Here is a demonstration of how to build Cisco's SSLV PN on AWS to solve the needs of employees for remote work. The article requires you to have a certain AWS and SSLV PN foundation.
Personal blog address: https://liuqianglong.com
Article video address: https://space.bilibili.com/408773931
1. Introduction to the experiment
Recently, I have been studying the SSL*** of Cisco firewall to solve the problem of remote office work. Traditionally, ASA55XX series hardware firewalls are generally used for SSL***, and there is almost no difference between using ASAv and hardware firewalls. ASAv can be deployed in both vSphere and AWS environments. Here we mainly introduce the steps to configure SSL*** on AWS using ASAv. We will continue to discuss the advanced features of SSL*** in depth in the future.
If you have experience in configuring ASA SSL***, you need to pay attention to the special scenarios on AWS. The following are the notes for the entire experiment:
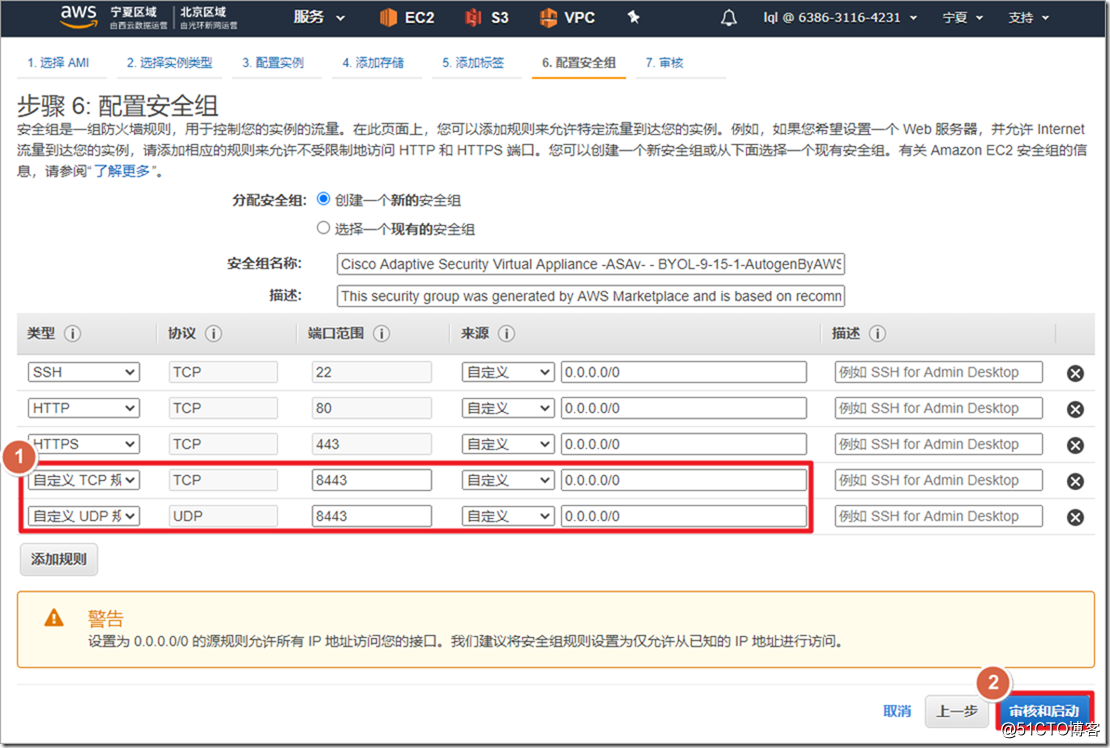
In China, if the AWS account has not been registered with ICP , TCP 80/443 cannot be used, so SSL*** is required to modify the default port 443.
The IP address assigned by the ASAv on AWS to the client can only be accessed after NAT translation, because the server does not have a packet return route.
Windows 2016 on AWS cannot install ASDM. It is recommended to use Windows 2019 to install ASDM software.
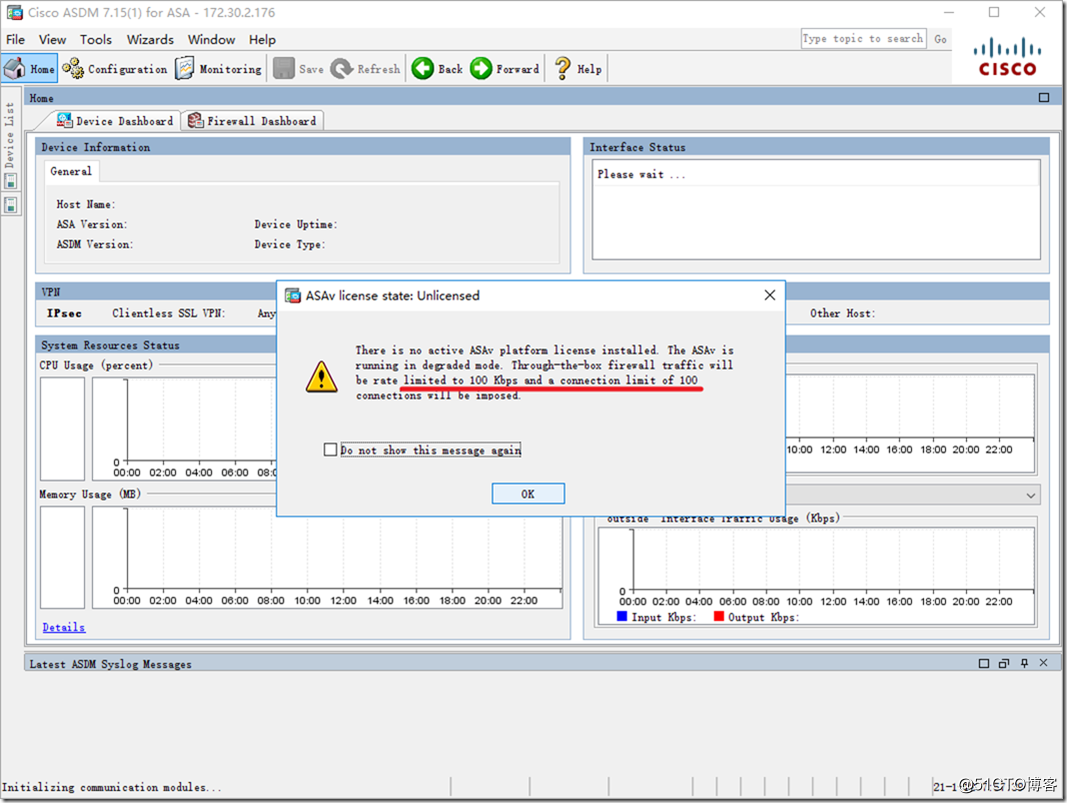
If the ASAv does not purchase a license, the speed limit is 100k and the maximum number of sessions is 100, which is sufficient for experimentation but cannot be used in a production environment.
2. Environmental introduction
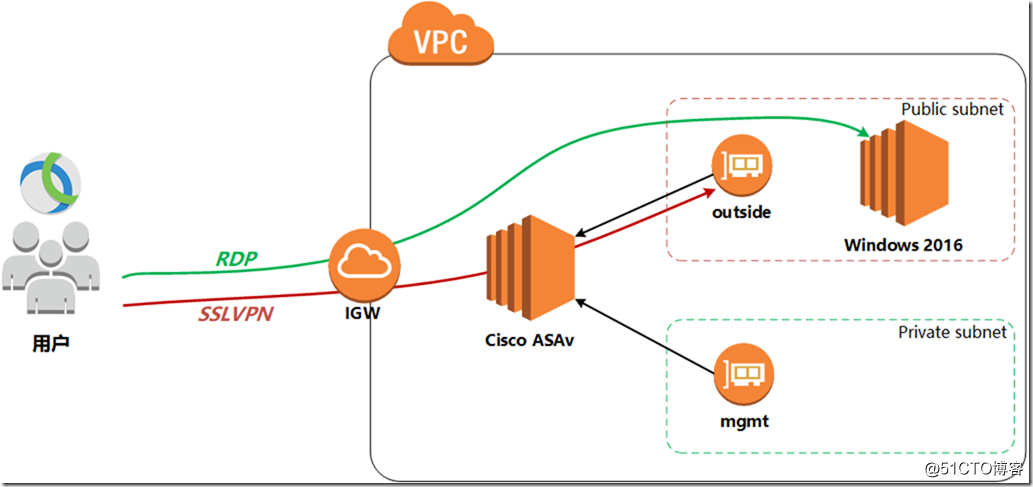
This experiment needs to use 2 subnets in the VPC. One public subnet is used to connect to the springboard. After connecting to Windows 2016, users can connect to ASAv through SSH and ASDM in Windows 2016. I won’t introduce AWS-related basic knowledge in detail here, such as how to create a VPC, how to create a public subnet, and a private subnet.
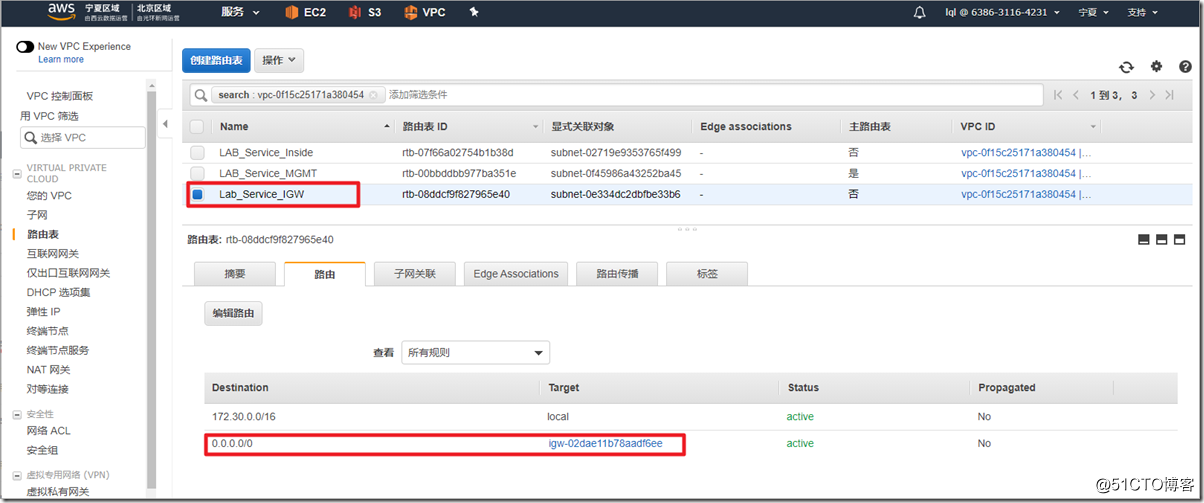
This is the public subnet that will be used in the experiment, and the default route points to IGW.
