGP4gateway to peerThe entity (Peer) publishes a list of ASs that can be reached
- BGP4 gatewayhop-by-hop routing(hop-by-hop) modePublish routing information
- BGP4 canForm a super network through route aggregation function(Supemet)
10、BGP将TCP用作其传输协议,运行在TCP的179端口上(目的端口)
五、路由器技术
(一)路由技术NAT
1、路由器技术NAT:网络地址翻译,解决IP短缺,路由器内部和外部地址进行转换。
- 静态地址翻译转换:静态NAT(一对一)
- 动态地址翻译转换:动态NAT(多对少)
- 网络地址翻译端口转换(地址伪装):NAPT(多对一)
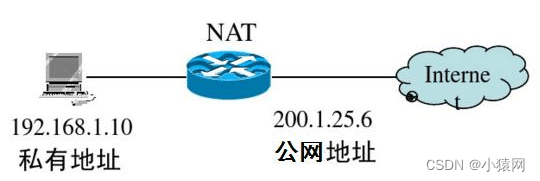
2、路由器技术NAT:静态NAT,内外一对一转换,用于web服务器,ftp服务器等固定IP的主机服务器
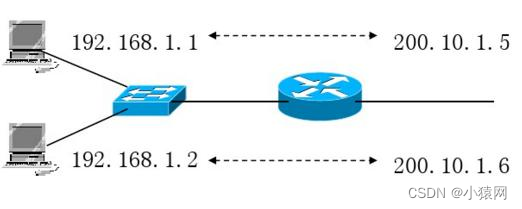
3、路由器技术NAT:动态NAT,内外多对少转换,用于内部局域网较多用户访问外部网络。外部需要地址池(pool)
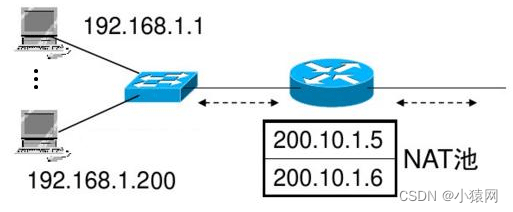
4、路由器技术NAT:网络地址端口转换:NAPT(PAT)(多对一)内外多对一转换,使用外部一个IP,多个端口号对应内部IP。也称为IP伪装,可以隐藏内部主机。
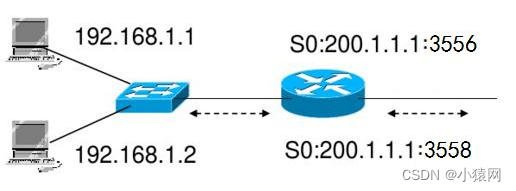
5、地址伪装是指,把多个内部地址翻译成一个外部地址和多个端口号
6、网络地址和端口翻译(NATP)就是用于把内部的所有地址映射到一个外部地址,好处就是隐藏了内部网络的IP地址
7、地址映射方式有:全相联方式、直接方式和组相联方式
8、做NAT一般的原则:对外服务器作静态NAT;个人电脑作动态NAT或PAT;内部服务器不作NAT
(二)路由协议MPLS
1、路由器技术MPLS:多协议标签交换,属于2.5层,MPLS包头的位置应该插入在以太帧头与IP头之间一般认为是第三层交换,硬件交换、速度快,叫一次路由,多次交换。==用标签交换代替复杂的路由运算
2、==路由器技术:MPLS基本原理。标记边缘路由器LER,标记交换路由器LSR
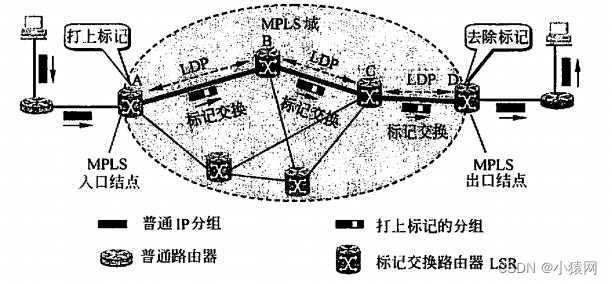
3、路由器技术:MPLS转发等价类(FEC),把等价的通信流汇聚转发. Markup is local. Provide QoS, granular control, load balancing, etc.
4. The router can aggregate multiple IP flows together according to the forwarding target to form a forwarding equivalence class.
5. MPLS technology is mainly proposed to improve the forwarding rate of the router. Its core idea is Use label switching to replace complex routing calculations and routing switching; the core of this technology is to putIP datagrams are encapsulated in MPLS packets
6. MPLS VPN consists of CE routers, PE routers, and P routers.Prouter isRouters in the MPLS core network,Responsiblehigh speed forwarding;PEThe router is on the MPLS core networkedgerouter, responsible forGeneration and Popping of MPLS Labels for Carrying Datagrams, will also initiate the establishment of theThe action of exchanging labels;CEThe router is directly connected to the carrierclient router
7. The router aggregates multiple IP flows together according to the forwarding target to form a forwarding equivalence class
(3) Routing protocol IP QoS
1. QoS (Quality of Service) is to provide better service capabilities for designated network communications, and is a technology used to solve problems such as network delay and congestion.
2. Under normal circumstances, if the network is only used for specific application systems without time limit, QoS is not required, such as Web applications, or E-mail, etc. But for critical applications and multimedia applications,When the network is overloaded or congested,QoS can ensure that important traffic will not be affected by delay or discard, and ensure efficient operation of the network.
3. When the network is congested, all data streams may be discarded; in order to meet the user's requirements for different application quality of service, it is necessary for the network to allocate and schedule resources according to the user's requirements.Provide different quality of service for different data streams:rightStrong real-time and important data packets are processed first; For ordinary data packets that are not real-time, provide lower processing priority for network congestion or even discarding, so that network bandwidth can be effectively allocated and network resources can be used more reasonably.
4. Router technologyQoS (Network Layer): Network Quality of Service. connect the networkThe data flow is divided into different classes,provide different services. haveIntegration Services(IntServ) anddifferentiated services(DiffServ)模型两种标准

5、路由器技术QoS:集成服务(IntServ)分成三种:保证质量的服务(有关协议是RSVP特点是由接收方向路由器预约资源,从源到目标单向预约)、控制负载的服务、尽力而为的服务(目前因特网提供的服务)
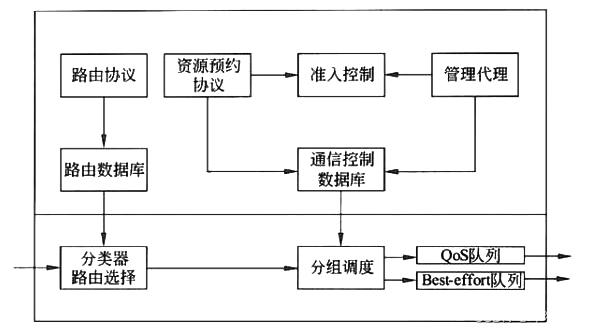
6、IntServ模型的优点:
- 提供绝对保证的QoS,因为RSVP在从源端到目地端的每个路由器上运行,能监视每个数据流,以防资源浪费。
- 在源端与目的地之间,RSVP可以用现有的路由协议决定数据流的通路,RSVP使用IP包承载,通过周期性重传路径和RESV消息,能对网络拓扑的变化做出反应。
- 可支持多播流,RSVP协议能让路径消息识别多播流的所有端点,并将路径消息发送给它们,还能把来自每个接收端的RESV消息合并到一个网络请求点上,让一个多播流能在分开的连接上发送。
7、IntServ模型的缺点: - 状态信息的数量与流的数目成正比。因此在大型网络中,按每个流进行资源预留会产生很大的开销。
- IntServ体系结构复杂。若要得到有保证的服务,所有的路由器都必须装有RSVP、接纳控制、分类器和调度器。
- 综合服务IntServ所定义的服务质量等级数量太少,不够灵活。
8、QoS是网络的一种安全机制,主要用来解决网络延迟和阻塞等问题.它主要有三种工作模式,分别为区分服务模型、集成服务模型及尽力而为服务模型。其中使用比较普遍的方式是尽力而为服务模型
9、路由器技术QoS:区分服务(DiffServ)不再使用资源预约,而是区分不同的业务流。分为三种:尽力服务BE(000000)、优质服务AF、加速服务EF(101110)
10、区分服务(DiffServ):区分服务代码点DSCP,利用IP包头的服务类型字段ToS. Hop-by-hop behavior PHB: The forwarding mode of hop-by-hop, each PHB corresponds to a forwarding mode
11. Advantages of DiffServ: - The main advantage of DiffServ is that it weakens the dependence on signaling and does not need to reserve a "soft state" for each service flow on each router like IntServ, avoidingIt avoids the transmission of large resource reservation information and has better scalability。
- DiffServDoes not provide end-to-end QoS guarantee。
- DiffServReduce the consistency of QoS to each area, thus reducing the complexity of this model implementation.
12. Disadvantages of DiffServ: - DiffServ does not provide end-to-end QoS guarantees for the entire network. The QoS it provides is only a relative QoS, which is the QoS relationship between different levels of service flows. The forwarding method still uses traditional IP network hop-by-hop Transmission mode
13. Qos is manifested in delay, jitter, throughput and packet loss rate. The technologies used include RSVP, DiffServ, MPLS
14. The integrated service model (IntServ) can be calculated for a single service (such as a telephone call) QoS guarantee; the differentiated service model is not for a single business, but for a class of business for QoS guarantee
15. During data transmission, the scheduled routing information must be refreshed regularly
Chapter 4 Computer Network Planning and Design
1. A computer network consists of a variety of basic elements. Common network basic elements include computer platforms, application software, physical equipment and topology, network software and utility software, interconnection equipment and wide area network connections, etc. 2. Network interconnection equipment:
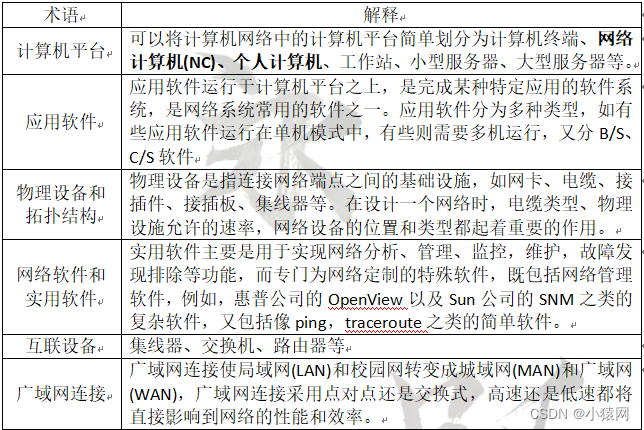
3
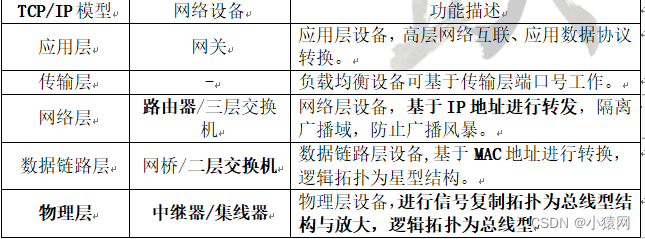
. A hub is a collision domain, an interface of a switch is a collision domain, and an interface of a router is a broadcast domain
4. When designing a network, the consideration of network performance parameters is one of the key contents of the design work. What needs to be considered Network performance parameters includeResponse time, throughput, latency, bandwidth, capacitywait.
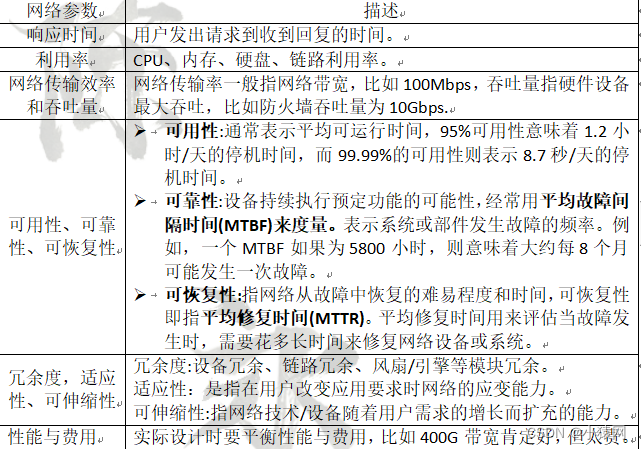
5. The factors that need to be considered in the security planning of the internal server group of the enterprise are: when any enterprise is doing security planning,First, divide the information security level according to the needs,Then depending on the security level,considerDMZ area security protection, physical security of the computer room, system security of the host computer, data backup mechanism, security management system, etc.。
2. Network analysis and design process
(1) Network norms
1. Design workCommon problems arising from non-compliance, these problems will lead to a decrease in user satisfaction with web applications.
1) The implementation result deviates from the network requirements
2) The requirements change
3) The construction period is delayed or the cost is overrun
4) The network implementation is inconsistent with the design
2. For large and complex network engineering projects, it is necessaryStandardization and highly accurate documentation
3. The tasks in the outline design stage include:Function design, call relationship design, input/output designetc. The tasks in the detailed design stage areAlgorithm Design, Data Structure。
(2) Principles of network design and analysis
1. When making network technology selection, consider:Communication bandwidth, technology maturity, connection service type, scalability, high investment-output ratio and other factors;
2. For large-scale network projects, the project itself cannot become a test field for new technologies.Try to use more mature technologies with more cases.
3. [Example: It is known that the network department has allocated an address segment 59.74.116.0/24 to the student apartment network, please give the student apartment network address planning and design scheme:59.74.116.0/24 can be divided into 64 subnets, and each subnet corresponds to a VLAN connection of a student apartment, which is only used for access. Users in the student apartment area can access the network through the Layer 3 device in this vlan segment as NAT.]
4. [Example: As shown in the figure below, and combined with technical factors such as dial-up Internet access, network security control, and in-band management to manage the network, describe the performance and configuration description of BRAS and OLT equipment:BRAS (Broadband Remote Access Server) is a network device configured with PPPOE to mainly implement access, authentication, billing, and management of broadband network users, which is the basis for the operation and management of broadband networks. OLT (Optical Line Terminal) is used to connect the terminal equipment of the optical fiber line, one end is connected to the user, and the other end is connected to the BRAS】
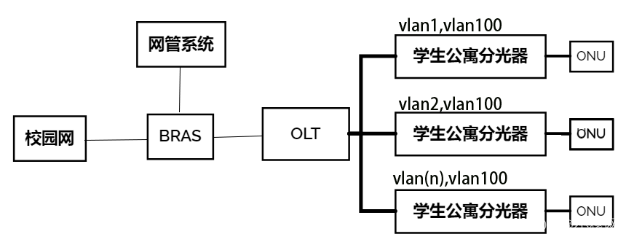
5、【例:如上图中BRAS设备用路由器(Router)替换,请分析在学生公寓网络规划上可能有哪些变化:使用router代替BRAS之后,通常需要根据接入网络的规模来确定其变化,对于较大规模的网络,内部网络会采用路由器或者多层交换机进行网络的划分,因此router只要考虑路由优化与快速检测等问题即可。而规模较小的接入网,可能是普通的2层网络,需要router提供较灵活的接入方式。如vlan接入】
(三)网络的生命周期
1、四阶段周期的长处在于工作成本较低、灵活性高,适用于网络规模较小、需求较为明确、网络结构简单的网络工程。四阶段为:构思与规划阶段->分析与设计阶段->实施与构建阶段->运行与维护阶段
2、五阶段模型:也叫瀑布模型
- 优势:所有的计划在较早的阶段完成,系统的负责人对系统的具体情况以及工作进度都非常清楚,更容易协调工作。
- 缺点:比较死板,不灵活。如果用户的需求经常会发生变化,这使得已开发的部分需要经常修改,从而影响工作进程,所以基于这种流程完成网络设计时,用户的需求确认工作非常重要。
- 五阶段周期存在较为严格的需求和通信分析规范,设计过程中充分考虑了网络的逻辑特性和物理特性,较为严谨,适用于网络规模较大,需求较为明确,在一次迭代过程中需求变更较小的网络工程。
- 阶段分为:需求分析->通信规范->逻辑网络设计->物理网络设计->实施阶段
3、六阶段模型: - 六阶段周期偏重于网络的测试和优化,侧重于网络需求的不断变更,由于其严格的逻辑设计和物理设计规范,使得该种模式适合于大型网络的建设工作。
- 六阶段(循环的):需求分析->逻辑设计->物理设计->设计优化->实施与测试->检测及性能优化->需求分析…
4、网络生命周期的迭代模型的核心思想中,成本评价机制决定是否结束网络系统的生命周期。
(四)网络开发过程
1. Decomposing large-scale problems into multiple small and solvable simple problems is a common method for solving complex problems. According to the five-stage iterative cycle model, the network development process can be divided into five stages. These five stages are:
- demand analysis.
- Existing network system analysis, that is, communication specification analysis.
- Determine the logical structure of the network, that is, the logical network design.
- Determine the physical structure of the network, that is, the physical network design.
- Installation and maintenance.
2. Constraints of network design - Policy constraints: For example, prisons and public security industry intranets cannot use WIFI technology, so it needs to be considered in the design.
- Budget constraints: As the name suggests, no money to design NB is nonsense.
- Time constraints: Especially for new projects with strict time requirements, such as new campuses, occupancy is required in September.
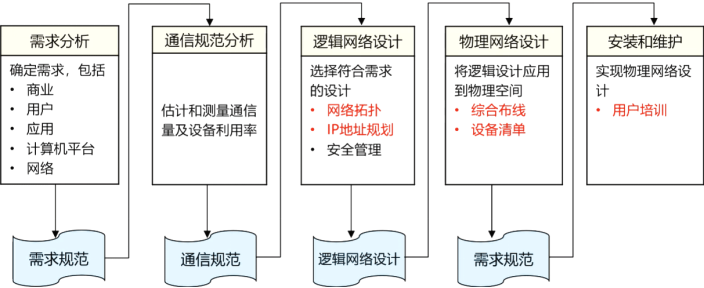
Application target inspection: that is, to conduct periodic reports with customers , prevent deviations, and finally rework.- Different groups have different needs and agreements, and conflicts of constraint conditions often occur. Solution ideas: a. Coordinated by the user's information management department; b. Prioritize conflicting constraints and give priority to the highest Restrictions
3. Analysis of Network Requirements
1. Necessity of network requirements
- Requirements analysis is a method used to obtain network system requirements and business requirements. The process isFundamentals of Web Development, is also a critical stage in the development process.
- During the requirement analysis phase, the userThe clearer and more detailed the definition of requirements, then the implementation period requiresless likely to change, and users of the post-construction networkhigher satisfaction.
2. Requirements analysis process: Aspects to consider:Business requirements, user requirements, application requirements, computer platform requirements, network requirements.
(1) Establish business requirements: - Business requirements investigation is the key to understanding the nature of the business, and should try toEnsure that the designed network can meet the needs of the business。
- In order for network engineers to provide network services collectively, there is a division of functions in the collective, and there are also different business requirements. Generally, users only have a very clear analysis of their own business requirements. The information is as follows:
- a. Determine the relevant personnel such as obtaining the organizational chart
- b. Determine key time points: For example, the time limit of the project is completeddeadline, for large-scale projects, a strict project implementation plan must be formulated to determine the stages andcritical time, and the products of these time points are also important milestones.
- c. Determine the scale of network investment: For the design and implementation of the entire network, cost is a major consideration, and the investment scale will directly affect the network engineeringDesign ideas, technical routes, equipment purchases, service levels。
- d. Identify business activities: Before designing a network project, the requirements of the network should be clarified through the understanding of business activities. Under normal circumstances, network engineering does not need to have a very detailed understanding of business activities, mainly through the analysis of business types to form various business requirements for the network, mainly includingMaximum number of users, number of concurrent users, peak bandwidth, normal bandwidth, etc.。
- e. Forecast growth rate: Forecasting the growth rate is another type of conventional requirement. Through the analysis of the network development trend, the scalability requirements of the network are clarified, such asbandwidth, storage spacewait.
- f. Determine network reliability and availability: The availability and reliability requirements of the network are very important, and even the parameters of these indicators may affect the design ideas and technical routes of the network.
- g. Determine the connectivity of the Web site and the Internet: The Web site can be built by itself or provided by a network service provider. No matter which method is used, a collective Web site or internal network always reflects its own business needs when designing. Only by understanding an organization's Internet business strategy can it be possible to design a network with reliability, availability, and security.
