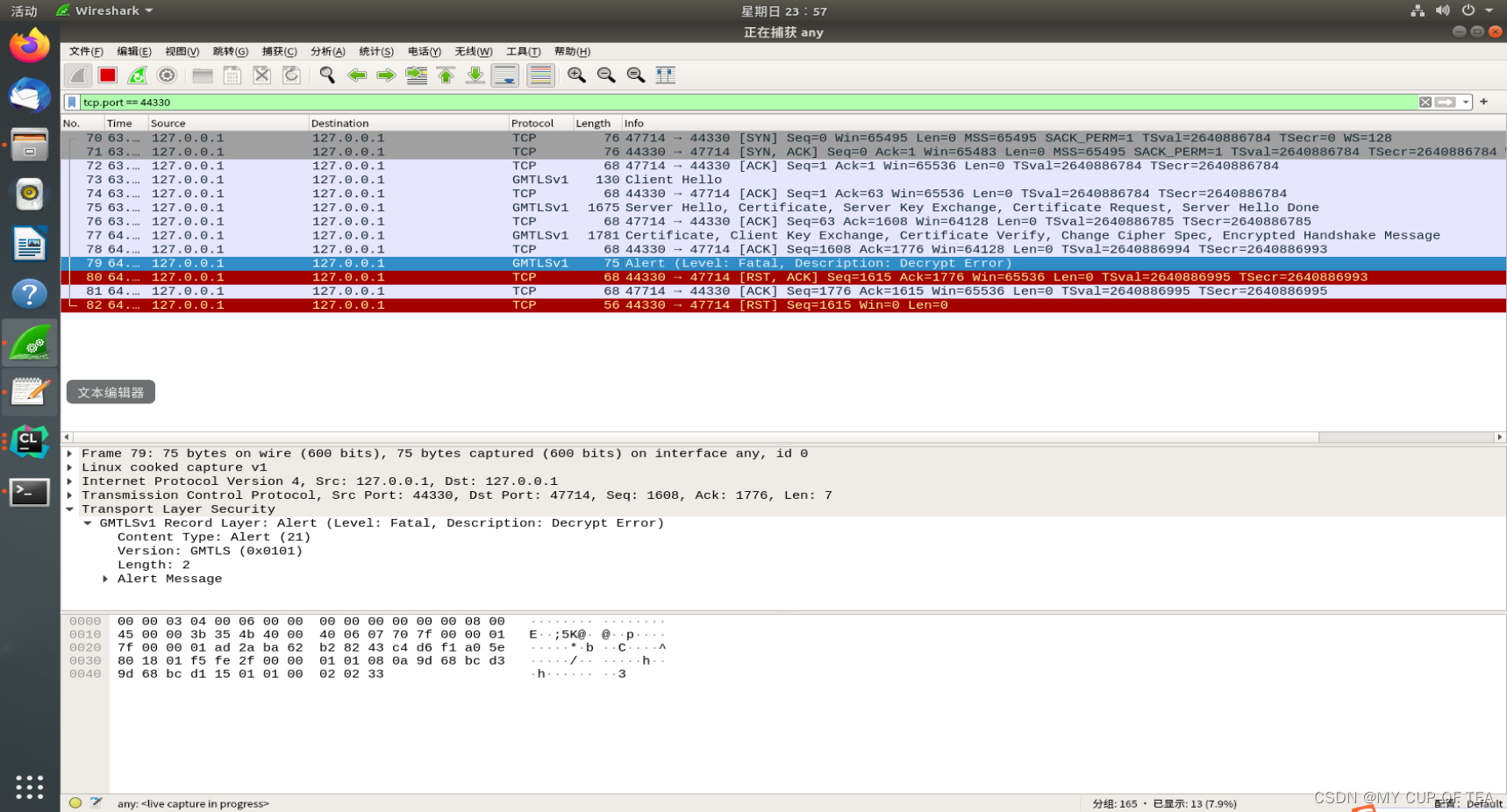
注意事项
- gmssl使用双证书双向认证的gmtl协议报错crypto/sm2/sm2_sign.c 510: sm2_do_verifySSL3 alert write:fatal:decrypt error_MY CUP OF TEA的博客-CSDN博客
- 需要根据上述链接修改gmssl的源代码,才能开启 国密双证书双向认证,否则会报错
目录
first(server) -> second(client)
gmssl客户端 和 吉大正元身份认证网关通信 (本阶段目前存在错误)
gmssl服务端和客户端之间通信
- 生成密钥
- gmssl ecparam -genkey -name sm2p256v1 -text -out encrypt.key
- 查看密钥
- gmssl pkey -in encrypt.key -text
- 根据私钥,生成请求
- gmssl req -new -sm3 -key encrypt.key -out encrypt.req -subj "/C=CN/O=SDT/CN=encrypt"
- 查看请求
- gmssl req -nout -in encrypt.req -text
- 查看证书
- gmssl x509 -noout -text -in sign.pem
- gmssl命令
- 服务端提供的参数:-msg -debug –state
- 客户端提供的参数:-showcerts
sm2Certs双证书通信
- 路径:/home/chy-cpabe/GMSSL_certificate/sm2Certs

- 服务端
- gmssl s_server -gmtls -accept 44330 -key SS.key.pem -cert SS.cert.pem -dkey SE.key.pem -dcert SE.cert.pem -CAfile CA.cert.pem -state -verify 1
- 必须要有 verify,verify是开启gmtls双向证书认证的关键,也就是对等证书验证,客户端也会验证服务端的证书
- 源码:GmSSL-master\apps\s_server.c
G:\code\gmssl_source_code\GmSSL-master\apps\s_server.c
{"verify", OPT_VERIFY, 'n', "Turn on peer certificate verification"},
{"Verify", OPT_UPPER_V_VERIFY, 'n',
"Turn on peer certificate verification, must have a cert"},
{"verify", OPT_VERIFY, 'n', "开启对等证书验证"},
{“Verify”,OPT_UPPER_V_VERIFY,'n',
"开启对等证书验证,必须有证书"},case OPT_VERIFY:
s_server_verify = SSL_VERIFY_PEER | SSL_VERIFY_CLIENT_ONCE;
verify_args.depth = atoi(opt_arg());
if (!s_quiet)
BIO_printf(bio_err, "verify depth is %d\n", verify_args.depth);
break;
case OPT_UPPER_V_VERIFY:
s_server_verify =
SSL_VERIFY_PEER | SSL_VERIFY_FAIL_IF_NO_PEER_CERT |
SSL_VERIFY_CLIENT_ONCE;
verify_args.depth = atoi(opt_arg());
if (!s_quiet)
BIO_printf(bio_err,
"verify depth is %d, must return a certificate\n",
verify_args.depth);- 由源代码可知,传入的参数 depth 并没有什么关键性的作用,只是接收并输出即可,并不会真正控制证书的层级和深度
chy-cpabe@ubuntu:~/GMSSL_certificate/sm2Certs$ gmssl s_server -gmtls -accept 44330 -key SS.key.pem -cert SS.cert.pem -dkey SE.key.pem -dcert SE.cert.pem -CAfile CA.cert.pem -state -verify 1
verify depth is 1
Using default temp DH parameters
[GMTLS_DEBUG] set sm2 signing certificate
[GMTLS_DEBUG] set sm2 signing private key
[GMTLS_DEBUG] set sm2 encryption certificate
[GMTLS_DEBUG] set sm2 decryption private key
ACCEPT
SSL_accept:before SSL initialization
SSL_accept:before SSL initialization
SSL_accept:SSLv3/TLS read client hello
SSL_accept:SSLv3/TLS write server hello
SSL_accept:SSLv3/TLS write certificate
SSL_accept:SSLv3/TLS write key exchange
SSL_accept:SSLv3/TLS write certificate request
SSL_accept:SSLv3/TLS write server done
SSL_accept:SSLv3/TLS write server done
depth=1 C = CN, ST = BJ, L = HaiDian, O = Beijing JNTA Technology LTD., OU = SORB of TASS, CN = Test CA (SM2)
verify return:1
depth=0 C = CN, ST = BJ, L = HaiDian, O = Beijing JNTA Technology LTD., OU = BSRC of TASS, CN = client sign (SM2)
verify return:1
SSL_accept:SSLv3/TLS read client certificate
ssl_get_algorithm2=f227000008x
SSL_accept:SSLv3/TLS read client key exchange
SSL_accept:SSLv3/TLS read certificate verify
SSL_accept:SSLv3/TLS read change cipher spec
SSL_accept:SSLv3/TLS read finished
SSL_accept:SSLv3/TLS write change cipher spec
SSL_accept:SSLv3/TLS write finished
-----BEGIN SSL SESSION PARAMETERS-----
MIICmAIBAQICAQEEAuATBCAWcAdtfPyMiEJmINUd/e/AmYdNqNTalV1AAbACRSQE
CgQwtuURXPYQpQ7gQIZ3fWRd9QpsP0Zi57oDT1D/X1xVBL3wy9yrr/BOpRw2afsu
4DH3oQYCBGMw/gSiBAICHCCjggIfMIICGzCCAcGgAwIBAgIJAIVjx+dwZIdmMAoG
CCqBHM9VAYN1MIGCMQswCQYDVQQGEwJDTjELMAkGA1UECAwCQkoxEDAOBgNVBAcM
B0hhaURpYW4xJTAjBgNVBAoMHEJlaWppbmcgSk5UQSBUZWNobm9sb2d5IExURC4x
FTATBgNVBAsMDFNPUkIgb2YgVEFTUzEWMBQGA1UEAwwNVGVzdCBDQSAoU00yKTAe
Fw0yMDA2MjAxMDE4MjZaFw0yNDA3MjkxMDE4MjZaMIGGMQswCQYDVQQGEwJDTjEL
MAkGA1UECAwCQkoxEDAOBgNVBAcMB0hhaURpYW4xJTAjBgNVBAoMHEJlaWppbmcg
