Cloudify4.5.0和Kubernetes1.13.0进行混合容器编排demo,并通过Ingress暴露服务
Kubernetes的其中一种外部访问方式:Ingress[nginx]
#Ingress:
Ingress 事实上不是一种服务类型。相反,它处于多个服务的前端,扮演着“智能路由”或者集群入口的角色。
你可以用 Ingress 来做许多不同的事情,各种不同类型的 Ingress 控制器也有不同的能力.
Ingress由两部分组成:Ingress Controller 和 Ingress 服务。 ingress控制器有两种:nginx和haproxy
Ingress Contronler 通过与 Kubernetes API 交互,动态的去感知集群中 Ingress 规则变化,然后读取它,
按照自定义的规则,规则就是写明了哪个域名对应哪个service,生成一段 Nginx 配置,再写到
Nginx-ingress-control的 Pod 里,这个 Ingress Contronler 的pod里面运行着一个nginx服务,
控制器会把生成的nginx配置写入/etc/nginx.conf文件中,然后 reload 一下 使用配置生效.
K8s中用deployment方式部署traefik来进行服务发布,并通过Ingress暴露服务
准备、了解工作:
用traefik进行服务发布。Traefik采用daemonset方式部署,连接api-server走的是http协议,也未配置rbac。
本文将介绍在k8s 1.9版本中使用deployment方式部署traefik来进行服务发布。
在开始之前,需要先了解一下什么是RBAC。
RBAC(基于角色的访问控制)使用 rbac.authorization.k8s.io API 组来实现权限控制,
RBAC 允许管理员通过 Kubernetes API 动态的配置权限策略。在 1.6 版本中 RBAC 还处于 Beat 阶段,
如果想要开启 RBAC 授权模式需要在 apiserver 组件中指定 --authorization-mode=RBAC 选项。
在 RBAC API 的四个重要概念:
Role:是一系列的权限的集合,例如一个角色可以包含读取 Pod 的权限和列出 Pod 的权限
ClusterRole: 跟 Role 类似,但是可以在集群中到处使用( Role 是 namespace 一级的)
RoloBinding:把角色映射到用户,从而让这些用户继承角色在 namespace 中的权限。
ClusterRoleBinding: 让用户继承 ClusterRole 在整个集群中的权限。
简单点说RBAC实现了在k8s集群中对api-server的鉴权,更多的RBAC知识点请查阅官方文档:https://kubernetes.io/docs/admin/authorization/rbac/
1、给集群的节点打上label