- h. Determine the security of the network: Determining the security requirements of the network and constructing a suitable security system are the guarantees of the network design work.
- i. Determine remote access: Remote access refers to accessing the internal network and enterprise network from the Internet or external network. When the network user is not inside the enterprise or organization network, he can access the internal network from a remote network by means of encryption technology, VPN and other technologies. Through remote access, the requirement of being able to work at any time and place can be realized, which also requires the configuration of corresponding remote access security technical requirements
(2) Output a list of business requirements such as: - a. Determine the main relevant personnel: sources of information, list of information management personnel, contact information of relevant personnel
- b. Determine the key time points: the start time of the project, the time schedule of each stage
- c. Determination of project investment: investment scale estimation, budget cost estimation
(3) User needs: related methods:Observation and questionnaires, intensive interviews, interviews with key persons.
(4) Application requirements: There are four common classifications: - Classified by function: document management, database, word processing, etc.;
- Classified by sharing: stand-alone application, multi-user software, network software;
- Classification by response: real-time applications and non-real-time applications;
- Classification by network model: applications can be divided into stand-alone software, peer-to-peer network software, C/S software, B/S software, and distributed software according to the network processing model.
(5) Computer platform requirements: - Gathering computer platform requirements is an indispensable step in the network analysis and design process. The computer platforms that need to be investigated are mainly divided into five categories:PC, Workstation, Minicomputer, Midrange, Mainframe。
- Determine required equipment:CPU, memory, hard disk space size, graphics card, RAID card, etc..
(6) Network requirements: the main requirements include the following - LAN functions: VLAN division, traffic analysis;
- Network topology: star, ring, bus or others;
- Performance: Gigabit, 10 Gigabit or 40G links for performance capacity, 100T switch capacity for core equipment or 200T, response time, delay, disaster recovery backup, etc.
- Network management: which devices need to be managed, with what protocols, and to what extent?
- Network security: will be introduced in detail in the following chapters;
- Choice of MAN/WAN: How to access MAN and WAN.
- networkdemand outputThe tables includeLAN function, network topology, network management, network security, MAN/WAN selection, etc.. Since the network requirements involve a wide range of areas and complex content, and the network requirements of different network projects are quite different, the network requirements table does not need a strict format. Designers can design the network requirements table by themselves according to the above content.
3. Write requirements specification: - The requirements specification is the first important document that can be circulated formally in the network design process. Its purpose is to clearly summarize the collected demand information, which is also theThe first document to be formally reviewed by the user management。
- There are two requirements for the network requirements specification: First, regardless of the organizational form of the requirements specification, the network requirements specification should includeRequirements in five aspects: business, user, application, computer platform, and network;Secondly, in order to standardize the preparation of requirements specifications, in general, requirements specifications should include the following five parts: overview, overview of requirements analysis stages, summary of requirements data, list of requirements queued by priority, and part of application approval
4. Analysis of Communication Specifications
1. Analysis of communication norms: the analysis of communication norms is in the second stage.Network Communication Patterns and Traffic Flow,Discover the key technical points that may lead to the bottleneck of network operation, so as to avoid this situation in the design work.
2. Subparts of communication specification analysis: communication mode analysis, communication boundary analysis, communication flow (direction) analysis, traffic analysis, network benchmark analysis, writing communication specification 1) 4 communication modes
:
- Peer-to-peer network mode (P2P) (decentralized)
- C/S mode, B/S mode
- Distributed Computing Communication Patterns
- Distributed computing refers to the application of multiple computing nodes working together to complete a common task. It has great potential in solving distributed applications, improving performance and price ratio, and providing practicability, fault tolerance and scalability of shared resources.
2) Communication boundary - LAN communication boundary (conflict domain):A hub is in a collision domain, an interface on a switch is a collision domain.
3) Communication boundary - LAN communication boundary (broadcast domain):The nodes connected to all interfaces of the switch belong to a broadcast domain, and each interface of a router is a broadcast domain.
4) Communication traffic analysis - 80/20 rule: The 80/20 rule is a general rule widely used in traditional networks. In a network segment, 80% of the communication traffic flows in this network segment, and only 20% of the communication traffic visits other network segments, that is, 80% of the total traffic is considered to be the traffic inside the network segment, while20% is traffic outside the network segment。
- 20/80 rule: 20% of the total is traffic inside the network segment, and 80% is traffic to the outside of the network segment. The local area network formed by computer users in the community, the workgroup network used by large companies to realize remote collaborative work, etc. The characteristics of these networks are: the internal users of the network segment have less access to each other,Most of them access resources outside the network segment, you can use the 20/80 rule.
5) Steps of communication flow analysis: - ① Divide the network into easy-to-manage network segments (VLAN).
- ② Determine the communication flow of individual users and network segment applications.
- ③ Determine the traffic flow on the local and remote network segments.
- ④Repeat steps ①~③ for each network segment.
- ⑤ Analyze the communication flow of the WAN and network backbone based on the information of each network segment. 6
) Network benchmark analysis: In addition to collecting user information and calculating communication traffic, it can also be more accurate基于通信量的计算法,即基准法。工具:网络流量分析软件or网管软件。
3、编写通信规范说明书:通信规范说明书记录了网络当前的状态,包括网络的配置、网络互联设备水平以及共享资源的利用率。通信规范说明书由下面主要内容组成。 - 执行情况概述
- 分析阶段概述
- 分析数据总结
- 设计目标建议
- 申请批准部分
- 修改说明书
五、逻辑网络设计
1、网络结构设计:
1)层次结构主要定义了根据功能要求不同将局域网络划分层次构建的方式,从功能上定义为核心层、汇聚层、接入层。层次局域网-般通过与核心层设备互连的路由设备接入广域网络。
2)网络冗余设计:双链路、双设备、双电源等。
3)三层架构中:出口层(OR):广域网接入、出口策略、带宽控制;核心层(CO):高速转发、服务器接入;汇聚层(SS):流量汇聚、链路冗余、设备冗余、路由选择;接入层(AS):用户接入、接入安全、访问控制。
2、物理层技术选择(三阶段的,物理只是一个修饰词):
1)物理层介质:双绞线、光纤两种选择,光纤可选单模和多模,具体差别和差异见第二章。
2)网卡:百兆or千兆,电口or光口,目前主流是千兆电口。
3、局域网技术选择与应用
1)STP生成树
2)虚拟局域网VLAN实现VLAN间通信的两种方式,借助路由器或三层交换机
3)无线局域网
4)交换机设备应用:链路冗余:链路聚合;网关冗余:VRRP
5)多业务模块:常见的网络业务模块包括防火墙(firewall)、入侵者检测(IDS)、入侵者防御(IPS)、流量控制(FC)等,这些业务模块相对于独立的业务产品将提供更强的业务处理能力。
6)以太网供电(POE)技术:通过以太网线路为IP电话、WLAN接入点、网络摄像机等小型网络设备直接提供电源的技术。该技术可以避免大量的独立铺设电力线,以简化系统布线,降低网络基础设施的建设成本。
7)POE标准:802.AF;POE+标准:802.AT;POE++标准:802.BT;
8)为了提高服务器的性能和工作负载能力,企业通常会使用DNS服务器、网络地址转换等技术来实现多服务器负载均衡,特别是对外服务的Web网站,许多都是通过几台服务器来完成服务器访问的负载均衡。一般来说,实现服务器的冗余和负载均衡有多种方式。
9)服务器负载均衡实现方案:
- 专业负载均衡设备,实现用户或流量在几台服务器之间负载均衡;
- 网络地址转换,将一个公网IP映射为多个内部私网IP,即内部多台服务器;
- DNS服务器,直接将域名映射为多个IP地址从而实现负载均衡。
10)服务器双机热备: - 双机热备份高可用(HA)系统,又称高可用性集群,一般由两台服务器构成,通过对关键部件的冗余设计,可以保证系统硬件具有很高的可用性,对于一般非关键应用场合,其硬件系统的可用性可以达到99.99%。在正常工作时,两台服务器同时工作或一台工作另一台热备,通过以太网和RS232口互相进行监测,不断完成同步操作,数据保存在共享磁盘阵列中。
- 传统的高可用性集群的工作模式主要是单活(active/passive)、双活(active/active)。
- The high-availability cluster at the database application level is mainly realized by the application cluster software provided by the database management system software. Among the commonly used data management system products, SQL Server mainly adopts the single-active mode.Oracle mainly adopts active-active mode.
4. Advantages of POE: - Easy to manage: Centralized power supply, convenient backup
- Simple connection: the network terminal does not need an external power supply, only one network cable is required
- save costs: Save power wiring cost, provide simple and convenient power supply
- Unified Standards and Interfaces: Conforms to IEEE 802.3bt, IEEE 802.3af, IEEE 802.3at standards, and uses a globally unified power interface.
- Improve reliability: Combined with UPS uninterruptible power supply, it can provide redundant power supply for IP camera, video server and IP phone, etc., to prevent power failure.
5. High availability and high reliability
1)availability: usually means the average run time, isavailable time divided by overall time. 95% availability means 1.2 hours/day of downtime, while 99.99% availability means 8.7 seconds/day of downtime.
2)reliability: The likelihood that a device will continue to perform its intended function, as measured by the mean time between failures (MTBF). Indicates the frequency with which a system or component fails. For example, if an MTBF is 5800 hours, it means that a failure may occur approximately every 8 months, which also meansAverage time between failures。
3)Recoverability (business continuity):指网络从故障中恢复的难易程度和时间。可恢复性即指平均修复时间MTTR)。平均修复时间用来估算当故障发生时,需要花多长时间来修复网络设备或系统。
6、IP地址设计:
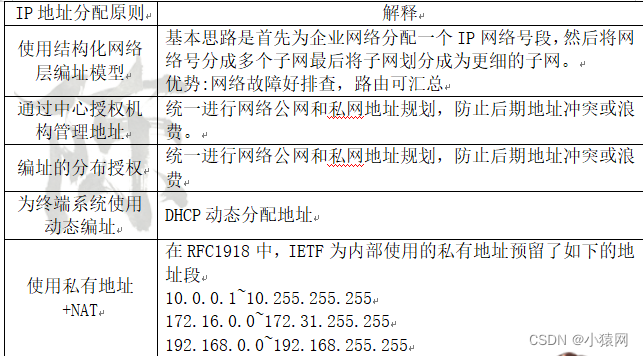
7、命名设计:遵循的原则:
1)增强易用性:名字应该简短、有意义、无歧义
2)名字可以包含位置代码,如第几分公司、总部等特殊的代码
3)名字中应尽量避免使用连字符、下划线、空格等字符
4)名字不应该区分大小写,否则会导致用户使用的不方便
8、STP中,收敛的定义是:所有端口都处于转发状态或阻塞状态。
9、MSTP+VRRP和堆叠iStack方式组网的优缺点: - 两种组网方式都能满足设备冗余和负载均衡的要求;
- MSTP+VRRP的组网方式设备兼容性要求不高,组网更灵活,可以跨交换机实现组网,但是配置更为复杂,维护成本更高;
- 堆叠对设备型号匹配要求较高,而且两台交换机之间不能有其他的交换机,但具有强大的网络扩展能力(增加端口数量带宽和处理能力),堆叠简化了配置和管理,可以实现跨设备链路聚合,实现快速收敛,在故障恢复方面,网络连续性也高于MSTP+VRRP
10、业务随行相对传统访问控制的优势有: - 在传统园区网络中,控制用户网络访问权限主要通过NAC技术结合VLAN和ACL技术来实现的,无法与IP地址解耦,IP地址变化时需到多个设备变更配置,维护工作量大。
- 而业务随行采用了基于业务的权限控制,能够让用户不论在哪里都能享受一致的业务体验;
- 集中配置,新增设备自动配置;在用户位置变更时自动适配,管理员无需操作;而且随着设备的规模增加,维修效率提升越明显;
六、物理网络设计
(一)结构化布线
1、结构化布线
- 结构化综合布线系统是基于现代计算机技术的通信物理平台,集成了语音、数据、图像和视频的传输功能,消除了原有通信线路在传输介质上的差别。
- 结构化布线系统包含6个子系统:工作区子系统、水平布线子系统、干线子系统、设备间子系统、管理子系统和建筑群子系统。口诀:群干监理不工作
2、几个重要的布线距离 - 通常情况下,信息插座的安装位置距离地面的高度为30~50cm
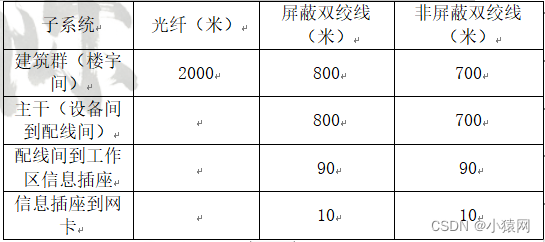
(二)机房设计
1、机房的位置选择
- 中心机房的物理位置在多层建筑或高层建筑物内宜设于第1~8层,更高层次不适合作为机房建设楼层。机房位置选择应符合以下要求。
- ①水源充足、电力比较稳定可靠、交通通信方便、自然环境清洁。
- ②远离产生粉尘、油烟、有害气体以及生产或储存具有腐蚀性、易燃易爆物品的工厂、仓库、堆场等。
- ③远离强振源和强噪声源。
- ④避开强电磁场干扰。
- 当无法避开强电磁场干扰为保障计算机系统信息安全,可采取有效的电磁屏蔽措施。
2、中心机房的组成 - 中心机房组成应按计算机运行特点及设备具体要求确定,一般宜由主机房、基本工作间、第一类辅助房间、第二类辅助房间和第三类辅助房间等组成。
- 主机房:部署交换机、路由器、服务器、存储等硬件设备;
- 基本工作间:完成信息处理过程和必要的技术作业的处所,一般是几台电脑,IT人员值班的地方;
- 第一类辅助房间:直接为计算机硬件维修、软件研究服务的处所。包括:硬件维修室、软件分析修改室、仪器仪表室、备件库、随机资料室、未记录磁介质库、示记录纸介质库、硬件人办公室、软件人员办公室、上机准备室和外来用户工作室等;
- 第二类辅助房间:为保证电子计算机机房达到各项工艺环境要求所必需的各公用专业技术用房。其中包括:变压器室、高低压配电室、不间断电源室、蓄电池室、发电机室、空调器室、灭火器材室和安全保卫控制室等;
- 第三类辅助房间:用于生活、卫生等目的的辅助部分。包括:更衣室、休息室、缓冲间和沐浴室等。
- 中心机房的使用面积应根据网络与计算机设备的外形尺寸布置确定。
3、设备布置: - 网络与计算机设备宜采用分区布置,一般可分为服务器区、存储器区、网络设备区、安全设备区、通信区和监控区等。
- 需要经常监视或操作的设备应布置于方便行走、便于操作的位置。
- 产生尘埃及废物的设备应远离对尘埃敏感的设备,并宜集中布置在靠近机房的回风口处。
4、机房环境条件: - 温湿度:温度为20±2℃,相对湿度为45%~65%,温度变化率==<5℃/h并不得结露==。
- 机房铺设活动地板,铺设高度应按实际需要确定,宜为200~350mm.
- 机房应采用下列4种接地方式。
- ①交流工作接地,接地电阻不应大于4Ω。
- ②安全工作接地,接地电阻不应大于4Ω。
- ③直流工作接地,接地电阻应按计算机系统具体要求确定。
- ④防雷接地,应按现行国家标准《建筑防雷设计规范》执行。
5、机房的补充 - 散热方式:风冷、水冷、自然冷却。
- PUE(电源使用效率)是国际上通行的数据中心电力使用效率的衡量指标。PUE=数据中心消耗的所有能源与IT负载消耗的能源之比。
- PUE值越接近于1,表示一个数据中心的绿色化程度越高。
- 国外先进的数据中心机房PUE值通常小于2,而我国的大多数数据中心的PUE值在2-3之间。绿色机房的PUE理想目标是1.5以下。
6、模块化机房数据中心优势: - 快速部署、缩短建设周期
- 方便扩展、分期建设
- 绿色、节能
- 智能管理、高运营
7、为了降低能耗,应当合理的进行机柜的布局。通常使机柜面对面、背对背的形式排列,形成冷、热通道。按照冷、热通道交替设置的原则布置机柜,冷通道设在机柜前面,热通道设在机柜的后面,可以减少冷热气流的混流,提高冷风的利用率,从而起到提高制冷率,降低数据中心用电成本。机房在设计装修机房时铺设了防静电地板,机房宜采用送风形式是下进风、上回风的布局。目前新型的数据中心机房中,为了应对云计算、虚拟化、集中化、高密化等服务器的变化,提高数据中心的运营效率,降低能耗,通常采用微模块形式组建数据中心.
7. Network testing and operation and maintenance
1. Network testing methods are divided into:Active and passive testing.
1) Active testing:
- Active testing: using test tools to actively test the network under testInject test traffic, analyze the technical parameters of the network according to the transmission situation of the test flow.
- The advantage is to havegood flexibility, can generate different flows, such as packet size and type (simulating various applications), etc. Active testing is "invasive" measurement, there are certainSecurity risks.
2) Passive testing: - Passive testing: Use specific testing tools to collect specific information on elements in the network (including devices such as routers, switches, and servers),A method for measuring network performance and functions through quantitative analysis。
- commonly usedSNMP protocol reads related MIB information, Tested by Sniffer, Ethereal and other special packet capture analysis tools. Passively testedThe advantage is its security. Disadvantages of passive testingIt is not flexible enough and has relatively large limitations. It only collects information passively and cannot perform tests according to the wishes of the measurers. It will be restricted by network organizations, test tools, etc.。
- Passive testing will not cause hidden dangers such as injection of DDos, network deception, etc.
2. Testing tools: mainlyThere are cable testers, network protocol analyzers and network testers - Cable tester: It is used to detect the quality of the cable, and can directly judge the on-off status of the line.
- Network protocol analyzer: mostly used for passive testing of the network,Analyzer captures packets and frames on the network, network maintenance personnel can quickly check network problems by analyzing the captured data, such as wireshark.
- Network Tester: DedicatedTest equipment combining hardware and software, with special test boards and test software. This type of equipment is mostly used for active testing of the network. It can comprehensively test network equipment, network systems and network applications. It has three typical functions:Datagram capture, load generation and intelligent analysis. Network testers are mostly used for testing large networks.
3. Multi-functional network cable finder/testing instrument, normal mode: precise cable hunting when cables are dense; POE mode: test network cable length, breakpoint, short-circuit point POE test 4. Optical fiber test
tool (red light pen): - Advantages: easy to carry, ready to use. Put the red light pen on the fiber optic head, adjust the button to light up continuously or pulse light, arrange someone to stare at the other end of the fiber optic cable, and see that the fiber head has light, it is on;
- Disadvantages: Only breakpoints can be tested, but there is no data reflection.
5. Optical fiber test tool (optical power meter): If you are Party A, the construction unit will say that the work of the optical cable is over. If you don't believe it, you can go to the site with an optical power meter and plug in the jumper first,Test the luminous power of the optical transceiver/optical module; Then connect this end of the fiber to the optical transceiver/optical module/light source, and then run to the other endPlug in the optical power meter,See how much light loss. In this matter, youFocus on results, not process.
6. Optical fiber test tool (OTDR): because they not only need to know the loss of the optical fiber, but more importantly, they also need to locate the fault point. Otherwise, how to rectify it and where to rectify it? They use OTDR for a dozen, this fiber where it is broken, where there are obvious steps,Where is there a problem with welding, where is there a bend, and the test length fault distanceIt is clear at a glance.
7. Comparison of optical power meter and optical time domain reflectometer OTDR principle: - The optical power meter can determine the optical fiber link under testTotal amount of loss or attenuation: At one end A of the optical fiber, a stable light source emits a signal at a specific wavelength. A signal formed by a continuous light wave; at the other end B, an optical power meter detects and measures the power level of the signal.
- What OTDR detects and analyzes is the signal returned by Fresnel (Fresnel) reflection and Rayleigh (Rayleigh) scattering.
- The optical power meter test loss is like this: I am in the linkHeadend sends100 photons, atThe terminal only receivesTo 20 photons, 80 of them are lost. The OTDR is not tested in this way. It also sends 100 photons at the beginning of the link, but it does not go to the opposite end to test, but waits for the rabbit to pass the test.Scatter or reflect back photons to get the result.