Sk5UQSBUZWNobm9sb2d5IExURC4xFTATBgNVBAsMDEJTUkMgb2YgVEFTUzEaMBgG
A1UEAwwRY2xpZW50IHNpZ24gKFNNMikwWTATBgcqhkjOPQIBBggqgRzPVQGCLQNC
AARV/eII1n2NVqYjwt9r9A5Eh6Z0iG+WUpsw4sGxhfKL0vr0OKcur6DZqjqLDSCr
ZEhU6yuntNtaW+pexPblqXAroxowGDAJBgNVHRMEAjAAMAsGA1UdDwQEAwIGwDAK
BggqgRzPVQGDdQNIADBFAiEAiX+PoCNW/n9SDbv6/o+NyCCV/7kBgunc7w5b7xGm
4RICIBMDlLjPZE2ACYhu1Wjqph23PfMPMgae4+Gtd7wzFz2UpAYEBAEAAAA=
-----END SSL SESSION PARAMETERS-----
Client certificate
-----BEGIN CERTIFICATE-----
MIICGzCCAcGgAwIBAgIJAIVjx+dwZIdmMAoGCCqBHM9VAYN1MIGCMQswCQYDVQQG
EwJDTjELMAkGA1UECAwCQkoxEDAOBgNVBAcMB0hhaURpYW4xJTAjBgNVBAoMHEJl
aWppbmcgSk5UQSBUZWNobm9sb2d5IExURC4xFTATBgNVBAsMDFNPUkIgb2YgVEFT
UzEWMBQGA1UEAwwNVGVzdCBDQSAoU00yKTAeFw0yMDA2MjAxMDE4MjZaFw0yNDA3
MjkxMDE4MjZaMIGGMQswCQYDVQQGEwJDTjELMAkGA1UECAwCQkoxEDAOBgNVBAcM
B0hhaURpYW4xJTAjBgNVBAoMHEJlaWppbmcgSk5UQSBUZWNobm9sb2d5IExURC4x
FTATBgNVBAsMDEJTUkMgb2YgVEFTUzEaMBgGA1UEAwwRY2xpZW50IHNpZ24gKFNN
MikwWTATBgcqhkjOPQIBBggqgRzPVQGCLQNCAARV/eII1n2NVqYjwt9r9A5Eh6Z0
iG+WUpsw4sGxhfKL0vr0OKcur6DZqjqLDSCrZEhU6yuntNtaW+pexPblqXAroxow
GDAJBgNVHRMEAjAAMAsGA1UdDwQEAwIGwDAKBggqgRzPVQGDdQNIADBFAiEAiX+P
oCNW/n9SDbv6/o+NyCCV/7kBgunc7w5b7xGm4RICIBMDlLjPZE2ACYhu1Wjqph23
PfMPMgae4+Gtd7wzFz2U
-----END CERTIFICATE-----
subject=/C=CN/ST=BJ/L=HaiDian/O=Beijing JNTA Technology LTD./OU=BSRC of TASS/CN=client sign (SM2)
issuer=/C=CN/ST=BJ/L=HaiDian/O=Beijing JNTA Technology LTD./OU=SORB of TASS/CN=Test CA (SM2)
Shared ciphers:SM9-WITH-SMS4-SM3:SM9DHE-WITH-SMS4-SM3:SM2-WITH-SMS4-SM3:SM2DHE-WITH-SMS4-SM3:RSA-WITH-SMS4-SHA1:RSA-WITH-SMS4-SM3
CIPHER is SM2-WITH-SMS4-SM3
Secure Renegotiation IS supported
- 客户端
- gmssl s_client -gmtls -connect localhost:44330 -key CS.key.pem -cert CS.cert.pem -dkey CE.key.pem -dcert CE.cert.pem -CAfile CA.cert.pem -state
chy-cpabe@ubuntu:~/GMSSL_certificate/sm2Certs$ gmssl s_client -gmtls -connect localhost:44330 -key CS.key.pem -cert CS.cert.pem -dkey CE.key.pem -dcert CE.cert.pem -CAfile CA.cert.pem -state -showcerts
[GMTLS_DEBUG] set sm2 signing certificate
[GMTLS_DEBUG] set sm2 signing private key
[GMTLS_DEBUG] set sm2 encryption certificate
[GMTLS_DEBUG] set sm2 decryption private key
CONNECTED(00000003)
SSL_connect:before SSL initialization
SSL_connect:SSLv3/TLS write client hello
SSL_connect:SSLv3/TLS write client hello
SSL_connect:SSLv3/TLS read server hello
depth=1 C = CN, ST = BJ, L = HaiDian, O = Beijing JNTA Technology LTD., OU = SORB of TASS, CN = Test CA (SM2)
verify return:1
depth=0 C = CN, ST = BJ, L = HaiDian, O = Beijing JNTA Technology LTD., OU = BSRC of TASS, CN = server sign (SM2)
verify return:1
SSL_connect:SSLv3/TLS read server certificate
Z=BCDCCB61AADD790C076DAC60ED09DDD5285A906A4025DD748DA2FB5816464C58
C=00021E3082021A308201C0A0030201020209008563C7E770648765300A06082A811CCF55018375308182310B300906035504061302434E310B300906035504080C02424A3110300E06035504070C074861694469616E31253023060355040A0C1C4265696A696E67204A4E544120546563686E6F6C6F6779204C54442E31153013060355040B0C0C534F5242206F6620544153533116301406035504030C0D546573742043412028534D3229301E170D3230303632303130313832365A170D3234303732393130313832365A308185310B300906035504061302434E310B300906035504080C02424A3110300E06035504070C074861694469616E31253023060355040A0C1C4265696A696E67204A4E544120546563686E6F6C6F6779204C54442E31153013060355040B0C0C42535243206F6620544153533119301706035504030C1073657276657220656E632028534D32293059301306072A8648CE3D020106082A811CCF5501822D03420004B999853302F02CC522CC4CCA287019E86B901FC24E3CCF9A61B93BB177B28C2CE8E23C5C522DF73C23F7AC36FF688CB2E685A3FA4770103F7C99EFC32D06C11FA31A301830090603551D1304023000300B0603551D0F040403020338300A06082A811CCF550183750348003045022100EC4368F400870BED441817AF4D359BDC61A9EDFDDEE54AB0C185084B450C46B902206E0C3A08BC584590046DC85603CD4E8A51F97D9669B1ACA3E2A3627BE61D49A2