3. Configure the springboard environment
Enable a window2016 on the public subnet to access the ASAv through SSH and ASDM later. Note that the instance should be windows 2016. After testing, windows 2019 cannot install ASDM . Through the quick start of AWS, a windows 2016 can be searched by entering "windows 2016". Note that Cisco ASDM cannot be installed in the window 2019 environment.
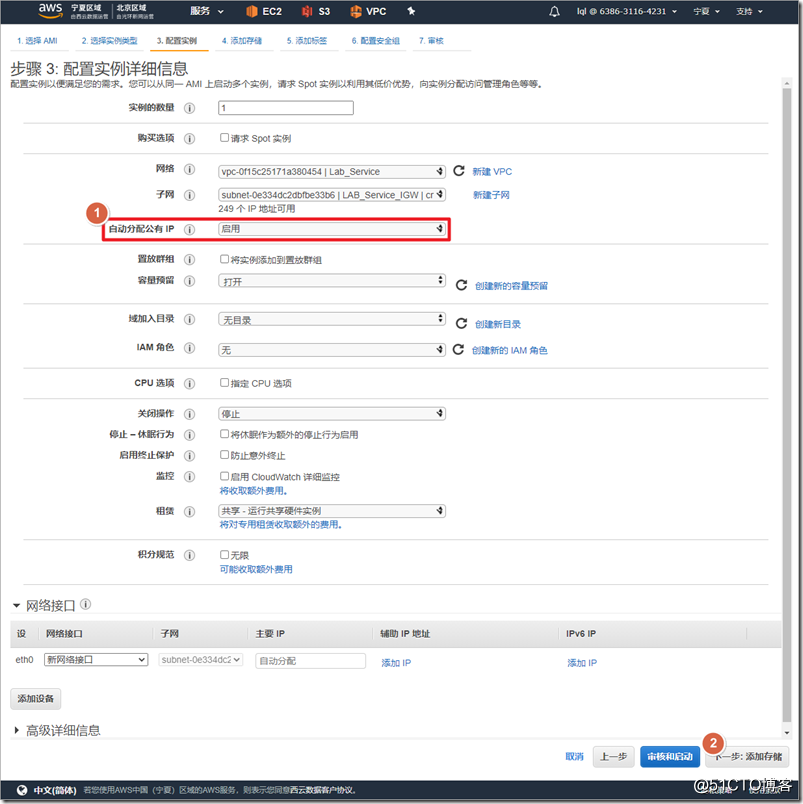
Window2016 is placed on a public subnet, and the function of assigning public IP is enabled.