8. Line test: - Twisted pair wire and optical fiber are the most widely used communication media at present. According to the EIA/TIA568B wiring standard and TSB-67 test standard, the qualified twisted pair and fiber optic cabling are shown in the figure:
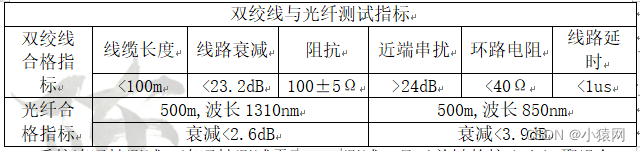
9. System connectivity test: Connectivity test requires the use of test tools to test key core and aggregation equipment and key servers , to perform a connectivity test. - It is required that all networked terminals must comply with the requirements of useall connected。
- Test method: Use test tools to test key network devices (such as switches and routers) on key servers, core layers, and aggregation layers of the network.10 Ping tests, each interval 1s, to test network connectivity. The test path should cover all subnets and VLANs.
- Sampling rules: no less than the total number of devices at the access layer10% ratio for sampling test,samplingFor less than 10 devices, all tests. Select at least one port in each sampling device, that is, the test point, and the test point should be able to cover different subnets and VLANs.
- Eligibility criteria: single item eligibility criterion: Ping test from test point to key nodeWhen connectivity reaches 100%, it is determined that the single-point connectivity meets the requirements.
- Comprehensive eligibility criteria:When the connectivity of all test points reaches 100%, it is determined that the connectivity of the system meets the requirements; otherwise, it is determined that the connectivity of the system does not meet the requirements.
10. Link transmission rate: - Full-duplex (such as switch) send port speed100% line speed flow,Half-duplex (such as hub) transmit port speed50% line speed flow(recommended frame length is 1518 bytes);
- Sampling rules:
- All tests: the backbone link of the core layer, the uplink link from the aggregation layer to the core layer;
- Sampling test with a ratio of no less than 10%: for the uplink links from the access layer to the aggregation layer, if the number of sampled links is less than 10, test all of them. Transmission rate qualification standard
11, throughput, transmission delay, packet loss rate: - Throughput:The maximum datagram forwarding rate that the tested network link can achieve without packet loss in the no-load network。
- Transmission delay: refers to data packetsTime elapsed from sending port (address) to destination port (address). Usually, the transmission delay is related to the transmission distance, passing equipment and channel utilization. Under normal network conditions, the transmission delay should not affect the use of various services (such as video on demand, IP-based voice/NoIP and high-speed Internet access, etc.).
- Packet loss rate: refers to the proportion of some data packets that cannot be forwarded due to network performance problems when the network is under 70% traffic load.
12. Test report: - After the test is completed, a complete test report should be provided. The test report should describe in detail the test objects, test tools, test environment, test content and test results in this test.
- The form of the test report is not fixed, it can be a short summary or a long written document. Usually the test report contains the following information.
- Purpose of the test: Explain the purpose of this test in one or two sentences.
- Conclusion: Information gained from the test and recommendations for next steps.
- Summary of Test Results: Summarize the tests and draw conclusions from them.
- Test content and method: briefly describe how the test was conducted, should include load patterns, test scripts and data collection methods, and explain
- How does the test method adopted ensure that the test results are related to the test purpose, and whether the test results are reproducible.
- Test Configuration: The network test configuration is represented graphically.
13. Safe backup strategies include: - Configuration and software of all network infrastructure equipment
- All servers and configurations that provide network services
- Regularly verify the correctness and completeness of backup files, etc.
14. Once the optical power is too high during the commissioning of optical network equipment, it is easy to cause the optical module to be burned. The operation requirements are as follows: - Before commissioning, you must first master the received optical power parameters required by the board, and perform commissioning in strict accordance with the received optical power requirements specified in the commissioning guide;
- Before the input optical signal is connected to the receiving optical port of the single board, it must first test whether the power meets the commissioning requirements. It is forbidden to operate without optical attenuation and self-loop when the optical power exceeds the receiving overload point, and ensure that the input optical power does not exceed the allowable limit of the device. maximum value.
- When testing the overload point, it is enough to meet the national standard, and it is forbidden to exceed the national standard by more than 2 dB.
- When using an OTDR and other instruments capable of outputting high-power optical signals to measure the optical path, disconnect the communication equipment from the optical path.
15. Sampling rules in network throughput test - All backbone links of the core layer should be tested
- All uplinks from the aggregation layer to the core layer should be tested
- The uplink link from the access layer to the aggregation layer shall be sampled and tested at a rate of not less than 10%.
- For the end-to-end link (that is, the user-to-user network path passing through the access layer, aggregation layer, and core layer) andNot less than 5% of the number of end usersRatio for random testing
16,OTDR,OTDR, is a precision optoelectronic integrated instrument made by using Rayleigh scattering and backscattering produced by Fresnel reflection when the light is transmitted in the optical fiber. It is widely used in the maintenance and construction of optical cable lines. carry lightMeasurement of fiber length, fiber transmission attenuation, joint attenuation and fault location。
17、TDR, time domain reflectometer,一种对反射波进行分析的遥控测量技术,在遥控位置掌握被测量物件的状况。在网络介质侧试中可用于测试电缆断点。
18、BERT,误码率测试仪,用于测试网络传输中的误码率。
19、Sniffer是一种网络数据嗅探器,是一种基于被动侦听原理的网络分析方式。使用这种技术方式,可以监视网络的状态、数据流动情况以及网络上传输的信息。
八、网络故障分析与处理
1、排查思路:故障定义->收集信息->根据情况,分析原因->建立行动计划->实施行动计划->观察结果->(现象消失问题被解决,终止进程)->没有消失就重复进程->还不行在收集信息->…
2、排查工具:排除网络故障的常用工具有多种,总的来说可以分为三类:设备或系统诊断命令、网络管理工具以及专用故障排除工具。
1)设备或系统诊断命令:许多网络设备及系统本身就提供大量的集成命令来帮助监视并对网络进行故障排除。
- display命令:可以用于监测系统的安装情况与网络的正常运行状况,也可以用于对故障区域的定位。
- debug命令:帮助分离协议和配置问题。
- ping命令:用于检测网络上不同设备之间的连通性。
- tracert命令:可以用于确定数据包在从一个设备到另一个设备直至目的地的过程中所经过的路径。
2)网络管理工具:一些厂商推出的网络管理工具如Cisco Works、HP OpenView、华为esight、华三IMC、锐捷SNC/RIL等都含有监测以及故障排除功能,这有助于对网络互联环境的管理和故障的及时排除。
3)专用故障排除工具:可能比设备或系统中集成的命令更有效。如: - 欧姆表、数字万用表及电缆测试器可以用于检测电缆设备的物理连通性。
- 时域反射计(TDR)与光时域反射计(OTDR)用于测定电缆断裂、阻抗不匹配以及电缆设备其他物理故障的具体位置。
- 断接盒(breakout boxes)智能测试盘和位/数据块错误测试器(BERT/BLERT)用于外围接口的故障排除。
- 红光笔和光功率计可以测试光纤连通性,后者可以测衰减。
- 网络监测器通过持续跟踪穿越网络的数据包,能每隔一段时间提供网络活动的准确图像。
- 网络分析仪(例如,NAI公司的Sniffer)可以对OSI所有7层上出现的问题进行解码,自动实时地发现问题,对网络活动进行清晰的描述,并根据问题的严重性对故障进行分类。
3、分层诊断:
1)物理层故障: - 物理层的故障主要表现为设备的物理连接方式是否恰当,连接电缆是否正确,确定路由器端口物理连接是否完好的最佳方法是使用display interface命令,检查每个端口的状态,解释屏幕输出信息,查看端口状态、协议建立状态和up状态。
- 千兆传输需要使用8芯网线,如果出现物理层故障,比如只能用7芯,可能将为百兆传输。
2)数据链路层故障: - 查找和排除数据链路层的故障,需要查看路由器的配置,检查连接端口的共享同数据链路层的封装情况。每对接口要和与其通信的其他设备有相同的封装。通过查看路由器的配置检查其封装,或者使用display命令查看相应接口的封装情况。
3)网络层故障: - 排除网络层故障的基本方法是:沿着从源到目标的路径,查看路由器路由表,同时检查路由器接口的IP地址。如果路由没有在路由表中出现,应该通过检查来确定是否已经输入适当的静态路由、默认路由或者动态路由。
4)应用层及其诊断 - 应用层提供最终用户服务,如文件传输、电子信息、电子邮件和虚拟终端接入等。排除应用层故障的基本方法是:首先可在服务器上检查配置,测试服务器是否正常运行, if there is no problem with the server, check whether the application client is configured correctly.
4. There are two important indicators to measure the system failure and recovery process, which meansThe time period from when the system fails and the service stops to when the system recovers to support the normal operation of the system is RTO, usually, the value of this indicatorsmaller, representing the data recovery capability of the disaster recovery systemstronger. expressAfter the system is restored, the index of the maximum amount of data loss that can be tolerated is RPO. The values of bothsmaller,At onceThe more effective it is to shorten the time interval of the business transition period。
Chapter 5 Network Resource Devices
1. Server foundation and hardware architecture
(1) Server concept and features
1. Server Server:
- A server is a kind of high-performance computer. As a node of the network, it stores and processes 80% of the data and information on the network, so it is also called the soul of the network.
- To make an image metaphor: the server is like a switch in a post office, and fixed or mobile network terminals such as computers, notebooks, PDAs, and mobile phones are like telephones scattered in homes, various office spaces, and public places.
2. Features of the server: - Reliability
- Reliability is the property of maintaining reliability and consistency. Data integrity and warning of hardware failures before they occur are two aspects of reliability, such asHardware redundancy, early warning, RAID technology
- High Availability
- High availability refers to features that are always present and ready for immediate use
- Rapid recovery from system failures; hot-swappable support for critical components; ability to replace failed components with new components
- Scalability
- There is a certain amount of expandable space and redundant components (such as disk array racks, PCI and memory slots, etc.) on the server.
- Ability to increase memory; increase processor capability; increase disk capacity; support limitations of multiple mainstream operating systems
- Usability
- Whether it is easy to operate, such as whether the user navigation system is perfect, whether the chassis design is humanized, whether there is a key recovery function, whether there is an operating system backup, and whether there is sufficient training support, etc.
- Manageability
- On the one hand, more efficient management, less manpower and material resources; on the other hand, it provides a simple infrastructure and simplifies management from the most basic level.
3. Measure the performance of the server: - Overall server performance index: TPC value
- CUP performance index: SPEC value (can be quantified to measure CPU performance index)
(2) Different classifications of servers
1. According to the processor architecture of the server (that is, the instruction operating system adopted by the server CPU), the server can be divided into RISC architecture server and IA architecture server. The latter includes two types of CISC architecture server and VLIW architecture server.
2. RISC architecture server: RISC (Reduced Instruction Set Computer) is relative to the traditional Complex Instruction Set Computer (CISC). The basic idea of RISC is to simplify the functions of computer instructions as much as possible, and only keep those instructions with simple functions that can be executed within one clock cycle, and implement more complex functions with a subroutine, and use pipeline technology to use a large number of general-purpose registers To reduce the number of memory accesses, thereby improving execution speed.
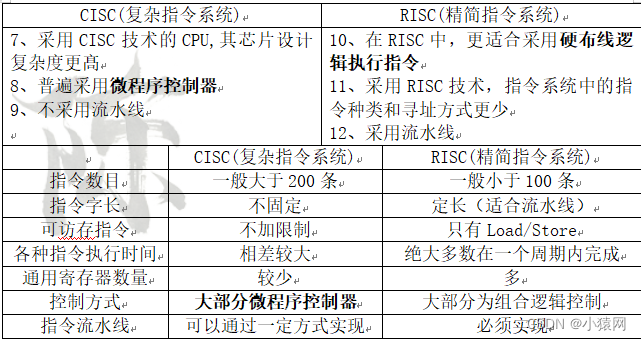
3. IA architecture server: A server using an Intel processor is usually called an IA architecture server, also known as a CISC (Complex Instruction Set) architecture server. The architecture server adopts an open system and is characterized by "small, compact, and stable". With its reliable performance and low price, it has realized industrial standardization technology and received support from a large number of domestic and foreign software and hardware suppliers, and has been widely used in my country. Applications.
4. The IA architecture server can complete more major applications such as file service, printing service, communication service, WEB service, email service, database service, application service, etc. in the Internet and LAN.
5. Server classification - application requirements:
- The priority of the database server for hardware requirements ismemory, disk, processor。
- The priority of the file server for hardware requirements isNetwork system, disk system and memory。
- The website is a static web server hardware requirements from high to low areNetwork system, memory, disk system, CPU. Intensive computing Web (for example, dynamically generating Web pages), the hardware requirements for the server are in orderMemory, CPU, disk subsystem and network system。
- The mail server's priority for hardware requirements ismemory, disk, network system, processor.
6. Server classification - appearance: rack (RACK), blade (Blade) server (similar to high-end switches), tower (Tower) server
1) rack (RACK) server - Standard telecommunications room equipment, the width is 19 inches, the height U is measured, and each U is 1.75 inches, or 4.445cm.
- Usually 1U, 2U, 4U and 8UMainly shipped in 2U and 1U, followed by 4U and 8U.
2) Blade server - A higher density server platform. pluggableComputing blade/storage blade/network blade。
- (8~20) "blades" can be inserted into a case, and each "blade" is actually a system motherboard.
3) Tower server - Vertical and horizontal chassis servers can be placed in office environments. The chassis structure is larger (similar to a desktop computer).
- Tower servers have low density and are mostly single-processor systems (a few are dual-processor systems).
- Graphics workstation, noisy.
7. Server classification - number of processors and application scenarios
1) According to the number of processors (single, dual, multi-channel) - Road: the number of CPUs supported by a server
- Core: multiple chips integrated in one package
- Threads: The more threads, the stronger the performance
2) According to the application scenario - File, ERP, WEB, FTP, database
- Mail, video surveillance, streaming media, game servers, etc.
8. Hyper-converged servers
1) Blade servers have integrated == switches and storage devices (== plug-in cards) - Space reason:Impact of memory/hard disk capacity expansion
- subject to cooling conditions and compactChassis Limitations,Blade server CPU performance is low
2) Hyper-converged server - Efficient use of space, 2U4 nodes
- The network is generally still an independent switch
- Self-contained server virtualization/storage virtualization/cloud operating system and other software
(3) Server composition and hardware architecture
1. CPU and memory:
- Each series has many models and specifications to choose from
- The CPU with V4 specifications has been released from the market, and the follow-up will be fully replaced by Platinum,Gold, Silver, bronze instead of
- Generally speaking, for the same type of CPU, the performance of the v4 specification is nearly 50% == or more than that of the v3 specification.
- The memory is divided into two specifications (16G/32G/64G) of DDR3 and DDR4 (16G/32G/64G), and now DDR4 is generally used
2. Hard disk indicators: capacity and speed
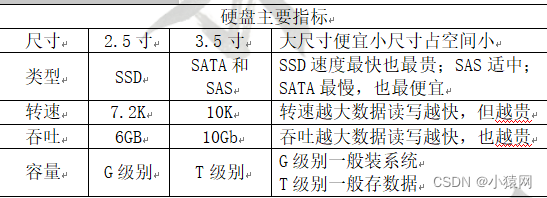
3, I/0 and RAID card - 网卡:服务器连IP网络,面向用户
- HBA卡:服务器连存储,面向数据
- RAID卡:用来做数据本地备份
4、为数据库服务和web服务选择高性能的解决方案,较好的方案应该是:数据库服务器用SMP计算机(主要是串行操作),web服务器用集群计算机(主要是并行操作)
二、服务器虚拟化与云平台
(一)服务器虚拟化
1、数据中心现状:(1)9-9-1规律:90%的服务器、90%的时间、CPU占用率低于10%;(2)数据中心能耗分布:30%的IT设备耗能、70%制冷散热、加湿;(3)系统冗余措施:双击热备、3击热备、N击热备
2、服务器虚拟化:
- 软件:Vmware ESXi、Microsoft Hyper-v、开源KVM(H3C CAS)
- 华为最早虚拟化基于Xen,后转移到KVM
- 深信服新华三等均基于KVM开发
3、虚拟化的优势: - 提高物理服务器CPU利用率.
- 提高数据中心能耗效率
- 提高数据中心高可用性
- 加快业务部署速度
4、借助虚拟化软件在一台物理服务器上运行多个操作系统,虚拟前后对比:
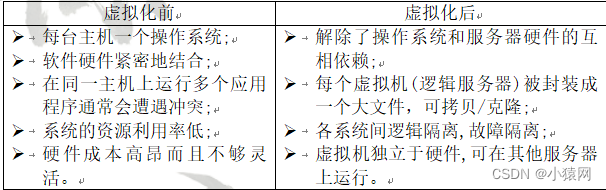
5、虚拟化技术的4大特性: - 分区:在单一物理服务器上同时运行多个虚拟机
- 隔离:在同一个服务器上的虚拟机之间相互隔离
- 封装:整个虚拟机都保存在文件中,且可以通过移动和复制这些文件来移动和复制该虚拟机
- Relative to hardware independence: Virtual machines can be run on any server without modification
6. Server virtualization classification:
1) Based on OS-Level (operating system): IBM AIX, CISCO N7K VDC saves the most resources, but it can only be used with the parent Consistent system
2) Hosted (host): VMware Workstation, Virtual Server
3) Based on Bare-Metal (logic): VMware ESX Server, Microsoft Hyper-V
7. When designing virtualized computing resources, some basic principles need to be followed, such as: - 1) Single virtual serverThe maximum configuration of CPU and memory is recommended not to exceed the maximum CPU and memory configuration of a single physical server in the physical computing resource cluster;
- 2) The sum of the CPUs of all virtual hosts on a single physical server shall not exceed 1.5 times the total cores of the physical machine;
- 3) On a single physical serverThe sum of the memory of all virtual hosts does not exceed 120% of the memory of the physical machine;
- 4) The built-in hard disk of the old server, that is, the availability and I/O throughput of the built-in disk are weak, it is not recommended to store virtual machines on it, and it is recommended to use an external high-performance disk array; 8.
Virtualizationbare metal architecture: The bare metal architecture isInstall virtualization software directly on the hardware, and then install the operating system and applications on it, relying on the virtualization layer kernel and server console for management。 - Advantages: The virtual machine does not depend on the operating system, can support multiple operating systems, multiple applications, and is more flexible
- Disadvantages: It is difficult to develop the virtual layer kernel
9. Virtualizationsojourn architecture: The sojourn architecture is to install and run virtualization programs on top of the operating system, relying on the support of the host operating system for devices and the management of physical resources; - Advantages: simple, easy to implement
- Disadvantage: Installing and running the application depends on the support of the device by the host operating system
(2) Advanced application of virtualization
1. VMware advanced application vMotion
- The principle of vMotion: put a normalA provisioning VM is moved from one physical server to anothertechnology (memory copy)
- Server hardware maintenance to ensure uninterrupted business
- Migrate workloads to maximize resource utilization
2. Prerequisites for implementing vMotion: - VM must be placed in shared memory
- The CPU type is the same (intel/amd cannot be mixed, and different models of intel are no problem)
- This function requires license support
3. Understanding of vMotion: - vMotionNot High Reliability Technology, The VM suddenly goes down, and vMotion is not helpful for failover and quick recovery of application access. Principle of vMotion:Move a normal in-service VM from a physical serverThe technique of moving to another physical server.
- Purpose: as much as possibleIt is convenient for service managers to schedule resources. (planned migration)
- vMotion usage scenarios: When the physical server needs to be replaced, shut down and restart, or the data center needs to be expanded, vMotion will come into play at this time.Such as: hardware maintenance, load balancing。
- When cross-data center site vMotion, it is very troublesome to solve the problem of cross-site shared storage. Since this part of the content has little to do with the network, it belongs to the territory of the storage manufacturer.
- vMotion drives data center intersiteLarge Layer 2 interconnection and multi-site dynamic route selectionNetwork requirements, leading to the emergence of a series of new network technologies such as OTV, LISP and VXLAN.
4. VMware Advanced Application - HA High Availability: ServerfailureAutomatic restart of virtual machines on other physical servers, corresponding advantages: - High availability for all applications at low cost
- Does not require identical duplicate hardware
- Compared with traditional clusters, it has a higher cost advantage and is easy to use and operate.