SSL_connect:SSLv3/TLS read server key exchange
SSL_connect:SSLv3/TLS read server certificate request
SSL_connect:SSLv3/TLS read server done
SSL_connect:SSLv3/TLS write client certificate
SSL_connect:SSLv3/TLS write client key exchange
ssl_get_algorithm2=3268600008x
SSL_connect:SSLv3/TLS write certificate verify
SSL_connect:SSLv3/TLS write change cipher spec
SSL_connect:SSLv3/TLS write finished
SSL_connect:SSLv3/TLS write finished
SSL_connect:SSLv3/TLS read change cipher spec
SSL_connect:SSLv3/TLS read finished
---
Certificate chain
0 s:/C=CN/ST=BJ/L=HaiDian/O=Beijing JNTA Technology LTD./OU=BSRC of TASS/CN=server sign (SM2)
i:/C=CN/ST=BJ/L=HaiDian/O=Beijing JNTA Technology LTD./OU=SORB of TASS/CN=Test CA (SM2)
-----BEGIN CERTIFICATE-----
MIICGjCCAcGgAwIBAgIJAIVjx+dwZIdkMAoGCCqBHM9VAYN1MIGCMQswCQYDVQQG
EwJDTjELMAkGA1UECAwCQkoxEDAOBgNVBAcMB0hhaURpYW4xJTAjBgNVBAoMHEJl
aWppbmcgSk5UQSBUZWNobm9sb2d5IExURC4xFTATBgNVBAsMDFNPUkIgb2YgVEFT
UzEWMBQGA1UEAwwNVGVzdCBDQSAoU00yKTAeFw0yMDA2MjAxMDE4MjVaFw0yNDA3
MjkxMDE4MjVaMIGGMQswCQYDVQQGEwJDTjELMAkGA1UECAwCQkoxEDAOBgNVBAcM
B0hhaURpYW4xJTAjBgNVBAoMHEJlaWppbmcgSk5UQSBUZWNobm9sb2d5IExURC4x
FTATBgNVBAsMDEJTUkMgb2YgVEFTUzEaMBgGA1UEAwwRc2VydmVyIHNpZ24gKFNN
MikwWTATBgcqhkjOPQIBBggqgRzPVQGCLQNCAAS0lHzt7CkOzCtyf6VwCqoT2PYD
CL/AJrCsHa+6lE8wDZ7DShI2bvfmrpavndEW67CHQOlO0q6/aoEB0PoAgpopoxow
GDAJBgNVHRMEAjAAMAsGA1UdDwQEAwIGwDAKBggqgRzPVQGDdQNHADBEAiB06JWp
uxFbGBfvG9juhe2Umu/auI1H2XeMdvDjbOtfuQIgMXT8jewkzq9TR3OPzRTkZCRH
3H+xKEb8r8JsEEStwaU=
-----END CERTIFICATE-----
1 s:/C=CN/ST=BJ/L=HaiDian/O=Beijing JNTA Technology LTD./OU=BSRC of TASS/CN=server enc (SM2)
i:/C=CN/ST=BJ/L=HaiDian/O=Beijing JNTA Technology LTD./OU=SORB of TASS/CN=Test CA (SM2)
-----BEGIN CERTIFICATE-----
MIICGjCCAcCgAwIBAgIJAIVjx+dwZIdlMAoGCCqBHM9VAYN1MIGCMQswCQYDVQQG
EwJDTjELMAkGA1UECAwCQkoxEDAOBgNVBAcMB0hhaURpYW4xJTAjBgNVBAoMHEJl
aWppbmcgSk5UQSBUZWNobm9sb2d5IExURC4xFTATBgNVBAsMDFNPUkIgb2YgVEFT
UzEWMBQGA1UEAwwNVGVzdCBDQSAoU00yKTAeFw0yMDA2MjAxMDE4MjZaFw0yNDA3
MjkxMDE4MjZaMIGFMQswCQYDVQQGEwJDTjELMAkGA1UECAwCQkoxEDAOBgNVBAcM
B0hhaURpYW4xJTAjBgNVBAoMHEJlaWppbmcgSk5UQSBUZWNobm9sb2d5IExURC4x
FTATBgNVBAsMDEJTUkMgb2YgVEFTUzEZMBcGA1UEAwwQc2VydmVyIGVuYyAoU00y
KTBZMBMGByqGSM49AgEGCCqBHM9VAYItA0IABLmZhTMC8CzFIsxMyihwGehrkB/C
TjzPmmG5O7F3sows6OI8XFIt9zwj96w2/2iMsuaFo/pHcBA/fJnvwy0GwR+jGjAY
MAkGA1UdEwQCMAAwCwYDVR0PBAQDAgM4MAoGCCqBHM9VAYN1A0gAMEUCIQDsQ2j0
AIcL7UQYF69NNZvcYant/d7lSrDBhQhLRQxGuQIgbgw6CLxYRZAEbchWA81OilH5
fZZpsayj4qNie+YdSaI=
-----END CERTIFICATE-----
2 s:/C=CN/ST=BJ/L=HaiDian/O=Beijing JNTA Technology LTD./OU=SORB of TASS/CN=Test CA (SM2)
i:/C=CN/ST=BJ/L=HaiDian/O=Beijing JNTA Technology LTD./OU=SORB of TASS/CN=Test CA (SM2)
-----BEGIN CERTIFICATE-----
MIICWjCCAgCgAwIBAgIJAP5W2mLaOWq5MAoGCCqBHM9VAYN1MIGCMQswCQYDVQQG
EwJDTjELMAkGA1UECAwCQkoxEDAOBgNVBAcMB0hhaURpYW4xJTAjBgNVBAoMHEJl
aWppbmcgSk5UQSBUZWNobm9sb2d5IExURC4xFTATBgNVBAsMDFNPUkIgb2YgVEFT
UzEWMBQGA1UEAwwNVGVzdCBDQSAoU00yKTAeFw0yMDA2MjAxMDE4MjVaFw0yNDA3
MjkxMDE4MjVaMIGCMQswCQYDVQQGEwJDTjELMAkGA1UECAwCQkoxEDAOBgNVBAcM
B0hhaURpYW4xJTAjBgNVBAoMHEJlaWppbmcgSk5UQSBUZWNobm9sb2d5IExURC4x
FTATBgNVBAsMDFNPUkIgb2YgVEFTUzEWMBQGA1UEAwwNVGVzdCBDQSAoU00yKTBZ
MBMGByqGSM49AgEGCCqBHM9VAYItA0IABArjN7ag+H8D12eqXJpMeTOR9m3sB2RC
ojH7fZPB77SDfHZb9g1lcqUhrug0nw2F8wBMsLfjvsK3wQn/ryi3YvSjXTBbMB0G
A1UdDgQWBBRCcBGiEpd09qSpUlkiGkZ+q+CFbDAfBgNVHSMEGDAWgBRCcBGiEpd0
9qSpUlkiGkZ+q+CFbDAMBgNVHRMEBTADAQH/MAsGA1UdDwQEAwIBBjAKBggqgRzP
VQGDdQNIADBFAiBjdylWVsUoTRcHu9DoMHv4lgtYJMf2xHAGLoJUjmbizAIhAOFD
i3EmFVUgGVdgbnztFZcBLxtBzIAh/Q4Q3dm3/MFu
-----END CERTIFICATE-----
---
Server certificate
subject=/C=CN/ST=BJ/L=HaiDian/O=Beijing JNTA Technology LTD./OU=BSRC of TASS/CN=server sign (SM2)