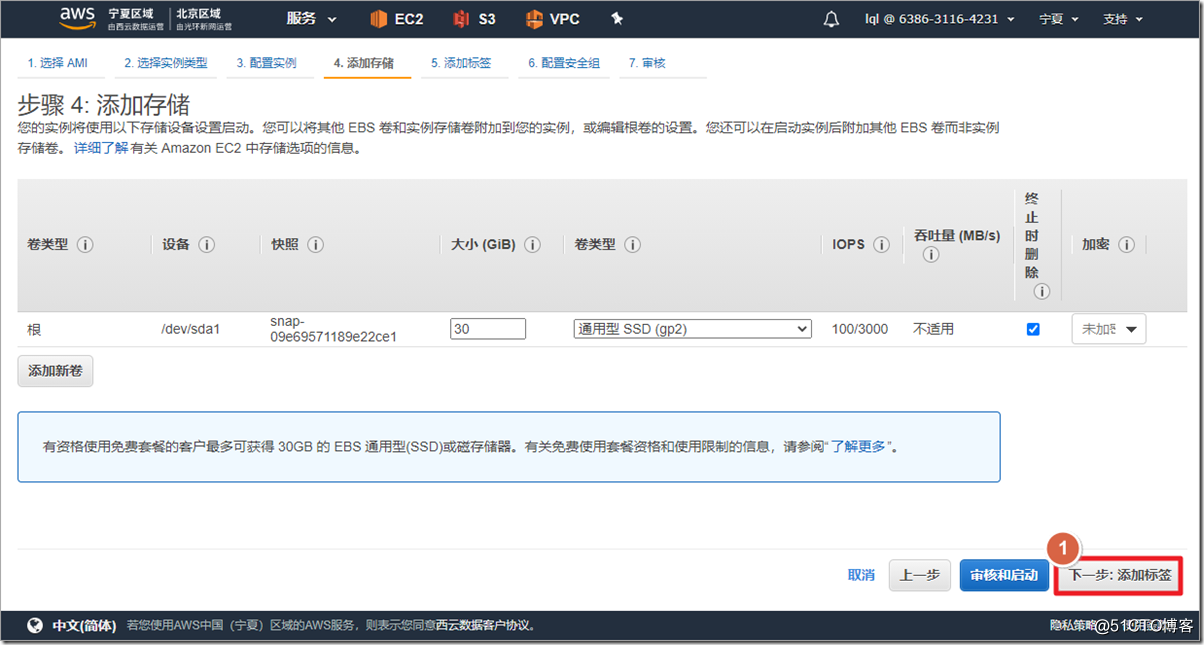
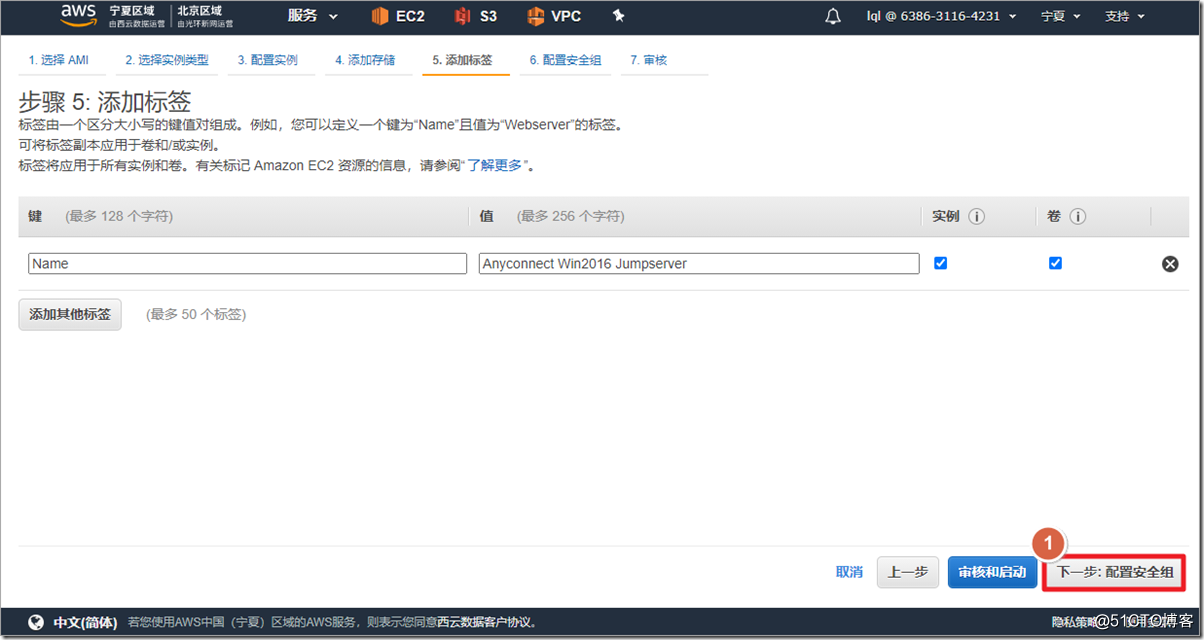
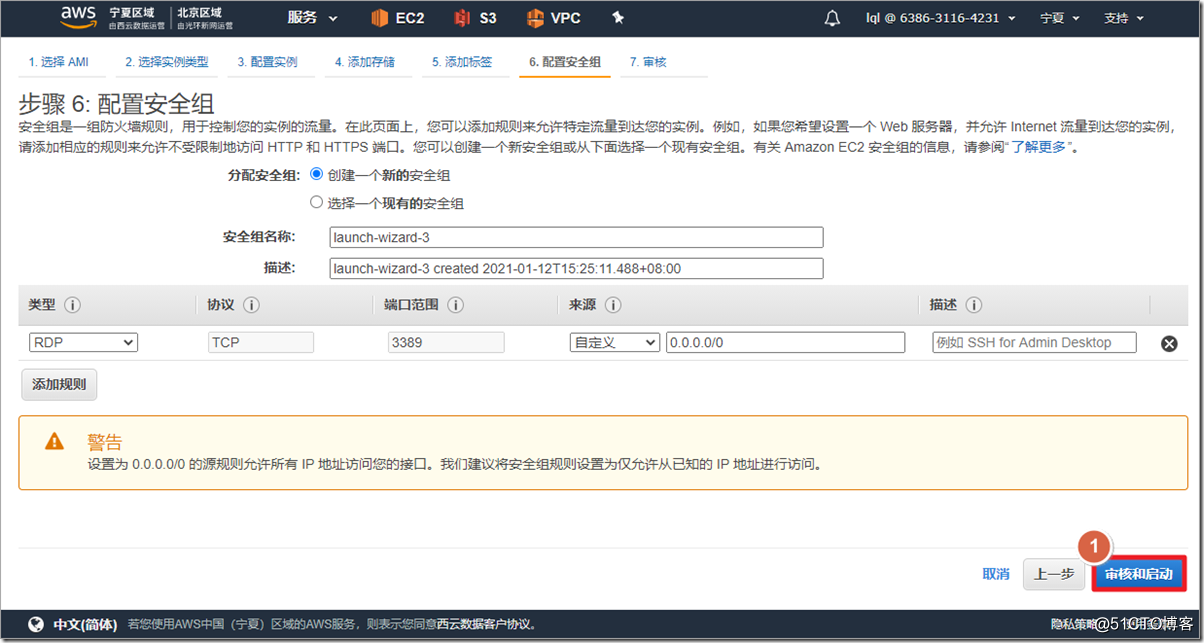
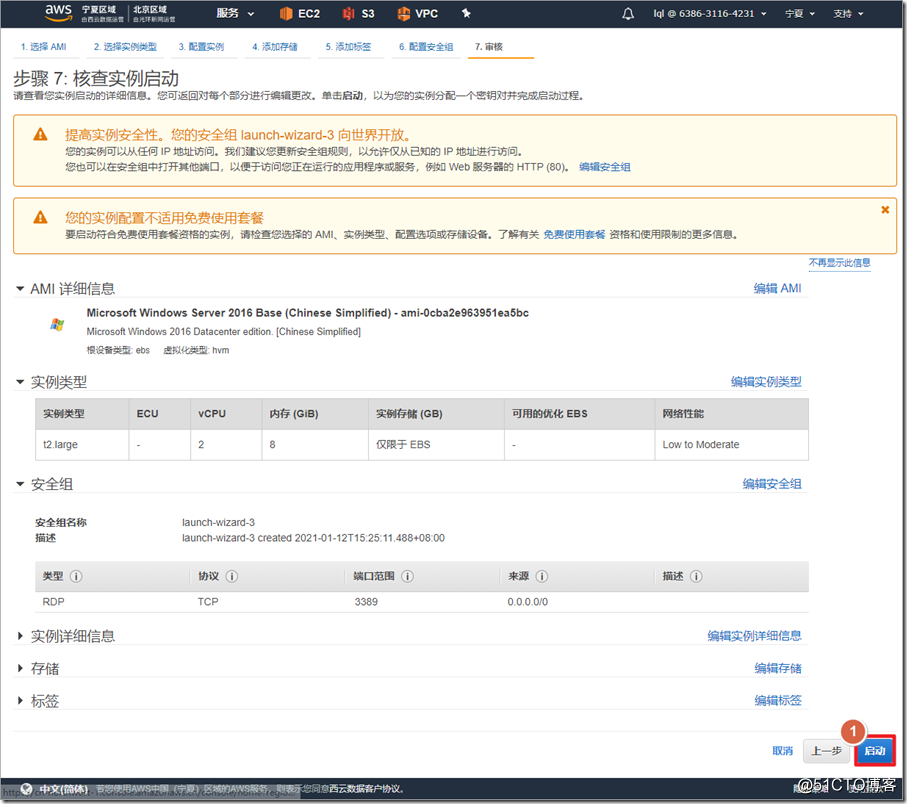
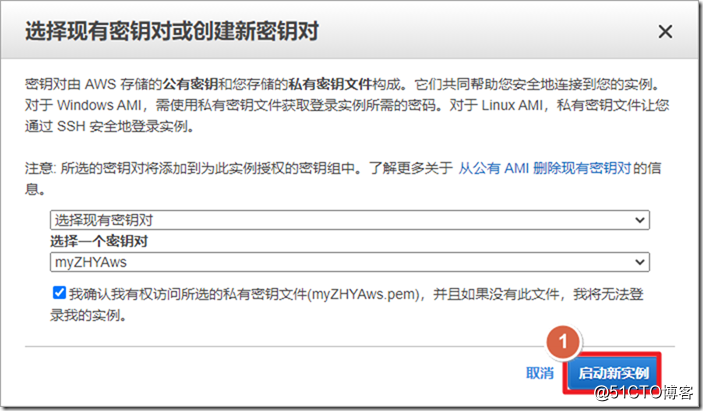
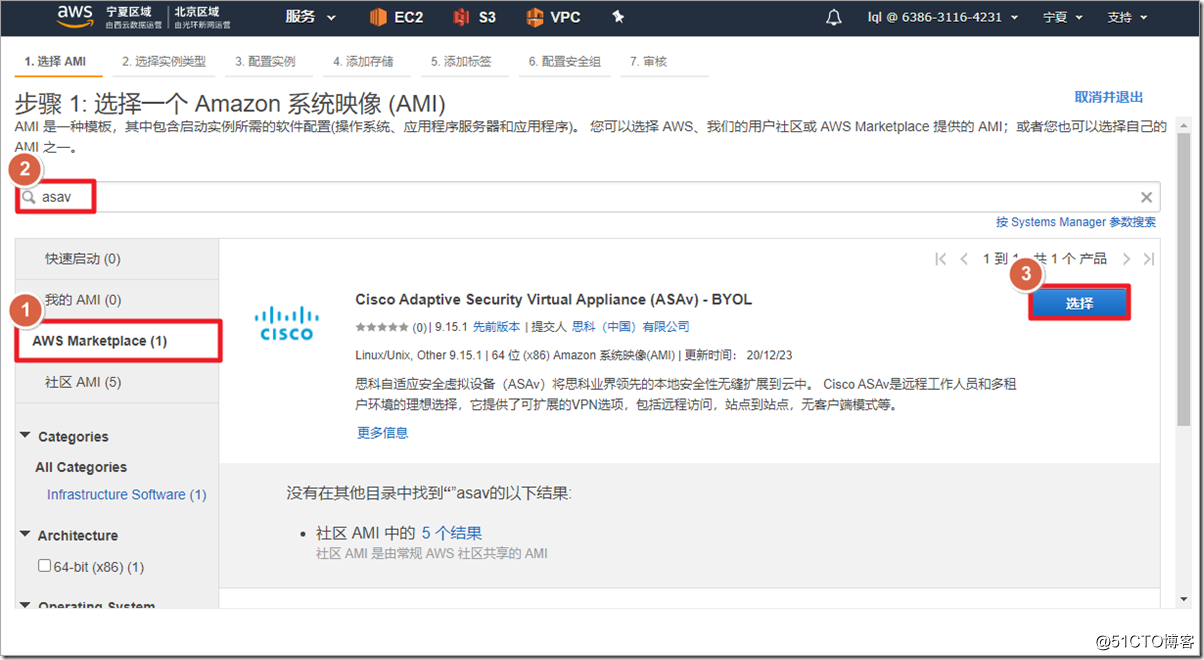
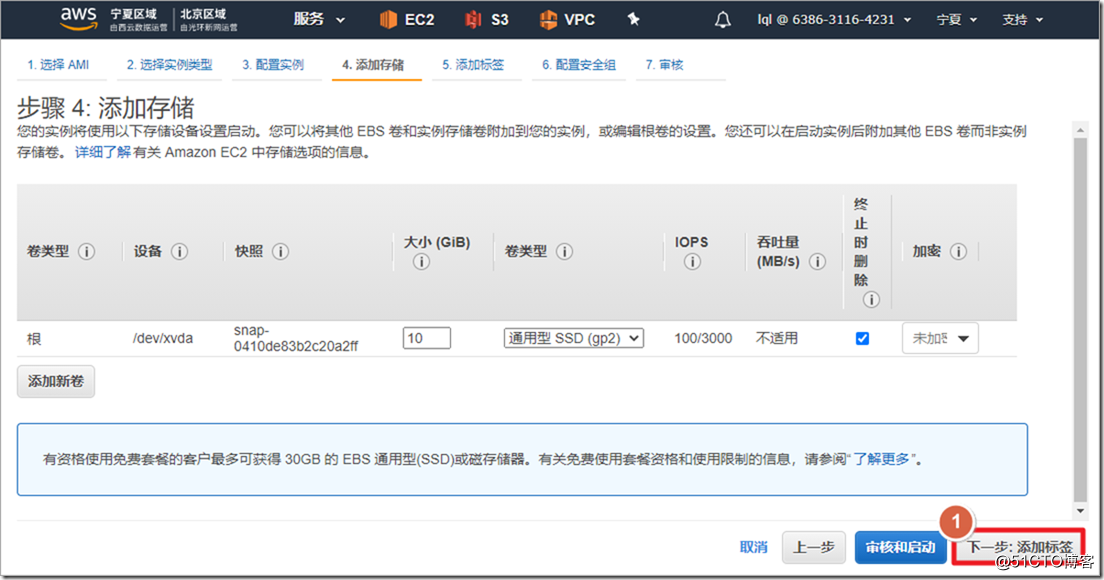
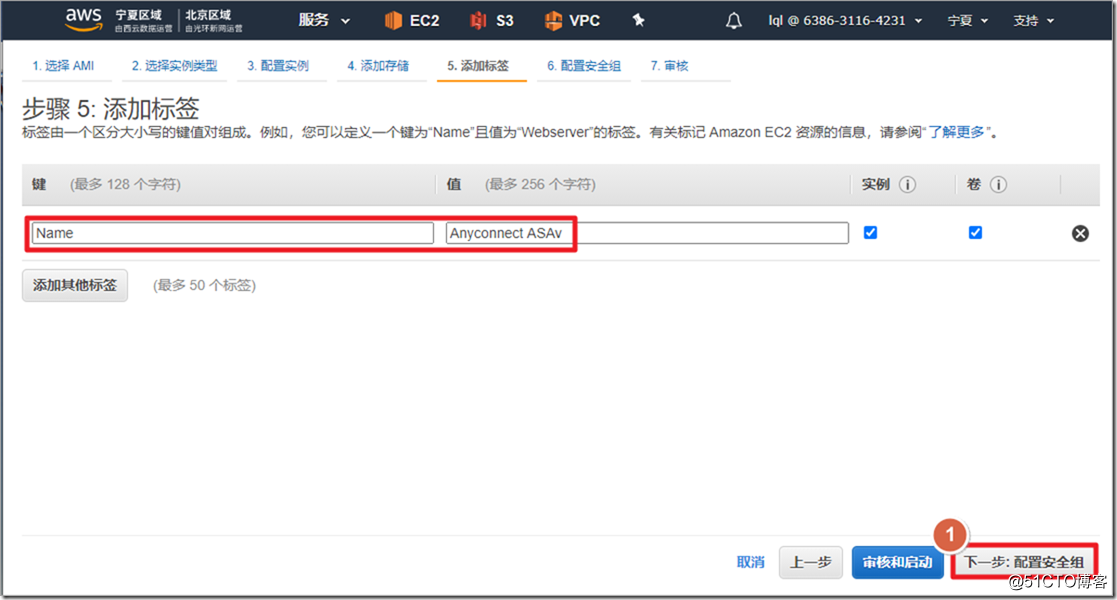
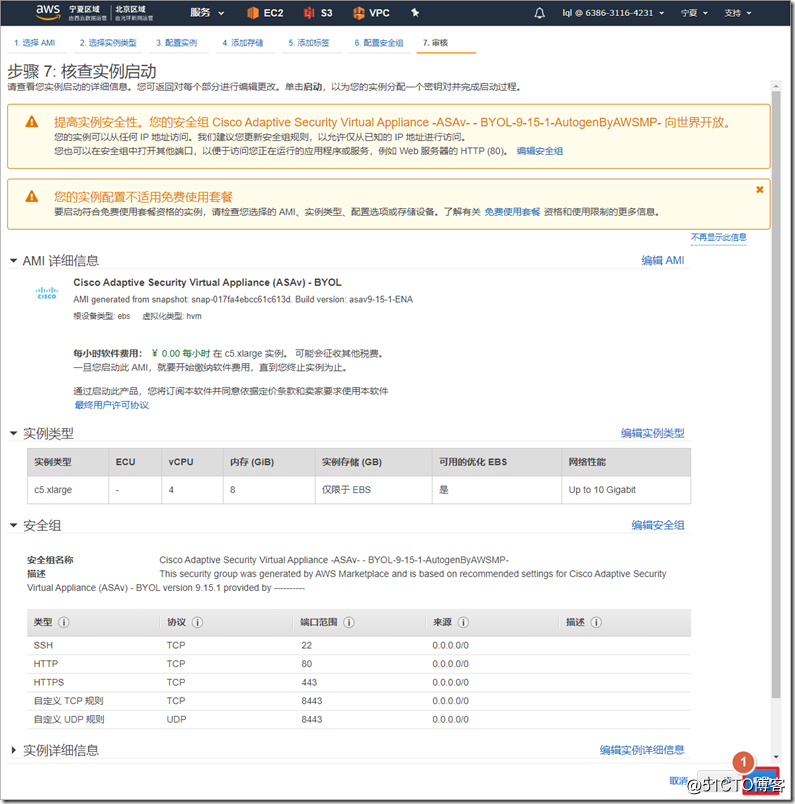
4. Create an ASAv instance
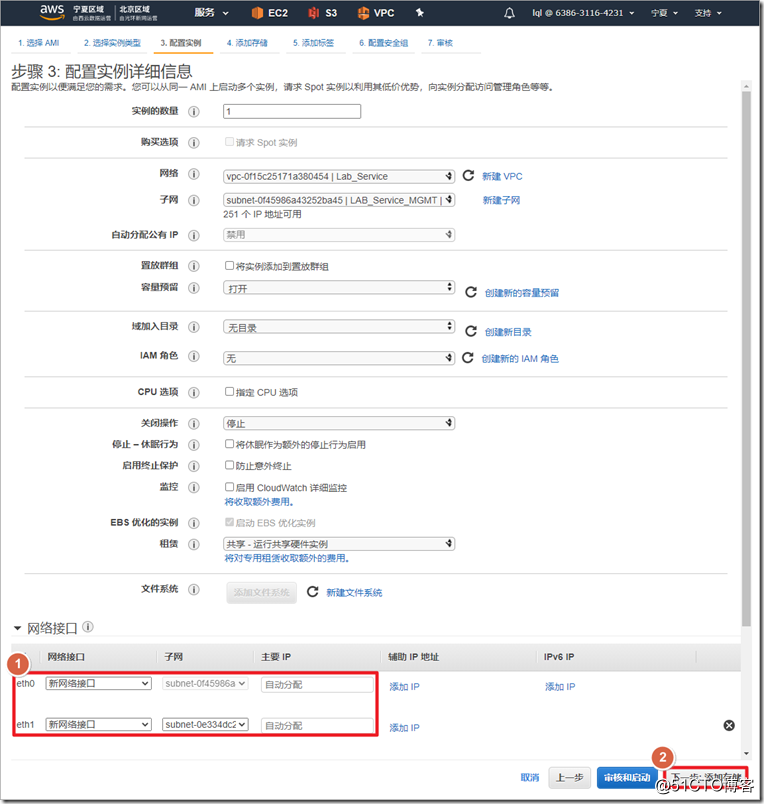
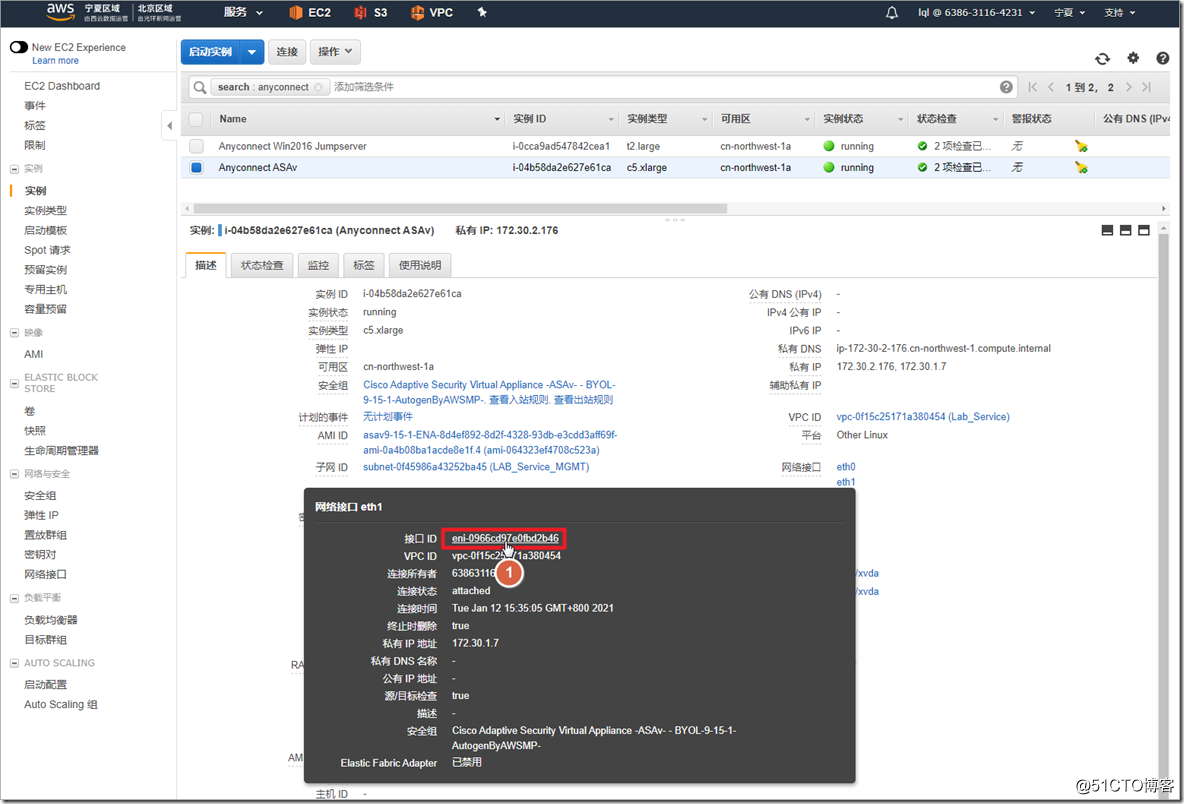
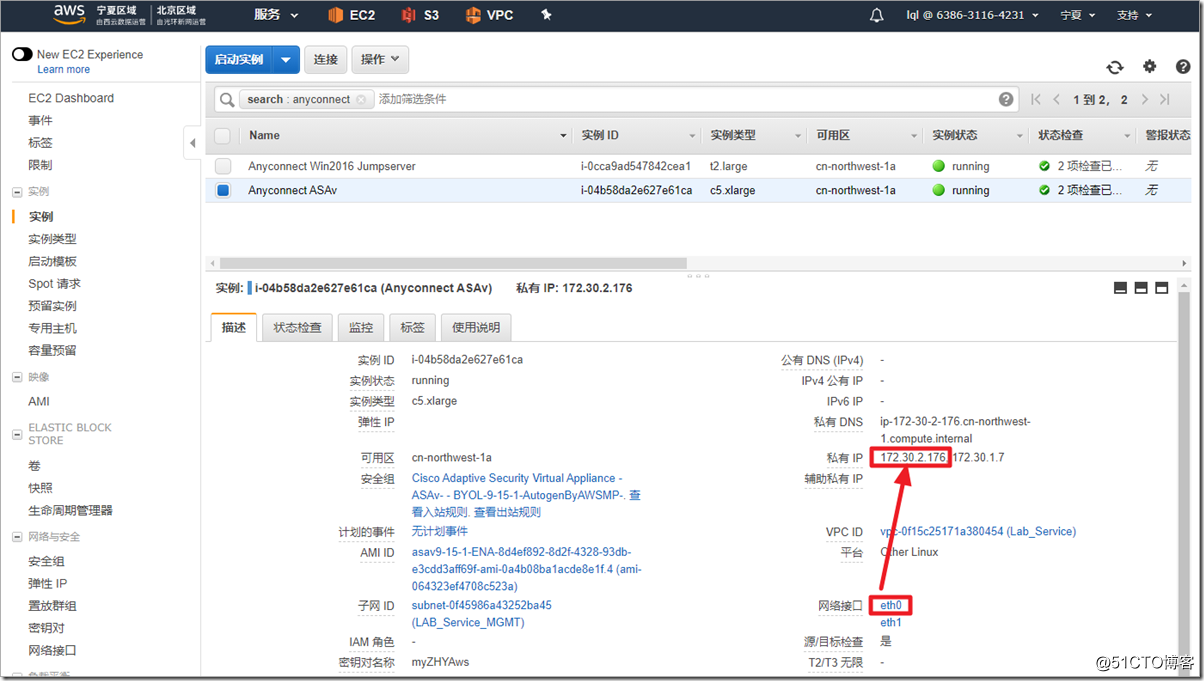
Search for asav in AWS Marketplace and select ami to enable it. It should be noted that ASAv defaults to eth0 as the management interface of ciscoasa. The management interface can only carry network management traffic and cannot transmit data traffic, so at least one eth1 needs to be added as an outside interface. If you need to add more interfaces, such as inside and dmz interfaces, you can add "network interface" and attach to the instance. In fact, in the AWS environment, an outside interface can run the AnyConnect environment.