因为选择deployment方式部署,所以要给集群的节点打上label,后续选择nodeSelector指定traefik=proxy,副本数和集群节点数一致的时候,所有的节点上都会运行一个pod
# kubectl get nodes --show-labels
# kubectl label node 你的node名称 traefik=proxy
# kubectl label node 你的node名称 traefik=proxy
# kubectl get nodes --show-labels
2.第一个是要部署RBAC文件,文件可以直接从云盘下载,稍加修改
链接:https://pan.baidu.com/s/1eKz7TLjX0YNH4-ymJum-YQ 密码:ump0
# cat traefik-rbac.yaml
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: traefik-ingress-controller
rules:
- apiGroups:
- ""
resources:
- services
- endpoints
- secrets
verbs:
- get
- list
- watch
- apiGroups:
- extensions
resources:
- ingresses
verbs:
- get
- list
- watch
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: traefik-ingress-controller
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: traefik-ingress-controller
subjects:
- kind: ServiceAccount
name: traefik-ingress-controller
namespace: kube-system
注意:小提示
在启用rbac的环境下,如果鉴权未配置清楚,则traefik pod会报错如下
E0226 00:15:27.729832 1 reflector.go:199] github.com/containous/traefik/vendor/k8s.io/client-go/tools/cache/reflector.go:94: Failed to list *v1.Service: services is forbidden: User "system:serviceaccount:kube-system:default" cannot list services at the cluster scope
