文章目录
说明
- 现在有一批虚拟机,通过dashboard底层无法登录,但是可以通过工具登录,做了蛮多修改,也不知道是修改到什么了,也不敢乱动人家虚拟机。。。
现在就是发现tty1这个进程和正常的有点不一样。 下面分别记录一下,以后搞懂逻辑了再处理吧。。。
报错
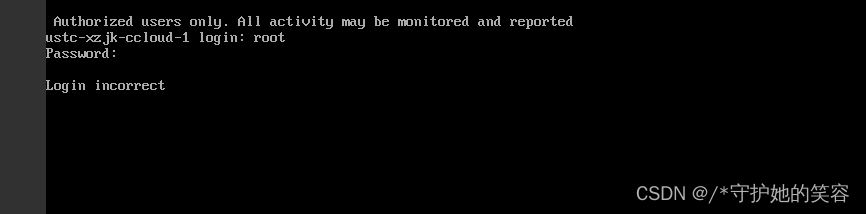
控制台登录虚拟机报错1
- 无论密码正确与否,都会提示下面报错内容
控制台登录虚拟机报错2
- 也有输入错误密码提示上面内容,输入正确密码提示下面内容的,反正最终都是无法登录进系统的!!!
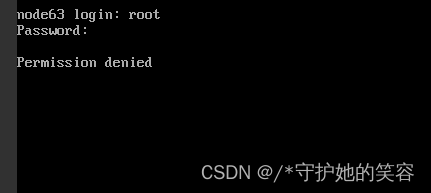
工具登录信息记录
登录工具是CRT
登录日志查询
每次控制台登录,都会生成这几个日志
tail -f /var/log/messages 记录
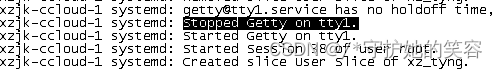
May 20 15:10:19 ustc-xzjk-ccloud-1 systemd: [email protected] has no holdoff time, scheduling restart.
May 20 15:10:19 ustc-xzjk-ccloud-1 systemd: Stopped Getty on tty1.
May 20 15:10:19 ustc-xzjk-ccloud-1 systemd: Started Getty on tty1.
vi编辑历史命令
修改配置文件有如下
[root@ustc-xzjk-ccloud-1 ~]# history | grep vi | more
2 vim /etc/sysctl.conf
5 vim /etc/sysctl.conf
12 vim /etc/sysconfig/ip6tables
15 service iptables restart
16 service iptables status
17 service ip6tables status
18 service ip6tables star
19 service ip6tables status
20 service ip6tables stop
21 vim /etc/sysconfig/ip6tables
22 service ip6tables status
23 service ip6tables stop
24 service ip6tables status
25 service ip6tables stop
26 service ip6tables status
27 service iptables stop
28 service ip6tables status
29 service iptables status
30 service ip6tables status
31 service iptables status
32 service iptables restart
33 service iptables status
34 service ip6tables status
35 service ip6tables stop
36 service ip6tables restart
37 service ip6tables status
38 service ip6tables stop
39 service ip6tables status
40 service iptables status
41 service iptables stop
42 service iptables status
43 service iptables restart
44 service iptables status
45 service iptables stop
46 service iptables status
47 service iptables restart
48 service ip6tables restart
49 service iptables status
50 service ip6tables status
51 vim /etc/sysconfig/ip6tables
52 service ip6tables status
53 service ip6tables restart
54 service ip6tables status
55 vim /etc/sysconfig/ip6tables
56 service ip6tables restart
57 service ip6tables status
58 service iptables status
59 service iptables stop
60 service iptables status
61 service ip6tables status
62 service ip6tables
63 service ip6tables reload
64 service ip6tables stop
65 service ip6tables status
66 service iptables status
67 service iptables stop
68 service iptables status
69 vim /etc/sysconfig/iptables
70 service iptables reload
71 service iptables restart
72 service iptables reload
73 service iptables status
74 service iptables stop
75 service iptables status
76 service iptables start
77 service iptables status
78 service iptables start
79 service iptables stop
80 service iptables status
82 vim /etc/sysctl.conf
89 vim docker-compose.yml
91 service iptables status
92 service ip6tables status
96 vim /etc/sysctl.conf
99 vim /etc/sysctl.conf
105 service docker restart
109 service ip6tables status
110 service iptables status
111 vim /etc/sysctl.conf
114 service iptables status
115 service iptables start
116 service iptables status
122 service docker restart
125 service iptables status
126 vim /etc/sysctl.conf
129 service iptables restart
130 service iptables status
133 service docker restart
138 service iptables status
139 service iptables reload
140 service iptables status
141 vim /etc/sysconfig/iptables
