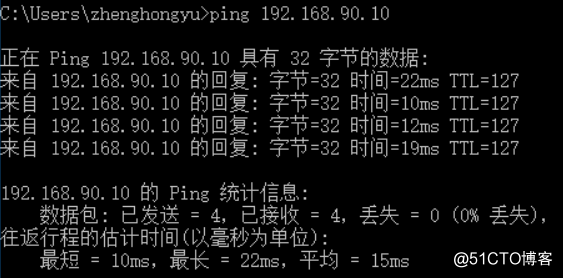
一、实验配置图及要求
在路由上建立ACL扩展的配置要求如下:
1、允许PC1访问Linux的web服务
2、允许PC2访问Linux的ftp服务
3、禁止PC1与PC2访问Linux的其它服务
4、允许PC1访问PC2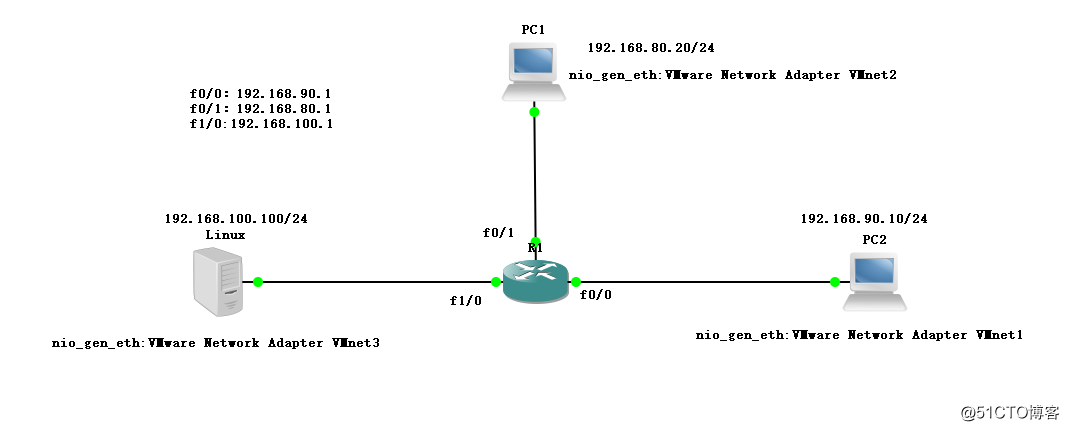
二、实验环境部署
1、pc1、pc2以及Linux系统均设置静态IP、子掩及网关,并且进行对应的网卡绑定。
2、完成Linux服务器相关服务的安装与启动
[root@localhost ~]# yum install vsftpd -y //安装ftp服务
[root@localhost ~]# yum install httpd -y //安装http服务
[root@localhost ~]# systemctl stop firewalld.service //关闭防火墙
[root@localhost ~]# setenforce 0 //关闭增强性安全功能
[root@localhost ~]# systemctl start httpd //启动服务
[root@localhost ~]# systemctl start vsftpd
[root@localhost ~]# netstat -ntap | egrep '(21|80)' //检查服务启动状况(80端口为http,21端口为ftp)
tcp6 0 0 :::80 :::* LISTEN 6399/httpd
tcp6 0 0 :::21 :::* 3、路由的配置:三个端口设置IP
R1#conf t
R1(config)#int f 0/0
R1(config-if)#ip add 192.168.90.1 255.255.255.0
R1(config-if)#no shut
R1(config-if)#int f 0/1
R1(config-if)#ip add 192.168.80.1 255.255.255.0
R1(config-if)#no shut
R1(config-if)#int f 1/0
R1(config-if)#ip add 192.168.100.1 255.255.255.0
R1(config-if)#no shut
R1(config-if)#ex
R1(config)#do show ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
C 192.168.90.0/24 is directly connected, FastEthernet0/0
C 192.168.80.0/24 is directly connected, FastEthernet0/1
C 192.168.100.0/24 is directly connected, FastEthernet1/04、进行扩展ACL的配置
R1(config)#access-list 100 permit tcp 192.168.80.20 0.0.0.255 192.168.100.100 0.0.0.255 eq 80
R1(config)#access-list 100 permit tcp host 192.168.90.10 host 192.168.100.100 eq 21
R1(config)#access-list 100 permit ip host 192.168.80.20 192.168.90.0 0.0.0.255
R1(config)#do show access-list
Extended IP access list 100
10 permit tcp 192.168.80.0 0.0.0.255 192.168.100.0 0.0.0.255 eq www
20 permit tcp host 192.168.90.10 host 192.168.100.100 eq ftp
30 permit ip host 192.168.80.20 192.168.90.0 0.0.0.255
R1(config)#int f0/1
R1(config-if)#ip access-group 100 in
R1(config-if)#int f0/0
R1(config-if)#ip access-group 100 in
R1(config-if)#ex 5、结果测试
pc1可以访问web网站服务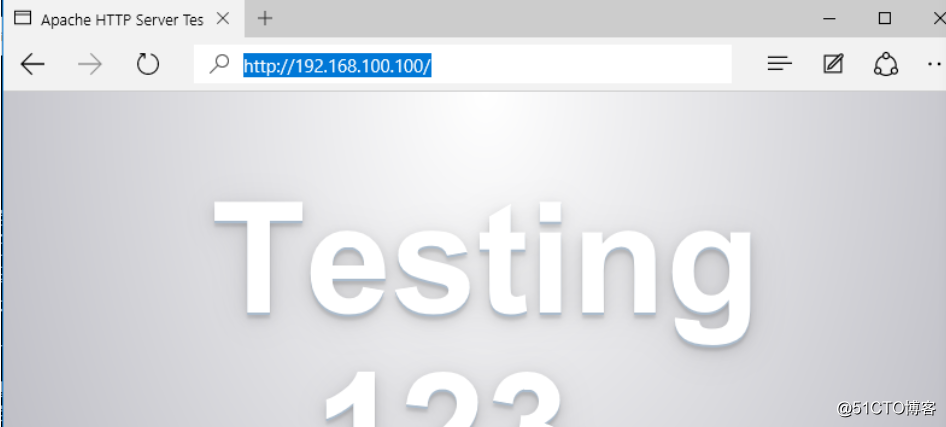
pc2可以访问ftp服务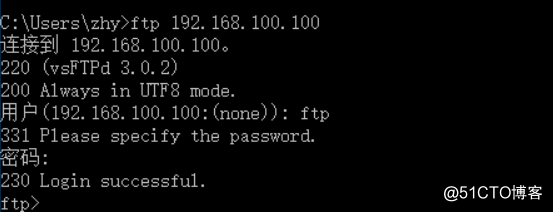
允许pc1访问pc2