E0226 00:15:29.013298 1 reflector.go:199] github.com/containous/traefik/vendor/k8s.io/client-go/tools/cache/reflector.go:94: Failed to list *v1.Endpoints: endpoints is forbidden: User "system:serviceaccount:kube-system:default" cannot list endpoints at the cluster scope
E0226 00:15:29.213354 1 reflector.go:199] github.com/containous/traefik/vendor/k8s.io/client-go/tools/cache/reflector.go:94: Failed to list *v1.Secret: secrets is forbidden: User "system:serviceaccount:kube-system:default" cannot list secrets at the cluster scope
E0226 00:15:29.698574 1 reflector.go:199] github.com/containous/traefik/vendor/k8s.io/client-go/tools/cache/reflector.go:94: Failed to list *v1beta1.Ingress: ingresses.extensions is forbidden: User "system:serviceaccount:kube-system:default" cannot list ingresses.extensions at the cluster scope
E0226 00:15:30.411837 1 reflector.go:199] github.com/containous/traefik/vendor/k8s.io/client-go/tools/cache/reflector.go:94: Failed to list *v1.Service: services is forbidden: User "system:serviceaccount:kube-system:default" cannot list services at the cluster scope
E0226 00:15:31.912887 1 reflector.go:199] github.com/containous/traefik/vendor/k8s.io/client-go/tools/cache/reflector.go:94: Failed to list *v1.Endpoints: endpoints is forbidden: User "system:serviceaccount:kube-system:default" cannot list endpoints at the cluster scope
