foreword
红中(hong_zh0)
CSDN内容合伙人、2023年新星计划web安全方向导师、
华为MindSpore截至目前最年轻的优秀开发者、IK&N战队队长、
吉林师范大学网安大一的一名普通学生、搞网安论文拿了回大挑校二、
阿里云专家博主、华为网络安全云享专家、腾讯云自媒体分享计划博主In a few days, I'm going to compete in the Internet security professional skills competition, and the questions are quite difficult to find.
Made the emergency reinforcement of bugku
There are a total of seven questions. I have finished the environment and closed it here, so there are not many pictures.
way of escalation
After entering the environment, I found that there is phpstudy on it
look at the next version
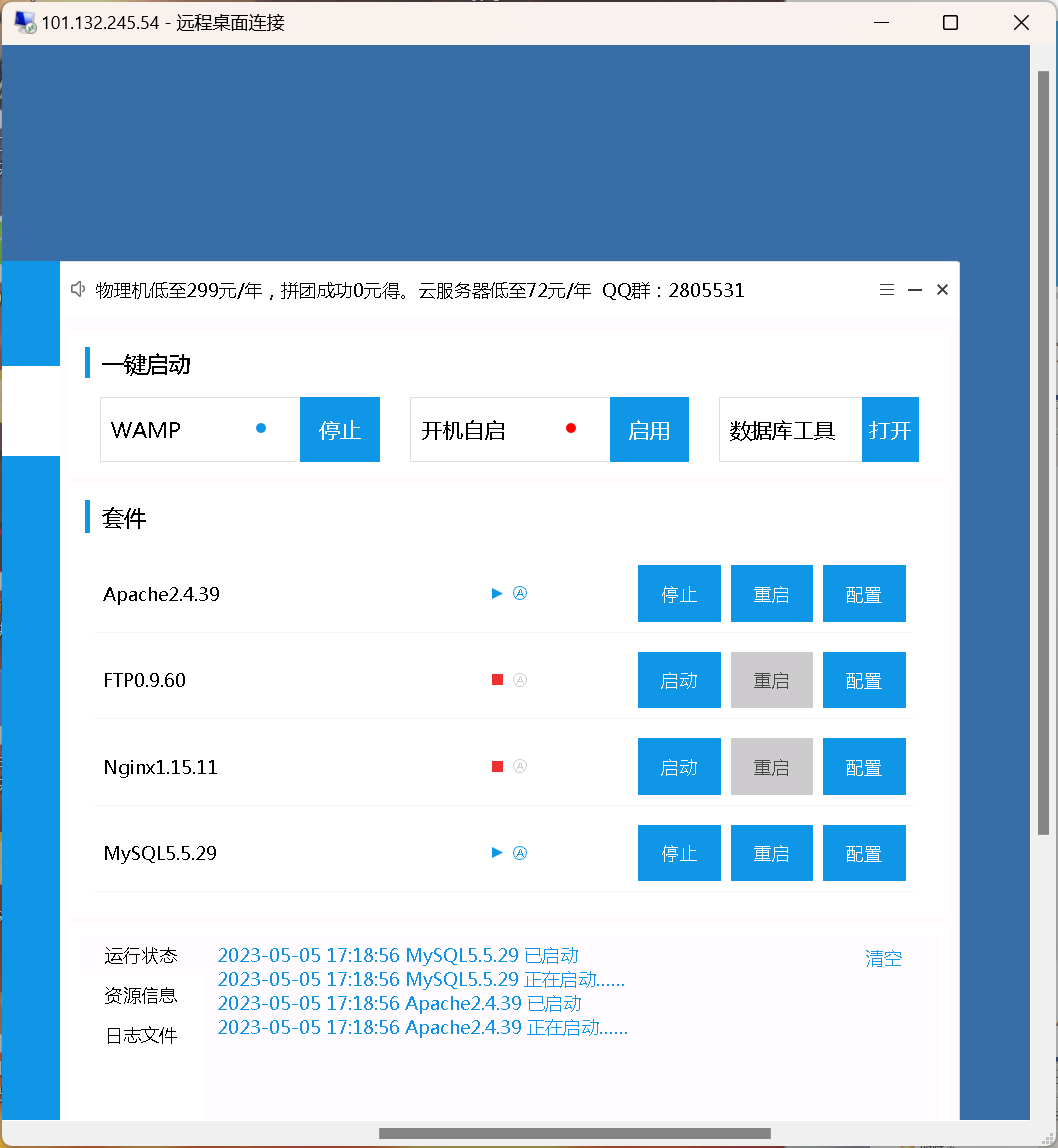
Take a look into the mysql folder and see the lib folder.