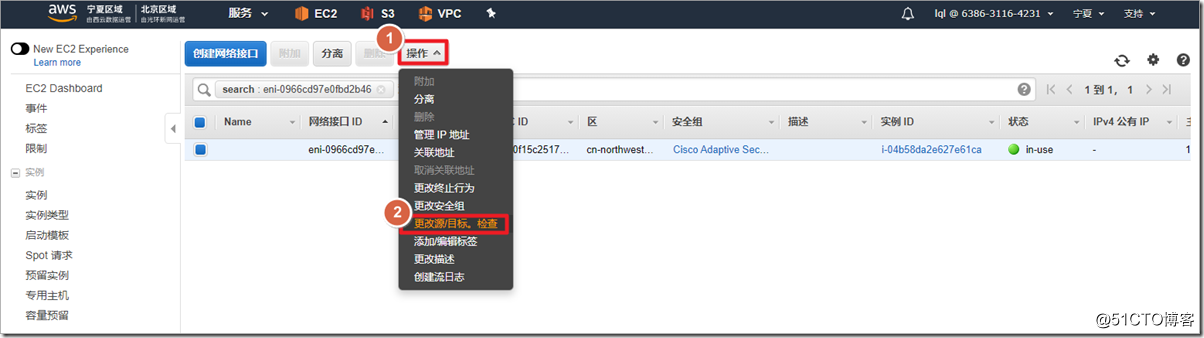
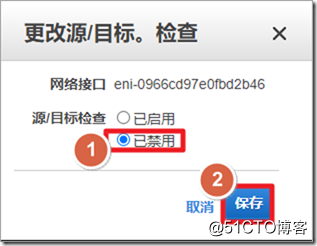
After the instance is successfully created, you need to configure the instance parameters in the AWS environment. On the AWS interface, traffic whose destination IP is not the IP of the interface is discarded by default , so if you want the ASA to forward traffic, you must close the outside interface
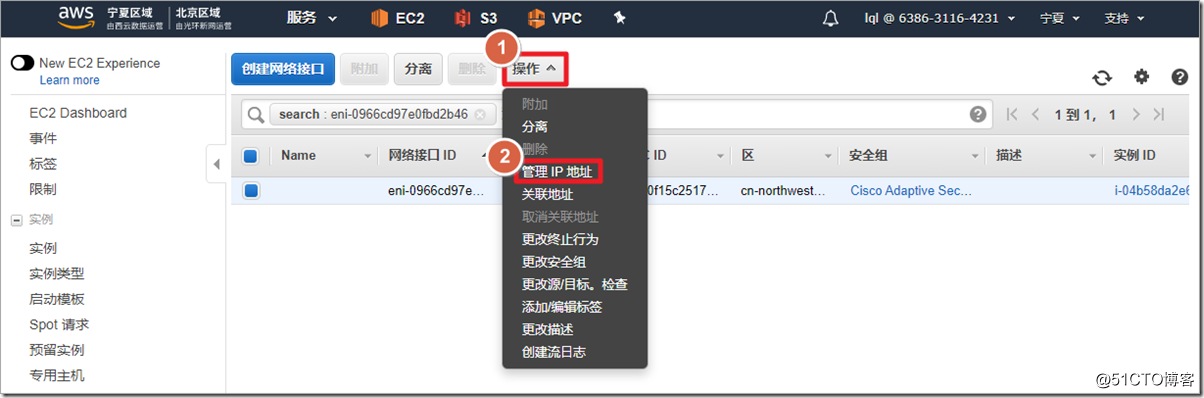
源/目标检查.
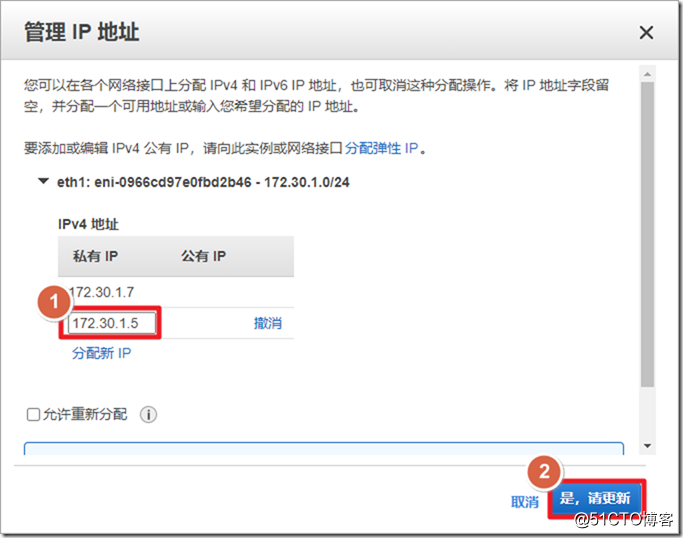
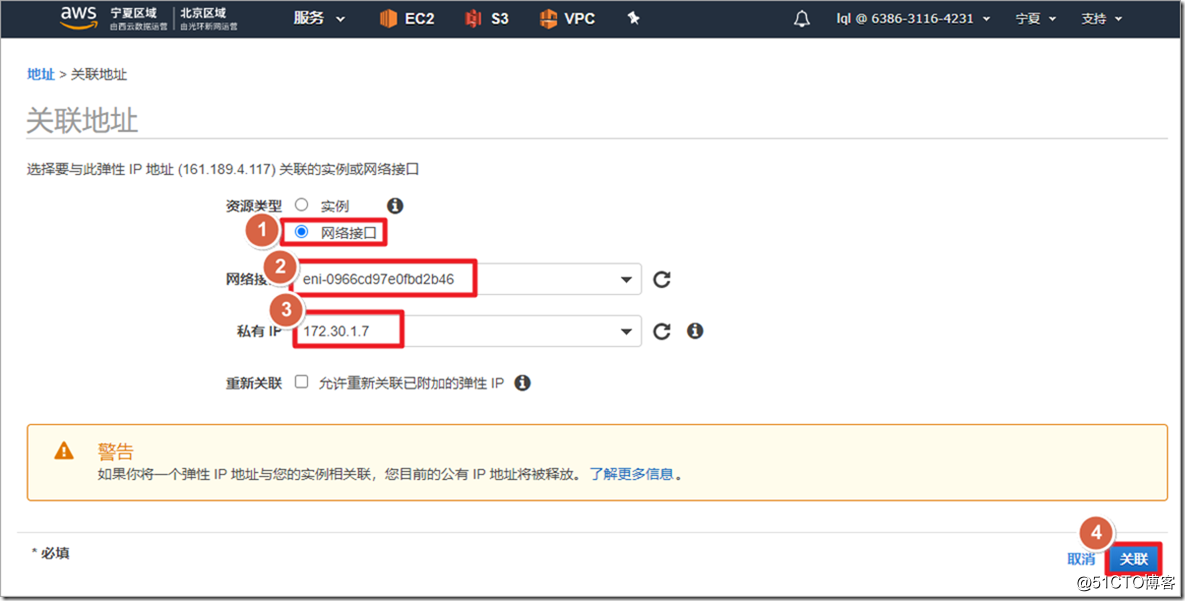
If the client wants to access the server in the private cloud, it cannot directly use the address pool allocated by the ASAv to access, otherwise the server will not have a packet return route. The solution is to do source NAT on the ASAv to convert the source IP address of the client to a secondary IP address on the outside (it cannot be converted to an outside interface address). If it is a vSphere environment, it can be converted to an outside interface address.
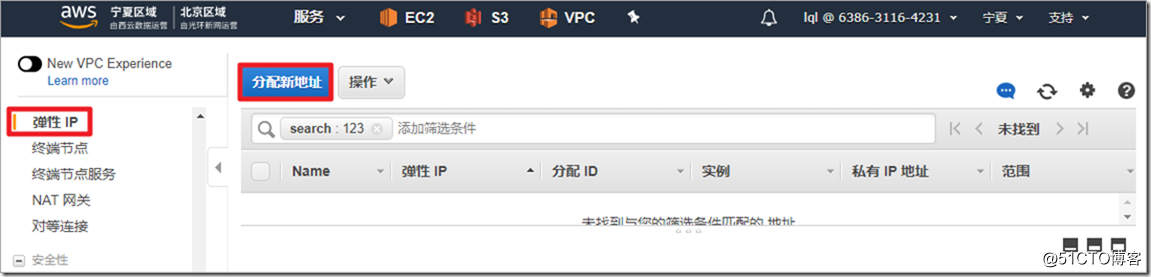
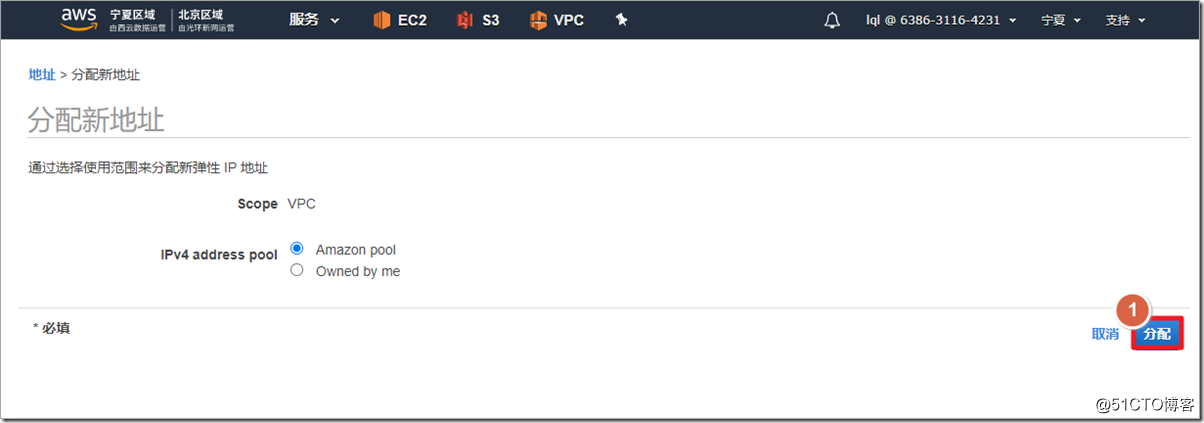
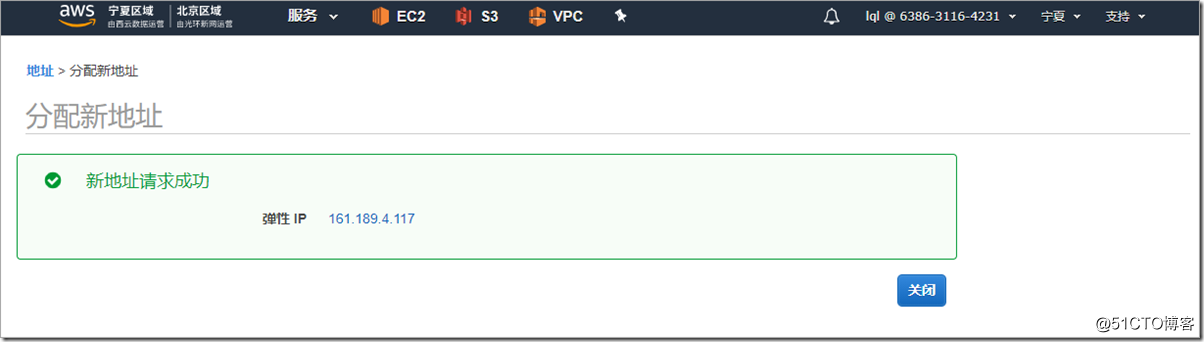
The firewall outside needs to be directly accessible from the public network, so a public network address is required.
