This sharing is only for learning and communication, please consciously abide by laws and regulations!
Search: Kali and programming, learn more online*** dry goods!
The next article will be published at 5 o'clock tomorrow afternoon, so stay tuned!
Use Metasploit*** framework for FTP service scanning
1. Background introduction
FTP is used to transfer files between two computers, and it is one of the most widely used services in the Internet. It can set the usage rights of each user according to actual needs, and it also has cross-platform features, that is, FTP clients and servers can be implemented in operating systems such as UNIX, Linux, and Windows, and files can be transferred between each other across platforms . Therefore, FTP service is one of the resource sharing methods often used in the network. The FTP protocol has two working modes: PORT and PASV, namely, active mode and passive mode.
FTP (File Transfer Protocol) is a file transfer protocol, which is a TCP-based protocol that uses a client/server model. Through the FTP protocol, users can upload or download files on the FTP server. Although there are many sites downloading through HTTP protocol, FTP protocol can well control the number of users and bandwidth distribution, and upload and download files quickly and conveniently. Therefore, FTP has become the preferred server for file upload and download in the network. At the same time, it is also an application program through which users can connect their computers with all servers running FTP protocol around the world, and access a large number of programs and information on the servers. The function of FTP service is to realize the remote transmission of complete files.
2. Resource equipment
1. One virtual machine with Kali Linux installed;
2. One victim virtual machine;
3. One Xiaobai who is ready to go.
3. Strategic Arrangement
3.1 Configure a firewall on the victim's Win2008 Server virtual machine (turn off the firewall), as shown in the figure below.