- traefik的deployment文件,注意这里使用了镜像:
== image: 10.10.31.205/szy/traefik ==
# cat traefik-deployment.yaml
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: traefik-ingress-controller
namespace: kube-system
---
kind: Deployment
apiVersion: extensions/v1beta1
metadata:
name: traefik-ingress-controller
namespace: kube-system
labels:
k8s-app: traefik-ingress-lb
spec:
replicas: 2
selector:
matchLabels:
k8s-app: traefik-ingress-lb
template:
metadata:
labels:
k8s-app: traefik-ingress-lb
name: traefik-ingress-lb
spec:
serviceAccountName: traefik-ingress-controller
hostNetwork: true
terminationGracePeriodSeconds: 60
containers:
- image: 10.10.31.205/szy/traefik
name: traefik-ingress-lb
ports:
- name: web
containerPort: 80
hostPort: 80
- name: admin
containerPort: 8081
args:
- --web
- --web.address=:8081
- --kubernetes
4.traefik的service文件
# cat traefik-service.yaml
apiVersion: v1
kind: Service
metadata:
name: traefik-web-ui
namespace: kube-system
spec:
selector:
k8s-app: traefik-ingress-lb
ports:
- port: 80
targetPort: 8081
5.通过yaml文件创建clusterrole、clusterrolebinding、deployment、serviceaccount、service
下载刚才的文件,或者从页面粘走,生成有效的文件,执行create操作:
# kubectl create -f traefik-rbac.yaml
# kubectl create -f traefik-deployment.yaml
# kubectl create -f traefik-service.yaml
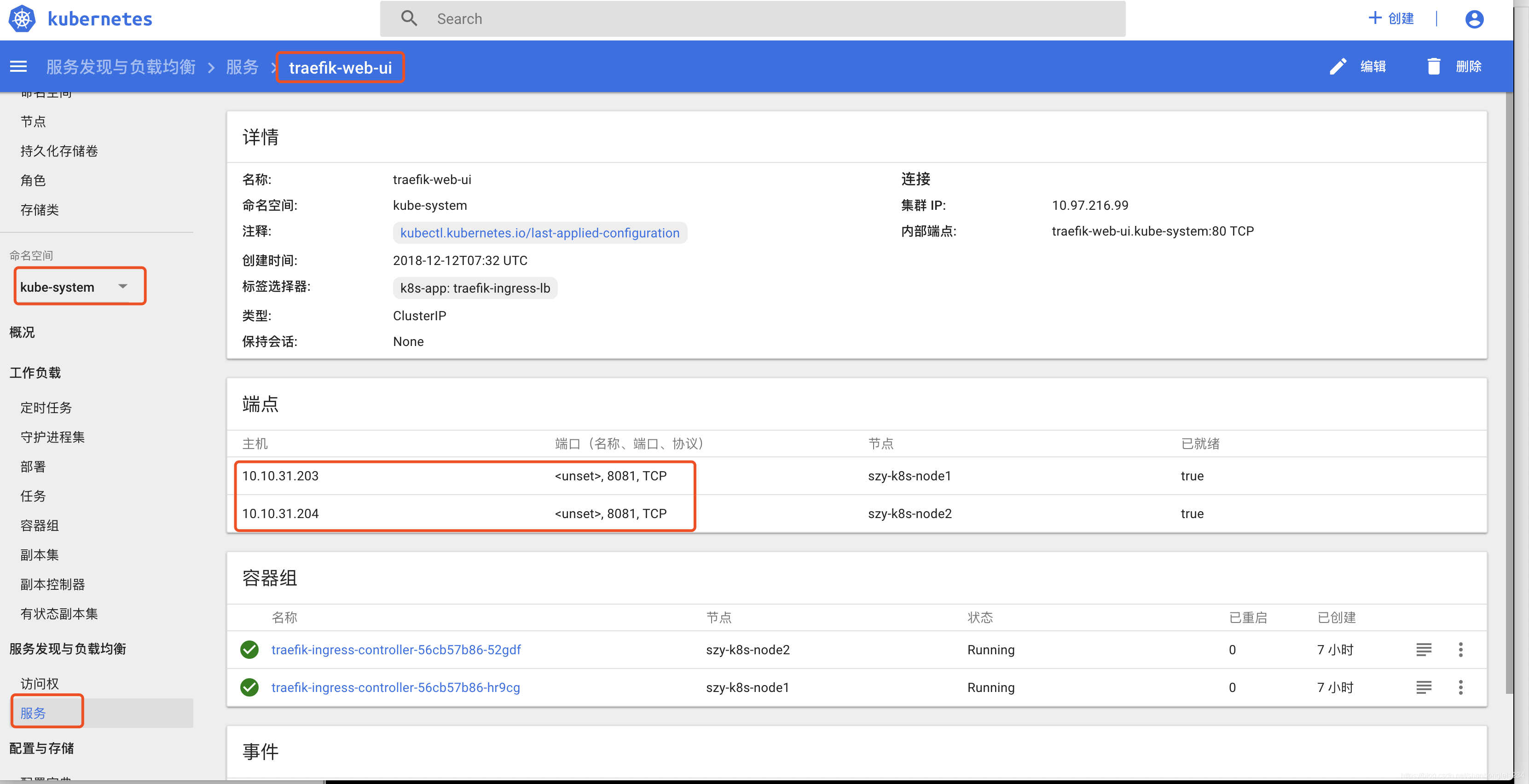