5. VMware advanced applications - FT fault tolerance - on a different hostRun the same virtual machine simultaneously
- When a hardware failure occurs, all virtual machines can achieve zero downtime and zero data loss failover
6. Comparison of vMotion HA and FT technologies: - vMotion:Planned Migration (Hot Migration). The virtual machine located on the single HOST server is manually, semi-automatically or automatically (combined with DRS) migrated to its host in the Cluster by the user. The whole process requires almost no downtime. Some people are used to calling it seamless migration;
- HA:全称High Availbility (高可用).计划外宕机保护功能,简单而言就是处于相同Cluster里的A HOST主机异常宕机(停电、硬盘坏掉等)之后,自动在Cluster里的其它HOST主机上启动原来A HOST主机上的VM的行为。这样做可以保证整体停机时间不超过5到10分钟,能起到意外宕机保护(需要VM重启);
- FT:全称Fault Tolerance(容错)。计划外宕机保护功能HA的进一步深化,它在HA的基础上实现了异常HOST主机上的处于FT保护下的虚拟机不用重启,直接可以在Cluster里的其它HOST主机上正常运行,整个过程无中断,常被人称为“计划外0宕机”保护。(FT目前要求单vCPU和EagerZeroed Thick模式的虚拟磁盘).
7、VMware高级应用——DRS分布式资源调度:例子说明:A服务器跑了2个虚拟机(利用率低),B服务器跑了12个虚拟机(利用率高),这时就可以把B上面的一些虚拟机分配到A服务器上,保证服务器的负载均衡
8、VMware高级应用——DPM分布式电源管理 - 群集需要的资源越少,就将工作负载整合到越少的服务器上
- 将不需要的服务器置于待机模式
- 工作负载需要增加时,再恢复服务器在线状态
- 保证服务级别的同时减少电力消耗
- 虚拟机不中断、不停机
9、VMware高级应用——SRM站点容灾管理 - 存储阵列之间的复制时间数据同步
- 与VMware SRM配合,实现虚拟机和存储阵列的同步切换
10、集群、虚拟化和存储的关系 - 集群、虚拟化环境,必须要用存储阵列(共用一个存储)
11、虚拟化的优缺点和风险: - (优点)资源利用率高、扩展性伸缩性好、冗余能力强、快速部署、集中统一管理、运维高效便捷、长期运维成本低等特点;
- (缺点)虚拟主机之间并非物理隔离,要安装虚拟机边界防护措施;
- "Three Storms":Start Storm, Antivirus Scan Storm, Upgrade Storm;
- Network bandwidth bottleneck: All operations of each user need to be transmitted through the network. After reaching a certain amount, it will cause a network bandwidth bottleneck problem. The network bandwidth can be designed and improved according to actual needs.
- Poor performance in special applications: For example, high-definition video, design drawing, and 3D animation require a dedicated graphics card.
- The unified investment of computing and storage resources is large: the short-term investment cost is higher than that of general traditional physical hosts and servers, and it is used for larger units or enterprises.
- The contradiction between centralized management and control and user habits
(3) Cloud Computing Platform
1. Functional architecture of the cloud management platform: downward resource management: computer resource management, storage resource management, network resource management, mirror management, management server virtualization (VMware, KVM), management storage virtualization (CEPH), management network virtualization (SDN platform: Huawei AC, ODL). Upward operation management: user management, work order management, measurement management, monitoring statistics, operation and maintenance management
2. Cloud management platform goal: eliminate the differences of virtualization systems, and realize unified scheduling, management, security and automation services
3. Cloud management Platforms and OpenStack:
- OpenStack is a cloud computing architecture, sub-modules can be freely selected
- Common cloud management platforms in the industry (Huawei, H3C, Inspur, Sugon, etc.) are basically developed based on OpenStack
- Cloud management platform (OpenStack) (boss) and virtualization platform (KVM) (manager) (difference)
4. Currently popular virtual cloud desktops are: - VDIVirtual Desktop Basicsarchitecture;
- RDSRemote DesktopServe;
- IDVsmart desktopvirtualization architecture;
- BUTTERvirtual operating systemInfrastructure
5. The advantages of using virtual cloud desktops are: - information security: All data is on the cloud platform, there is no data locally, and cannot be copied, burned, etc.
- Easy to manage and maintain: All applications and data are on the cloud platform, which can be managed, disinfected and backed up by maintenance personnel in a unified manner, reducing maintenance costs and improving maintenance efficiency.
- cost-effective: Because the cloud terminal does not have a hard disk, it has low requirements on CPU, memory and other performance, the price of the terminal equipment is low, the life cycle is long, and the investment is saved
3. Storage basis
(1) Network storage foundation
1. Storage medium:
- Floppy disk: reading and writing of floppy disk is completed through the floppy disk drive (1.44M 3.5-inch floppy disk)
- Magnetic tape: A strip of magnetically loaded material used for recording sound, video, digital, or other signals (Walkman)
- Hard disk: It is one of the main storage media of the computer, consisting of one or more aluminum or glass discs
- Optical disc: optical disc uses optical information as the carrier of storage (VCD/DVD)
- Flash memory: a non-volatile memory device (SSD hard disk is composed of a set of Flash + controller)
2. Generalized storage definition: - Storage hardware system (disk array, controller, disk cabinet, tape library, etc.)
- Storage software (backup software: management software, snapshot, replication and other value-added software)
- Storage network (HBA card, fiber switch, FC/SAS cable, etc.)
- Storage solutions (centralized storage, archiving, backup, disaster recovery, etc.)
3. Storage system hierarchy: divided intocache memory, main memory, and external memory.
4. [Example: Assuming that there is a single point of failure in the storage department, it can be improved: two FC fiber switches can be configured, the server is configured with dual HBA cards and connected to two FC fiber switches, and the storage device is connected to two FC fiber switches]
5 2. Different types of storage methods: In order to reduce the overall investment in storage, enterprises usually adopt different storage methods for different data:Online storage (OnStroe) (often used), near-line storage (NearStore) (occasionally used) and offline storage (OffStore) (for backup).
6. The performance indicators of the mechanical hard disk in the computer include: disk speed, capacity and average seek time
7. The main performance indicators for the evaluation of the database management system are:The maximum number of connections, the number of indexes allowed by the database, and the maximum concurrent transaction processing capabilitywait
(2) Commonly used storage media
1. Storage medium: mechanical hard disk, solid-state hard disk; backup medium: tape library/CD tower
2. Hard disk type: desktop-level hard disk is aimed at desktop PC/notebook, etc.; enterprise-level hard disk is aimed at enterprise-level servers, storage disk arrays, and graphics workstations wait.
- Capacity: Compared with desktop-level hard drives, enterprise-level hard drives have larger storage capacity, and the current maximum capacity of a single hard drive can reach 6TB
- Performance: mainly reflected in speed, cache, average seek time, etc.
- Reliability: Enterprise-class hard drives have a higher mean time between failures (MTBF). The MTBF of desktop-class hard drives is generally 500,000 hours, and enterprise-class hard drives are above 1 million hours.
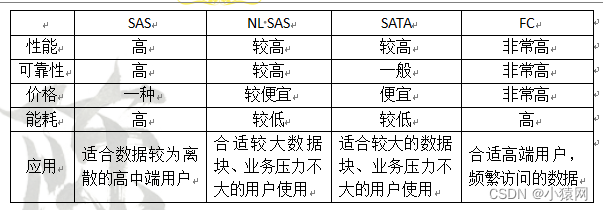
3. Mainstream hard disk types:
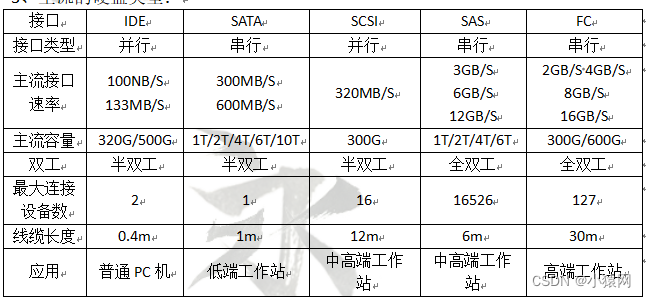
4. Mechanical hard disk and SSD hard disk: - The continuous read and write performance of the mechanical hard disk is very good, but the random read and write performance is poor. Because it takes time for the magnetic head to move to the correct track, during random read and write, the magnetic head keeps moving, and the time is spent on the magnetic head seeking, so the performance is not high.
- Applications with frequent random reading and writing: small file storage (picture), database, mail server (focus on IOPS) (SSD is recommended)
- Applications with frequent sequential reading and writing: video surveillance, video editing (focus on throughput) (recommended to use HDD)
5. Key indicators of hard disk - Hard Disk Capacity (Volume): The unit is megabytes (MB) or gigabytes (GB). The factors that affect the hard disk capacity are single disk capacity and the number of disks.
- Rotational speed: The rotational speed of the hard disk refers to the number of revolutions of the hard disk platter per minute. The unit is RPM (Rotation Per Minute), which measures the read and write performance. Generally, the SATA hard disk speed is 5.4K/7.2KRPM, the SAS hard disk speed is 10K/15K, and the SSD hard disk has no speed.
- Average access time * (Average Access Time) = average seek time + average waiting time.
- Data transfer rate/throughput (Date Transfer Rate): The data transfer rate of a hard disk refers to the speed at which the hard disk reads and writes data, and the unit is megabytes per second (MB/s). For applications with a large number of sequential reads and writes, such as TV station video editing, video on demand, etc., more attention should be paid to the throughput index.
- IOPS (Input/Output Per Second): The amount of input and output per second (or the number of reads and writes), is one of the main indicators to measure disk performance. For applications with frequent random reads and writes, such as OLTP (Online Transaction Processing), IOPS is the key measurement indicator.
6. Storage medium: - Tape library: store cold data, with tape as the main medium (such as storing clothes)
- Disk array or cloud storage: store temperature data, with hard disk as the main medium (such as daily commuting clothes)
- Memory array: store hot data, with flash memory as the main medium (such as underwear, panties and socks that need to be changed every day)
7. Advantages of tape library: - Low cost, more power saving, lighter
- More solid (after the tape library is broken, the tape can be reconnected, and all the data will not be lost; if the hard disk is broken, the entire data may be lost)
- Safer (the tape library crashed, and the tapes are offline, should I use scissors to cut them short one by one? For hard drives, such as rm -f /* in Linux, the data can be destroyed instantly) 8
.The biggest feature of SATA is large capacity and low cost, Compatibility with SAS hard drives is also good. For online, near-line work is better.
9. SAS is mainly suitable for online, high availability, random read and write environments.Data storage for key business systems is more appropriate, and high performance, good scalability.
4. Disk array RAID technology
(1) Basics of RAID
1. RAID technology instantly combines multiple individual physical disks into a logical disk in different ways, thereby improving the read-write performance and data security of the disk. 2. RAID data organization and access methods: 1)
Block
: Divide a partition into multiple blocks of equal size and contiguous addresses, these blocks are called partitions. It is the element that makes up the strip.
2) Stripe: A partition to the same "position" (or the same number) on multiple disk drives in a disk array.
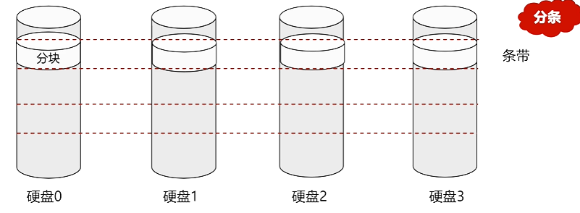
3. RAID hot backup and reconstruction
1) Hot backup: when redundant RAID groupa hard drive failsWhen the current RAID system is not affected, use theThe spare hard disk automatically replaces the failed hard disk, Ensure the redundancy of the RAID system in time.
2) Hot standby is generally divided into two types:
- Global type: the spare hard disk is shared by all redundant RAID groups in the system
- Dedicated: The spare hard disk is dedicated to a redundant RAID group in the system.
4. The most important technologies in Raid areMirroring, striping, data verification, in order to avoid data problems caused by disk failure, you can set a hot spare disk to solve the problem that the system automatically replaces the faulty disk after a hard disk failure.
(2) Commonly used RAID analysis
1. RAID0: Striped disk array without fault-tolerant design, the data of the RAID group is evenly distributed among the disks in the form of stripes (for example: raw capacity: 12 blocks of 2T=24T; effective capacity: RAID0 (12 blocks of 2T ) = 24T; at least 2 blocks, no bad disks are allowed)
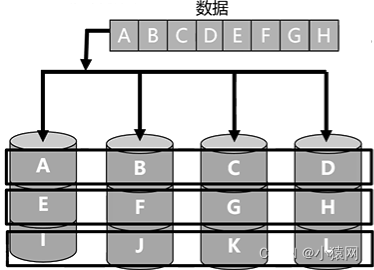
2. RAID1 is also called mirroring, and the data is written to the primary disk and the mirror disk at the same time (bare capacity: 12 blocks of 2T=24T; effective capacity: RAID1 (12 blocks of 2T)=12T ;Minimum 2 blocks, half of the disks are allowed to be damaged)
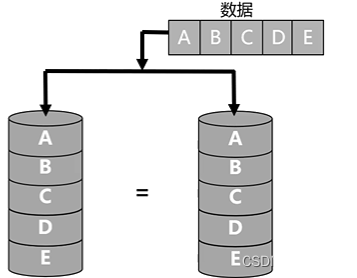
3. RAID3: Parallel data transmission array with parity, the data is striped and distributed in the data disk, while usingDedicated calibration disk to store calibration data(Bare capacity: 12 pieces of 2T=24T; effective capacity: RAID3(N-1)=22T; at least 3 pieces, allowing 1 bad disk) 4. RAID5:
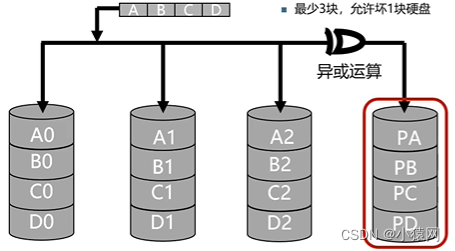
Similar to RAID3 mechanism, but the verification data is evenly distributed among each data On the hard disk, data and verification information are saved on the RAID member hard disk at the same time, and the data block and corresponding verification information are saved inon a different hard drive. RAID5 is one of the most commonly used RAID methods (bare capacity: 12 blocks of 2T=24T; effective capacity: RAID5 (N-1)=22T; at least 3 blocks, 1 bad disk is allowed)
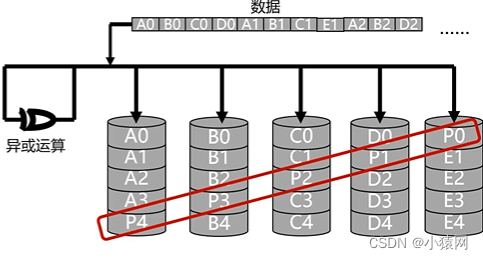
5. RAID6: Similar to RAID5, but There are two verification data (horizontal data, oblique data, such as one is P, one is DP) in one disk (bare capacity: 12 pieces of 2T=24T; effective capacity: RAID6 (N-2)=20T; at least 4 block, 2 bad disks are allowed)

6. RAID10: A RAID level that combines mirroring and stripes in two levels,The first level is a RAID1 mirror pair, and the second level is RAID0. RAID10 is also a widely used RAID level
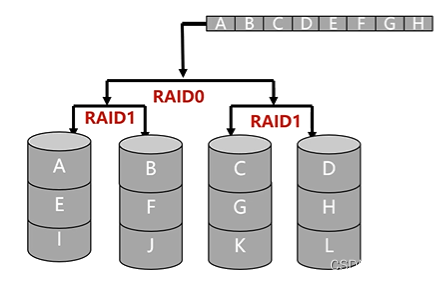
7, RAID50: a RAID level that combines RAID5 and RAID0 in two levels,The lowest level is RAID5, and the second level is RAID0.
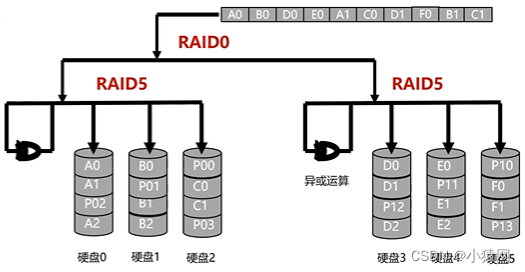
8. Common RAID technology comparison:
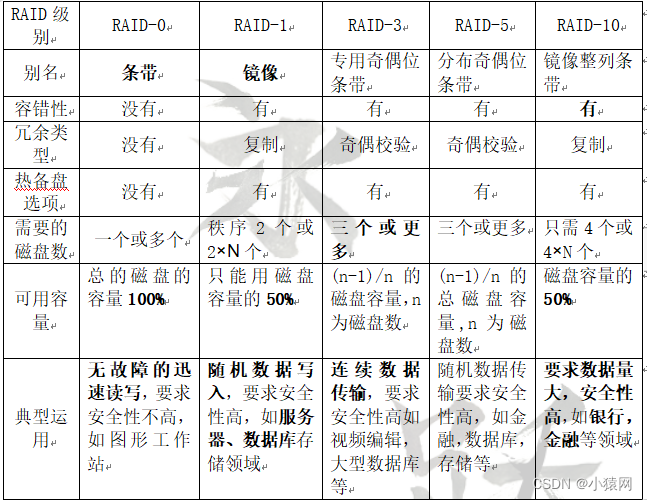
(3) RAID2.0 technology
1. Why there is RAID2.0
- Traditional refactoring is slow and affects performance
- Traditional RAID is limited by the number of disks
2. Comparison between traditional RAID and RAID2.0
3. RAID2.0 optimization - Rapid reconstruction (distributed distribution of hot spare space)
- Disk load balancing (distributed distribution of LUN space)
- Disk utilization (greatly improved performance, improved disk utilization)
- Storage management efficiency (storage pool is easy to expand, LUN easy to expand)
4. RAID2.0 technical description:
1) Reconstruction: In traditional RAID reconstruction, the data of the faulty disk can only be reconstructed and written to a hot spare disk . In the reconstruction of RAID 2.0, because the hot spare space is scattered on multiple disks, the bottleneck of writing to a single hot spare disk is avoided, so the reconstruction speed is very fast.
2) Disk load balancing: LUN data is evenly distributed to all disks in the array, which can prevent local disks from overheating and improve reliability
. The read and write performance of the LUN is greatly improved. In terms of capacity: the number of hard disks in the resource pool is not limited to the RAID level, eliminating the situation that some RAID groups have high space utilization and some RAID groups have low space utilization in the traditional RAID environment, and use intelligent thin provisioning to improve the capacity utilization of hard disks Rate.
4) Improve storage management efficiency: Based on RAID2.0 technology, there is no need to spend too much time on storage domain planning, just simply combine multiple hard disks into a storage pool, set the layering strategy of the storage pool, and divide from the storage pool LUN is enough; when it is necessary to expand the storage pool, just insert a new hard disk, the system will automatically adjust the data distribution, so that the data is evenly distributed to each hard disk; when it is necessary to expand the LUN, just enter the size of the LUN you want to expand , the system will automatically divide the required space from the storage pool, and automatically adjust the data distribution of the LUN, so that the LUN data is more evenly distributed to all hard disks.