issuer=/C=CN/ST=BJ/L=HaiDian/O=Beijing JNTA Technology LTD./OU=SORB of TASS/CN=Test CA (SM2)
---
Acceptable client certificate CA names
/C=CN/ST=BJ/L=HaiDian/O=Beijing JNTA Technology LTD./OU=SORB of TASS/CN=Test CA (SM2)
Client Certificate Types: RSA sign, DSA sign
---
SSL handshake has read 2121 bytes and written 2115 bytes
Verification: OK
---
New, GMTLSv1.1, Cipher is SM2-WITH-SMS4-SM3
Server public key is 256 bit
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : GMTLSv1.1
Cipher : SM2-WITH-SMS4-SM3
Session-ID: 1670076D7CFC8C88426620D51DFDEFC099874DA8D4DA955D4001B0024524040A
Session-ID-ctx:
Master-Key: B6E5115CF610A50EE04086777D645DF50A6C3F4662E7BA034F50FF5F5C5504BDF0CBDCABAFF04EA51C3669FB2EE031F7
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1664155140
Timeout : 7200 (sec)
Verify return code: 0 (ok)
Extended master secret: no
---
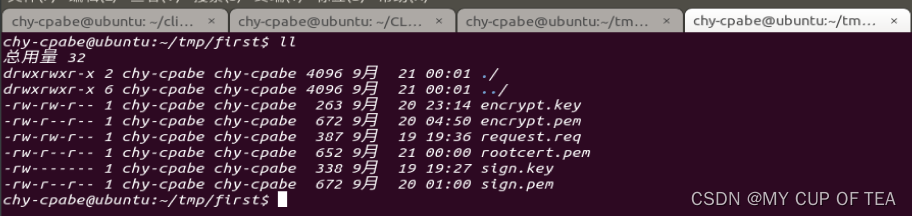
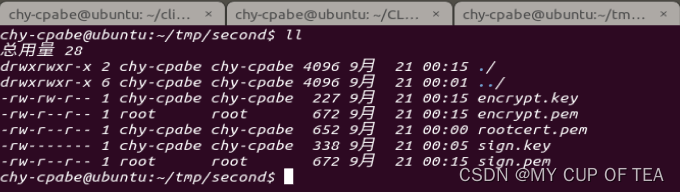
吉大正元PKI派发的两对签名和加密双证书之间通信
相关内容
- first(server) -> second(client)
- first路径: /home/chy-cpabe/tmp/first
- second路径:/home/chy-cpabe/tmp/second
证书名称
- encrypt.key 加密私钥
- encrypt.pem 加密证书
- sign.key 签名私钥
- sign.pem 签名证书
- rootcert.pem 根证书
first作为服务端
second作为客户端
- 服务端
- gmssl s_server -gmtls -accept 44330 -key sign.key -cert sign.pem -dkey encrypt.key -dcert encrypt.pem -CAfile rootcert.pem -state -verify 1
chy-cpabe@ubuntu:~/tmp/first$ gmssl s_server -gmtls -accept 44330 -key sign.key -cert sign.pem -dkey encrypt.key -dcert encrypt.pem -CAfile rootcert.pem -state -verify 1
verify depth is 1
Using default temp DH parameters
[GMTLS_DEBUG] set sm2 signing certificate
[GMTLS_DEBUG] set sm2 signing private key
[GMTLS_DEBUG] set sm2 encryption certificate
[GMTLS_DEBUG] set sm2 decryption private key
ACCEPT
SSL_accept:before SSL initialization
SSL_accept:before SSL initialization
SSL_accept:SSLv3/TLS read client hello
SSL_accept:SSLv3/TLS write server hello
SSL_accept:SSLv3/TLS write certificate
SSL_accept:SSLv3/TLS write key exchange
SSL_accept:SSLv3/TLS write certificate request
SSL_accept:SSLv3/TLS write server done
SSL_accept:SSLv3/TLS write server done
depth=1 C = CN, O = SDT, CN = SDTCA SM2
verify return:1
depth=0 C = CN, O = SDT, CN = encrypt
verify return:1
SSL_accept:SSLv3/TLS read client certificate
ssl_get_algorithm2=e7bcf00008x
SSL_accept:SSLv3/TLS read client key exchange
SSL_accept:SSLv3/TLS read certificate verify
SSL_accept:SSLv3/TLS read change cipher spec
SSL_accept:SSLv3/TLS read finished
SSL_accept:SSLv3/TLS write change cipher spec
SSL_accept:SSLv3/TLS write finished
-----BEGIN SSL SESSION PARAMETERS-----
MIICQQIBAQICAQEEAuATBCDvMDMjHF+PCTjwx5X6SCfBO26qG1VTYekEc4oBhx4R
3wQwzUIGQ08Y/rU1vUp2OeRVHynrigjiBchmbFLuYzIWVjI7bET8y1FgkA9gK9H7
1bWZoQYCBGMxCi2iBAICHCCjggHIMIIBxDCCAWqgAwIBAgIIbWIFSpEszbwwCgYI
KoEcz1UBg3UwLzELMAkGA1UEBhMCQ04xDDAKBgNVBAoMA1NEVDESMBAGA1UEAwwJ
U0RUQ0EgU00yMB4XDTIyMDkyMTAyNDcwM1oXDTI3MDkyMDAyNDcwM1owLTELMAkG
A1UEBhMCQ04xDDAKBgNVBAoMA1NEVDEQMA4GA1UEAwwHZW5jcnlwdDBZMBMGByqG
SM49AgEGCCqBHM9VAYItA0IABOfaNlRm3f7SDM3c7UAfJB1W7fWVfGjBOooU/IQb
pXKeXsFhwrT1uOdvQurPOfSBMH5j33z/hQTV/se7mR2bMGmjcjBwMAsGA1UdDwQE
AwIGwDAhBgNVHR8EGjAYMBagFKAShhBodHRwOi8vMTI3LjAuMC4xMB0GA1UdDgQW
BBTSHzbgPVJVSELlvK3MrKHd+d4PIjAfBgNVHSMEGDAWgBQIF9WfrzTikWWPK87N
8rWq57HivDAKBggqgRzPVQGDdQNIADBFAiBQvYSXsyF8AF5BWkYXUZKuIRldlMO5
xOLG3fpm4KS0XgIhAN5UsbUwsyx3hPBZLltQ956jVJETinGv9OTEfD1tuTDqpAYE
BAEAAAA=
-----END SSL SESSION PARAMETERS-----
Client certificate
-----BEGIN CERTIFICATE-----
MIIBxDCCAWqgAwIBAgIIbWIFSpEszbwwCgYIKoEcz1UBg3UwLzELMAkGA1UEBhMC
Q04xDDAKBgNVBAoMA1NEVDESMBAGA1UEAwwJU0RUQ0EgU00yMB4XDTIyMDkyMTAy
NDcwM1oXDTI3MDkyMDAyNDcwM1owLTELMAkGA1UEBhMCQ04xDDAKBgNVBAoMA1NE
VDEQMA4GA1UEAwwHZW5jcnlwdDBZMBMGByqGSM49AgEGCCqBHM9VAYItA0IABOfa