# kubectl get pod -n kube-system
# kubectl get svc -n kube-system
# kubectl get svc
6.可以看到集群中default namespace中存在一个frontend服务。kube-system namespace中存在nginx-test、traefik-web-ui、kubernetes-dashboard三个服务。我们后续将创建4个ingress
7.通过yaml文件创建ingress
# cat ui.yaml
apiVersion: v1
kind: Service
metadata:
name: traefik-web-ui
namespace: kube-system
spec:
selector:
k8s-app: traefik-ingress-lb
ports:
- port: 80
targetPort: 8081
---
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: traefik-web-ui
namespace: kube-system
annotations:
kubernetes.io/ingress.class: traefik
spec:
rules:
- host: traefik-ui
http:
paths:
- backend:
serviceName: traefik-web-ui
servicePort: 80
7.cat webui-ing.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: traefik-ingress
namespace: kube-system
annotations:
kubernetes.io/ingress.class: traefik
spec:
rules:
- host: k8s.webui
http:
paths:
- backend:
serviceName: kubernetes-dashboard
servicePort: 443
8.执行创建ui.yaml 、webui-ing.yaml
# kubectl create -f ui.yaml
# kubectl create -f webui-ing.yaml
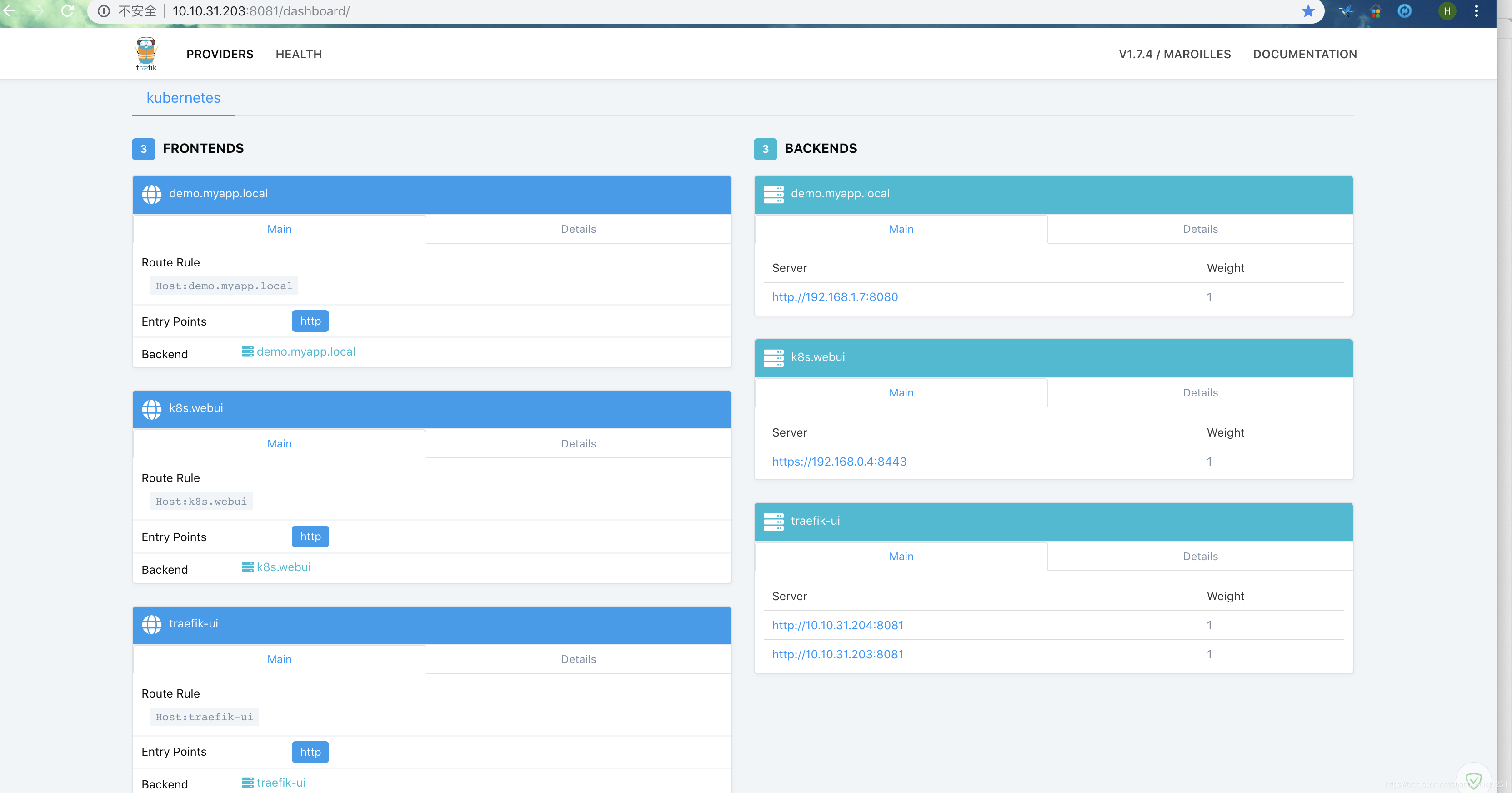
#配置好traefik和ingress后,ui展示效果:
10.10.31.203:8081
10.10.31.204:8081
Cloudify 创建tomcat8-5-cst-ingress蓝图
&:Cloudify 创建tomcat8-5-cst-ingress蓝图然后将容器服务通过ingress 展示出来,这里只配置域名,就可以访问我们的应用了。