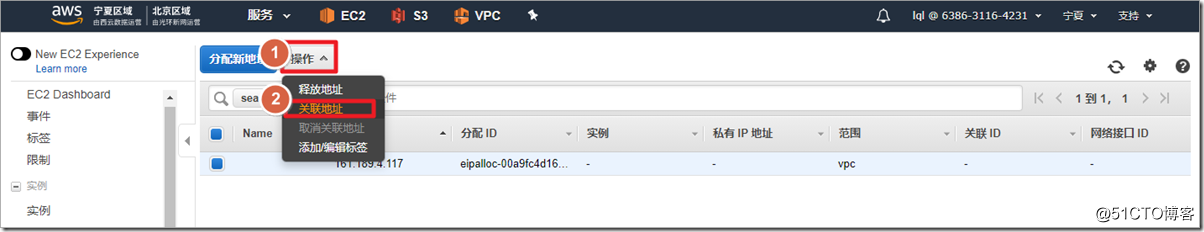
The public network address is associated with the outside interface of the firewall.
After startup, eth0 is the management interface . You can only connect to the management interface during the first connection . If you want to connect to other interfaces, you can configure it after connection.
5. ASAv basic configuration
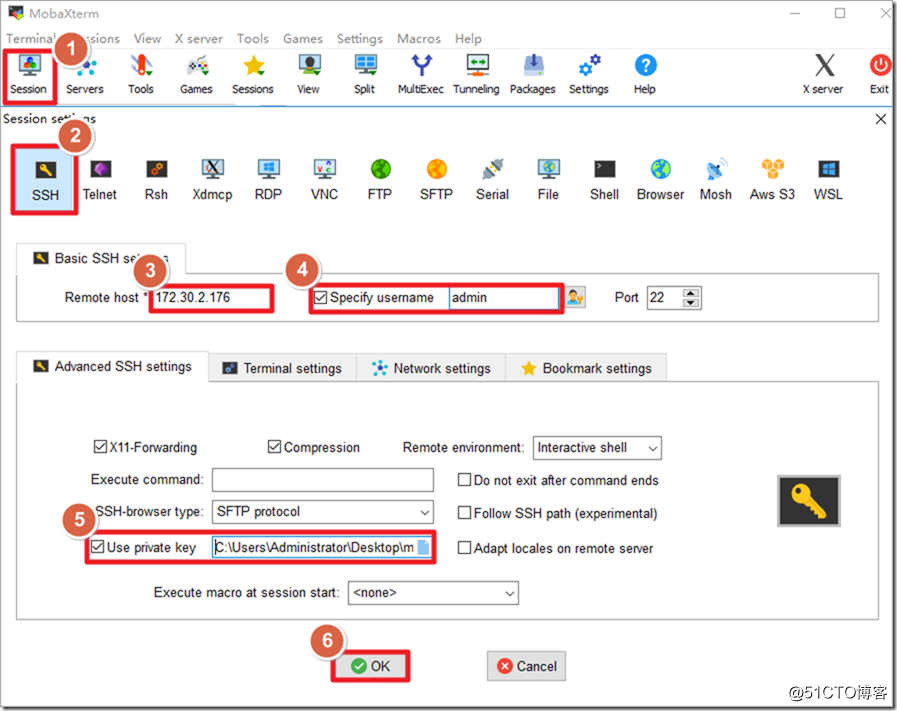
First, connect to the management port of ASAv through SSH for some basic configuration. Here I use it
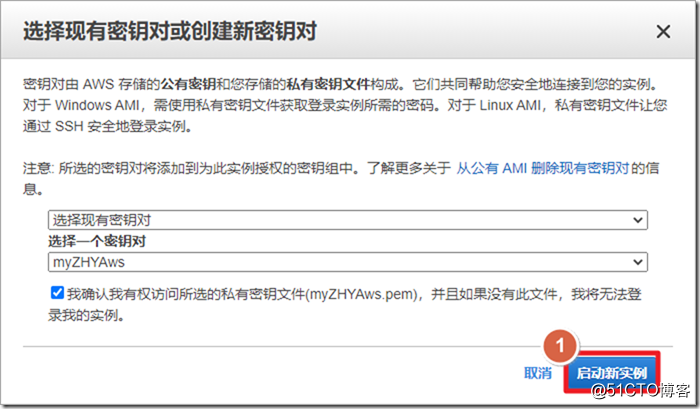
MobaXtermas an SSH client, and the download address will be placed at the end. The default username of the ASAv launched on AWS isadminto log in with the corresponding key.
First, you need to set the enable password
ciscoasa> enable
The enable password is not set. Please set it now.
Enter Password: ****
Repeat Password: ****
Note: Save your configuration so that the password persists across reboots
("write memory" or "copy running-config startup-config").
The added eth1 interface is down by default
ciscoasa# show interface ip brief Interface IP-Address OK? Method Status Protocol Internal-Data0/0 169.254.1.1 YES unset up up Management0/0 172.30.2.176 YES DHCP up up TenGigabitEthernet0/0 172.30.1.7 YES CONFIG administratively down up
Open eth1, the configuration name is outside
interface TenGigabitEthernet0/0 no shutdown nameif outside
To connect to the ASAv through ASDM, you need to enable the http server and allow http traffic to enter from the management port, which
0 0means that the IP address range is not restricted. If you want to only allow http connections on the 192.168.1.0/24 network segment, you can configure http 192.168.1.0 255.255.255.0. Configure the http authentication method to be local authentication, and configure a local 15-level user name and password.
http server enable http 0 0 management aaa authentication http console LOCAL username cisco password ciscoasa privilege 15
Access the management interface address of the ASAv through the web page
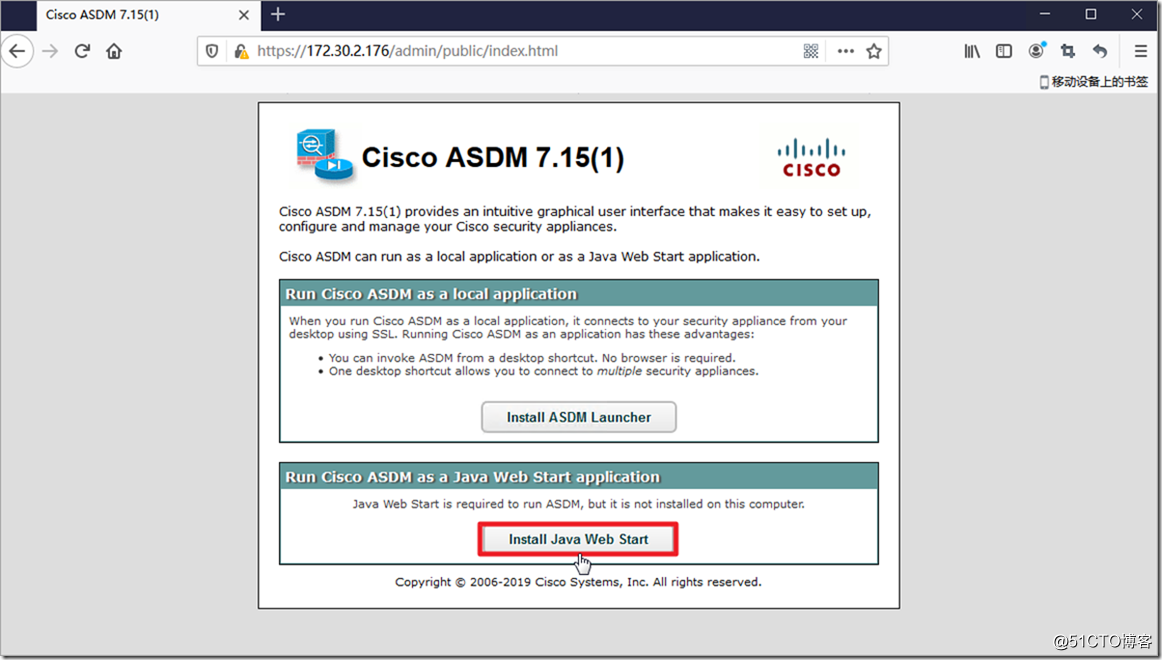
First download and install the Java environment, then download and install the ASDM software.
Download and install the ASDM environment.