Command: Win+R/cmd/firewall.cpl 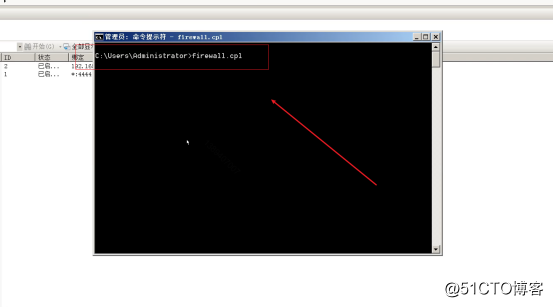
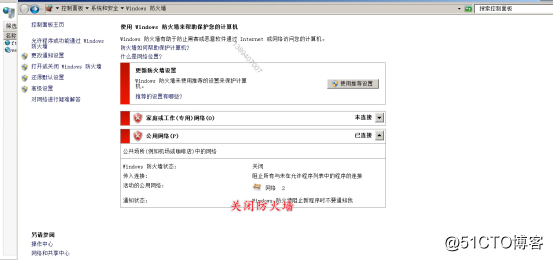
3.2 Open the Postgresql database on the *** host (Kali Linux host), as shown in the figure below.
Command: service postgresql start 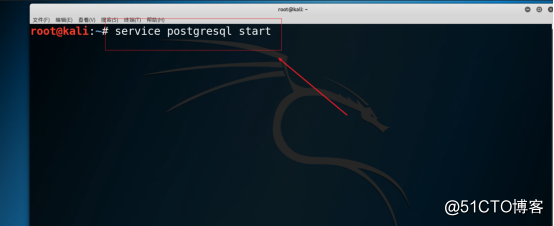
3.3 Open the Metasploit (msf)*** framework on the Kali Linux host on the VPN side, as shown in the figure below.
Command: msfconsole
3.4 Use the nmap plug-in of Metasploit (msf)*** framework to scan the victim's host, as shown in the figure below.
Command: nmap -p 21 192.168.78.165 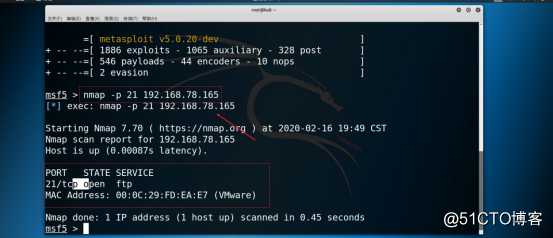
3.5 Retrieve ftp service related vulnerabilities, as shown in the figure below.
Command: search ftp_version 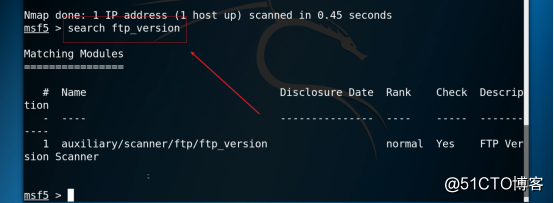
3.6 Use the retrieved ftp related vulnerability exploit module, as shown in the figure below.
Command: use auxiliary/scanner/ftp/ftp_version
3.7 View the configuration information of the ftp exploit module, as shown in the figure below.
Command: show options 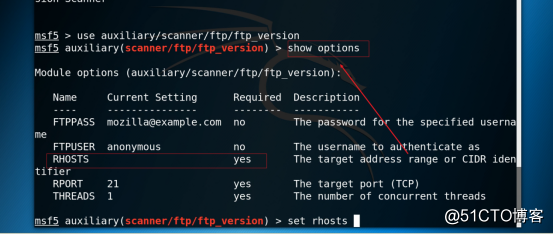
3.8 Configure rhosts parameters, as shown in the figure below.
Command: set rhosts 192.168.78.165 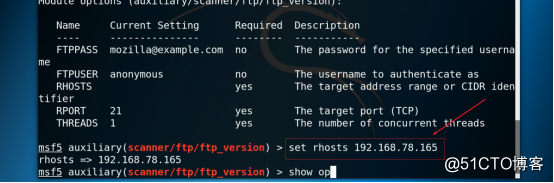
3.9 Check whether the above parameters are successfully configured, as shown in the figure below.
Command: show options 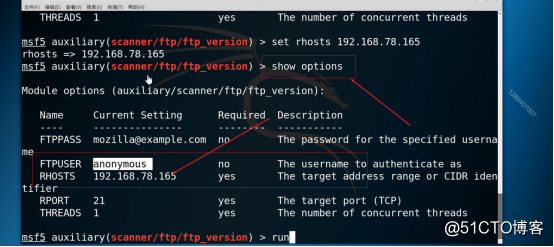
3.10 Run the exploit module, as shown in the figure below.
Command: run 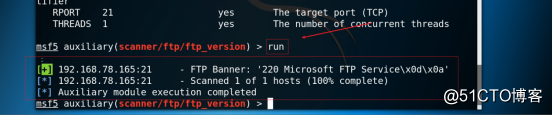
3.11 Exit the current exploit module and return to the previous layer, as shown in the figure below.
Command: back
3.12 View ftp related vulnerabilities and perform fuzzy query as shown in the figure below.
Command: search /ftp/an 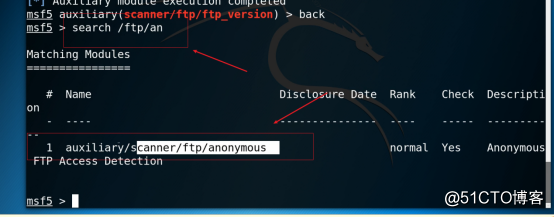
3.13 Use the retrieved vulnerability module, as shown in the figure below.
Command: use auxiliary/scanner/ftp/anonymous
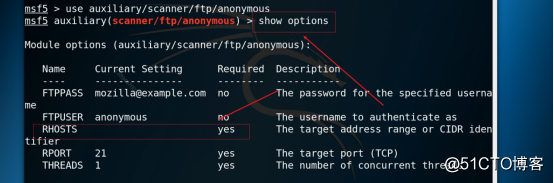
3.14 View configuration information, as shown in the figure below.
Command: show options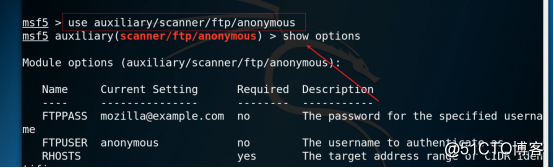
3.15 Set rhosts parameter information, as shown in the figure below.
Command: set rhosts 192.168.78.165 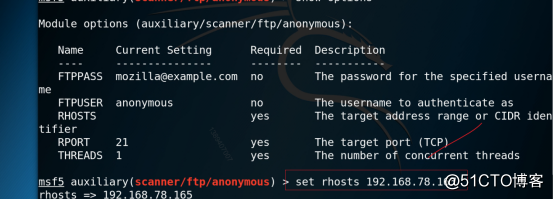
3.16 Run the exploit module, as shown in the figure below.
Command: run 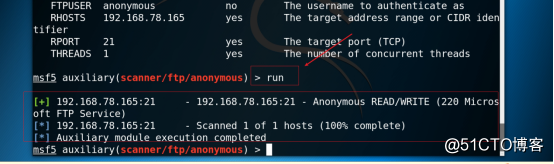
PS: This is the end of the study, thank you for watching, please continue to pay attention to this number for more dry goods!
Hard work and originality, everyone, please remember to praise and pay attention! You can also search: Kali and programming, learn more Kali Linux*** and white hat programming skills!
Click me to learn more Kali Linux*** testing and network*** practical skills! Please add link description