5. Network storage system
(1) Storage protocol
1. The main storage protocol
- SCSI protocol: (Small Computer System Interface, small computer system interface) is an interface technology developed for minicomputers, used for the connection between the host and external devices. SCSI-3 is the basis of all storage protocols, and other storage protocols use the SCSI instruction set. advantage:Host-independent, multi-device parallel, high bandwidth. Disadvantages: The number of connected devices is small and the connection distance is very limited。
- FC protocol: FC is the abbreviation of Fiber Channel (Fiber Channel), which is used for the connection between servers and shared storage devices, and the internal connection between storage controllers and drives. It is a high-performance serial connection standard. Its interface transmission rate currently has several standards such as 4G, 8G, and 16G. The transmission medium can choose copper cable or optical fiber,Long transmission distance, supports a variety of interconnection topologies.Fiber Channel is the basis for constructing FC SAN, and is the hardware interface and communication interface of FC SAN system。
- iSCSI protocol: (Internet Small Computer System Interface) Internet Small Computer System Interface, is a standard for data block transmission on TCP/IP, which can be understood as SCSI over IP. iSCSI can be configured based onIP SAN, providing users with high-speed, low-cost, long-distance storage solutions. iSCSI encapsulates SCSI commands into TCP/IP data packets, so that I/O data blocks can be transmitted through the IP network.is the way of future development。
- SAS protocol: (Serial Attached SCSI) is the serial standard of the SCSI bus protocol,That is, serial connection SCSI; SAS uses serial technology to obtain higher scalability and is compatible with SATA disks. At present, the highest transmission rate of SAS is as high as 3Gpbs, 6Gbps,Support full duplex mode。
- Comparison of major storage protocols:
- 其他协议:SAN协议、AOE协议、FCOE、RDMA等
2、IP SAN把SCSI协议封装在IP协议中,这样只允许本机的SCSI协议可以通过TCP/IP网络发送
3、InfimniBand可以处理存储I/O、网络I/O,也能够处理进程间通信(IPC)
4、InfimniBand可以将磁盘阵列、SAN、LAN、服务器和集群服务器进行互联,也可以连接外部网络
5、FC网络架构: - 基本接口为N、F、E端口
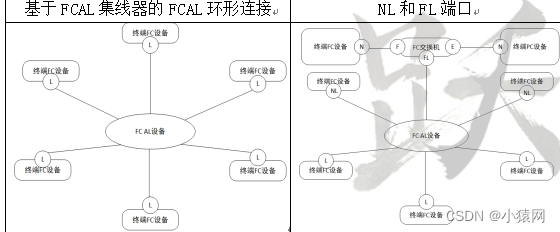
6、在延迟说法中,服务器延迟的主要是队列延迟和磁盘IO延迟
7、存储资源池建设中,目前主要可选的磁盘有SATA、SAS和SSD三种。适用于大、中型企业关键任务资料的存储的磁盘是SAS,适合高性价比,海量资源存储的是SATA,适合大批量,小数据库快,高随机读写频率的是SSD。这三种硬盘中,IOPS最高的是SSD。
8、IP-SAN和FC-SAN存储:
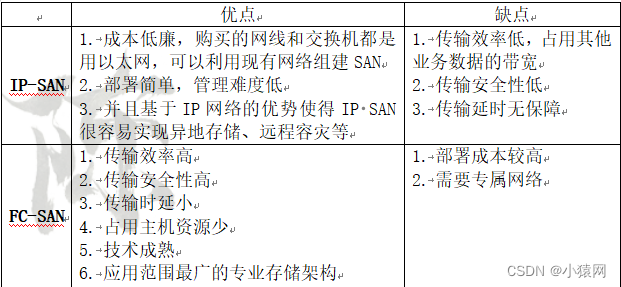
9、硬盘域可以由同种存储介质或不同存储介质的硬盘组成。同种存储介质的硬盘组成一个存储层,每一个存储层特点: - 高性能层是由SSD盘组成,性能最高,由于其存储介质成本较高且单盘容量小,适给存放访问频率很高的数据。
- 性能层是由SAS盘组成,性能较高,由于其存储介质成本适中且单盘容量较大,适合存放访问频率中等的数据。
- 容量层是由NL-SAS盘组成,性能最低,由于其存储介质成本最低且单盘容量大,适合存放大容量的数据以及访问频率较低的数据。
10、IP-SAN在服务器和客户机的数据通信中采用iSCSI命令传输,数据处理采用块级,而安全性和速度相对较高的FC-SAN在通信中是直接传输SCSI命令。FC-SAN最终将实现在异种Under the operating system, the maximum data sharing and data optimization management, as well as the seamless expansion of the system.
(2) DAS/SAN/NAS
1. Direct-attached storage (DAS) network-attached storage (NAS) storage area network and its protocol (SAN)
2. Storage development history: from being attached to the server to an independent system
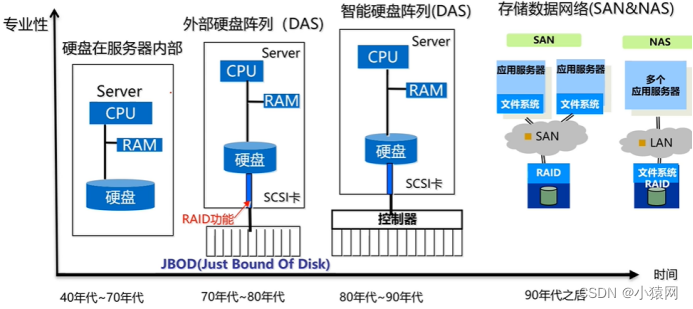
3. Origin of DAS
- Time: 70s
- Background: Users first had storage requirements due to the increase in the amount of data, resulting in the earliest and simplest storage architecture directly connected to the additional storage DAS.
- Connection method:FC、SCSI、SAS
- Access method: The connection channel between the direct-attached storage and the server host usually adopts SCSI connection
- Link rate: 20MB/s, 40MB/s, 80MB/s, 320M/s
- Provide snapshot, backup and other functions
4. FC SAN origin (from DAS to FC SAN) - Time: Mid to late 1990s
- Background: In order to solve the problem of poor scalability of DAS, storage devices are networked,Can connect to hundreds of servers at the same time
- Connection method:FC fiber,useDedicated FC switch[2G/4G/8G/16G]
- Access method: the storage space of the back-end storage device can be divided into multipleLUN, each LUN can only belong to 2 front-end servers
- Link rate: 2Gbps, 4Gbps, 8Gbps
- Provide advanced data protection functions such as snapshot and disaster recovery
5. Origin of IP SAN (from FC SAN to IP SAN) - Background: To solve FC-SAN inPrice and Managementmany thresholds above
- Connection method: useethernetas a connecting link,ethernet switch
- Access method: The storage space of a storage device at the back end can be divided into multiple LUNs, and each LUN can only belong to one front-end server
- Link rate:1Gbps、10、40、100Gbps,
- Provides advanced data protection functions such as snapshot and disaster recovery
6. Reasons why iSCSI is favored - Can adopt very mature IP network management tools and infrastructure
- IP networks are widely used, which can save a lot of construction, management and personnel costs for enterprises.
7. The origin of NAS (network data sharing and exchange requirements) - Time: Early 1990s
- Background: The rapid development of the Internet,Large amounts of data need to be shared and exchanged, a dedicated NAS storage device appears and becomesThe core of data sharing and exchange
- Access method: multiple front-end serverssharedBack-end storage device, the storage space on the back-end NAS device throughCIFS (window system), NFS (Linux system) protocolShared to the front-end host, the same directory or file can be performed at the same timeconcurrent read and write
- The file system resides on the backend storage device
- Link rate: 1Gbps, 10Gbps
8. Three kinds of storage networking, each with its own advantages and disadvantages.

9. SAN and NAS are not two competing technologies. They usually complement each other to provide access to different types of data. SAN forMassive block-oriented data transfer, while the NAS providesFile-level data access and sharing services. More and more data centers use SAN+NAS to realize data integration, high-performance access and file sharing services.
10. Example:
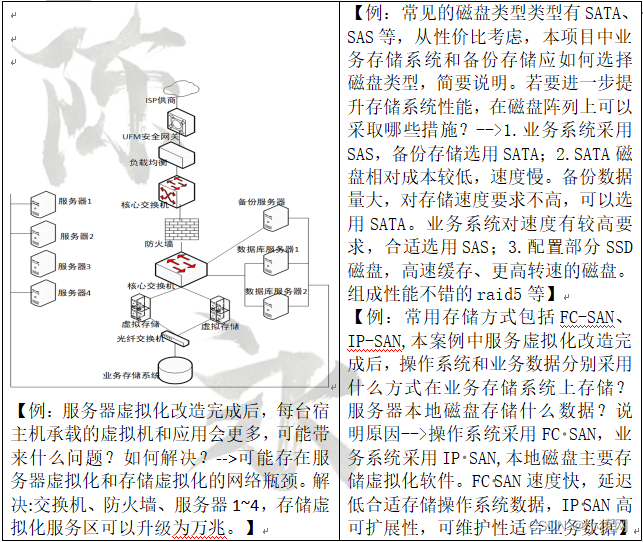
11. Example
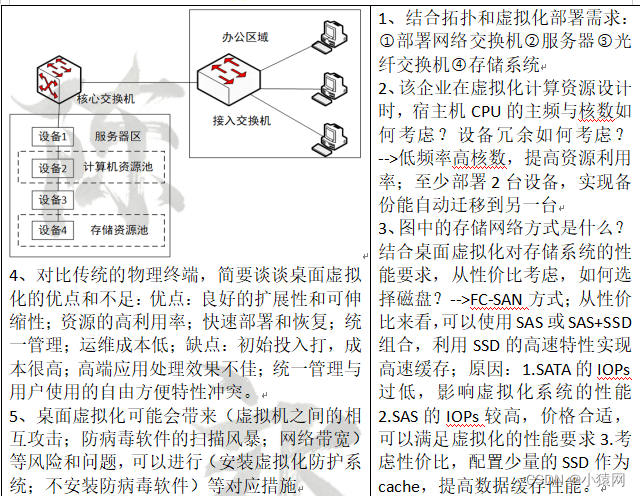
12. FC-SAN adopts FC protocol, uses dedicated fiber channel transmission, and maps the fiber channel device as a logical drive accessible to the operating system. When performing data transmission, the utilization rate of the fiber link is high. The transmission rate reaches above 4G. Its high performance, low latency, and high cost are suitable for business needs that require high data transmission speed and high performance.
13. IP-SAN uses the iSCSI protocol and uses IP network channel transmission. In the current general gigabit network environment, when data transmission is performed, the link utilization and transmission rate are much lower than FC channel transmission. Its low cost, good openness, strong network adaptability, easy remote data access, shared storage resources, and improved resource utilization are suitable for business needs such as low data access speed, large capacity, and low-cost investment. (For example, if two places 80km apart use the data center SAN of the headquarters, what is the reasonable choice of SAN technology?) Obviously, the sub-campus is 80Km apart, and the investment in using FC san is huge, and the more appropriate choice is IPsan.
14.FC SANFor an independent FC network, the server needs to be installedHBA card, connected to the optical fiber storage switch
15, common backup methods (Host-Base/LAN-Base/LAN-Free/Server-Free), LAN-Free and Server-Free backup are based on SAN.
6. Data protection technology
(1) Data backup
1. Business challenges
- Logical failure (80%): virus damage, deletion of data tables, misoperation, etc.
- Physical failure (12%): motherboard damage, hard disk failure, network card failure, etc.
- Extreme failure (8%): extreme natural disasters, power, energy failure
2, data backup:
1) Data backup (Backup) generally refers to the use of backup software (such as Veritas' NetBackup 40% share, EMC (Legato) Networker, CA BrightStor, etc.) put the dataBackup from disk to tape for offline storage(The latest backup technology also supports disk-to-disk backup, that is, the disk is used as a storage medium for backup data to speed up data backup and recovery).
2) The format of the backup data isTape format, not directly accessible by data processing systems. When the source data is damaged or lost, the backup data must be restored to usable data by the backup software before it can be accessed by the data processing system.
3) The composition of the backup system: - Backup software: complete the formulation of backup strategies, backup media management and other extended functions
- Backup media: tape library, disk array, virtual tape library, optical library/optical tower
- Backup server: a server used for safe backup software, and backs up data to backup media through the backup strategy pre-established by the backup server.
3. Backup media: disk array, tape library, virtual tape library, CD library. Virtual tape library and physical tape library have their own advantages and disadvantages, and they are complementary. In fact, the most fundamental reason is the legal requirements of various countries, making tape storage must exist. Then a virtual tape library was born to solve the shortcomings of tape storage.
4. Tape backup problem: - High failure rate of mechanical parts: The core components of the tape library, the manipulator and the tape drive, are mechanically vulnerable parts, which have a high failure rate, and unpredictable failures such as dust and moisture, resulting in poor equipment availability.
- Long backup/restore times: Mechanical actions such as tape grabbing, loading, and mechanical positioning of files prolong the waiting time. If multiple tapes are required to restore data, business continuity will be greatly affected.
- Backup Media Security: The tape is non-sealed media and there is no fault-tolerant containment between tapes in the library. Any disk in the tape group involved in the backup businessWear, tape, mildew, adhesionetc. will cause the entire backup system to be unrecoverable.
- Comparison of backup media:
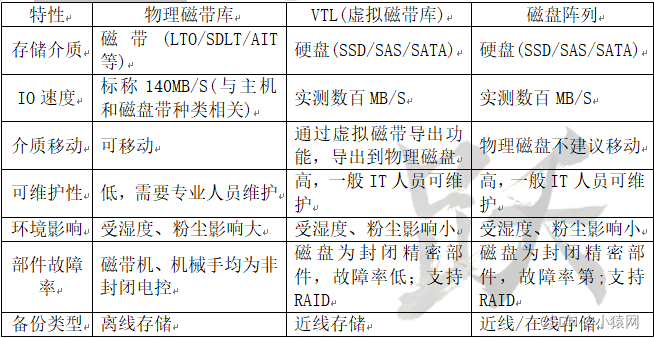
5. Advantages and disadvantages of different backups:
(1) Full backup: backup all data in the system - Advantages: shortest recovery time, most reliable, most convenient to operate
- Disadvantages: the number of backups is large, and the time required for backup is long
(2) Incremental backup: backup all data updated after the last backup - Advantages: less data is backed up each time, less space is occupied, and the backup time is shorter
- Disadvantages: full backup and multiple incremental backups are required for recovery
(3) differential backup: backup all data updated after the last full backup - Pros: Short data recovery time
- Disadvantages: The backup time is long, and full backup and differential backup are required for recovery.
6. Data replication technology: - Data backup generally refers to using backup software to back up data from disk to tape for offline storage.The backup data format cannot be directly accessed by the computer, and needs to be restored by backup software。
- Over time, backups also start using disks, but the data must be restored accordingly to be usable
- Data replication refers to the use of replication software to copy data from one disk to another to generate a data copy. thisThe data copy is directly accessible by the data processing system without any data recovery operations, This is the biggest difference between replication and backup
7. Continuous data protection technology (CDP): It can track data changes and store them independently of production data to ensure that data can be restored to any point in time. The continuous data protection system can be implemented based on blocks, files or applications, and can provide sufficiently fine-grained recovery efforts for recovery objects to achieve almost unlimited recovery time points.
8. The characteristics and application scenarios of the three data backup technologies of snapshot, remote replication and LUN copy: - snapshotThe implementation principle determines that this feature hasFast execution speed, small storage space occupied, fast recovery speed, etc.. Therefore, snapshots can be broadly应用于快速数据备份与恢复、数据持续保护、重新定义数据用途等场景。
- 在业务离线的情况下,可以使用LUN拷贝进行不同LUN之间的数据拷贝。LUN拷贝特性的典型应用场景包括数据迁移、数据快速分发和数据集中备份。
- 远程复制主要应用于数据的容灾备份,典型的业务应用场景包括中央容灾备份站点和两地三中心。不同的远程复制模式适用于不同的应用场景。同步远程复制:用于主站点和从站点距离较近的场景,如同城(相同的数据中心或相同校园中)容灾备份。异步远程复制:适合于主站点和从站点距离较远或网络带宽有限的场景,如异地(跨国家/地区,全球)容灾备
9、数据中心应该合理地划分为核心数据域、核心业务域、安全管理域三个安全域。
(二)数据容灾
1、容灾级别:
(1)数据容灾
- 建立一个异地数据系统对本地系统关键应用数据进行复制。
- 出现灾难导致应用系统数据损坏时,能够通过异地保存的数据进行灾难恢复。
(2)应用容灾 - 异地建立一套完整的、与本地数据系统相当的应用系统(AP/AA模式)
- 灾难出现后,远程应用系统可承担原有业务运行,必须有数据容灾作为基础。
(3)业务容灾 - 包含非IT系统:如办公地点、人员、设施等等。(地震案例/医院断网案例)
2、容灾和备份的区别 - 容灾就是尽量减少或避免因灾难的发生而造成的损失;备份是容灾的基础,将全部或部分数据集合从应用主机的硬盘或阵列复制到其它的存储介质的过程。
- 容灾不是简单的备份:真正的数据容灾就是要避免传统冷备份的先天不足,它能在灾难发生时,全面及时地恢复整个系统。
- 容灾不仅仅是技术:由于容灾所承担的是用户最关键的核心业务,其重要性勿庸置疑,因此也决定了容灾是一个工程,而不仅仅是技术。
3、数据保护解决方案: - 备份系统(数据备份):主要是一些逻辑错误,如操作失误、病毒、升级故障、软件缺陷、人为破坏
- 主数据中心(本地高可用容灾):主要是一些设备故障,如磁盘故障、应用中断、组件故障、数据损坏
- 同城数据中心(同城容灾):主要是数据中心故障,如网络问题、空调故障、电源故障、建筑火灾
- 异地数据中心(异地容灾):主要是区域性灾难,如恐怖行动、国内动乱、自然灾害
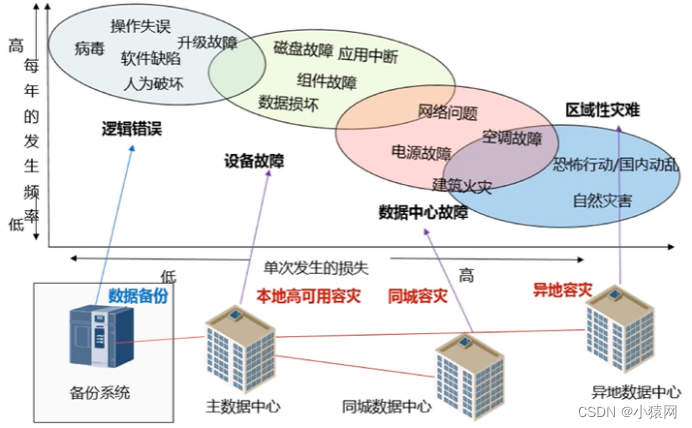
4、容灾三个指标: - RTO(恢复时间目标)指“将信息系统从灾难造成的故障或瘫痪状态恢复到可正常运行状态,并将其支持的业务功能从灾难造成的不正常状态恢复到可接受状态”所需时间,其中包括备份数据恢复到可用状态所需时间、数据处理系统切换时间、以及备用网络切换时间等,该指标用以衡量容灾方案的业务恢复能力。
- RPO(恢复点目标),RPO是业务系统所允许的灾难过程中的最大数据丢失量(以时间来度量),这是一个与数据备份系统所选用的技术有密切关系的指标,用以衡量灾难恢复方案的数据冗备份能力。
- 容灾半径:是指生产中心和灾备中心之间的直线距离,用以衡量容灾方案所能防御的灾难影响范围。同城灾备100KM内,一般40KM最佳。异地灾备一般100KM-400KM。
(三)双活与两地三中心
1、容灾发展方向
- 双活数据中心、两地三中心、分布式多活数据中心
- 业务系统支持:服务器、存储、网络、虚拟化、数据库、业务软件
2、两地三中心 - “两地三中心”是指同城双中心加异地灾备一种商用容灾备份解决方案,两地指同城和异地三中心指生产中心、同城容灾中心、异地容灾中心。
3、两地三中心优势 - 同城范围有效保证了数据的安全性和业务连续性;
- 异地复制数据根据灾难情形,尽可能降低数据丢失机率;
- 同城双中心为同步复制,数据实时同步,RPO=0;
- 异地无距离限制,保证数据一致性,保证了数据的有效保护;
第六章 网络安全
一、恶意代码
1、恶意代码的定义与分类
- Common features of malicious code: (1) have malicious purpose; (2) itself is a computer program. (3) Work through execution
- The main types of malicious code areComputer Viruses, Internet Worms, Trojan Horses, Backdoors, DDoS Programs, Bots, Rootkits, Hacking Tools, Spyware, Adware, Spam, and Pop-upswait.
2. Common malicious code types:
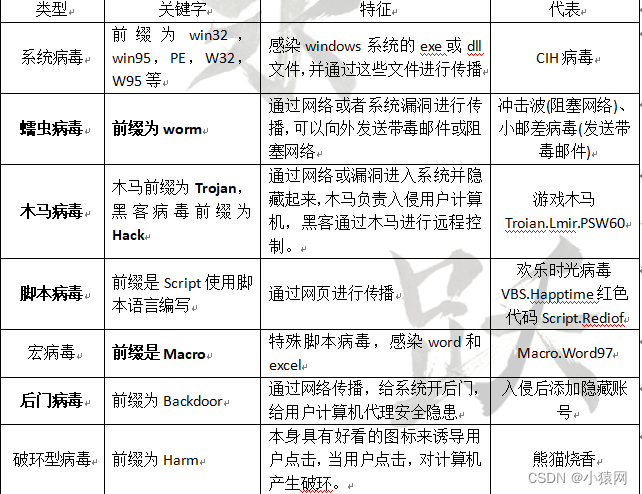
3. Typical malicious code - computer virus
1) Computer virus is one of the programs with the largest number and types of malicious code. The biggest difference between computer virus and other malicious code is thatComputer viruses can spread, and requires user action to trigger execution.
