OAuth2.0 learning summary
OAuth full name: Open Authorization (Open Authorization Protocol), OAuth2.0 refers to version 2.0 of the Open Authorization Protocol
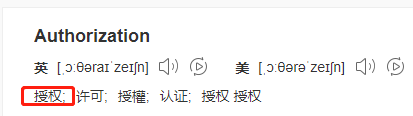
open authorization Open authorization protocol: is a safe and open authorization protocol, an application layer protocol, its function and purpose is to protect resources (protect the safe issuance of resources!) and has a safe and open authorization, a safe and open resource use protection protocol
Essence: Identity authentication protocol and resource protection policy protocol that emphasize and focus on the "authorization" function

Third-party resource users, through the secure and open authorization mode of the resource owner (OAuth2.0 protocol flow), third-party resource users no longer need to touch the original identity credentials of the resource owner (the highest level of identity authentication information: user In the case of name + password), the private resources of the relevant resource owner can be used safely and effectively through the authorization of the resource owner! This is the benefit that OAuth2.0 protocol brings us! (Authorization mode is safe! Open! Lightweight!)
The Open Authorization 2.0 agreement has the following provisions (convention) definitions:
1: Resource owner: usually a person (an account or a user)
![]() , The resource belongs to the user, and the user puts his resource on the resource server. The resource server can identify the legitimacy of the user's identity credential AccessToken (identity token)
, The resource belongs to the user, and the user puts his resource on the resource server. The resource server can identify the legitimacy of the user's identity credential AccessToken (identity token)
----------------------------------------------
2: Resource server: A server that can provide resources or services. The user stores resources belonging to a specific user on the resource server. These resources of the user are protected by the resource server. Only the user's identity information is legally authenticated by the resource server. Users can access their corresponding resources and services. The resource server has the ability to authenticate the user's identity information (validation) (identity authentication comparison). The resource server can authenticate the user's valid identity credentials (user name + password or AccessToken access token) (validity check)
There are many forms of resources, as long as two constraints are guaranteed (1) the resource belongs to a certain user (2) to access the resource belonging to a certain user, the user identity information of the resource server must be authenticated to access these resources

——————————————————————————————
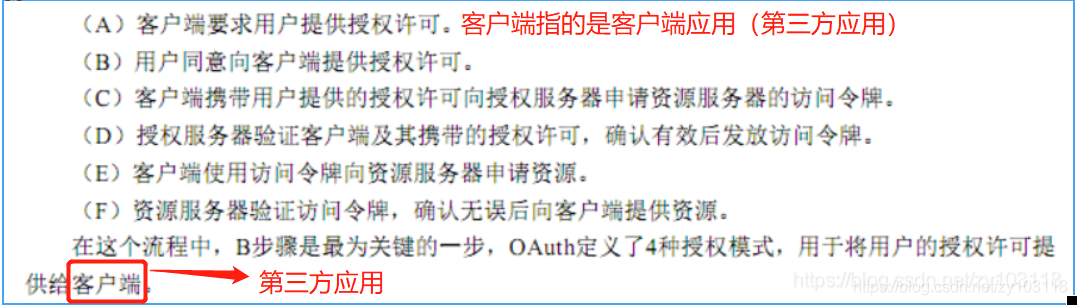
3: Authorization server: A server that can verify the authorization code or authenticate and verify whether the content authorized by the user is legal. For example, if the user authorizes something, it will temporarily replace the user's deity. I will go to the resource server to check For a thing, then the user should give this thing an authorization credential, indicating that the thing is authorized by the user. The authorized thing takes the user’s authorization credential and runs to the authorization server. The authorization server knows the authenticity of the authorization credentials. Fake, if the authorization credential is authenticated by the authorization server, the authorization server will return an AccessToken (access token) to the authorized person, and the authorized person can look up the resource server on behalf of the user with this access token AccessToken The user's resources are gone (the authorized person takes the AccessToken token to the resource server to ask for resources)
The authorization server is an authorization tool for users to authorize other client applications! ! Only authorized server users can perform authorization. The user will log in to the authorization server with his own legal identity credentials to perform authorization operations. When the identity authentication is passed, the authorization server will provide the user with an authorization code, which the customer must pass directly or indirectly. To the authorized person (usually a third-party application (client application) that applies for authorization from the user), the authorized person holds the authorization code given to it by the user and exchanges the user's identity token AccessToken to the authorization server (this thing represents the user The legal identity of the resource server and the authentication validity check of the AccessToken)

——————————————————————————
4: Client application: I want to get user authorization, and I want to temporarily represent the user's deity, and I want to obtain such a greedy third-party application that belongs to a specific user resource from the resource server! If he wants to find resources on the resource server on behalf of the user, he must get the user’s authorization. When the user authorizes the client application, he usually provides a legal authorization code to the client application through some means. The application takes the authorization code and goes to the authorization server to ask for AccessToken. Only AccessToken can represent the legal identity of the user on the resource server. The authorization code only represents a credential for user authorization. The resource server does not recognize the authorization code but only recognizes the AccessToken. The authorization server recognizes the authorization code. The authorization code will be bound to the user's identity credentials (user name + password) and (AccessToken). When a third-party application sends the authorization code provided by the user to the authorization server, the authorization server will The code gets the corresponding user identity certificate AccessToken and sends it to this third-party client application! Let the third-party client application represent a specific user, and the third-party client application that has obtained the AccessToken will be proud. He can ask the resource server for the user's resources, because whoever has the AccessToken represents the possession of the user's deity!
![]()
——————————————————————————————————————
5: Resource owner agent: a tool that represents the user's action behavior (it can be understood as the avatar of the user in a certain field). This avatar is usually a browser in the network. In short, it can represent such a thing or object of the user.
It can be understood as the avatar of the user. If the user uses a browser to interact with the authorization server, one cannot let a person yell at the server by shouting. The user agent is usually a GUI tool.
6: User identity information (1 username and password, 2 identity token (AccessToken)) usually in these two forms
————————————————————————————————————————————————
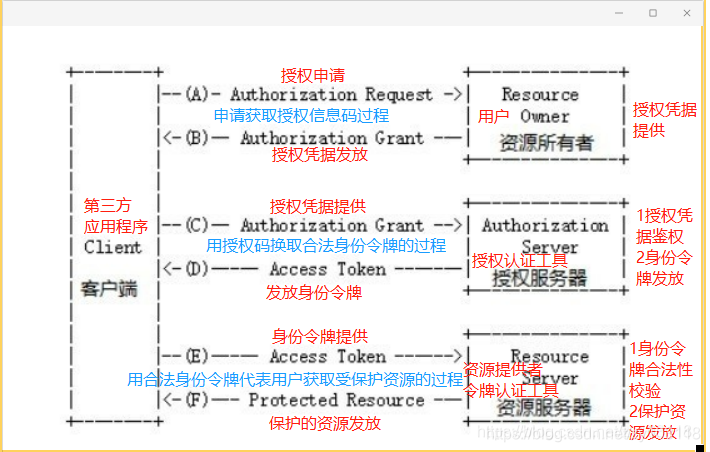
Graphical description of the agreement:
![]()
The following is an abstract description of the agreement. The specific implementation depends on the specific implementation of the specific software tool product. The agreement and the agreement software are the abstract concept of the agreement and the specific realization of the specific software product. Generally, there will be behaviors that look like but the specific methods will be. With the realization of specific software products slightly different