&:tomcat8-5-cst-ingress这个蓝图有一点变化,就是不能重复的名字,提出来了,每次本所蓝图创建deployment时,不用再担心会重复名称了。
&:镜像:10.10.31.205/szy/tomcat8-5-cst

tosca_definitions_version: cloudify_dsl_1_3
imports:
- 'http://www.getcloudify.org/spec/cloudify/4.5/types.yaml'
- 'plugin:cloudify-kubernetes-plugin'
inputs:
kubernetes_master_configuration:
default:
apiVersion: v1
kind: Config
preferences: {}
current-context: kubernetes-admin@kubernetes
clusters:
- name: kubernetes
cluster:
certificate-authority-data:
get_secret: kubernetes_cloud_certificate_authority_data
server:
concat:
- 'https://'
- get_secret: kubernetes_cloud_master_ip
- ':'
- get_secret: kubernetes_master_port
contexts:
- name: kubernetes-admin@kubernetes
context:
cluster: kubernetes
user: kubernetes-admin
users:
- name: kubernetes-admin
user:
client-certificate-data:
get_secret: kubernetes-admin_cloud_client_certificate_data
client-key-data:
get_secret: kubernetes-admin_cloud_client_key_data
Deployment-name:
default: null
App-name:
default: null
Service-name:
default: App-service
Containers-name:
default: tomcat
Image-name:
default: 10.10.31.205/szy/tomcat8-5-cst
Service-port:
default: 80
Target-port:
default: 8080
Replicas:
default: 1
Domain-name:
default: demo.myapp.local
node_types:
cloudify.kubernetes.resources.Ingress:
derived_from: cloudify.kubernetes.resources.CustomBlueprintDefinedResource
properties:
api_mapping:
default:
create:
api: ExtensionsV1beta1Api
method: create_namespaced_ingress
payload: V1beta1Ingress
read:
api: ExtensionsV1beta1Api
method: read_namespaced_ingress
delete:
api: ExtensionsV1beta1Api
method: delete_namespaced_ingress
payload: V1DeleteOptions
update:
api: ExtensionsV1beta1Api
method: patch_namespaced_ingress
node_templates:
kubernetes_master:
type: cloudify.kubernetes.nodes.Master
properties:
configuration:
file_content:
get_input: kubernetes_master_configuration
relationships: []
App_deployment:
type: cloudify.kubernetes.resources.Deployment
properties:
definition:
apiVersion: extensions/v1beta1
kind: Deployment
metadata:
name:
get_input: Deployment-name
spec:
selector:
matchLabels:
app:
get_input: App-name
replicas:
get_input: Replicas
template:
metadata:
labels:
app:
get_input: App-name
spec:
containers:
- name:
get_input: Containers-name
image:
get_input: Image-name
ports:
- containerPort:
get_input: Target-port
relationships:
- type: cloudify.kubernetes.relationships.managed_by_master
target: kubernetes_master
App_service:
type: cloudify.kubernetes.resources.Service
properties:
definition:
apiVersion: v1
kind: Service
metadata:
name:
get_input: Service-name