This is where you start, since mysql 5.1, this folder is gone, go in and have a look
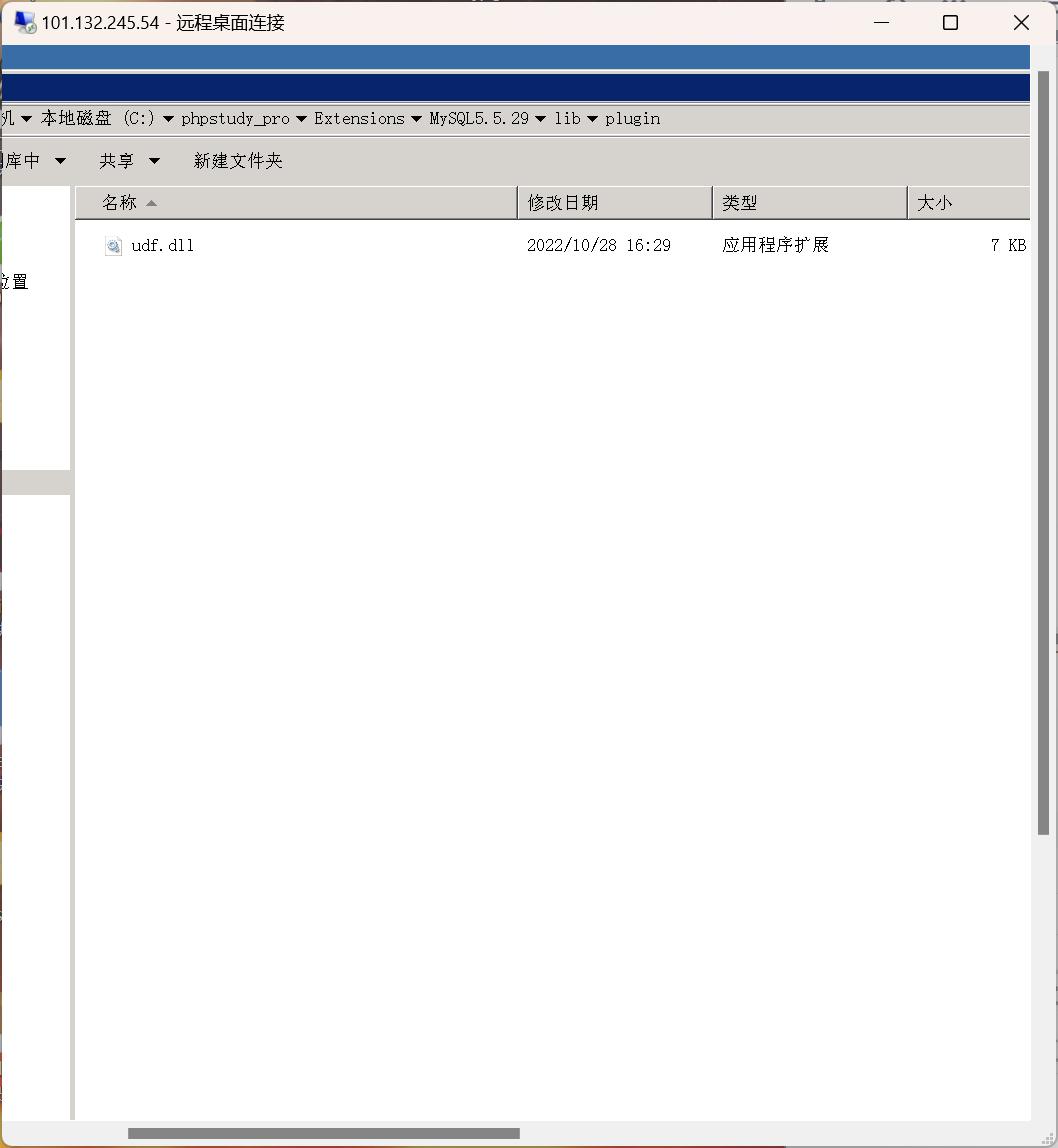
Done, udf rights raised
Hacker's webshell
webshell, take a look in the log

SQL injection, not a big problem
To find the back door, generally use POST
Search for POST
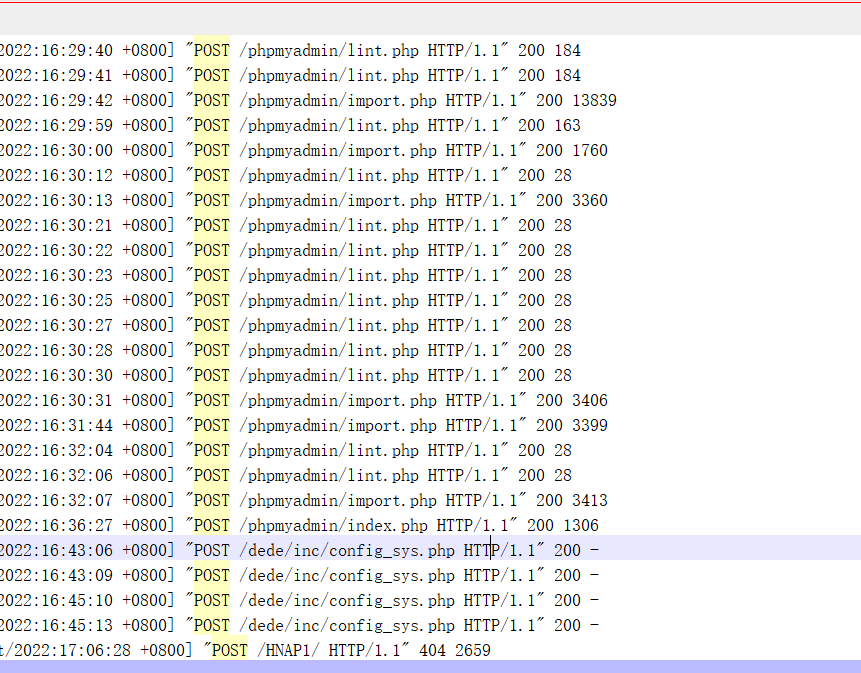
There are only a few files in total, and each of them will come out after looking through them.
config_sys.php
hacker account
He should not hide this, we are using the administrator account, just delete it.
If it is hidden, delete it in the registry
Backdoor Trojan
There is a gadget system6.exe in the startup item
delete first