142 service iptables status
143 service ip6tables status
145 service docker restart
147 service iptables status
155 vim harbor.yml
165 vim docker-compose.yml
166 vim harbor.yml
173 service iptables status
175 service iptables stop
176 service iptables status
180 service iptables status
181 service docker restart
195 vim /etc/sysconfig/iptables
196 vi /etc/sysconfig/iptables
197 vim /etc/sysconfig/iptables
198 vim /etc/hostname
200 vim /etc/hosts
201 vi /etc/sysconfig/iptables
213 vim /etc/ntp.conf
229 service ntp start
257 vim /etc/shadow
261 vi shadow
264 vi shadow
274 vim shadow
278 vim shadow
300 vi /etc/profile
303 vi /etc/csh.cshrc
313 vim /etc/ssh/sshd_config
328 systemctl status sshd.service
377 if [ $NFSSTATUS = 0 ] ; then echo "NFS services online:$NFSSTATUS"; echo "Numbers in hosts.allow:$NFSAllowNo"; echo "NFS check result:true"; else if [ $NFSAllowNo != 0 ]; then echo "NFS services online:$NFSSTATUS"; echo "Num
bers in hosts.allow:$NFSAllowNo"; echo "NFS check result:true"; else echo "NFS services online:$NFSSTATUS"; echo "Numbers in hosts.allow:$NFSAllowNo"; echo "NFS check result:false"; fi; fi;
389 telnet_port=`cat /etc/services | grep -w "^telnet" | awk '{print $2}' | awk -F/ 'NR==1 {print $1}'`
401 if [ x"$SSHSTATUS" != "x0" ]; then if [[ `grep "^PermitRootLogin no" /etc/ssh/sshd_config|wc -l` != 0 ]]; then grep "^PermitRootLogin no" /etc/ssh/sshd_config; echo "This device does not permit root to ssh logi
n,check result:true"; else echo "This device permits root to ssh login,check result:false" ; fi; else echo "The ssh service of device is not running,check result:true"; fi
403 if [ x"$TELSTATUS" != "x0" ]; then if ([ -f /etc/securetty ] && [ `grep -i "^pts" /etc/securetty|wc -l` = 0 ]); then echo "This device does not permit root to telnet login,check result:true"; else echo "This devi
ce permits root to telnet login,check result:false"; fi; else echo "The telnet service of device is not running,check result:true" ; fi
480 service iptables status
484 service iptables status
485 service iptables stop
486 service iptables status
517 cd backservice_usercenter/
552 vim repositories.json
626 vim docker-compose.yml
627 service iptables stop
628 service iptables status
629 echo " Authorized users only. All activity may be monitored and reported " > /etc/motd
630 echo " Authorized users only. All activity may be monitored and reported " > /etc/issue.net
631 echo " Authorized users only. All activity may be monitored and reported " > /etc/issue
651 echo " Authorized users only. All activity may be monitored and reported " > /etc/issue.net
656 echo " Authorized users only. All activity may be monitored and reported " >/etc/sshbanner
658 vi /etc/ssh/sshd_config
662 vi /etc/login.defs
669 vi /etc/profile
670 vi /etc/csh.cshrc
671 vi /etc/bashrc
672 vi /etc/csh.login
673 vi /root/.bashrc
674 vi /root/.cshrc
677 vi /etc/hosts.allow
678 vi /etc/hosts.deny
683 vi /etc/pam.d/system-auth
691 vim /etc/hosts.deny
739 if [ $NFSSTATUS = 0 ] ; then echo "NFS services online:$NFSSTATUS"; echo "Numbers in hosts.allow:$NFSAllowNo"; echo "NFS check result:true"; else if [ $NFSAllowNo != 0 ]; then echo "NFS services online:$NFSSTATUS"; echo "Num