NlRm3f7SDM3c7UAfJB1W7fWVfGjBOooU/IQbpXKeXsFhwrT1uOdvQurPOfSBMH5j
33z/hQTV/se7mR2bMGmjcjBwMAsGA1UdDwQEAwIGwDAhBgNVHR8EGjAYMBagFKAS
hhBodHRwOi8vMTI3LjAuMC4xMB0GA1UdDgQWBBTSHzbgPVJVSELlvK3MrKHd+d4P
IjAfBgNVHSMEGDAWgBQIF9WfrzTikWWPK87N8rWq57HivDAKBggqgRzPVQGDdQNI
ADBFAiBQvYSXsyF8AF5BWkYXUZKuIRldlMO5xOLG3fpm4KS0XgIhAN5UsbUwsyx3
hPBZLltQ956jVJETinGv9OTEfD1tuTDq
-----END CERTIFICATE-----
subject=/C=CN/O=SDT/CN=encrypt
issuer=/C=CN/O=SDT/CN=SDTCA SM2
Shared ciphers:SM9-WITH-SMS4-SM3:SM9DHE-WITH-SMS4-SM3:SM2-WITH-SMS4-SM3:SM2DHE-WITH-SMS4-SM3:RSA-WITH-SMS4-SHA1:RSA-WITH-SMS4-SM3
CIPHER is SM2-WITH-SMS4-SM3
Secure Renegotiation IS supported
hello
ERROR
shutting down SSL
CONNECTION CLOSED
ACCEPT
- 客户端
- gmssl s_client -gmtls -connect localhost:44330 -key sign.key -cert sign.pem -dkey encrypt.key -dcert encrypt.pem -CAfile rootcert.pem -state -showcerts
chy-cpabe@ubuntu:~/tmp/second$ gmssl s_client -gmtls -connect localhost:44330 -key sign.key -cert sign.pem -dkey encrypt.key -dcert encrypt.pem -CAfile rootcert.pem -state -showcerts
[GMTLS_DEBUG] set sm2 signing certificate
[GMTLS_DEBUG] set sm2 signing private key
[GMTLS_DEBUG] set sm2 encryption certificate
[GMTLS_DEBUG] set sm2 decryption private key
CONNECTED(00000003)
SSL_connect:before SSL initialization
SSL_connect:SSLv3/TLS write client hello
SSL_connect:SSLv3/TLS write client hello
SSL_connect:SSLv3/TLS read server hello
depth=1 C = CN, O = SDT, CN = SDTCA SM2
verify return:1
depth=0 C = CN, O = SDT, CN = server
verify return:1
SSL_connect:SSLv3/TLS read server certificate
Z=17AE1C9FD1008FAF130C9873AB28EBFBF9B1C14BEDF417A2C59534D4DE0AD3EC
C=0001C7308201C330820169A00302010202084D271B78E5E63ED3300A06082A811CCF55018375302F310B300906035504061302434E310C300A060355040A0C035344543112301006035504030C09534454434120534D32301E170D3232303932303036353030305A170D3332303931373036353030305A302C310B300906035504061302434E310C300A060355040A0C03534454310F300D06035504030C067365727665723059301306072A8648CE3D020106082A811CCF5501822D03420004BC39C09B0EDF0D05F519F396ABF923E14211477575A561C227F6D0F48490512249717D40DD56E96C166A1C14662257700AD77D3FAAF0AEFBF8CC0E511ACA153AA3723070300B0603551D0F04040302043030210603551D1F041A30183016A014A0128610687474703A2F2F3132372E302E302E31301D0603551D0E041604141587CA6751D0742743E58F7D19915969690DF702301F0603551D230418301680140817D59FAF34E291658F2BCECDF2B5AAE7B1E2BC300A06082A811CCF55018375034800304502200B43000E6E76504FE3D854A45ABBC9C5F3F6B378E575E0D543C0715F38C15C810221008AD145EC60920C49B03F779B4033D62D2842F9A22BE7323851E2E7F839F3A40A
SSL_connect:SSLv3/TLS read server key exchange
SSL_connect:SSLv3/TLS read server certificate request
SSL_connect:SSLv3/TLS read server done
SSL_connect:SSLv3/TLS write client certificate
SSL_connect:SSLv3/TLS write client key exchange
ssl_get_algorithm2=8619800008x
SSL_connect:SSLv3/TLS write certificate verify
SSL_connect:SSLv3/TLS write change cipher spec
SSL_connect:SSLv3/TLS write finished
SSL_connect:SSLv3/TLS write finished
SSL_connect:SSLv3/TLS read change cipher spec
SSL_connect:SSLv3/TLS read finished
---
Certificate chain
0 s:/C=CN/O=SDT/CN=server
i:/C=CN/O=SDT/CN=SDTCA SM2
-----BEGIN CERTIFICATE-----
MIIBxDCCAWmgAwIBAgIINwb7oeZmMW4wCgYIKoEcz1UBg3UwLzELMAkGA1UEBhMC
Q04xDDAKBgNVBAoMA1NEVDESMBAGA1UEAwwJU0RUQ0EgU00yMB4XDTIyMDkyMDA2
NTAwMFoXDTMyMDkxNzA2NTAwMFowLDELMAkGA1UEBhMCQ04xDDAKBgNVBAoMA1NE
VDEPMA0GA1UEAwwGc2VydmVyMFkwEwYHKoZIzj0CAQYIKoEcz1UBgi0DQgAE5eMR
L3fEq4uY6Eyuwwr4w7NukLJZYnmvLhftRuivanAX0Zq0uMAZB6nvvKLqwDjS5xfR
JR8o4PDZiwy702C9OqNyMHAwCwYDVR0PBAQDAgbAMCEGA1UdHwQaMBgwFqAUoBKG
EGh0dHA6Ly8xMjcuMC4wLjEwHQYDVR0OBBYEFCGBPUxVjGCBb+mAO/swdQAlFlU4
MB8GA1UdIwQYMBaAFAgX1Z+vNOKRZY8rzs3ytarnseK8MAoGCCqBHM9VAYN1A0kA
MEYCIQDYLvNxiPa61U+cWTZwpMqzTHOLrAIlo/ygExFuHLNqYgIhANCG27z52TCA
oTuQu8ZE3jQjAfansfgaaKZyVYRttwZu