2) Computer virus features: infectious, procedural, destructive, unauthorized, concealed, latent, triggerable and unforeseeable.
3) The life cycle of a computer virus generally consists of the following four stages - (1)latent stage: Viruses are in a dormant state at this stage, and these viruses will eventually be activated by certain conditions (such as the date, the appearance of a specific program or specific file, and the capacity of the memory exceeding a certain range). Of course, not all viruses go through this phase.
- (2)propagation stage: The virus program copies itself to other programs or a certain area of the disk, or spreads to other computers, and each infected program or computer therefore contains a copy of the virus, thus entering the propagation stage.
- (3)trigger phase: After the virus is activated, it will perform a specific function to achieve a certain purpose. Like the virus in the incubation period, the trigger condition of the virus in the trigger stage is some system events, such as the number of times the virus can replicate itself, or the system date Or time, such as the CIH1.2 virus outbreak on April 26.
- (4)Seizure stage:病毒在触发条件成熟时,即可在系统中发作。由病毒发作体现出来的破坏程度是不同的,有些是无害的,有些则给系统带来巨大危害。
4、网络蠕虫:由于不需要用户干预来触发,因而其传播速度要远大于网络病毒。因而,其对网络性能产生的影响更为显著和严重
5、典型的反病毒技术有:特征码技术、虚拟机技术、启发扫描技术、主动防御技术、和病毒疫苗
(1)特征码技术:包含两个部分反病毒引擎和病毒特征库。特征值检测技术已被公认是检测已知病毒最简单有效的方法(最常用)。
(2)启发式扫描技术:主要是分析文件中的指令序列,根据统计知识判断该文件可能感染或者可能没有感染,从而有可能找到未知的病毒。因此,启发性扫描技术是一种概率方法,遵循概率理论的规律。
(3)虚拟机技术:启动虚拟机软件模拟模块,监视病毒的运行,待病毒自身的加密代码解码后,再运用特征值检测方法来识别病毒的种类。
(4)行为监控技术:病毒不论伪装得如何巧妙,它总是存在着一些正常程序不同的行为。例如,病毒总要不断复制自己,否则它无法传染。再如病毒总是要想方设法地掩盖自己的复制过程如不改变自己所在文件的修改时间等。病毒程序的伪装行为越多,它们露出的马脚就越多,就越容易被监测到。
(5)主动防御技术:不是一项全新的技术,集成了启发式扫描技术和行为监控及行为阻断等技术。
6、为系统打补丁,能有效预防蠕虫,但不能有效预防病毒
7、静态病毒和动态病毒: - 静态病毒是指存在于辅助存储介质上的计算机病毒,静态病毒不存在于计算机内存
- 能激活状态的病毒能借助截留盗用系统正常运行机制转变为激活态病毒,获得系统控制权
- 失活态病毒与静态内存的不同仅在于病毒代码存在于内存中,但得不到执行
二、网络攻击与防范
1. Hacker information collection and attack methods
(1) The main methods of information collection are as follows:
- (1) Network monitoring. A class of tools that quickly detect computer vulnerabilities in a network. Including sniffing application software, which can capture data information such as passwords in the transmission process within the computer or through the network.
- (2) Social engineering. Use manipulative techniques to obtain information, for example, asking for information such as passwords or account numbers during a beer conversation, or pretending to be another person to obtain information.
- (3) Public resources and garbage. Gather information from publicly available advertising material or even trash.
- (4) Backdoor tools. These are toolkits used to disguise the fact that computer security has been compromised.
(2) Hacking methods mainly include the following types:Denial of service attack, buffer overflow attack, vulnerability attack, spoofing attack.
(3) DOS and DDOS - Denial of service attack DOS:Consumes host CPU, memory, disk, networkand other resources, so that the host cannot provide services to normal users.
- Distributed denial of service attack DDOS: The attacker first invades and controls some computers, and then controls these computers to launch a denial of service attack to a specific target at the same time. Traditional denial of service attacks areLimited by network resources and poor concealment, two major disadvantages, and the distributed denial of service attack overcomes these two fatal weaknesses of the traditional denial of service attack.
(4) The three-level architecture generally adopted by DDOS - ==Client (client)==Run on the attacker's host, used to initiate and control DDoS attacks;
- ==Handler (main control terminal, springboard/proxy server)==runs on the host that has been invaded by the attacker and obtained control, and is used to control the proxy terminal;
- ==Agent (agent)==Runs on the host that has been invaded and controlled by the attacker, receives commands from the host, and is responsible for the actual attack on the target.
(5) Denial of service attack defense method: - Strengthen the feature recognition of data packets: Although the attacker has added camouflage or even encryption when conveying attack commands or sending attack data, there are still some characteristic strings in the data packets. By searching for these signature strings, the location of the attacking server and the attacker can be determined.
- Set up firewall to monitor localhost port usage. Monitor sensitive ports in the local host, such as UDP31335, UDP27444, and TCP27665. If these ports are found to be in the listening state, the system is likely to be attacked. Even if the attacker has modified the location of the port, if the external host actively initiates a connection request to a high-label port inside the network, the system is likely to be invaded.
- Statistics on the amount of communication data can also obtain information about the location and number of attacking systems. For example, prior to an attack, the target network's name servers often receive far more than normal numbers of reverse and forward address queries. During the attack, the source address of the attack data will send out a data volume that exceeds the normal limit.
- Fix the discovered problems and system vulnerabilities as much as possible。
- Deploy anti-DDOS system, or purchase anti-DDOS service(Remember this one, and understand the others).
(6) Buffer overflow attack and defense - Buffer overflow attack principle: by writing to the buffer of the program beyond its length, causing buffer overflow, so as to destroy the stack of the program and make the program execute other preset instructions in order to achieve the purpose of the attack. Buffer overflow is a very common and very serious vulnerability that exists widely in various operating systems.
(7) Buffer overflow attack defense: - Preventive strategies for system management: shut down unnecessary privileged programs, patch program vulnerabilities in time。
- Preventive Strategies in the Process of Software Development
a) Write correct code to ensure that the data in the target buffer does not cross the boundary;
b) Program pointer integrity check, if the program pointer is maliciously changed, the program refuses to execute;
c) Improve the hidden danger of buffer overflow attack in C language function library;
d) Use the compiler to separate the storage address of the function address pointer in the static data segment from the storage address of other data.
(8) Program loopholes and defenses - Vulnerabilities are in hardware, software, protocolDefects in specific implementations or system security policies, so that an attacker can access or destroy the system without authorization. In a sense, program errors are almost inevitable. Any small negligence and fallacies of software developers will give intruders an opportunity.
2. Common Web vulnerability attacks:CGI漏洞攻击、SQL注入、跨站脚本。
1)CGI漏洞攻击:CGI即公共网关接口,在Web服务器上定义了Web客户请求与应答的一种方式,是外部扩展应用程序(如per|脚本)与WWW服务器交互的一个标准接口。只要CGI脚本中有一点安全方面的失误,如口令文件、私有数据以及任何其他敏感内容,就能使入侵者方便地侵入到计算机。
2)CGI脚本漏洞防范的主要方法如下: - (1)使用最新版本的Web服务器,安装最新的补丁程序,正确配置服务器。
- (2)按照帮助文件正确安装CGI程序,删除不必要的安装文件和临时文件。
- (3)使用安全有效的验证用户身份的方法。
3)SQL注入与防范: - SQL注入攻击:黑客从正常的网页端口,进行网站访问,通过巧妙构建SQL语句,获取数据库敏感信息,或直接向数据库插入恶意语句。
- 对用户输入做严格检查,防止恶意SQL输入;
- 部署DBS数据库审计系统、WAF防火墙,进行安全阻断。
4)XSS跨站脚本攻击防范思路 - ==不信赖用户输入,对特殊字符如”转义,可以从根本上防止这一问题;
- 部署WAF网页应用防火墙,自动过滤攻击报文==。
- XXS将恶意代码嵌入到用户浏览的web网页中,从而达到恶意的目的
3、TCP/IP协议栈攻击与防范 - Ping of Death攻击:早期windows系统,ping大于65536(64K报文)的数据包直接蓝屏死机。
- Teardrop攻击:恶意修改IP分组的偏移量,导致数据不能正常重组,缓冲区溢出导致系统崩溃。
- WinNuke攻击:是一种拒绝服务攻击。WinNuke攻击又称带外传输攻击,它的特征是攻击目标端口,被攻击的目标端口通常是139、138、137、113、53、而且URG位设为“1”,即紧急模式。
- Land攻击:SYN包中的源地址和目标地址都被设置成某一个服务器地址,这时将导致接受服务器向它自己的地址发送SYN+ACK消息,结果这个地址又发回ACK消息并创建一个空连接,每一个这样的连接都将保留直到超时。对Land攻击反应不同,许多UNIX实现将崩溃,而Windows会变得极其缓慢。
- 预防措施:及时打补丁,部署防火墙,安装终端防护软件等。编程时提高代码质量,减少安全漏洞。
4、端口扫描 - 端口扫描的目的:(1)判断目标主机上开放了哪些服务(2)判断目标主机的操作系统。
- 原理:尝试与目标主机的某些端口建立连接,如果目标主机该端口有恢复(三次握手的第二次),则说明该端口开放,即为“活动端口”。端口扫描分类:

5、欺骗攻击与防御–ARP欺骗 - ARP欺骗原理:攻击者发送恶意ARP应答信息,刷新被攻击者ARP缓存,让对方不能正常二层封装。
- ARP欺骗的防范措施
- ==(1)在主机上进行ARP静态绑定,例如:arp -S 10.0.0.254 00-11-d8-64-6b-bc;
- (2)主机和服务器采用双向绑定的方法解决并且防止ARP欺骗。
- (3)使用ARP服务器。通过该服务器查找自己的ARP转换表来响应其他机器的ARP广播。确保这台ARP服务器不被黑==。
6、欺骗攻击与防御–DNS欺骗 - DNS欺骗首先是冒充域名服务器,然后把查询的IP地址设为攻击者的IP地址,这样,用户上网就只能看到攻击者的主页,而不是用户想要取得的网站的主页了,这就是DNS欺骗的基本原理。DNS欺骗其实并不是真的“黑掉”了对方的网站,而是冒名顶替、招摇撞骗罢了。
- 防范措施:被动监听检测、虚假报文探测、交叉检测查询三种
7、所谓网络安全漏洞是指:网络节点的系统软件或应用软件在逻辑设计上的缺陷.
8. The reason why the ARP attack causes the network to fail to communicate across network segments is: the forged gateway ARP message makes the data packet unable to be sent to the gateway.
9. Active defense is a new type of anti-virus technology, the principle of which is (Identify virus programs based on specific behavior and prevent them from running)
10. The idea of physical isolation is:Separate the internal and external networks, but write and read a storage device in real time, and indirectly realize information exchange.
11. The main technologies for isolating the gatekeeper are: real-time switch technology; one-way connection technology; network switch technology
12. Measures should be taken at the place where the worm virus breaks out, such as: disconnection investigation; upgrade system patch; repair system loopholes; isolate infected hosts Prohibit access to the network; install anti-virus software
13. Measures to be taken for remote command execution vulnerabilities: upgrade vulnerability patches; deploy related equipment or software that can block remote commands
14. Measures to be taken for cross-script attacks: reasonably filter user input and control; deploy a web defense system that can prevent XSS
15. Benefits of deploying a vulnerability scanning system: Periodically scan for security vulnerabilities on devices and servers in the network, discover security vulnerabilities, update patches in a timely manner, and implement security management in Security operation and maintenance requirements.
16. SQL injection attacks, reasonable solutions are: strictly check the type and format of input variables, and perform strict verification; filter and escape special characters; use the pre-compilation mechanism to deploy WAF before the corresponding service.
17. Phishing attacks. Preventive measures against phishing attacks need to be considered from two perspectives: (1) Strengthen security awareness management so that all employees have a strong security awareness; (2) Strengthen security technology prevention, Set up corresponding security protection software in the network, and install corresponding virus killing and security protection software on user computers; (3) Standardize the corresponding security management system.
18. Commonly used DDOS attack prevention methods: (1) Purchase carrier traffic cleaning services; (2) Purchase anti-DDOS equipment; (3) Repair system vulnerabilities and close unnecessary open ports; (4) Purchase cloud acceleration services; ( 5) Increase export bandwidth and improve hardware performance; (6) CDN acceleration
19. [Example: With the rapid development of computer-related technologies, briefly explain the main application directions of network security in the next ten years. –>IPv6 network security; control network security; cloud security; artificial intelligence security; quantum encryption】
3. Firewall & IDS/IPS
1、防火墙可以实现内部网络(信任网络)与外部不可信任网络(Internet)之间或是内部网络不同区域隔离与访问控制,防火墙隔离四大区域:内网、外网、DMZ、Local;
2、防火墙技术与分类:包过滤、状态化防火墙、应用层网关、应用层检测DPI。
3、防火墙技术分类:
- 包过滤(packet filtering)型防火墙。工作在OSI网络参考模型的网络层和传输层,它根据数据包头源地址、目的地址、端口号和协议类型等标志确定是否允许数据包通过。只有满足过滤条件的数据包才被转发到相应的目的地,其余数据包则被从数据流中丢弃。
- 应用层网关防火墙。应用层网关(Application Level Gateways)防火墙是在OSI/RM应用层上建立协议过滤和转发功能。它针对特定的网络应用服务协议使用指定的数据过滤逻辑,并在过滤的同时,对数据包进行必要的分析、登记和统计,并形成报告提供给网络安全管理员作进一步分析。
- 代理服务型防火墙。代理服务型(Proxy Service)防火墙是针对数据包过滤和应用层网关技术存在的缺点而引入的防火墙技术,其特点是将所有跨越防火墙的网络通信链路分为两段。防火墙内外计算机系统间不能直接连接,都要通过代理服务型防火墙中转连接。外部计算机的网络链路只能到达代理服务型防火墙,从而起到了隔离防火墙内外计算机系统的作用。
4、防火墙的经典体系结构主要有三种形式双重宿主主机体系结构、被屏蔽主机体系结构和被屏蔽子网体系结构。
5、入侵检测系统的分类: - 按信息来源分类:HIDS/NIDS/DIDS(主机/网络/分布式)
- 按响应方式分:实时检测和非实时检测
- 按数据分析技术和处理方式分:异常检测、误用检测和混合检测
- 异常检测:建立并不断更新和维护系统正常行为的轮廓,定义报警阈值,超过阈值则报警能够检测从未出现的攻击,但误报率高
- Misuse detection: extract known intrusion behavior features to form an intrusion pattern library, and alarm if matchedThe accuracy of known intrusion detection is high, and the accuracy of unknown intrusion detection is low, highly dependent on the signature database expert system and pattern matching
6. Intrusion Prevention System IPS - Definition: Intrusion prevention system is a preemptive network security detection and defense system,Ability to detect attacks and respond proactively。
- IPS not only has the ability of intrusion detection system to detect attack behavior, but also has the function of intercepting and blocking attacks.
- IPS is not a simple combination of IDS and firewall functions. IPS adopts an active, comprehensive and in-depth defense in response to attacks.
- IPS detection technology:Feature-based matching technology, protocol analysis technology, anti-DDOS/DOS technology, intelligent detection technology honeypot technology.
7. Intrusion Prevention System IPS & Intrusion Detection System IDS - The deployment location is different:IPS general serial deployment, IDS general bypass deployment。
- Different intrusion response capabilities:IPS can detect intrusions, and can actively defend and block ongoing attacks. IDS can only detect and record logs and issue alarms
8. The advantages of deploying the intrusion detection system in the DMZ are: - You can view the status of hosts in the protected area being attacked
- It can detect whether the policy configuration of the firewall system is reasonable
9. Functions in the intrusion detection system :- Assess the integrity of critical system resources and data files
- Identify known attacks
- Statistical analysis of abnormal behavior
10. The basic model of intrusion detection is the PDR model, which is the earliest network security model that embodies the idea of active defense. PDR models includeProtect, Detect, Respondthree parts.
11. (1) Firewall: establish a defense system to isolate the local and external networks through the firewall; (2) IDS/IPS: monitor all communications and find possible malicious attacks, and prevent malicious attacks; (3) Deploy identity authentication server: manage Personal identity authentication information to achieve legal login; (4) Realize the isolation of monitoring network and information network: physical isolation, blocking attacks, eliminating Internet traffic, and improving efficiency.
12. Necessity and deployment of IDS: Necessity: IDS is mainly used to prevent attacks from the internal network, and it can also prevent attacks from the periphery after the firewall fails or is breached. It is an important technology in enterprise network security. On-Premises: Usually placed inLocations that need to be protected in the internal network, such as server farms and other core departments.
13. The entire network is divided into three different levels of security areas: - Internal network: the highest security level, credible and key protection area. Including all internal hosts, database server, DHCP server and FTP server.
- External network: the lowest level of security, untrusted, and areas to be guarded against. Includes external Internet user hosts and devices.
- DMZ area (demilitarized zone): The security level is medium, because some specific services and applications need to be opened to the outside world, and it is protected to a certain extent, and it is an area with a low security level. Including Web servers, mail servers and streaming media servers that provide WWW access to the outside world.
14. In the network - The preventive measures that can be deployed by the firewall include: access control, NAT, DDoS attack detection and prevention
- The preventive measures that can be deployed on IDS include: Packet inspection and analysis
- The preventive measures that can be deployed on the IPS include: abnormal traffic blocking, vulnerability scanning
4. Access Control and IPSec VPN
1. Access control includes three elements: subject, object and control strategy.
- Subject: is the subject entity that can apply actions to other entities
- Object: is a passive entity that is accessed by other entities
- Control strategy: It is the set of operation behaviors and constraints set by the subject on the object.
2. Access control includesCertification, Control Policy Implementation and Auditingthree aspects - Authentication: The identification and authentication of the subject to the object and the inspection and authentication of the object to the subject, the authentication relationship between the subject and the object is mutual.
- The specific implementation of the control strategy: how to set the rule set to ensure the legal use of information resources by normal users, not only to prevent illegal users, but also to consider the leakage of sensitive resources. For legitimate users, they cannot exceed their authority to perform functions other than the rights granted by the control policy.
- Auditing: The manager of the object, that is, the administrator, has the right to operate, and he may abuse this right, which cannot be constrained in the policy. These actions must be recorded, so as to achieve the purpose of deterrence and ensure the normal implementation of access control.
3. The role of ACL: - Can limit network traffic and improve network performance. For example, the priority of the data packet can be specified according to the protocol of the data packet.
- Provides control over traffic flow. For example, the length of routing update information can be limited or simplified, thereby limiting the communication flow through a certain network segment of the router.
- Basic means of providing secure access to the network. For example, host A is allowed to access a resource network, while host B is denied access.
- Which type of traffic is forwarded or blocked can be determined at the router port. For example, users can allow E-mail traffic to be routed and deny all Telnet traffic.
4. Traditional access control technology
1) Autonomous access control (DAC) - Allow legal users to access the objects stipulated by the policy as users or user groups, while preventing unauthorized users from accessing objects, and some users can also independently grant access rights to objects they own to other users.discretionary access control. Linux, UNIX, Windows NT or Server operating system
2) Mandatory access control (MAC) - In the beginning, in order to implement a stricter access control strategy than DAC, the US government and military developed various control models, and these programs or models have relatively complete and detailed definitions. The one-way flow of information is achieved through the graded security label, so it has been adopted by the military.
- The most famous ones are the Bell-LaPadula model and the Biba model.The Bell-LaPadula model has the characteristics of only allowing downward reading and upward writing,Can effectively prevent confidential information from leaking to subordinates;The Biba model has the characteristics of not allowing downward reading and upward writing, can effectively protect the dataintegrity.
3) Role-Based Access Control (RBAC) - The basic idea is to assign access permissions to certain roles, and users can obtain the access permissions of roles by playing different roles.
5. PPP, PPTP, L2TP technology comparison summary
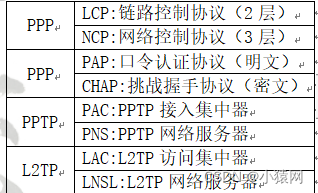
6. PPP inLCP:Used to establish and configure data links;NCP: Used for protocol network layer parameters, encapsulating multiple protocols, such as dynamically assigning IP addresses, etc.