bers in hosts.allow:$NFSAllowNo"; echo "NFS check result:true"; else echo "NFS services online:$NFSSTATUS"; echo "Numbers in hosts.allow:$NFSAllowNo"; echo "NFS check result:false"; fi; fi;
751 telnet_port=`cat /etc/services | grep -w "^telnet" | awk '{print $2}' | awk -F/ 'NR==1 {print $1}'`
763 if [ x"$SSHSTATUS" != "x0" ]; then if [[ `grep "^PermitRootLogin no" /etc/ssh/sshd_config|wc -l` != 0 ]]; then grep "^PermitRootLogin no" /etc/ssh/sshd_config; echo "This device does not permit root to ssh logi
n,check result:true"; else echo "This device permits root to ssh login,check result:false" ; fi; else echo "The ssh service of device is not running,check result:true"; fi
765 if [ x"$TELSTATUS" != "x0" ]; then if ([ -f /etc/securetty ] && [ `grep -i "^pts" /etc/securetty|wc -l` = 0 ]); then echo "This device does not permit root to telnet login,check result:true"; else echo "This devi
ce permits root to telnet login,check result:false"; fi; else echo "The telnet service of device is not running,check result:true" ; fi
836 service iptables status
838 vim /etc/sysconfig/iptables
840 vi /etc/sysconfig/iptables
841 service iptables status
842 service iptables restart
843 service iptables status
844 service iptables stop
845 service iptables status
852 vi iptables
855 service iptables status
856 service iptables restart
857 service iptables status
859 vi iptables
861 vi iptables
863 vi iptables
864 service iptables restart
871 vi iptables
872 service iptables status
873 service iptables restart
874 service iptables status
875 vi iptables
880 service iptables restart
881 service iptables status
883 vi iptables
886 vi iptables
888 vim iptables
891 vim /etc/sysconfig/iptables
893 vim /etc/docker/daemon.json
895 vim /etc/sysconfig/iptables
909 service iptables status
930 service iptalbes restart
932 vi /etc/sysconfig/iptables
933 service iptables restart
939 vi iptables
943 vi /etc/sysconfig/iptables
949 service iptables status
957 vi iptables
960 vi /etc/pam.d/su
981 vi /usr/bin/tty
992 vi /etc/grub.conf
993 vi /etc/inittab
998 vi /etc/securetty
999 vi /etc/grub.conf
1000 history | grep vi | more
[root@ustc-xzjk-ccloud-1 ~]#
tty1进程记录【重要】
- 我怀疑就是这个的问题导致的控制台不能登录【该主机运行了很多docker容器,不知道是不是容器占用了这个tty1】
- 可以看到不能通过控制台登录的tty1 的进程是
/sbin/agetty --noclear tty1 linux,我不知道这个是啥意思,也替换不了。。。 - 而正常的tty1的进程是
-bash。。。。

- 可以看到不能通过控制台登录的tty1 的进程是
/etc/sysctl.conf
- 下面三行均为新增
不知道他这是啥意思【好像是启用ipv6?,1是禁用,0好像是启用】,但我注释了,再控制台登录依然不行,和这应该没关系。
[root@ustc-xzjk-ccloud-1 ~]# cat /etc/sysctl.conf
# sysctl settings are defined through files in
# /usr/lib/sysctl.d/, /run/sysctl.d/, and /etc/sysctl.d/.
#
# Vendors settings live in /usr/lib/sysctl.d/.
# To override a whole file, create a new file with the same in
# /etc/sysctl.d/ and put new settings there. To override
# only specific settings, add a file with a lexically later
# name in /etc/sysctl.d/ and put new settings there.
#
# For more information, see sysctl.conf(5) and sysctl.d(5).
net.ipv6.conf.all.disable_ipv6 = 0
net.ipv6.conf.default.disable_ipv6 = 0
net.ipv6.conf.lo.disable_ipv6 = 0
[root@ustc-xzjk-ccloud-1 ~]#
/etc/pam.d/system-auth
- 我简单对比了下配置文件,发现下面新增了一行内容
auth required pam_deny.so
翻译: 对所有不满足上述任意条件的登录请求直接拒绝。required表示一个错误则全返回错误,只不过最后返回错误 - 我有把该行注销再控制台尝试登录,并没有解决,应该和这没关系【我注销没有重启啥服务,这个好像也不需要重启啥服务】