spec:
ports:
- port:
get_input: Service-port
targetPort:
get_input: Target-port
selector:
app:
get_input: App-name
relationships:
- type: cloudify.kubernetes.relationships.managed_by_master
target: kubernetes_master
- type: cloudify.relationships.depends_on
target: App_deployment
tomcat_ingress:
type: cloudify.kubernetes.resources.Ingress
properties:
definition:
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name:
get_input: Service-name
annotations:
kubernetes.io/ingress.class: traefik
spec:
rules:
- host:
get_input: Domain-name
http:
paths:
- backend:
serviceName:
get_input: Service-name
servicePort: 80
relationships:
- type: cloudify.kubernetes.relationships.managed_by_master
target: kubernetes_master
- type: cloudify.relationships.depends_on
target: App_service
根据刚才创建的蓝图,创建deployment,如下图,记得输入框中填写需要内容
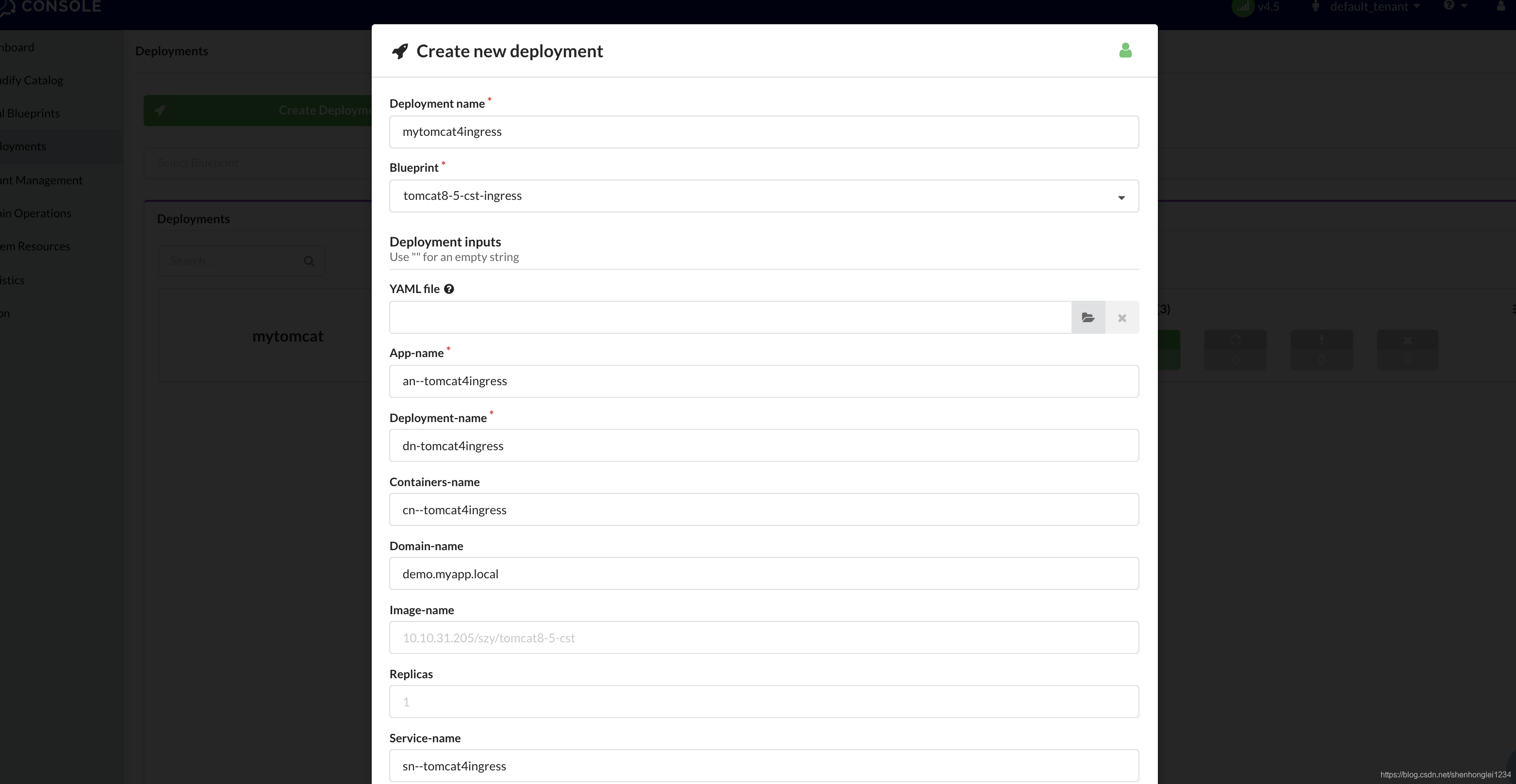
Deploy
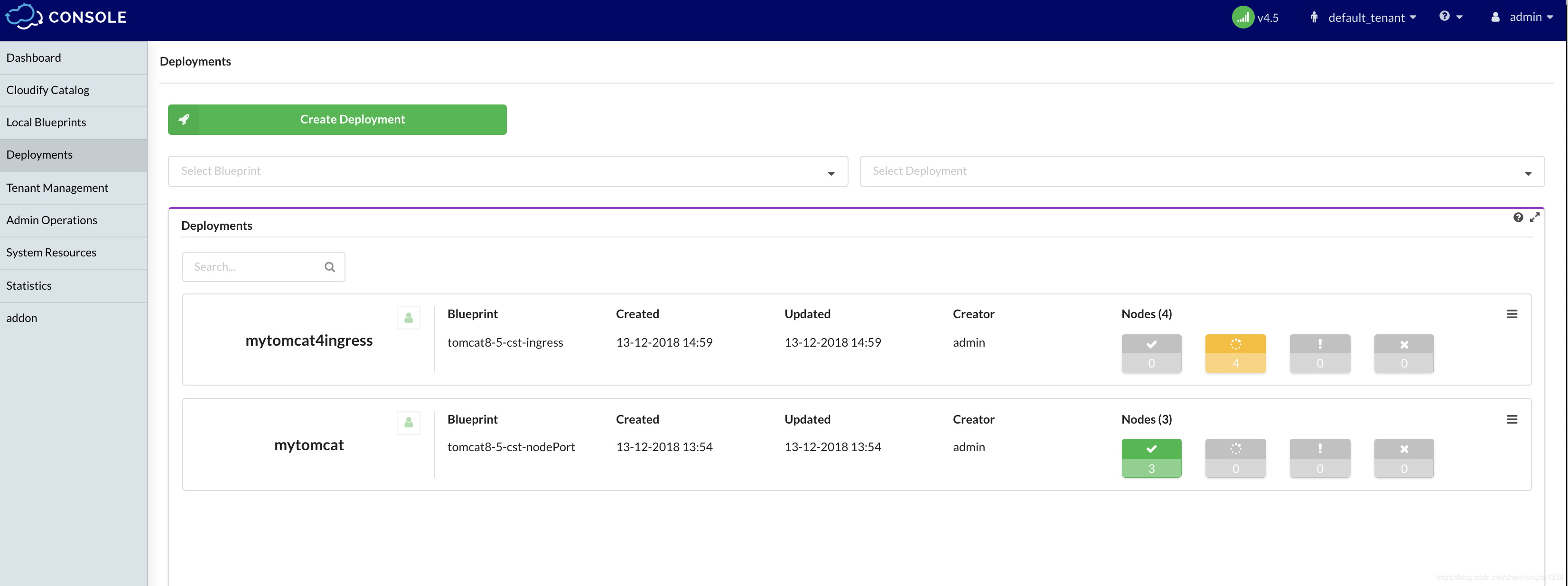
install

install成功后,可以查看k8s的部署信息,已经创建了。
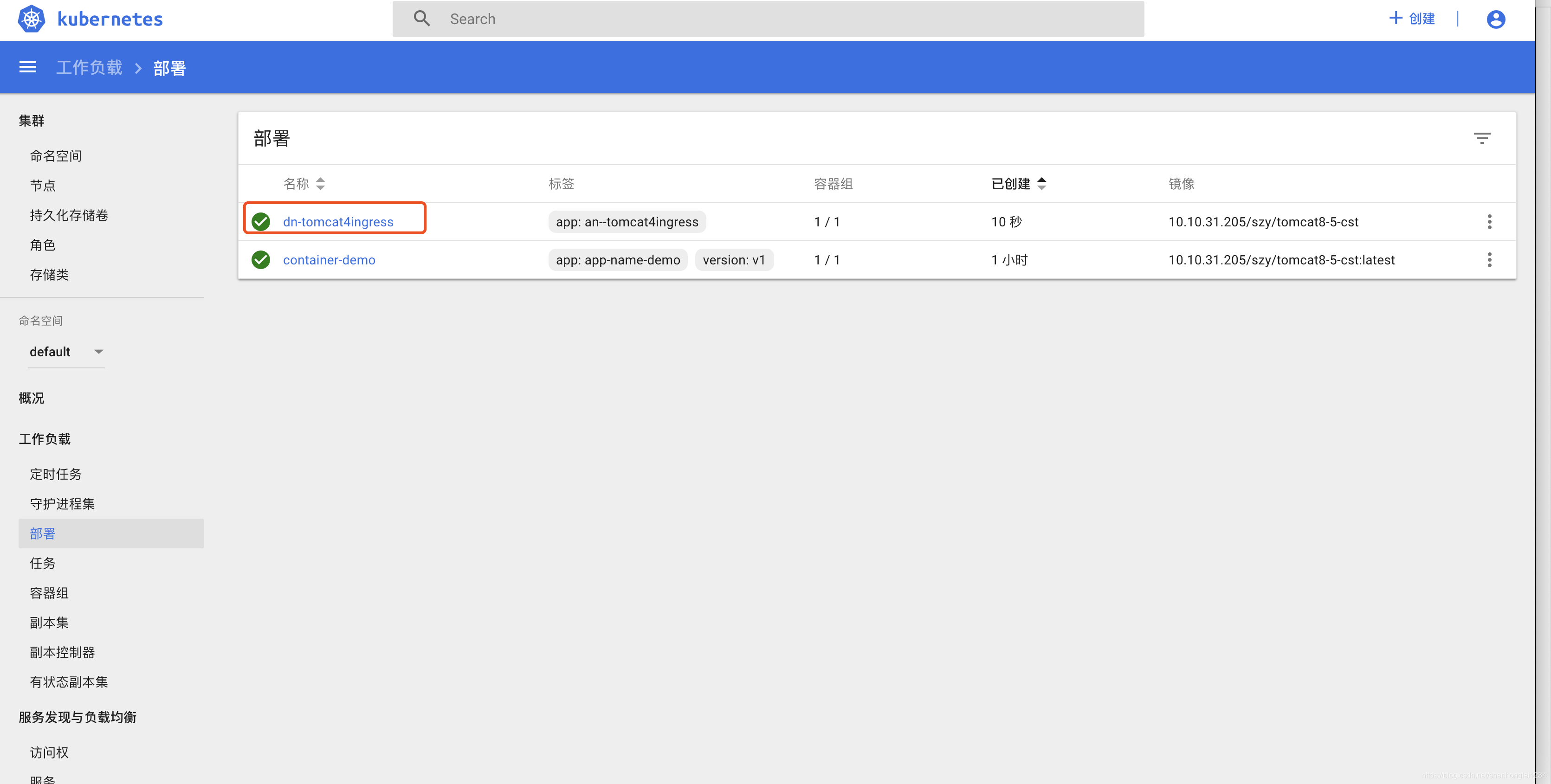
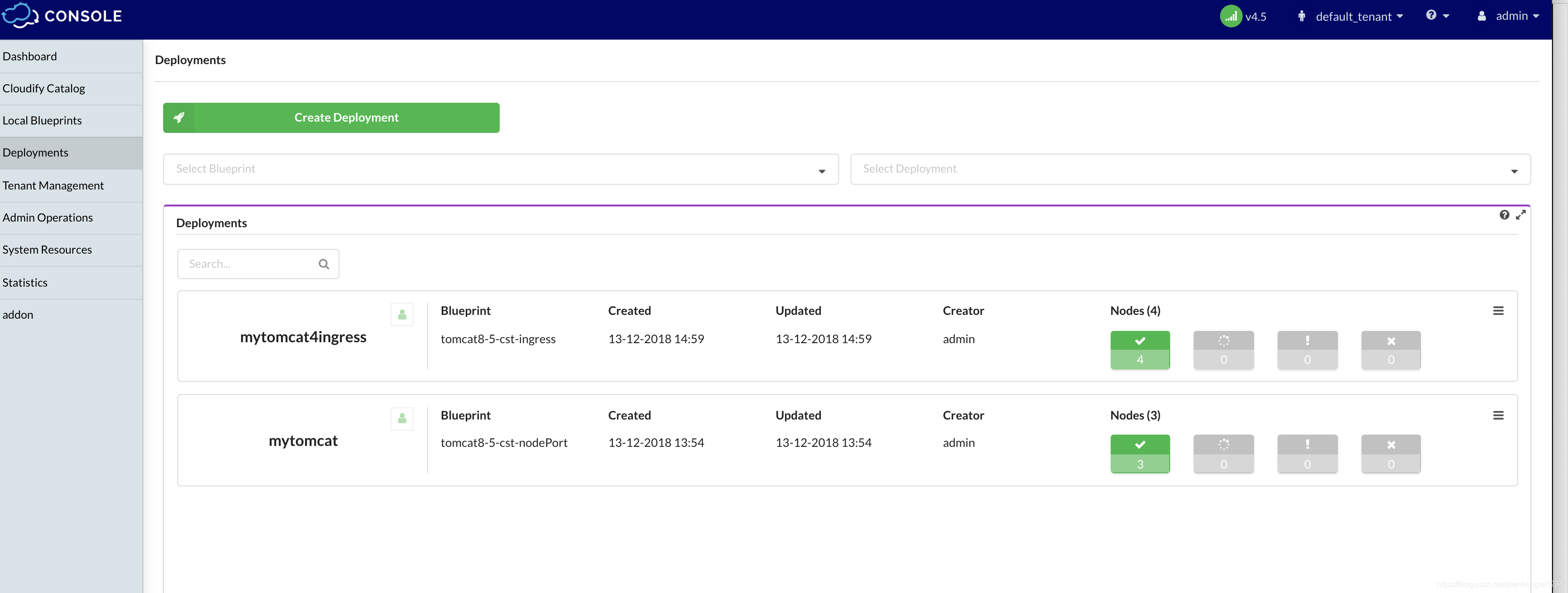
Cloudify显示全部安装成功。
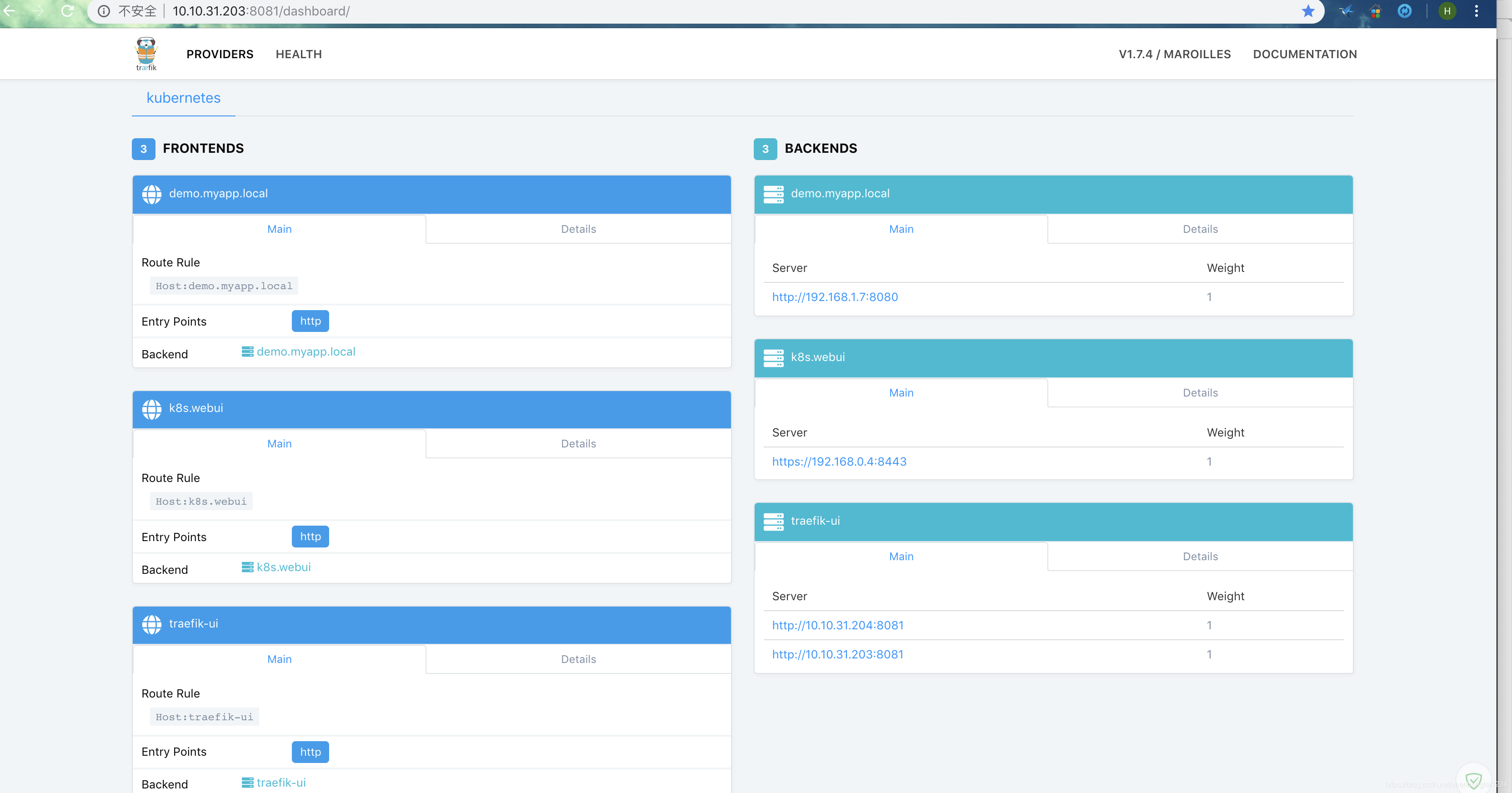
查看我们的traefik是否有我们配置的域名,然后在本地的host中配置下ip地址,就可能访问了。
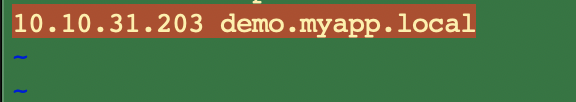
vi /etc/hosts 中配置一下。
来看最终的效果吧。
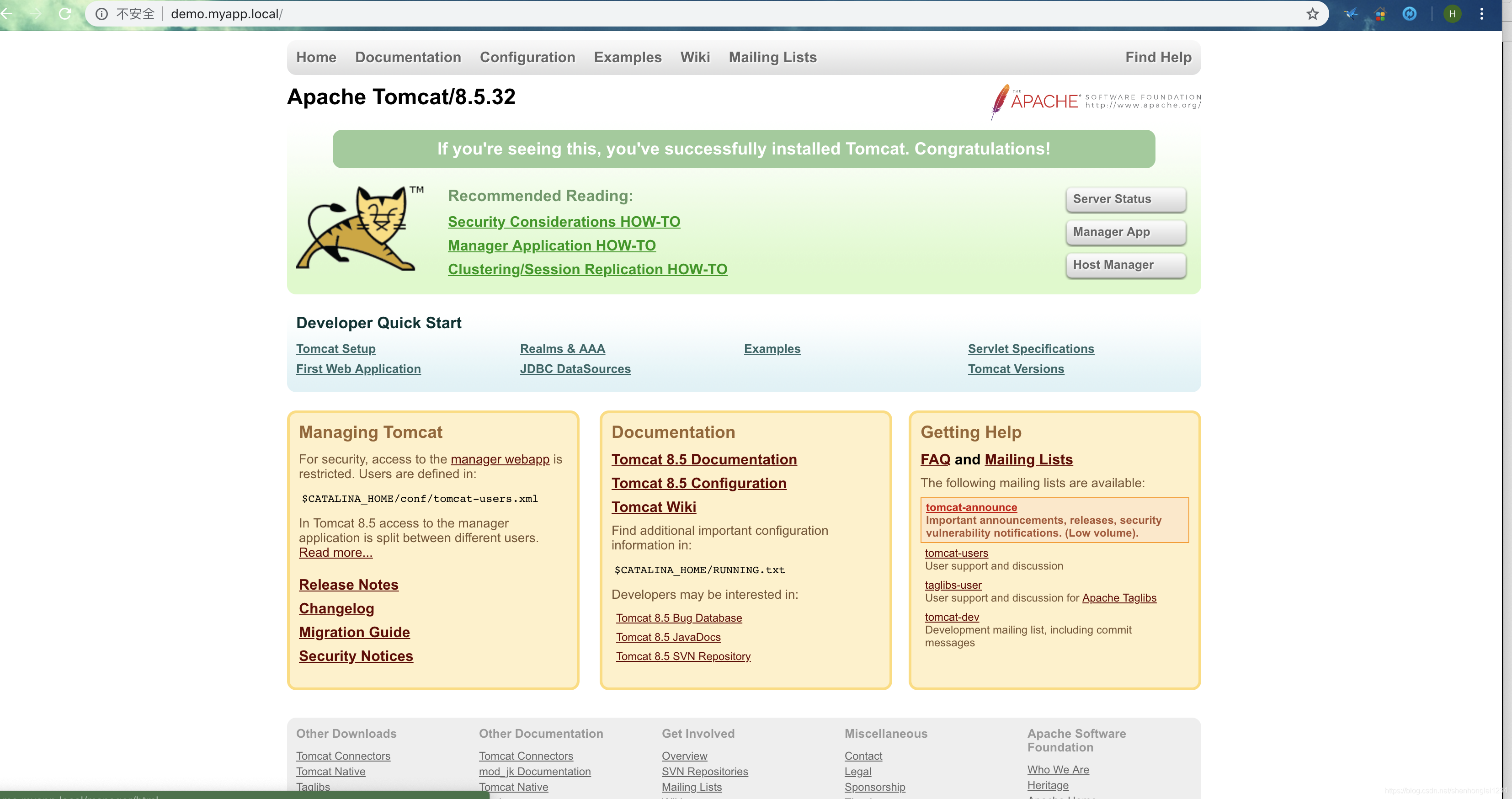
可以像正常的tomcat的使用喽~~~~