7. CHAP is a secure authentication protocol, the challenger should beconnecting party.
8. PPP is an encapsulation protocol for connecting to WAN, which can control the establishment of data links; can allocate and manage IP addresses of WAN; can effectively perform error detection 9. PPP is a data link layer protocol
: - MRUforNegotiate the maximum packet transmission capacity of the PPP link, the local end notifies the peer end of the receivedMaximum message length。
- ACCMis inNotify the peer on the asynchronous link which characters are used by the local for control。
- Magic NumberIt is a magic word used for both sides of the negotiation. The magic words at both ends cannot be repeated. It can be used forDetect the loopback of the link。
- ACFCforNegotiate whether the address and control field of PPP packets can be compressed.
10. Virtual private network: a communication network established on the public network and dedicated to a certain organization or a certain group of users - Layer 2 VPN: L2TP and PPTP (based on PPP), PPTP relies on TCP/IP
- Layer 3 VPN: IPSec and GRE
- Layer 4 VPN: SSL and TLS
11. IPSec is a set of protocols defined by IETF to enhance the security of IP networks.
12. The IPSec protocol set provides the following security services: data integrity, authentication, confidentiality, application transparent security - IPSec functions are divided into three categories:Authentication Header (AH), Encapsulating Security Payload (ESP), Internet Key Exchange Protocol (IKE)
- Authentication header (AH):Provides data integrity and data origin authentication, but does not provide data confidentiality services MD5, SHA
- Encapsulating Security Payload (ESP):Provide data encryption function, encryption algorithms include DES, 3DES, AES, etc.
- Internet Key Exchange Protocol (IKE): forGenerate and distribute in ESPand the key used in AH

13. Two encapsulation modes of IPSec:
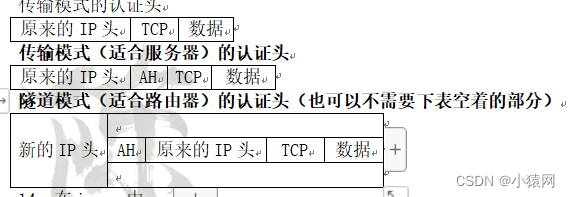
14. In ipsec: - ESP supports the confidentiality of data, using DES, Triple-DES, RC5, RC4, IDEA and other algorithms.
- AH can provide data source authentication (ensure that the received data is from the sender), data integrity (ensure that the data has not been changed), and anti-relay protection (ensure the integrity of the order in which data arrives)
- IPSec is a protocol system consisting of two parts: the key exchange protocol for establishing a secure packet flow and the protocol for protecting the packet flow. The former is the IKE protocol, and the latter includes the AH and ESP protocols.
- IPSec is a standard third-layer security protocol, which is a protocol package.
15. When IKE dynamic negotiation is used to establish an IPSec tunnel, there are two types of SA: IKE SA and IPsec SA. The difference between the two SAs is:The role of IKE SA is to negotiate a set of security parameters used to protect IPsec tunnels,andThe purpose of IPSec SA is to negotiate the security parameters used to protect user data,In IKE dynamic negotiation mode, IKE SA is the basis, the establishment of subsequent IPSec SAs is completed using a series of keys established by the IKE SA.
16. IPSec VPN is a commonly used VPN technology at present, and its application scenarios are divided intosite-to-site, end-to-end, end-to-site。 - 1)Site-to-Site. Site-to-site is also known as gateway-to-gateway,Multiple remote institutions use the operator's network to establish IPSec tunnels, to connect their respective internal networks.
- 2)End-to-End, also known asRemotelyaccess. end-to-end akaPC to PC,Right nowCommunication between two PCs is done by IPSec. Usually through a form of remote access, resume ad hoc connections. Such as establishing through PPTP vpn, SSL-vpn, etc.temporary connection
- 3)End-to-Site. end-to-site, byThe IPSec session between the gateway and the remote PC is completed. Here, the branch office is used as the site, and the headquarters network is used as the site. It is necessary to establish a site-to-site VPN. In this way,IPSec VPN can only work in queue mode.
17. The technologies mainly used in VPN are: identity authentication technology, data encryption technology, key management technology, tunnel technology, etc. The mainstream VPN tunnel technology includes Layer 2 L2TP, PPTP and Layer 3 IPsec.
18. VPN refers toTemporary, secure connections established by users over public networks。
5. Principles and applications of cryptography
(1) Overview of Network Security
1. Types of network security threats (understand):
- (1)tapping: Such as wiretapping, installing communication monitors and reading information on the Internet, etc.
- (2)counterfeit: Impersonation occurs when an entity conducts online activities masquerading as another entity.
- (3)replay: Repeat a message or part of a message to produce an authorized effect.
- (4)Traffic Analysis: Observing and analyzing online information flow to infer useful information transmitted online.
- (5)data integrity breach: Intentionally or unintentionally modify or destroy information systems, or modify data in an unauthorized and unmonitorable mode.
- (6)denial of service: When an authorized entity cannot obtain due access to network resources. SYN-Flooding
- (7)Unauthorized use of resources: That is, usage inconsistent with the defined security policy.
- (8)Trapdoors and Trojan Horses: By replacing the legal program of the system, or inserting malicious code into the legal program,
2. Network attack: - ==Passive attack: typically monitoring, the most difficult to be detected, the focus is on prevention, the main means is encryption
- Active attack: counterfeiting, replay, spoofing, message tampering and denial of service. The focus is on detection rather than prevention. The means include firewalls, IDS and other technologies ==
- Physical proximity attack: preventing outsiders from entering the computer room
- Insider Attacks: Insider Infiltration, Kuomintang-Communist War of Resistance, Internal Disintegration
- Distribution attack: the software is tampered with before it is installed after being developed
3. Security measures and goals - Access control
- Authentication: identity authentication, message authentication
- Integrity: Ensuring that the information received is consistent with the information sent
- Audit: non-repudiation
- Confidentiality: Ensure that sensitive information is not disclosed
- 基本安全技术:数据加密、数字签名、身份认证、防火墙、入侵检测、内容检查
4、ISO7498-2描述了5种安全服务:鉴别、访问控制、数据保密、数据完整性和防止否认
5、ISO7498-2描述了8种特定的安全机制:加密机制、数据完整性机制、访问控制机制、数据完整性机制、认证机制、通信业务填充机制、路由控制机制、公证机制
6、ISO7498-2描述了5种特定普遍性的安全机制:可信功能、安全标号、事件检测、安全审计跟踪、安全恢复
7、SSL的子协议主要有记录协议、警告协议和握手协议,其中握手协议用于产生会话状态的密码参数,协商加密算法及密钥等。
8、SSL是处于应用层和传输层之间,是一个两层协议。
(二)密码学原理
1、密码学原理:
- 加密:指一个过程,将一组信息(或称明文)经过密钥及加密函数的转换,变成读不懂的密文。
- 解密:接收方则将此密文经过解密密钥和解密函数还原成明文。
- 现代密码理论的一个根本性原则Kerckhoffs原则,即密码体制的安全性不依赖于算法的保密,而仅仅依赖于密钥的保密。
2、对称加密算法(也叫共享密钥加密算法):加密和解密密钥一样,典型算法有DES、3DES、AES、RC4、IDEA。
3、对称加密的安全使用要求: - 需要一个强加密算法
- 发送者和接收者必须通过一个安全的方式获得密钥并且保证密钥安全
4、对称加密的安全取决于密钥的保密性而非算法的保密性。密钥管理和分发难。
5、Diffie-hellman功能是密钥交换。
6、非对称加密算法(也叫公钥加密算法):加密和接密密钥不一样 - The public key cryptosystem has two keys, one can be used to encrypt data, called the public key; the other is used to decrypt, called the private key. The private key is kept secret and the public key is made public.
- Public key encryption, private key decryption (applied to data encryption transmission) private key encryption, public key decryption (applied to digital signature)
- Public key cryptography solves the problem of non-contact secure communication on insecure channels, essentiallyResolved issue with insecure channel key distribution。
- The most commonly used public key algorithms areRSA and DH.
7. InEnsuring data security while taking into account the efficiency of the key algorithm, the most suitable encryption algorithm is (RC-5).
8. In the SET protocol, the default use (OF THE) Symmetric encryption algorithm
9. The SSL protocol consists of upper and lower layers, and the lower layer is (SSL Record Protocol).
10. Digital certificates are identity proofs for information exchange and business activities on the Internet.
11. [Example: A website has applied for a data certificate from the CA, and the user passesCA's signatureTo verify the authenticity of the website. When users communicate securely with the site, users canThe public key in the certificate is encrypted and verified, the site passesWebsite's private key to decrypt and sign】
12. The security of the RSA algorithm based on the principle of number theory is based on (The difficulty of factoring large numbers) basis. RSA is widely used inprivate key distribution.
13. The most common implementation method of digital signature is based on (Public Key Cryptosystem and One-way Secure Hash Function Algorithm) based on the combination.
14. According to the processing method of the cipher system to the plaintext, the cipher system can be divided into (block ciphers and sequence ciphers) - Block cipher system: The ciphertext is only related to the encryption algorithm and key.
- Sequence cipher system: In addition to the encryption algorithm and key, the ciphertext is also related to the position of the encrypted plaintext part in the entire plaintext.
15. Personal digital signature system usually includes two parts: applying signature and verifying signature.
16. Formake up WEPAmendments enacted, definingAES-based encryption protocol CCMP, the algorithm requires high hardware.
17. The most common implementation method of digital signature is based onPublic Key Cryptosystem and One-way Secure Hash Function Algorithmbased on the combination.
18. The most common implementation method of digital signature is based onCombination of public key cryptosystem and one-way secure hash function algorithmbased on.
(3) Network security application
1. Message digest Hash (hash function) MD5 SHA
- Convert a piece of data (arbitrary length) into a piece of fixed-length data through one calculation.
- ==Irreversibility (one-way)== It is almost impossible to deduce the original text through the Hash result, that is, it is impossible to deduce x through the Hash value of x
- Collision freeIt is almost impossible to find a y such that the hash value of y is equal to the hash value of x
- avalanche effectThe input changes slightly, and the Hash output value changes greatly.
2. Digital signature: Bob Alice sends aMessage encrypted with own private key. When A1ice receives the ciphertext, she finds that she can decrypt it with Bob's public key, thus proving that the message was indeed encrypted by Bob. In this way, the entire encrypted message becomes a digital signature. Furthermore, since it is impossible to tamper with the message without Bob's private key, the digital signature not only authenticatesmessage origin, which also guarantees data integrity.
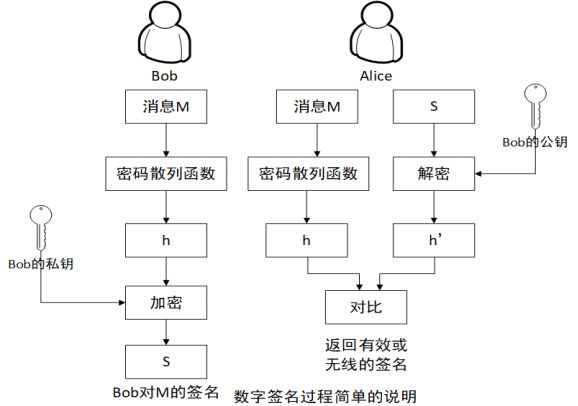
3. Data encryption methods are divided into three types: link encryption, node encryption and end-to-end encryption 4.
[Example: Give some appropriate suggestions for the deployment of security equipment in a city's metropolitan area network: there are security flaws; because the network lacks For active defense capabilities, an appropriate amount of supporting security facilities such as intrusion detection, vulnerability scanning, and WAF should be added. 】
(4) PKI and Kerberos
- 1. User/end entity: Refers to the customer who will apply for a digital certificate from the certification authority, which can be an individual, a group or a group, a government agency, etc.
- 2. Registration agency RA: The registration authority provides an interface between the user and the CA, which obtains and authenticates the user's identity, and submits a certificate request to the CA. It mainly completes the functions of collecting user information and confirming user identity. Registration agencies do not issue certificates to users, but only conduct qualification examinations on users. For smaller institutions, the CA may concurrently serve as the RA.
- 3. Certificate Authority CA: Responsible for issuing certificates to users.
- 4. Certificate issuance system:Responsible for certificate issuance, such as through the user itself or through the directory service.
- CRL library: Certificate revocation list, storing expired or invalid certificates.
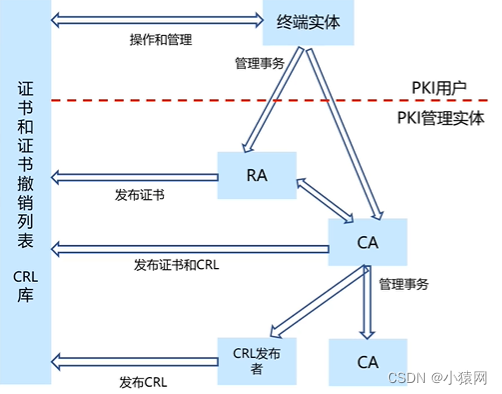
2. Keberos system architecture
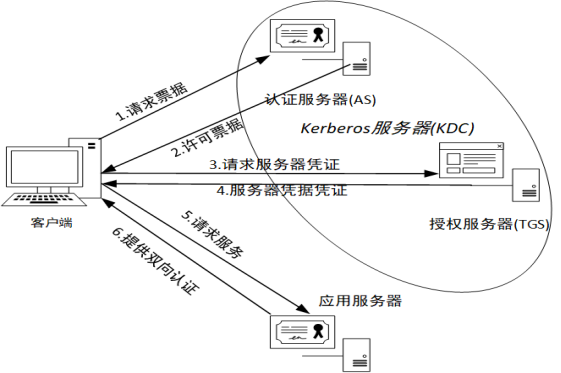
3. The one responsible for generating and signing data certificates is: the certificate authority CA; the one responsible for verifying the identity of users is the registration authority RA; 4.
The functions of the PKI CA certification center include: (certificate issuance, certificate review, certificate backup) - Receive and verify applications for end-user digital certificates
- Issue or deny digital certificates to applicants
Generate and publish the certificate revocation list (RL), which is used when verifying the certificate status 5 and Kerberos for key distributionAES、DESEquivalent symmetric key encryption.
6. The person responsible for verifying the identity of the user is (Registration AuthorityRA),Internet equipmentIt is not possible to apply for digital certificates in the PKI system.
7. Kerberos adopts a single-key system design; there is no CA server for authentication services, only AS and TGS servers.
6. System security and security management
(1) Physical security and system security
1. The environmental safety of the computer room should be considered from three aspects:
- One is natural disasters, physical damage and equipment failure;
- The second is electromagnetic radiation, taking advantage of opportunities, leaking traces, etc.;
- The third is operational errors, accidental omissions, etc.
2. Safe and reliable power supply - Large computer roomMultiple redundant power supply。
- In order to improve the reliability of the power supply and distribution system of the equipment in the computer room, add AC at the front end of the power distribution equipmentUninterruptible Power System UPS, To achieve reliable and uninterrupted power supply, stable quality and no interference.
- There are two types of grounding in the equipment room: system grounding and shielding grounding. System grounding includes the following four types of grounding.
3. Select the appropriate transmission medium: - The physical network infrastructure includesChoice of physical media and network topology. Physical security controls are controls over physical infrastructure, physical equipment security, and physical access.
- Shielded twisted pair has stronger anti-interference ability, and it is required to be equipped with connecting devices that support the shielding function and to have good grounding (preferably multiple grounding). For areas with severe interference, shielded twisted-pair cables should be used and placed in metal pipes to enhance anti-interference ability.
- Optical fiber is the most efficient way for ultra-long-distance and high-capacity transmission systems, From the analysis of transmission characteristics, no matter what kind of optical fiber, it has transmission frequency bandwidth, high speed, low transmission loss, long transmission distance, good anti-lightning and electromagnetic interference, good confidentiality, and is not easy to be eavesdropped or intercepted. The bit error rate is very low, high reliability, small size and light weight. Unlike twisted pair or coaxial cables, optical fibers do not radiate energy, effectively preventing eavesdropping.
4. Host system security: - Host system security mainly includesOperating system security, database system security, system access control security, security audit and host operation security。
- Host system security mainly includesIdentity authentication, autonomous access control, mandatory access control, security audit, system protection, remaining information protection, intrusion prevention, malicious code prevention and resource control.
5. DMZ area: - DMZ is to solve the problem after installing the firewallThe problem that the external network cannot access the internal web serverand set up a non-safety system and a safe system betweenbuffer zone。
- This buffer zone is located in the small network area between the internal network and the external network of the enterprise. In this small network area, someServer facilities that must be disclosed,likeEnterprise Web Server, FTP Server and Forumwait. The entire internal network that needs to be protected is connected behind the port of the trust zone, and no access is allowed to realize the separation of internal and external networks to meet user needs.
6. The disaster recovery of the database belongs to (System Security and Application Security) content
7,Safety requirementscan be divided intothingPhysical security (such as computer room security),netNetwork security (intrusion detection, access control policy configuration),systemsystem security (vulnerability patch management) andanswerApplication security (database security), host security (operating system)
8. The grounding of the computer room is generally divided into AC working grounding, DC working grounding, protective grounding and lightning protection grounding.
9. Example
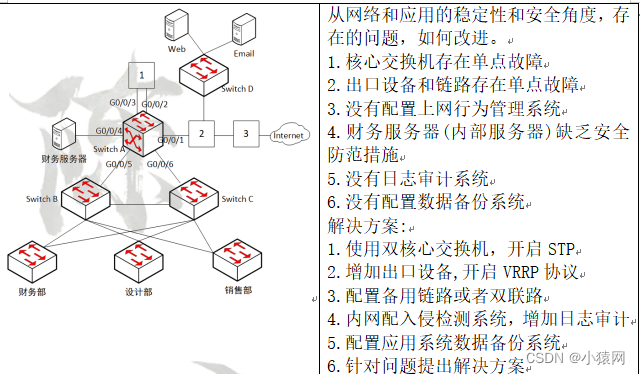
10. The technical indicators for evaluating system reliability include:MTBF and MTTRtwo kinds;The more MTBF, the higher the reliability; the smaller the MTTR value, the higher the reliability.
11. CommonFault Detection TechnologyincludeBFD and EFM,Protectswitching technologyincludeInterface backup, GR, NSR, interface monitoring group, VRRP, dual-system hot standbywait.
12. Network information security management: refers to taking appropriate security measures for network assets to ensure the security of network assets.Availability, integrity, control and non-repudiationwait for no causeNetwork management, network communication protocol, network service, network managementaffected by man-made and natural factors, andcause network disruption, information disclosure or destruction。
(2) File encryption and electronic signature
1. File encryption technology is a common application of cryptography, involvingCryptography, operating systems, file analysis techniques。
- Utilizing the above technologies, file encryption mainly includes the following contents.
- The content of the file is encrypted, usually using binary encryption.
- File attributes are encrypted.
- Encryption of file input and output and operation process, that is, dynamic file encryption.
2. EFS file encryption: - Windows can control users' unauthorized access to files through login authentication and NTFS permissions, but if users install different operating systems on the same computer, login authentication and NTFS permission settings can be bypassed. To eliminate this security hole, Microsoft provides an Encrypting File System (Encrypting File System, EFS), which is tightly integrated with NTFS to provide deep protection for sensitive data. When a file is encrypted by EFS, only the encryption user and the data recovery agent user can decrypt the encrypted file, and other users cannot decrypt it even if they obtain the ownership of the file.
- EFS useCombination of symmetric key and asymmetric key technologyThe method to provide file protection, the symmetric key is used to encrypt the file, and the public key in the asymmetric key is used to encrypt the symmetric key.
- EFS encryption occurs at the file system layer not at the application layer, so its encryption and decryption process is transparent to encryption users and applications. When users use encrypted files, they feel the same as ordinary files.
3. Electronic signature: - Electronic signature not only includes what we usually meandigital signature,also includeComputer passwords, biometric handwriting recognition, fingerprint recognition, and the newly emerging iris perspective recognition method, facial pattern recognitionwait.
- In practice, the main technologies of the electronic seal system includePKI technology (or biometric technology), smart card technology and digital watermark technology.
4. Digital watermark: - imperceptibility, or concealment. That is, the embedded watermark will not cause obvious degradation, or the visual or auditory quality of the digital product will decrease, and it will not be easily noticed.
- hidden location security. The watermark information is hidden in the data instead of the file header, and the transformation of the file format should not cause the loss of the watermark data.