[root@ustc-xzjk-ccloud-1 ~]# cat /etc/pam.d/system-auth
#%PAM-1.0
# This file is auto-generated.
# User changes will be destroyed the next time authconfig is run.
auth required pam_env.so
auth required pam_tally2.so deny=6 onerr=fail no_magic_root unlock_time=120
uth required pam_faildelay.so delay=2000000
auth sufficient pam_unix.so nullok try_first_pass
auth requisite pam_succeed_if.so uid >= 1000 quiet_success
# 下面行是新增的
auth required pam_deny.so
account required pam_unix.so
account sufficient pam_localuser.so
account sufficient pam_succeed_if.so uid < 1000 quiet
account required pam_permit.so
password requisite pam_cracklib.so dcredit=-1 ucredit=-1 lcredit=-1 ocredit=-1 minclass=2 minlen=8
password sufficient pam_unix.so md5 shadow nullok try_first_pass use_authtok
password required pam_deny.so remember=5
session optional pam_keyinit.so revoke
session required pam_limits.so
-session optional pam_systemd.so
session [success=1 default=ignore] pam_succeed_if.so service in crond quiet use_uid
session required pam_unix.so
[root@ustc-xzjk-ccloud-1 ~]#
/etc/profile
- 这个文件被跑脚本,里面的内容基本上都被改了,至于有没有影响无重验证。
下面是无法登录的虚拟机文件内容。
[root@ustc-xzjk-ccloud-1 ~]# cat -n /etc/profile
1 # /etc/profile
2
3 # System wide environment and startup programs, for login setup
4 # Functions and aliases go in /etc/bashrc
5
6 umask 027
7
8 # It's NOT a good idea to change this file unless you know what you
9 # are doing. It's much better to create a custom.sh shell script in
10 # /etc/profile.d/ to make custom changes to your environment, as this
11 # will prevent the need for merging in future updates.
12
13 pathmunge () {
14 case ":${
PATH}:" in
15 *:"$1":*)
16 ;;