-----END CERTIFICATE-----
1 s:/C=CN/O=SDT/CN=server
i:/C=CN/O=SDT/CN=SDTCA SM2
-----BEGIN CERTIFICATE-----
MIIBwzCCAWmgAwIBAgIITScbeOXmPtMwCgYIKoEcz1UBg3UwLzELMAkGA1UEBhMC
Q04xDDAKBgNVBAoMA1NEVDESMBAGA1UEAwwJU0RUQ0EgU00yMB4XDTIyMDkyMDA2
NTAwMFoXDTMyMDkxNzA2NTAwMFowLDELMAkGA1UEBhMCQ04xDDAKBgNVBAoMA1NE
VDEPMA0GA1UEAwwGc2VydmVyMFkwEwYHKoZIzj0CAQYIKoEcz1UBgi0DQgAEvDnA
mw7fDQX1GfOWq/kj4UIRR3V1pWHCJ/bQ9ISQUSJJcX1A3VbpbBZqHBRmIldwCtd9
P6rwrvv4zA5RGsoVOqNyMHAwCwYDVR0PBAQDAgQwMCEGA1UdHwQaMBgwFqAUoBKG
EGh0dHA6Ly8xMjcuMC4wLjEwHQYDVR0OBBYEFBWHymdR0HQnQ+WPfRmRWWlpDfcC
MB8GA1UdIwQYMBaAFAgX1Z+vNOKRZY8rzs3ytarnseK8MAoGCCqBHM9VAYN1A0gA
MEUCIAtDAA5udlBP49hUpFq7ycXz9rN45XXg1UPAcV84wVyBAiEAitFF7GCSDEmw
P3ebQDPWLShC+aIr5zI4UeLn+DnzpAo=
-----END CERTIFICATE-----
2 s:/C=CN/O=SDT/CN=SDTCA SM2
i:/C=CN/O=SDT/CN=SDTCA SM2
-----BEGIN CERTIFICATE-----
MIIBtDCCAVmgAwIBAgIIOPps5HcsfX4wCgYIKoEcz1UBg3UwLzELMAkGA1UEBhMC
Q04xDDAKBgNVBAoMA1NEVDESMBAGA1UEAwwJU0RUQ0EgU00yMCAXDTIyMDQyMTEy
MTU0OFoYDzIwNTIwNDEzMTIxNTQ4WjAvMQswCQYDVQQGEwJDTjEMMAoGA1UECgwD
U0RUMRIwEAYDVQQDDAlTRFRDQSBTTTIwWTATBgcqhkjOPQIBBggqgRzPVQGCLQNC
AAQD837XAcEb1IMLPCGSE/I25QVgr3vaeuS8KFaOLZeNIpO2gOFF6EUDmoAHbC6U
ZeIfcyKAJf/EqQ7HcMmjaYKWo10wWzALBgNVHQ8EBAMCAQYwDAYDVR0TBAUwAwEB
/zAdBgNVHQ4EFgQUCBfVn6804pFljyvOzfK1quex4rwwHwYDVR0jBBgwFoAUCBfV
n6804pFljyvOzfK1quex4rwwCgYIKoEcz1UBg3UDSQAwRgIhAIgteb0r4smsZ6TA
Ih+XO8FQ2MZ3t5FH/0OGrIR8SVayAiEA3XTP9UDJnLOY3pZ4VMtYAvx4A1ducIJ5
DftGpEhN3GA=
-----END CERTIFICATE-----
---
Server certificate
subject=/C=CN/O=SDT/CN=server
issuer=/C=CN/O=SDT/CN=SDTCA SM2
---
Acceptable client certificate CA names
/C=CN/O=SDT/CN=SDTCA SM2
Client Certificate Types: RSA sign, DSA sign
---
SSL handshake has read 1698 bytes and written 1773 bytes
Verification: OK
---
New, GMTLSv1.1, Cipher is SM2-WITH-SMS4-SM3
Server public key is 256 bit
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : GMTLSv1.1
Cipher : SM2-WITH-SMS4-SM3
Session-ID: EF3033231C5F8F0938F0C795FA4827C13B6EAA1B555361E904738A01871E11DF
Session-ID-ctx:
Master-Key: CD4206434F18FEB535BD4A7639E4551F29EB8A08E205C8666C52EE63321656323B6C44FCCB5160900F602BD1FBD5B599
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1664158253
Timeout : 7200 (sec)
Verify return code: 0 (ok)
Extended master secret: no
---
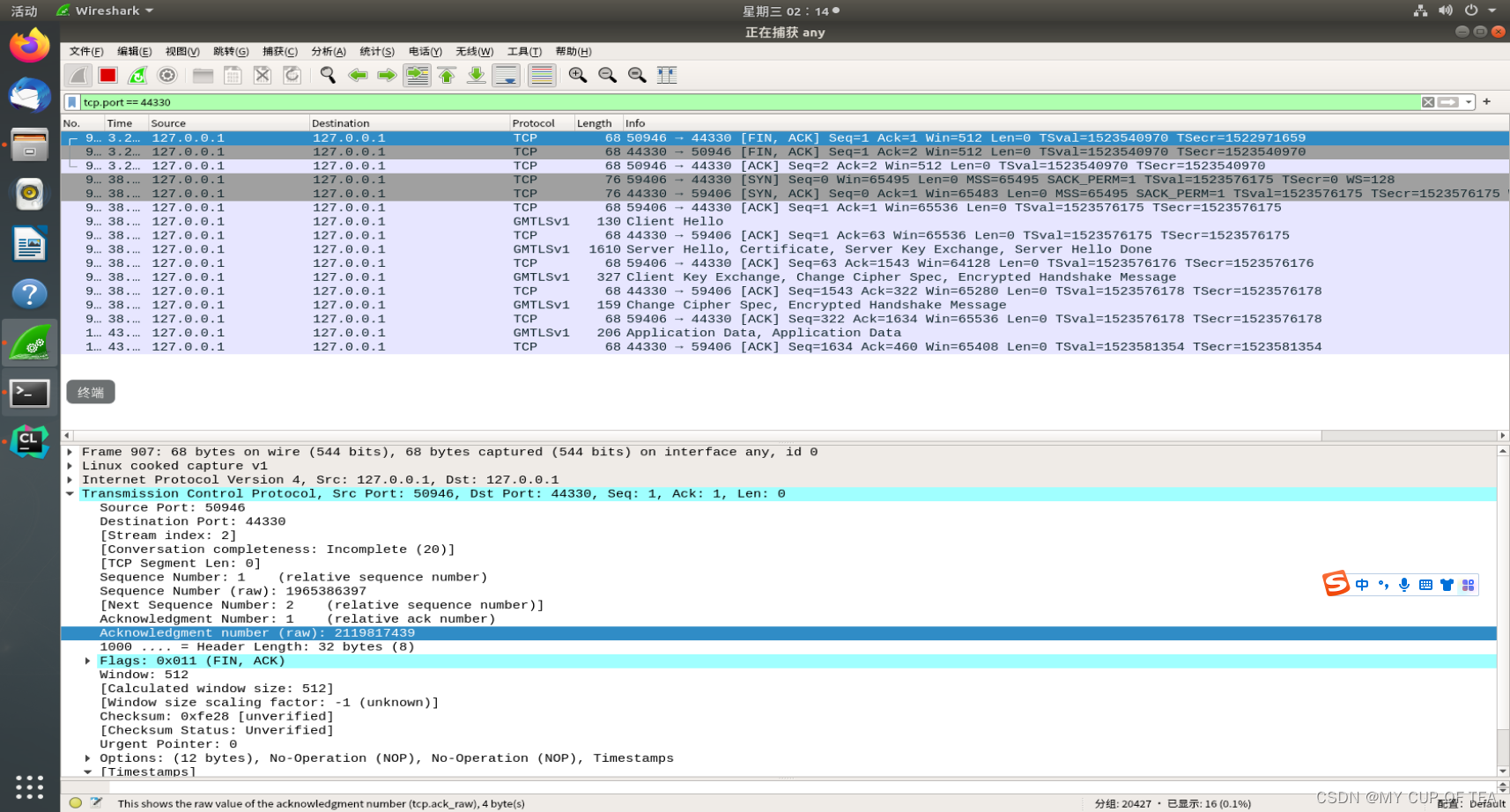
吉大正元SDK+USBkey 和 gmssl服务端程序通信 (出错,未解决)
- first路径:/home/chy-cpabe/tmp/first second也可以,均是由根证书派发出来的签名和加密证书
- 服务端
- gmssl s_server -gmtls -accept 44330 -key sign.key -cert sign.pem -dkey encrypt.key -dcert encrypt.pem -CAfile rootcert.pem -state -verify 3
chy-cpabe@ubuntu:~/tmp/first$ gmssl s_server -gmtls -accept 44330 -key sign.key -cert sign.pem -dkey encrypt.key -dcert encrypt.pem -CAfile rootcert.pem -state -verify 3
verify depth is 3
Using default temp DH parameters
[GMTLS_DEBUG] set sm2 signing certificate
[GMTLS_DEBUG] set sm2 signing private key
[GMTLS_DEBUG] set sm2 encryption certificate
[GMTLS_DEBUG] set sm2 decryption private key
ACCEPT
SSL_accept:before SSL initialization
SSL_accept:before SSL initialization
SSL_accept:SSLv3/TLS read client hello
SSL_accept:SSLv3/TLS write server hello
SSL_accept:SSLv3/TLS write certificate
SSL_accept:SSLv3/TLS write key exchange
SSL_accept:SSLv3/TLS write certificate request
SSL_accept:SSLv3/TLS write server done
SSL_accept:SSLv3/TLS write server done
depth=1 C = CN, O = SDT, CN = SDTCA SM2
verify return:1
depth=0 C = CN, O = SDT, CN = Device2
verify return:1
SSL_accept:SSLv3/TLS read client certificate
ssl_get_algorithm2=b0abe00008x
SSL_accept:SSLv3/TLS read client key exchange
crypto/sm2/sm2_sign.c 510: sm2_do_verify
SSL3 alert write:fatal:decrypt error
SSL_accept:error in error
ERROR
139623765504000:error:1417B07B:SSL routines:tls_process_cert_verify:bad signature:ssl/statem/statem_srvr.c:2941:
shutting down SSL
CONNECTION CLOSED
ACCEPT
- 客户端
- 指定服务地址和端口号即可
- 源代码
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include "zwy_iot_interface.h"
//TODO 填充信息
#define WORK_PATH "/home/chy-cpabe/CLionProjects/jdzy_ssl" //工作路径
#define CA_PATH "/home/chy-cpabe/CLionProjects/jdzy_ssl/rootcert.pem" //CA路径
//#define CERT_REQ_IP "192.168.80.110" //服务地址
//#define CERT_ERQ_PORT 8889 //服务端口
#define CERT_REQ_IP "127.0.0.1" //服务地址
#define CERT_ERQ_PORT 44330 //服务端口
unsigned char req_data[] = "GET /index.html\r\n\r\n";
int main() {
//获取版本号
printf("版本号为: %s\n" ,zwy_iot_get_version());
//变量初始化
void *sdk_ctx = nullptr; //sdk操作句柄
void *dev_ctx = nullptr; //设备操作句柄
void *ssl_ctx = nullptr; //ssl操作句柄
size_t key_num = 0; //USBKEY数量
unsigned int state = 0; //USBKEY状态
int ret = 0; //函数执行结果
unsigned int verify_result = 0; //证书验证结果
size_t key_name_len = 0; //USBKey标识长度
//TODO 证书的名字和PIN,证书的名字可以直接赋值或者通过zwy_iot_get_ukey_state进行获取
// char tmpname[] = "F623281404280421";
char key_name[128] = {0}; //USBKey标识
char usr_pin[] = "123456"; //USBKey标识PIN
// char usr_pin_new[] = "111111"; //更新PIN
size_t nwrite = 0; //写入字节数
size_t nread = 0; //读取字节数
unsigned char buf[4096]={0};//缓冲区
//初始化
ret = zwy_iot_init(&sdk_ctx, WORK_PATH, CA_PATH);
if (ret != ZWY_IOT_OK){
printf("zwy_iot_init return 0x%04X\n",ret);
goto clear;
}
//获取USBKey状态
// ret = zwy_iot_get_ukey_state(key_name,&state);
// if (ret != ZWY_IOT_OK ){
// printf("zwy_iot_get_ukey_state return 0x%04X\n",ret);
// goto clear;
// }
//TODO 检测设备状态
// ZWY_IOT_KEY_ST_ABSENT: 设备不存在
// ZWY_IOT_KEY_ST_PRESENT: 设备存在
// ZWY_IOT_KEY_ST_UNKNOW: 设备状态未知
//获取插入的USBKey数量
ret = zwy_iot_get_dev_number(&key_num);
if (ret != ZWY_IOT_OK){
printf("zwy_iot_get_dev_number return 0x%04X\n",ret);
goto clear;
}
printf("USBKEY的数量为:%zu\n",key_num);
//TODO USBKEY的数量从0到key_num范围之内,只提取第一个USBKEY
if(key_num > 0){
//获取第1个usbkey的标识
ret = zwy_iot_get_dev_name(key_name, &key_name_len,sizeof(key_name), 1);
if (ret == ZWY_IOT_OK){
printf("zwy_iot_get_dev_name return 0x%04X\n", ret);
// goto clear;
}
//获取USBKey状态
ret = zwy_iot_get_ukey_state(key_name,&state);
if (ret == ZWY_IOT_OK ){
printf("zwy_iot_get_ukey_state return 0x%04X\n",ret);
// goto clear;
}
//使用USBKey标识,连接USBKey设备
ret = zwy_iot_connect_dev(key_name,usr_pin,&dev_ctx);
if (ret == ZWY_IOT_OK){
printf("zwy_iot_connect_dev return 0x%04X\n",ret);
// goto clear;
}
//建立SSLVPN连接
ret = zwy_iot_sslvpn_connect(&ssl_ctx,&verify_result,CERT_REQ_IP,
CERT_ERQ_PORT,sdk_ctx,dev_ctx);
if (ret != ZWY_IOT_OK ){
printf("zwy_iot_sslvpn_connect return 0x%04X\n", ret);
goto clear;
}
//向SSLVPN中写入数据
ret = zwy_iot_sslvpn_write(&nwrite,req_data,sizeof(req_data),ssl_ctx);
if (ret != ZWY_IOT_OK ){
printf("zwy_iot_sslvpn_write return 0x%04X\n", ret);
goto clear;
}
//从SSLVPN中读取数据
// ret = zwy_iot_sslvpn_read(buf, &nread, sizeof(buf), ssl_ctx);
// if (ret != ZWY_IOT_OK) {
// printf("zwy_iot_sslvpn_read return 0x%04X\n", ret);
// goto clear;
// }
// printf("recv data: %s \n", buf);
printf("SSL success \n");
}
clear:
//资源释放
//断开SSLVPN连接
ret = zwy_iot_sslvpn_free(ssl_ctx);
ssl_ctx = nullptr;
//关闭USBKey设备
zwy_iot_close_dev(dev_ctx);
dev_ctx = nullptr;
zwy_iot_free(sdk_ctx);
sdk_ctx = nullptr;
return ret;
}

gmssl客户端 和 吉大正元身份认证网关通信 (本阶段目前存在错误)
- 吉大正元身份认证网关:192.168.80.110 8889
- first路径:/home/chy-cpabe/tmp/first second也可以,均是由根证书派发出来的签名和加密证书
- 客户端
- gmssl s_client -gmtls -connect 192.168.80.110:8889 -key sign.key -cert sign.pem -dkey encrypt.key -dcert encrypt.pem -CAfile rootcert.pem -state
chy-cpabe@ubuntu:~/tmp/first$ gmssl s_client -gmtls -connect 192.168.80.110:8889 -key sign.key -cert sign.pem -dkey encrypt.key -dcert encrypt.pem -CAfile rootcert.pem -state
[GMTLS_DEBUG] set sm2 signing certificate
[GMTLS_DEBUG] set sm2 signing private key