- robustness. The so-called robustness means that the digital watermark can still maintain integrity or be accurately identified after undergoing various unintentional or intentional signal processing processes. Possible signal processing processes include channel noise, filtering, digital/analog and analog/digital conversion, resampling, shifting, scaling, and lossy compression coding.
(3) Safety Audit and Safety Management
1. Security audit includesIdentify, record, store, analyze information related to security-related actions
, Audit records are used to check security- related activities and responsible persons
- Safety management system: for example, registration records are required to enter the computer room;
- Security management organization: such as a network security management team, a unit director or a virtual team led by a leader;
- Security management personnel: a list of personnel specifically responsible for network security;
- Safety construction management: carry out standardized safety construction such as grading, rectification, and evaluation according to the standard of Class Insurance 2.0;
- Safety operation and maintenance management: After the construction is completed, standardized safety operation and maintenance, emergency drills, etc. will be carried out.
Chapter VII Standardization and Legal Regulations
1. Standardized knowledge
1. The "Standardization Law of the People's Republic of China" divides standardization into 4 levels
1) National standards;
−GB: mandatory national standards
−GB/T: recommended national standards
−GB/Z: guiding national standards
−GSB: national Physical standard
−SJ: Indicates industry standard
2) Industry standard
− For technical requirements that do not have national standards but need to be unified within a certain industry in the country, industry standards can be formulated, −It
is a highly professional and technical standard.
−Industrial standards are planned, approved, numbered, released and managed by the industry standard department.
− As a supplement to the national standard, when the corresponding national standard is implemented, the industry standard shall be abolished automatically.
3) Local standards
4) Enterprise standards
5) In addition, there are international standards, such as: ISO (International Organization for Standardization), IEC (International Electrotechnical Commission), ITU (International Telecommunication Union).
2. Validity period of the standard
− From the date of implementation of the standard to the reconfirmation, revision or abolition of the standard review, it is called the validity period of the standard, also known as the age of the standard. Due to the different conditions of each country, the standard validity period is also different.
− Taking the ISO standard as an example, the standardReview every 5 years, with an average standard age of 4.92 years.
−China stipulates in the national standard management method that the national standard shall be reviewed within 5 years of implementation, that is, the national standardThe home standard is valid for 5 years。
2. Intellectual property rights
1. Laws related to intellectual property protection
− China mainly has five laws in the field of IT: "Copyright Law", "Computer Software Protection Regulations", "Patent Law", "Trademark Law" and "Anti-Unfair Competition Law" Protect.
−Computer software is a special case of copyright-protected works, so when there is no relevant provision in the "Computer Software Protection Regulations", it will refer to the "Computer Software Protection Regulations"Copyright Law》
2、知识产权可分为两类:工业产权和著作权
3、保护期限
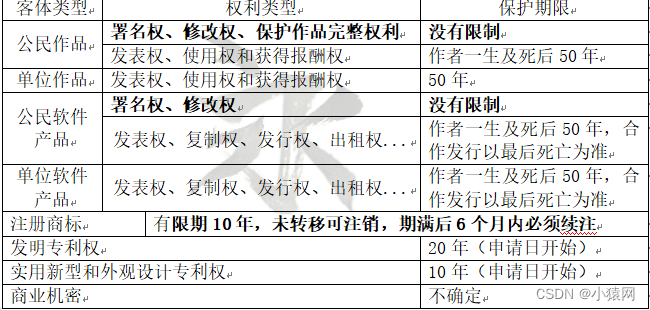
4、知识产权确定人
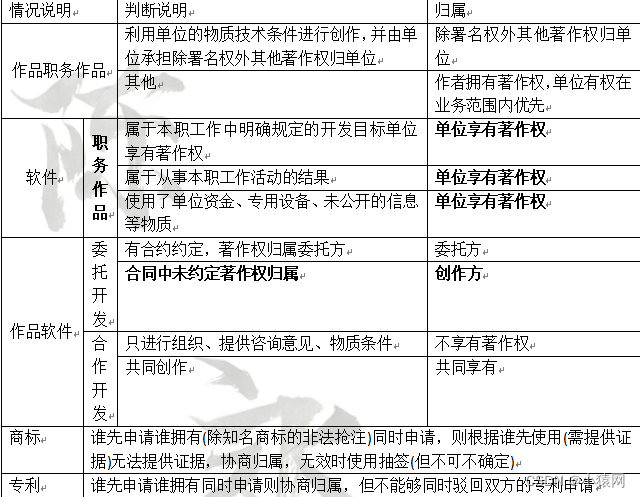
第八章网络产品方案
注:这一章节主要是对一些网络产品的特征做了一些说明,以下列举了一些网络产品的型号及其相应的特性,可供参考。可自行到相应的官网进行挑一些产品进行了解,可当做论文的素材,用于园区网的挑几个,用于数据中心的挑几个,可以在不同的厂家进行挑选(如防火墙用深信服的,交换机用华为的…)。以下也提供一些相应知名度较高的官网链接。
华为:https://e.huawei.com/cn/
华三:https://www.h3cmall.com/
深信服:https://www.sangfor.com.cn/
锐捷:https://www.ruijie.com.cn/cp/
奇安信:https://www.qianxin.com/product/
相应市面上的厂商还有很多,可以自行了解一下,以下是以华为为例,其他产品自行下去了解。以下内容感觉文字还是有点多的,多读几遍很多东西有个印象也就差不多了,写论文提供一些素材和写的内容(不管什么论文都可以写的万能的东西挑出来多记忆一下)
一、华为园区网交换机功能与特性
(一)超高带宽
1、高速数据传输:华为园区网交换机支持高速数据传输,能够处理大量的数据流量。它采用高性能的交换芯片和优化的数据转发算法,实现低延迟和高吞吐量的数据传输。
2、多个高速接口:交换机提供多个高速接口,包括千兆以太网、万兆以太网)和更高速的接口类型(如25G、40G、100G以太网)。这些高速接口能够满足对超高带宽的需求。
3、聚合链路技术:华为园区网交换机支持链路聚合技术,可以将多个物理链路捆绑成一个逻辑链路,提供更高的带宽和冗余。通过聚合链路技术,可以实现带宽的扩展和负载均衡,满足对超高带宽的需求。
4、高密度端口设计:华为园区网交换机设计了高密度的端口布局,可以提供更多的端口数量。这样可以支持更多设备的连接,满足大规模园区网络的需求。
5、流量调度和优先级管理:交换机支持流量调度和优先级管理功能,可以根据不同的流量类型和优先级进行带宽分配和流量控制。这样可以保证关键业务的带宽需求,提供良好的服务质量(QoS)。
6、华为园区网交换机通过高速接口、聚合链路技术、高密度端口设计和流量调度等功能,实现了超高带宽的支持,适应了现代园区网络对大带宽的需求。
(二)有线无线融合
1. Wireless access support: Huawei campus network switches have built-in wireless access controllers (ACs), which can manage and control wireless access points (APs) in the campus. With wireless access support, the switch can provide wireless network coverage to meet the wireless access needs of mobile devices.
2. Unified management platform: Huawei campus network switches adopt a unified network management platform that can manage wired and wireless network devices at the same time. Administrators can configure, monitor and troubleshoot wired switches and wireless access points through the centralized management platform to realize integrated management of wired and wireless networks.
3. Consistent user authentication: The switch supports a consistent user authentication mechanism, which can realize consistent authentication of wired and wireless users. Users can access wired and wireless networks through a unified identity authentication method (such as 802.1X authentication), providing unified user experience and security.
4. Seamless switching and roaming: The switch supports seamless switching and roaming functions, which can realize smooth switching and uninterrupted roaming of mobile devices in the campus. Users can freely switch between different wireless access points to achieve continuous connection and stability of the wireless network.
5. Enhanced security: Huawei campus network switches provide enhanced security protection mechanisms, including identity authentication, access control, traffic encryption, and security auditing. These security features apply to both wired and wireless networks, protecting the network from unauthorized access and malicious attacks.
6. Huawei campus network switches passFunctions such as wireless access support, unified management platform, consistent user authentication and enhanced security realize the integration of wired and wireless networks. In this way, an integrated network solution can be provided to meet the needs of the campus network for wired and wireless convergence.
(3) High reliability
1、冗余设计:华为园区网交换机采用冗余设计,包括冗余电源、冗余风扇和冗余线卡等。这样可以避免单点故障,提高设备的可靠性和可用性。
2、热备份:交换机支持热备份功能,即在主设备发生故障时,备用设备能够自动接管工作,实现无缝切换。这样可以避免业务中断,提供持续的网络连接。
3、链路聚合:华为园区网交换机支持链路聚合技术,可以将多个物理链路捆绑成一个逻辑链路,提供带宽的扩展和冗余。在链路故障时,流量会自动切换到其他可用链路,确保数据的连续传输。
4、快速恢复:交换机具备快速恢复能力,能够迅速检测并处理网络故障。它支持快速的链路状态检测和故障通知机制,能够快速切换到备用路径,减少业务中断时间。
5、可靠的故障检测和诊断:交换机提供可靠的故障检测和诊断功能,可以实时监测网络设备和链路的状态,并提供相应的告警和日志信息。快速定位和解决网络故障,提高故障排除的效率。
(四)精细运维
1. Unified management platform: Huawei campus network switches can be centrally managed and configured through a unified network management platform. Administrators can centrally monitor, configure, and troubleshoot switches through this platform, simplifying the operation and maintenance workflow
2. Real-time performance monitoring and alarming: Huawei campus network switches provide real-time performance monitoring functions, which can monitor the performance of network devices and links Indicators, such as bandwidth utilization, traffic statistics, and error messages. At the same time, it also supports the performance alarm function. When the performance index reaches the set threshold, an alarm notification will be sent in time.
3. Traffic analysis and fault diagnosis: The switch has traffic analysis and fault diagnosis functions, which can conduct in-depth analysis of network traffic and help administrators locate network problems and fault causes. It supports functions such as traffic capture, packet analysis, and troubleshooting, and provides detailed network fault diagnosis information.
4. Configuration management, backup and recovery: Huawei campus network switches support configuration management and backup and recovery functions, enabling centralized management and backup of switch configurations. Administrators can modify, back up and restore the configuration through the configuration management platform to ensure the consistency and reliability of the configuration.
5. Logging and auditing functions: The switch has logging and auditing functions, which can record the operation logs of network devices and links, and provide audit trail functions. Administrators can view log records and audit information to understand the operation history and changes of the network for fault analysis and security auditing
(5) Security
1. Access control: The switch supports access control functions based on MAC address, IP address, port and user identity. Administrators can configure access control lists (ACLs) as required to limit access rights of network devices and users to prevent unauthorized access.
2. Identity authentication: Huawei campus network switches provide multiple identity authentication methods, such as 802.1X authentication, MAC address authentication, and Web Portal authentication. Through identity authentication, the switch can verify the user's identity and grant corresponding network access rights to ensure network security.
3. Security protocol support: the switch supports a variety of security protocols, such as SSH, SSL and IPsec. These protocols can encrypt data transmission, authenticate communicating parties, and provide data confidentiality and integrity protection.
4. Security audit: Huawei campus network switches have a security audit function, which can record operation logs of network devices and users, and provide an audit trail function. Administrators can check audit logs, monitor and analyze network security events and abnormal behaviors, and take corresponding measures in a timely manner.
5. Defensive security functions: The switch has built-in defensive security functions, such as anti-MAC address spoofing, ARP protection and DHCP Snooping, etc. These functions can prevent network attacks and malicious behaviors, and protect the security and stability of the network.
6. Security management platform integration: Huawei campus network switches can be integrated into the security management platform to achieve unified security management and monitoring. Administrators can perform centralized security policy configuration, vulnerability scanning, and threat detection on switches through the security management platform to improve the overall security level of the network
(6) Green energy saving
1、节能设计:华为园区网交换机采用节能设计,通过优化硬件组件和电路设计,以及采用低功耗芯片和模块,实现能耗的降低。这样可以减少能源消耗,降低运行成本。
2、功耗管理:交换机支持功耗管理功能,可以根据网络流量和连接状态动态调整设备的功耗。当网络负载较低时,交换机会自动进入低功耗模式,以节省能源。
3、睡眠模式:华为园区网交换机支持睡眠模式,当交换机处于闲置状态时,可以自动进入低功耗的睡眠模式。在睡眠模式下,交换机仍然可以快速唤醒以响应网络流量。
4、智能风扇控制:交换机配备智能风扇控制功能,可以根据设备的温度和负载状态智能调整风扇的转速和功耗。这样可以降低风扇噪音和能耗,提供更安静的工作环境。
5、环境监测:华为园区网交换机支持环境监测功能,可以实时监测设备周围的温度和湿度等参数。当环境温度超过设定阈值时,交换机可以发出警报并采取相应的保护措施,以防止设备过热。
二、华为数据中心交换机产品方案
1. CloudEngine 16800 series:
−High-density ports: Provide high-density 40GbE and 100GbE ports, suitable for large-scale data centers and cloud computing environments.
−Flexible scalability: supports flexible modular design, and can perform port expansion and bandwidth upgrade according to requirements.
−Non-blocking forwarding: It has non-blocking data forwarding capability to ensure low-latency and high-throughput data transmission.
−VXLAN support: Supports Virtualized Extended Local Area Network (VXLAN) to realize cross-data center virtual network interconnection.
−Programmability: With programmable switch features, it supports SDN and network automation deployment.
2. CloudEngine 12800 series:
−High-performance switching: Provides high-performance data forwarding and processing capabilities, suitable for large enterprises and cloud data centers.
−Multiple interface types: support the interconnection of various interface types such as Ethernet, Fiber Channel, and InfiniBand.
−Flexible modular design: Modular port expansion and function enhancement can be carried out according to requirements.
−High reliability and redundancy: support hot-standby plug and redundant devices to ensure high availability and reliability of the network.
−Scalability: Supports flexible network expansion and upgrades to meet growing business needs.
3. CloudEngine 8800 series:
−High-density ports: Provide high-density 10GbE and 40GbE ports, suitable for large-scale data centers and enterprise networks.
−High-performance forwarding: It has high-performance data forwarding and processing capabilities to meet the needs of high-speed network traffic.
−Programmability and scalability: Supports SDN and network automation deployment, and has flexible expansion capabilities.
−Security features: Supports security features and multi-layer network security protection to protect the security of the data center network.
−Intelligent O&M and management: Provides intelligent network O&M and management functions to simplify the network O&M process.
4. CloudEngine 6800 series:
−High-performance forwarding: With high-performance data forwarding and processing capabilities, it is suitable for medium-sized enterprises and distributed data centers.
−Multiple interface types: support the interconnection of various interface types such as Ethernet, Fiber Channel, and InfiniBand.
−Flexible modular design: Modular port expansion and function enhancement can be carried out according to requirements.
−High reliability and redundancy: support redundant equipment and hot-standby plugging to ensure high availability of the network.
3. Huawei AR series low/medium/high-end router product solutions
1. Huawei AR1200 series:
−Reliable network connection: Provides various interface types, including Ethernet interface, WAN interface, wireless interface, etc., to meet various network connection requirements.
−Basic routing function: supports static routing and some dynamic routing protocols, and realizes basic data forwarding and routing control.
−Security function: Provides basic firewall functions and VPN support to protect network security.
−Simple management: Provides an easy-to-use management interface and basic network management functions to facilitate network configuration and monitoring.
2. Huawei AR160 series:
−Small and medium-sized enterprise routers: suitable for small and medium-sized enterprises and branch offices, providing reliable network connections and basic routing functions.
−Multiple interface types: support Ethernet interface, WAN interface, wireless interface and other interface types to meet different network connection requirements.
−Security function: Provides basic firewall functions and VPN support to protect network security.
−Simplified management: Provides an easy-to-use web interface and a centralized network management platform to simplify the network configuration and management process.
3. Huawei AR1220E series:
−High-performance processing capability: Provides high-performance data processing and forwarding capabilities, suitable for small and medium-sized enterprises and branches.
−Multiple interface types: support Ethernet, WAN interface, wireless interface and other interface types to meet different network connection requirements.
−VPN function: It supports various VPN technologies such as IPSec VPN, GRE VPN, and L2TP VPN, and provides secure remote access and site interconnection functions.
−Multi-level security protection: Provides security features such as firewall, intrusion detection and prevention system (IDS/IPS), and security audit to protect the network from threats.
4. Huawei AR2220E series:
−High-performance processing capability: Provides high-performance data processing and forwarding capabilities, suitable for small and medium-sized enterprises and branches.
−可扩展性:支持模块化的设计和扩展,可以根据需求进行接口和功能的灵活扩展。
−多种接口类型:支持以太网、WAN接口、无线接口等多种接口类型,满足不同的网络连接需求。
−高级的路由功能:支持静态路由、动态路由(如OSPF、BGP)、多路径路由等功能,实现高效的数据转发和路由控制。
5、华为AR3260系列:
−高性能处理能力:提供强大的数据处理和转发能力,适用于大型企业和复杂网络环境。
−多种接口类型:支持以太网、WAN接口、无线接口等多种接口类型,满足灵活的网络连接需求。
−高级的安全特性:提供防火墙、VPN、入侵检测与防御系统等多种安全功能,保护网络免受威胁。
−可靠性和冗余性:支持冗余设备和热备插拔,确保网络的高可用性和可靠性。
−高级的QoS功能:支持流量控制、带宽管理、流量优先级等QoS功能,确保关键应用的性能和服务质量。
6、华为AR6460系列:
−高性能处理能力:提供卓越的数据处理和转发能力,适用于大型企业和复杂网络环境。
−多种接口类型:支持以太网、WAN接口、无线接口等多种接口类型,满足灵活的网络连接需求。
−高级的安全特性:提供防火墙、VPN、入侵检测与防御系统等多种安全功能,保护网络免受威胁。
−可靠性和冗余性:支持冗余设备和热备插拔,确保网络的高可用性和可靠性。
−高级的QoS功能:支持流量控制、带宽管理、流量优先级等QoS功能,确保关键应用的性
四、华为NE系列高端路由器产品方案
1. NE9000 series:
−Support ultra-large-scale data centers and cloud computing networks, with high-density interfaces and ultra-high bandwidth, suitable for large enterprises and operators.
−High performance: Using multi-core processors and large-capacity memory, it provides excellent performance and data processing capabilities.
−High-density interface: supports Gigabit Ethernet and 10 Gigabit Ethernet interfaces to meet high bandwidth requirements.
−Multilayer switching function: supports functions such as VLAN, QoS, and ACL, and realizes flexible flow control and service quality management.
−High reliability and redundancy design: provide hardware redundancy and routing redundancy technology to ensure the availability and continuity of the network.
−Advanced security: supports functions such as firewall, VPN, and security encryption to protect network security and data privacy.
2. NE5000 series:
−Suitable for large-scale enterprises and operators, providing high-performance and high-density interfaces, and supporting large-scale data centers and cloud computing networks.
−High performance: Equipped with multi-core processors and large-capacity memory to achieve fast data processing and response.
−High-density interface: supports Gigabit Ethernet and 10 Gigabit Ethernet interfaces to meet high bandwidth requirements.
−Multilayer switching function: supports functions such as VLAN, QoS, and ACL, and realizes flexible flow control and service quality management.
−High reliability and redundancy design: provide hardware redundancy and routing redundancy technology to ensure high availability of the network.
−Advanced security: supports functions such as firewall, VPN, and security encryption to protect network security and data privacy.
3. NE40E series:
−Suitable for large enterprises and operators, providing high performance and reliability, supporting large-scale data transmission and complex network applications.
−High performance: Equipped with multi-core processors and large-capacity memory to achieve high-speed data processing and fast response.
−High-density interface: supports Gigabit Ethernet and 10 Gigabit Ethernet interfaces to meet high bandwidth requirements.
−Multilayer switching function: supports functions such as VLAN, QoS, and ACL, and provides flexible flow control and quality of service guarantee.
−High reliability and redundancy design: supports hardware redundancy and routing redundancy technology to ensure the reliability and continuity of the network.
−Advanced security: Provides functions such as firewall, VPN, and security encryption to protect the security of the network and data.
4. These high-end router product solutions of Huawei NE series are allProvides a wealth of network functions and security features, such as high-speed forwarding, QoS (Quality of Service), security protection, multi-path redundancy and flexible interface options, etc., to meet the needs of networks of different scales and complexity. In addition, theyIt also supports Huawei's intelligent network management system, providing centralized network management and operation and maintenance capabilities。