17 *)
18 if [ "$2" = "after" ] ; then
19 PATH=$PATH:$1
20 else
21 PATH=$1:$PATH
22 fi
23 esac
24 }
25
26
27 if [ -x /usr/bin/id ]; then
28 if [ -z "$EUID" ]; then
29 # ksh workaround
30 EUID=`/usr/bin/id -u`
31 UID=`/usr/bin/id -ru`
32 fi
33 USER="`/usr/bin/id -un`"
34 LOGNAME=$USER
35 MAIL="/var/spool/mail/$USER"
36 fi
37
38 # Path manipulation
39 if [ "$EUID" = "0" ]; then
40 pathmunge /usr/sbin
41 pathmunge /usr/local/sbin
42 else
43 pathmunge /usr/local/sbin after
44 pathmunge /usr/sbin after
45 fi
46
47 HOSTNAME=`/usr/bin/hostname 2>/dev/null`
48 HISTSIZE=1000
49 if [ "$HISTCONTROL" = "ignorespace" ] ; then
50 export HISTCONTROL=ignoreboth
51 else
52 export HISTCONTROL=ignoredups
53 fi
54
55 export PATH USER LOGNAME MAIL HOSTNAME HISTSIZE HISTCONTROL
56
57 # By default, we want umask to get set. This sets it for login shell
58 # Current threshold for system reserved uid/gids is 200
59 # You could check uidgid reservation validity in
60 # /usr/share/doc/setup-*/uidgid file
61 if [ $UID -gt 199 ] && [ "`/usr/bin/id -gn`" = "`/usr/bin/id -un`" ]; then
62 umask 027
63 else
64 umask 032
65 fi
66
67 for i in /etc/profile.d/*.sh /etc/profile.d/sh.local ; do
68 if [ -r "$i" ]; then
69 if [ "${-#*i}" != "$-" ]; then
70 . "$i"
71 else
72 . "$i" >/dev/null
73 fi
74 fi
75 done
76
77 TMOUT=180
78 export TMOUT
79
80 unset i
81 unset -f pathmunge
82 export PATH=/home/tcloud/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/root/bin
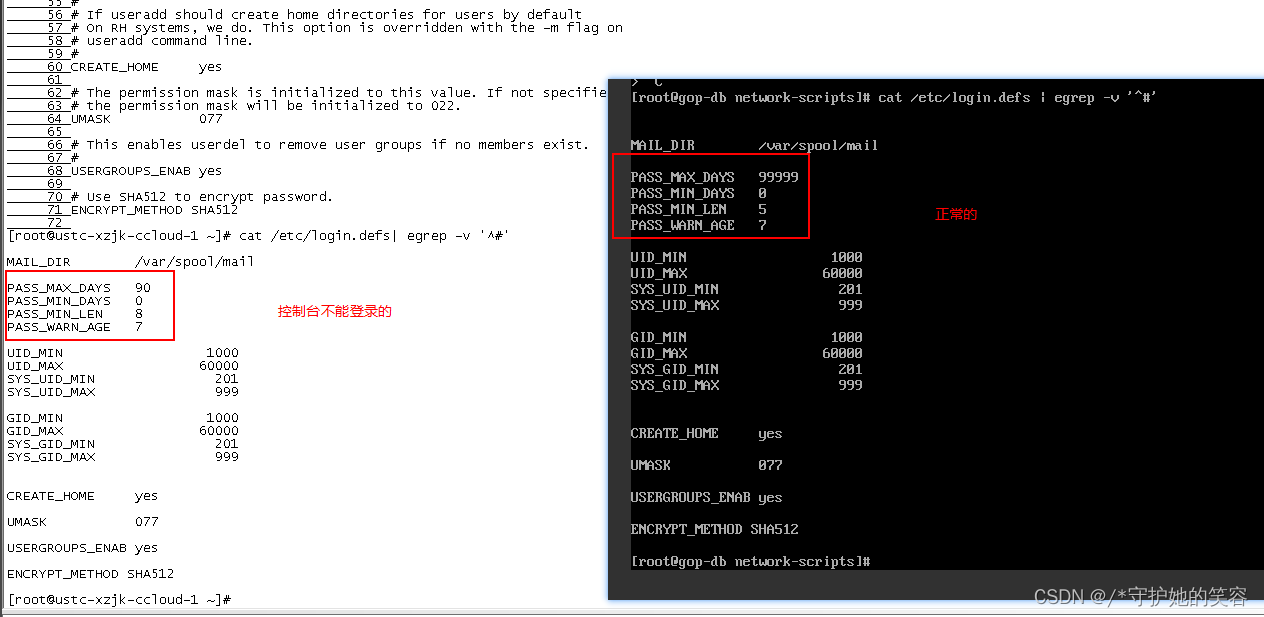
/etc/login.defs
- 我对比了下,这里面就更新了一些失效而已,不存在影响。
/etc/csh.cshrc
umask一般是文件权限,和用户登录应该没关系。
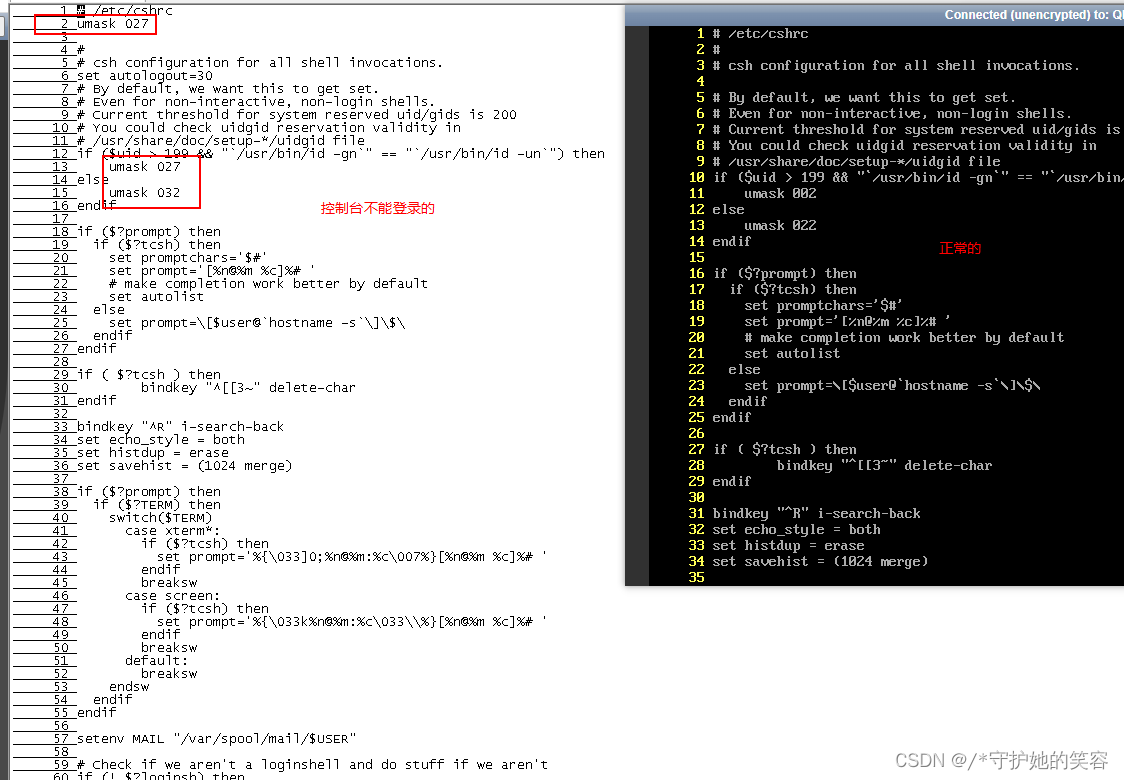
tty1相关的几个配置文件
我对比了能登录的虚拟机配置,这些都是正常的,没有做啥改动。