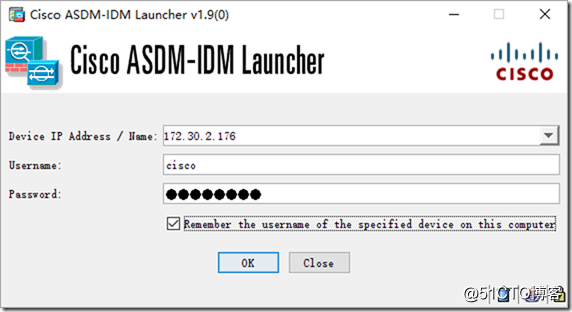
Use the local 15-level account password to log in.
If the ASAv does not import the license, the speed limit is 100Kbps, and the maximum number of sessions is 100 connections.
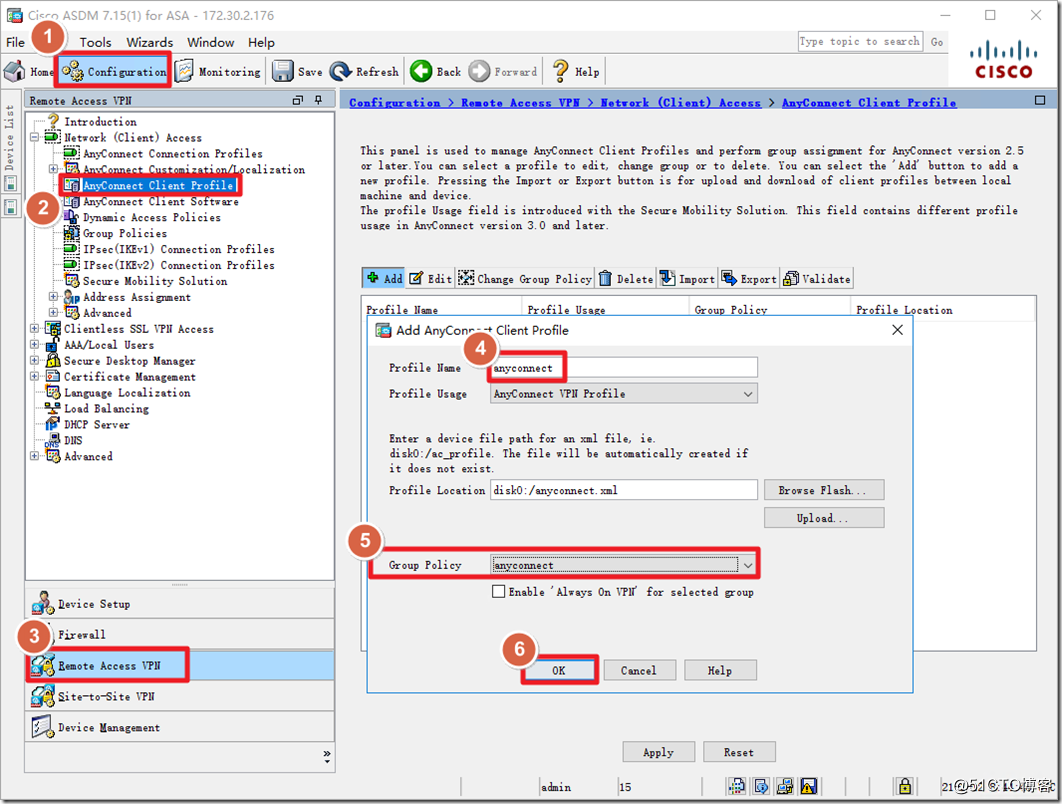
Here, the AnyConnect file is imported through the file management function of ASDM.
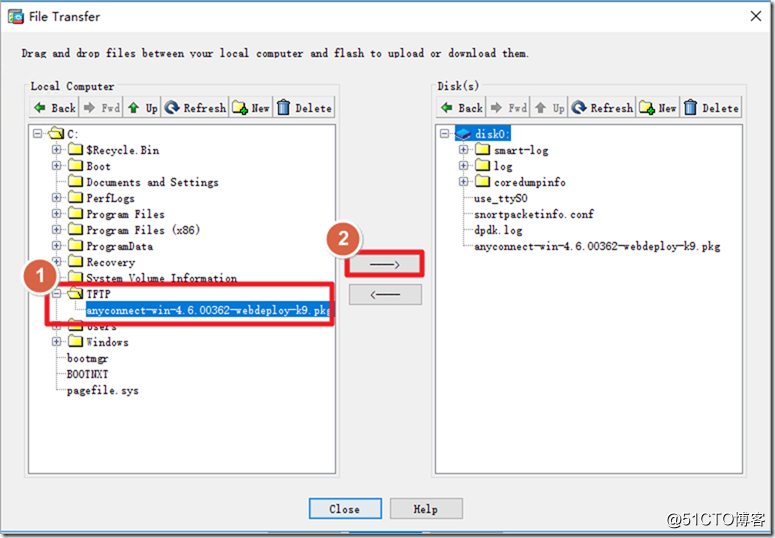
Import the local AnyConnect client file.
Check the disk to confirm that there are client files.
ciscoasa# dir Directory of disk0:/ 86 -rwx 41077110 08:00:10 Jan 12 2021 anyconnect-win-4.6.00362-webdeploy-k9.pkg
6. ASAv configure SSL***
The following is almost a minimal configuration of ASAv on AWS, and the advanced functions of AnyConnect are not discussed here. The meaning of the following command: When the client accesses any other address, the source address is converted to 172.30.1.5.
object network asa_outside_address host 172.30.1.5 object network anyconnect_pool_object subnet 192.168.1.0 255.255.255.0 nat (outside,outside) source dynamic anyconnect_pool_object pat-pool asa_outside_address
By default, the ASAv cannot be accessed at the same security level , and traffic cannot enter and exit from the same interface . You need to enable these two features here.
same-security-traffic permit inter-interface same-security-traffic permit intra-interface
Create client address pool
ip local pool anyconnect_client_pool 192.168.1.1-192.168.1.254 mask 255.255.255.255
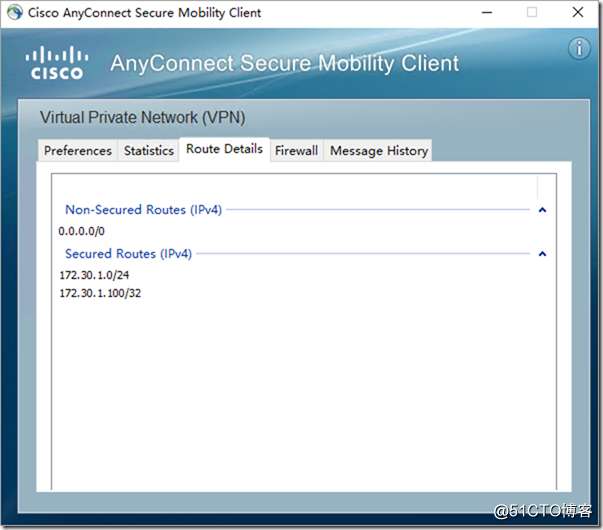
Define the tunnel to separate the address segments. Only when the user accesses 172.30.1.0/24, the traffic will reach the ASAv through the SSL tunnel, and the traffic to other network segments will still go out of the local network.
access-list anyconnect_split standard permit 172.30.1.0 255.255.255.0
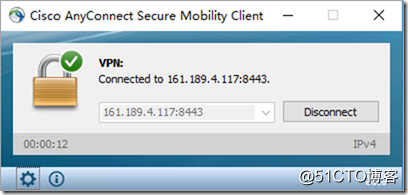
Enable the web*** function, modify the port to 8443 (TCP80/443 cannot be used without ICP filing in AWS China), and activate the anyconnect dial-up function.
web*** port 8443 enable outside anyconnect enable anyconnect image disk0:/anyconnect-win-4.6.00362-webdeploy-k9.pkg
Configure group-policy to allow dial-in through web pages and clients, and define traffic as a tunnel separation mode.
group-policy anyconnect internal group-policy anyconnect attributes ***-tunnel-protocol ssl-client ssl-clientless split-tunnel-policy tunnelspecified split-tunnel-network-list value anyconnect_split address-pools value anyconnect_client_pool
Create a local account for dial test.
username anyuser password ciscoasa username anyuser attributes *** - group-policy anyconnect
Currently, the default route of the firewall is obtained through the management interface DHCP, and the default route needs to be changed to outside. The modification steps are as follows:
Open outside ssh management
Configure the management interface as a static IP, the default route obtained will automatically disappear
Reconnect to ciscoasa through the outside interface
Specify the default route exit as outside
View the existing default route out through the mgmt interface
ciscoasa# show route S* 0.0.0.0 0.0.0.0 [1/0] via 172.30.2.1, management C 172.30.1.0 255.255.255.0 is directly connected, outside L 172.30.1.7 255.255.255.255 is directly connected, outside C 172.30.2.0 255.255.255.0 is directly connected, management L 172.30.2.176 255.255.255.255 is directly connected, management
Allow ssh to connect to the outside interface
ssh 0 0 outside
Configure the management interface as a static address, and the obtained default route will disappear automatically.
interface management 0/0 ip address 172.30.2.176 255.255.255.0
After reconnecting to the outside interface via SSH, add a default route to go out of the outside interface.
route outside 0 0 172.30.1.1
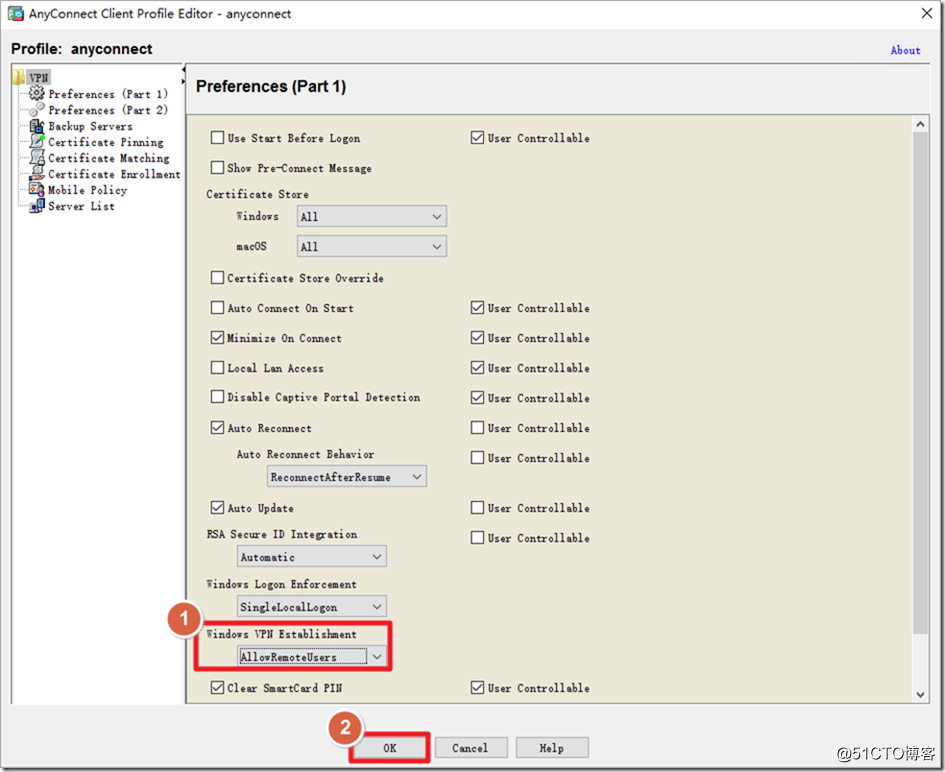
By default, AnyConnect does not allow dialing via remote desktop. You need to create an AnyConnect Client Profile file and edit the parameters inside.