[GMTLS_DEBUG] set sm2 encryption certificate
[GMTLS_DEBUG] set sm2 decryption private key
CONNECTED(00000003)
SSL_connect:before SSL initialization
SSL_connect:SSLv3/TLS write client hello
SSL_connect:SSLv3/TLS write client hello
SSL_connect:SSLv3/TLS read server hello
depth=1 C = CN, O = SDT, CN = SDTCA SM2
verify return:1
depth=0 C = CN, O = SDT, CN = 192.168.80.110
verify return:1
SSL_connect:SSLv3/TLS read server certificate
Z=57A18ADE9AE65C4518E01851C91150B786FEC8CD4FA1C22DCA623E2D1C4B494D
C=0001CF308201CB30820171A003020102020842C7314545E1F9E0300A06082A811CCF55018375302F310B300906035504061302434E310C300A060355040A0C035344543112301006035504030C09534454434120534D32301E170D3232303930383038353031395A170D3237303930373038353031395A3034310B300906035504061302434E310C300A060355040A0C035344543117301506035504030C0E3139322E3136382E38302E3131303059301306072A8648CE3D020106082A811CCF5501822D03420004728DDC8FE396FB0FDAB3242DB3ED4E370A275E0A422215CA62BA993E7FDAB6B400EBD45CA92E31ABAD1B20C7DC868E98DB4439A56CCD6B7501E76B2C2A9D5160A3723070300B0603551D0F04040302043030210603551D1F041A30183016A014A0128610687474703A2F2F3132372E302E302E31301D0603551D0E041604141A0578239BFB5814A30439EB36C65EADB9A12487301F0603551D230418301680140817D59FAF34E291658F2BCECDF2B5AAE7B1E2BC300A06082A811CCF55018375034800304502202A93DC8D02F6E0ADD981DF18F56A6A4266A976C037263B731E08DC52BD11847A022100A5E6D842CC52D7A49B897A92DF49C91E7D52595A12D7B7100C2B70E318A80218
SSL_connect:SSLv3/TLS read server key exchange
SSL_connect:SSLv3/TLS read server certificate request
SSL_connect:SSLv3/TLS read server done
SSL_connect:SSLv3/TLS write client certificate
SSL_connect:SSLv3/TLS write client key exchange
ssl_get_algorithm2=d97f400008x
SSL_connect:SSLv3/TLS write certificate verify
SSL_connect:SSLv3/TLS write change cipher spec
SSL_connect:SSLv3/TLS write finished
SSL3 alert read:fatal:decrypt error
SSL_connect:error in SSLv3/TLS write finished
139882148483072:error:1409441B:SSL routines:ssl3_read_bytes:tlsv1 alert decrypt error:ssl/record/rec_layer_s3.c:1385:SSL alert number 51
---
Certificate chain
0 s:/C=CN/O=SDT/CN=192.168.80.110
i:/C=CN/O=SDT/CN=SDTCA SM2
1 s:/C=CN/O=SDT/CN=192.168.80.110
i:/C=CN/O=SDT/CN=SDTCA SM2
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIByzCCAXGgAwIBAgIIMBQFazElStAwCgYIKoEcz1UBg3UwLzELMAkGA1UEBhMC
Q04xDDAKBgNVBAoMA1NEVDESMBAGA1UEAwwJU0RUQ0EgU00yMB4XDTIyMDkwODA4
NTAxOVoXDTI3MDkwNzA4NTAxOVowNDELMAkGA1UEBhMCQ04xDDAKBgNVBAoMA1NE
VDEXMBUGA1UEAwwOMTkyLjE2OC44MC4xMTAwWTATBgcqhkjOPQIBBggqgRzPVQGC
LQNCAATlDQxehfZeFn05t6UUNR+I0dA2zYjtOeUtHdB/WRCjE6YlMzUYRDmsvHXF
KtXeAioY+DwazbfwkHEBJhyIgzWUo3IwcDALBgNVHQ8EBAMCBsAwIQYDVR0fBBow
GDAWoBSgEoYQaHR0cDovLzEyNy4wLjAuMTAdBgNVHQ4EFgQUSd5ccizI5+TH9ODp
Aq6++mew1OAwHwYDVR0jBBgwFoAUCBfVn6804pFljyvOzfK1quex4rwwCgYIKoEc
z1UBg3UDSAAwRQIhAOdvLFjuQ2ZwbyR26T3PHMyW/Dfli5gpC4TX7xSWFjlbAiBE
6MtGGkPaS1I1lB2Vkiq5ifWNdTCzBzFeV6W6sHeGag==
-----END CERTIFICATE-----
subject=/C=CN/O=SDT/CN=192.168.80.110
issuer=/C=CN/O=SDT/CN=SDTCA SM2
---
Acceptable client certificate CA names
/C=CN/O=SDT/CN=SDTCA SM2
Client Certificate Types: RSA sign, ECDSA sign
---
SSL handshake has read 1154 bytes and written 1773 bytes
Verification: OK
---
New, GMTLSv1.1, Cipher is SM2-WITH-SMS4-SM3
Server public key is 256 bit
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : GMTLSv1.1
Cipher : SM2-WITH-SMS4-SM3
Session-ID:
Session-ID-ctx:
Master-Key: 307742745E494A6FA89F39964AD5B84BB2C82C5C247A6CD0D13FE7D2A557BC634BAC20764CBD84B9EE947B0E462E4AC6
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1663752320
Timeout : 7200 (sec)
Verify return code: 0 (ok)
Extended master secret: no
---
chy-cpabe@ubuntu:~/tmp/first$
- 报错:Decrypt Error

吉大正元SDK+USBkey 和 身份认证网关 之间通信
- 修改程序中服务器的地址和端口号