[root@ustc-xzjk-ccloud-1 ~]# cat /etc/grub.conf
default=0
timeout=0
title CentOS Linux 7 (3.10.0-957.1.3.el7.x86_64)
root (hd0)
kernel /boot/vmlinuz-3.10.0-957.1.3.el7.x86_64 ro root=UUID=f856d385-fe64-4188-b4f8-51f6089b75e6 console=hvc0 LANG=en_US.UTF-8
initrd /boot/initramfs-3.10.0-957.1.3.el7.x86_64.img
[root@ustc-xzjk-ccloud-1 ~]#
[root@ustc-xzjk-ccloud-1 ~]# cat /etc/inittab
# inittab is no longer used when using systemd.
#
# ADDING CONFIGURATION HERE WILL HAVE NO EFFECT ON YOUR SYSTEM.
#
# Ctrl-Alt-Delete is handled by /usr/lib/systemd/system/ctrl-alt-del.target
#
# systemd uses 'targets' instead of runlevels. By default, there are two main targets:
#
# multi-user.target: analogous to runlevel 3
# graphical.target: analogous to runlevel 5
#
# To view current default target, run:
# systemctl get-default
#
# To set a default target, run:
# systemctl set-default TARGET.target
#
[root@ustc-xzjk-ccloud-1 ~]#
[root@ustc-xzjk-ccloud-1 ~]# cat /etc/securetty
console
vc/1
vc/2
vc/3
vc/4
vc/5
vc/6
vc/7
vc/8
vc/9
vc/10
vc/11
ttyS0
tty1
tty2
tty3
tty4
tty5
tty6
tty7
tty8
tty9
tty10
tty11
ttysclp0
sclp_line0
3270/tty1
hvc0
hvc1
hvc2
hvc3
hvc4
hvc5
hvc6
hvc7
hvsi0
hvsi1
hvsi2
xvc0
[root@ustc-xzjk-ccloud-1 ~]#
修改密码提示 permission denied
- 报错如下,网上有很多方法,都照着弄了,没用。
[root@ustc-xzjk-ccloud-1 ~]# passwd root
Changing password for user root.
passwd: Permission denied
[root@ustc-xzjk-ccloud-1 ~]#
- 我们可以绕过这个报错,换一种语法来修改
echo user:newpasswd | chpasswd
[root@ustc-xzjk-ccloud-1 ~]# passwd root
Changing password for user root.
passwd: Permission denied
[root@ustc-xzjk-ccloud-1 ~]#
[root@ustc-xzjk-ccloud-1 ~]# echo root:root | chpasswd
[root@ustc-xzjk-ccloud-1 ~]#