It is found that it is running and cannot be deleted. that's the back door
tasklist /svc file
netstat -ano -p tcp | findstr "pid" to find hacker IP
then directly
taskkill /f /t /im "system6.exe"
Then just delete the process
hardened server
password policy in security policy
The shortest password is 8 characters
Shudo
UDF privilege escalation is mainly these three points
- The MySQL database is not in safe mode
- A known database account has the authority to insert and delete the MySQL database, preferably the highest authority of root.
- The shell has permission to write to the database installation directory.
in phpstudy_pro/Extansions/mysql5.5.29/my.ini
Riga
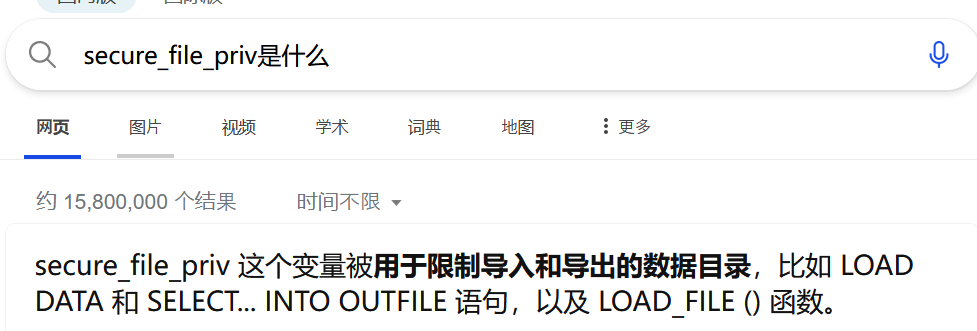
secure_file_priv=null