Allow dialing via remote desktop.
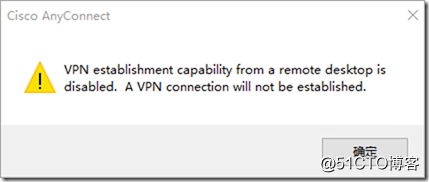
If this parameter is not modified, the following error will be reported after dialing through the remote desktop.
7. Test AnyConnect dial
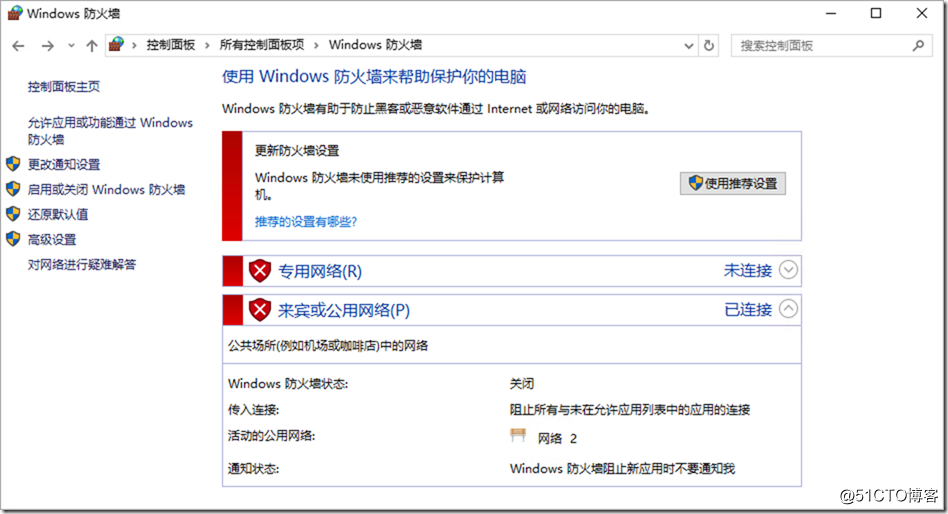
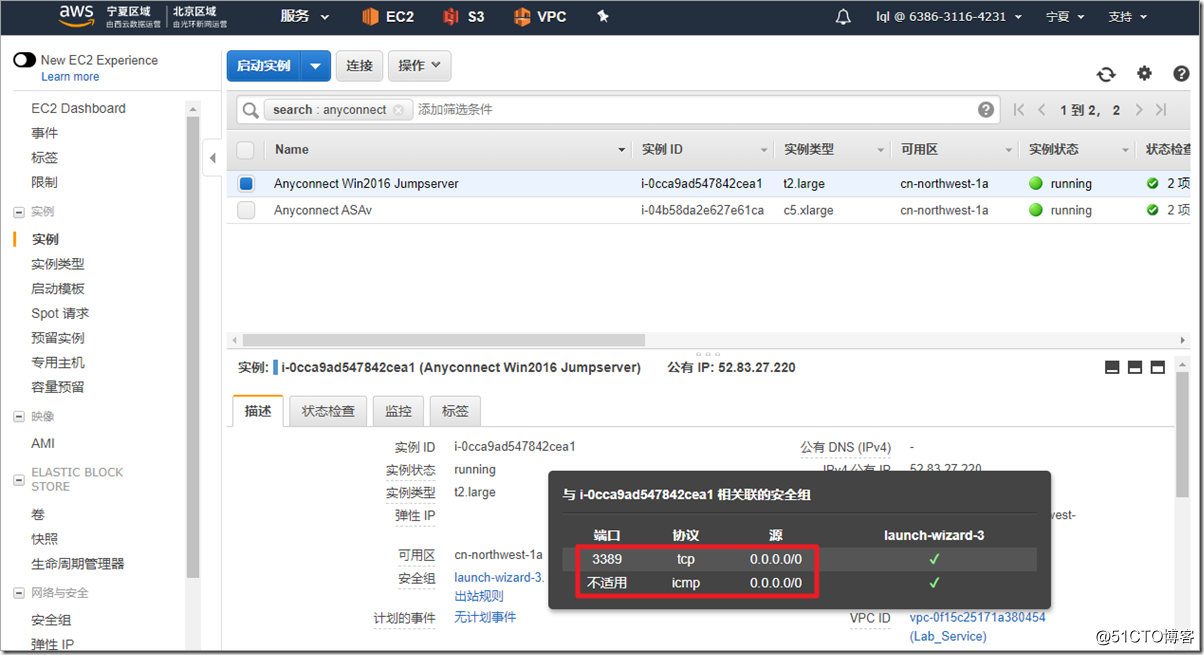
After the dial-up is successful, access to the intranet address of Windows 2016 through the SSL channel can prove that the access is successful. Windows 2016 needs to close the firewall to ping through.
The security group also needs to pass the ICMP protocol.
Successfully dialed on the public network.
The traffic to the 172.30.1.0/24 network segment will be accessed through an encrypted tunnel.
Test access to the intranet Windows2016
C:\Users\Administrator>ping 172.30.1.131 Ping 172.30.1.131 with 32 bytes of data: reply from 172.30.1.131: byte=32 time=1ms TTL=128 reply from 172.30.1.131: byte= 32 Time=1ms TTL=128 Reply from 172.30.1.131: Byte=32 Time=1ms TTL=128 Reply from 172.30.1.131: Byte=32 Time=1ms TTL=128
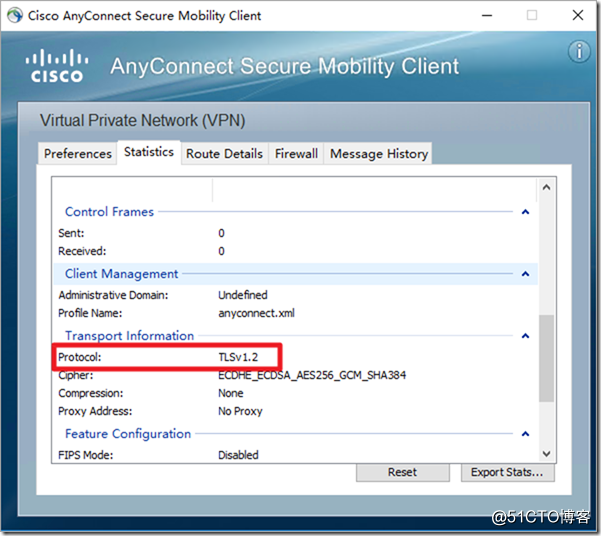
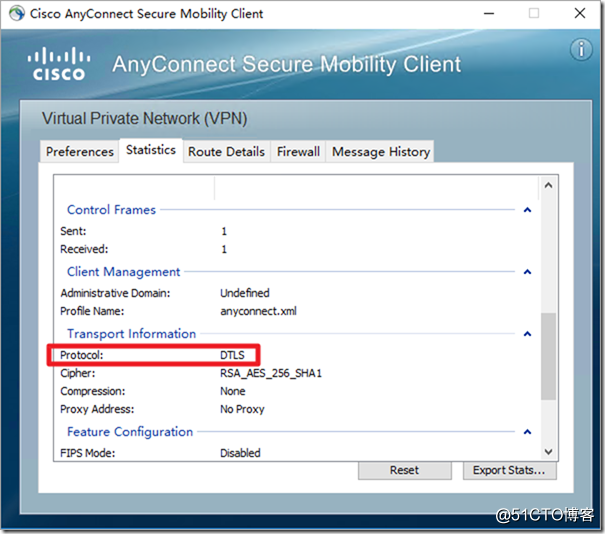
The protocol here is TLS by default, which is the connection established by TCP. If the network environment is not stable and you need to use voice and video traffic, it is recommended to use the DTLS channel , which is UDP connection.
Modify the DTLS port to 8443
web *** dtls port 8443
Enable DTLS under group-policy
group-policy anyconnect attributes web*** anyconnect ssl dtls enable
Redial to view the agreement.
View client information on ASAv
ciscoasa(config)# show ***-sessiondb anyconnect Session Type: AnyConnect Username : anyuser Index : 3 Assigned IP : 192.168.1.1 Public IP : 52.83.196.213 Protocol : AnyConnect-Parent SSL-Tunnel License : AnyConnect Premium Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES-GCM-256 Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA384 Bytes Tx : 18613 Bytes Rx : 7928 Group Policy : anyconnect Tunnel Group : DefaultWEB***Group Login Time : 09:46:43 UTC Tue Jan 12 2021 Duration : 0h:01m:51s Inactivity : 0h:00m:00s VLAN Mapping : N/A VLAN : none Audt Sess ID : ac1e02b0000030005ffd7003 Security Grp : none
1. Mobaxterm download address
2. Java environment download address